八、K8S metrics-server
发布时间:2024年01月16日
下载yaml文件
wget https://github.com/kubernetes-sigs/metrics-server/releases/latest/download/high-availability.yaml
改名:mv high-availability.yaml metrics-server.yaml
查看镜像地址
查看镜像地址
grep -rn image high-availability.yaml
150: image: k8s.gcr.io/metrics-server/metrics-server:v0.6.1
151: imagePullPolicy: IfNotPresent
设置镜像地址为阿里云
sed -i "s#k8s.gcr.io/metrics-server#registry.cn-hangzhou.aliyuncs.com/chenby#g" high-availability.yaml
查看镜像地址已更新
grep -rn image high-availability.yaml
150: image: registry.cn-hangzhou.aliyuncs.com/chenby/metrics-server:v0.6.1
151: imagePullPolicy: IfNotPresent
vim high-availability.yaml
添加"- --kubelet-insecure-tls"
执行配置
kubectl apply -f high-availability.yaml
[root@k8s-master-1 cfg]# kubectl get pod -n kube-system
NAME READY STATUS RESTARTS AGE
metrics-server-6f6c655778-ds596 1/1 Running 0 28m
metrics-server-6f6c655778-m6r7g 1/1 Running 0 28m
#启动正常,查看top 报错如下图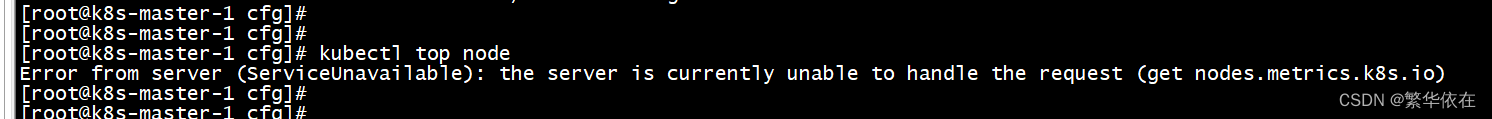 ?查看API-server日志报错如下
?查看API-server日志报错如下

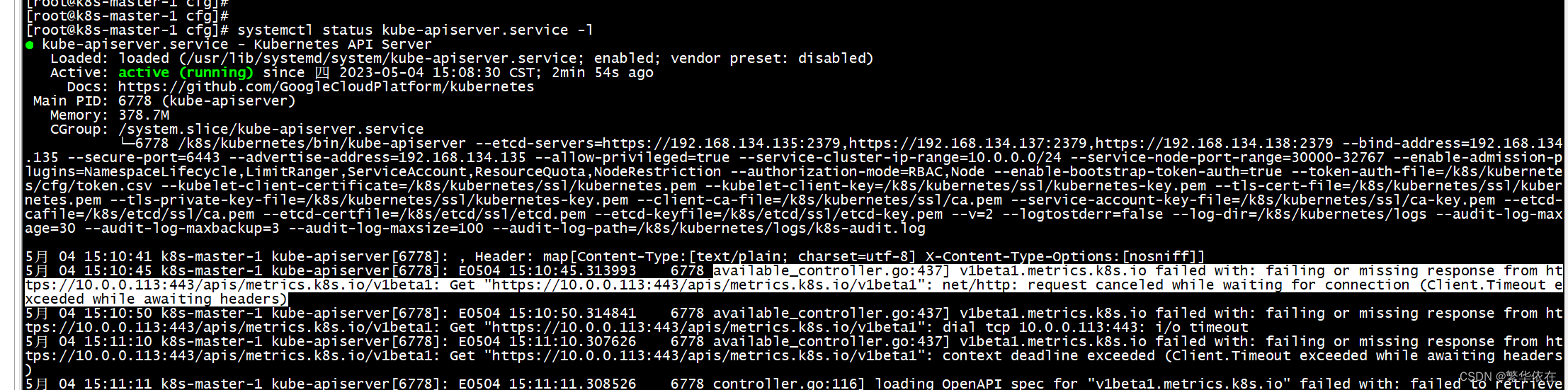
是因为缺少认证的证书文件,创建文件
[root@k8s-master-1 ssl]#
[root@k8s-master-1 ssl]# cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -profile=kubernetes -config=ca-config.json proxy-client-csr.json | cfssljson -bare proxy-client
2023/05/04 14:53:56 [INFO] generate received request
2023/05/04 14:53:56 [INFO] received CSR
2023/05/04 14:53:56 [INFO] generating key: rsa-2048
2023/05/04 14:53:56 [INFO] encoded CSR
2023/05/04 14:53:56 [INFO] signed certificate with serial number 469318432138754596153118826805525884889293204022
2023/05/04 14:53:56 [WARNING] This certificate lacks a "hosts" field. This makes it unsuitable for
websites. For more information see the Baseline Requirements for the Issuance and Management
of Publicly-Trusted Certificates, v.1.1.6, from the CA/Browser Forum (https://cabforum.org);
specifically, section 10.2.3 ("Information Requirements").
[root@k8s-master-1 ssl]#
[root@k8s-master-1 ssl]#
[root@k8s-master-1 ssl]# ls
ca-config.json ca-csr.json ca.pem kube-proxy-csr.json kube-proxy.pem kubernetes-csr.json kubernetes.pem proxy-client-csr.json proxy-client.pem
ca.csr ca-key.pem kube-proxy.csr kube-proxy-key.pem kubernetes.csr kubernetes-key.pem proxy-client.csr proxy-client-key.pem
[root@k8s-master-1 ssl]#
[root@k8s-master-1 ssl]# ?修改kube-apiserver.conf,添加如下内容
--runtime-config=api/all=true \
--requestheader-allowed-names=aggregator \
--requestheader-group-headers=X-Remote-Group \
--requestheader-username-headers=X-Remote-User \
--requestheader-extra-headers-prefix=X-Remote-Extra- \
--requestheader-client-ca-file=/k8s/kubernetes/ssl/ca.pem \
--proxy-client-cert-file=/k8s/kubernetes/ssl/proxy-client.pem \
--proxy-client-key-file=/k8s/kubernetes/ssl/proxy-client-key.pem \
参数说明:
–requestheader-client-ca-file: 客户端 CA 证书。
–requestheader-allowed-names: 允许访问的客户端 common names 列表,通过header中–requestheader-username-headers 参数指定的字段获取。
客户端 common names 的名称需要在 client-ca-file 中进行设置,将其设置为空值时,表示任意客户端都可访问。
–requestheader-username-headers: 参数指定的字段获取。
–requestheader-extra-headers-prefix: 请求头中需要检查的前缀名。
–requestheader-group-headers 请求头中需要检查的组名。
–requestheader-username-headers 请求头中需要检查的用户名。
–proxy-client-cert-file: 在请求期间验证 Aggregator 的客户端 CA 证书。
–proxy-client-key-file: 在请求期间验证 Aggregator 的客户端私钥。
#重启kube-apiserver
[root@k8s-master-1 cfg]# systemctl daemon-reload && systemctl restart kube-apiserver
#验证
[root@k8s-master-1 cfg]# kubectl top node
NAME CPU(cores) CPU% MEMORY(bytes) MEMORY%
k8s-node-1 80m 4% 812Mi 22%
k8s-node-2 81m 4% 775Mi 21%
[root@k8s-master-1 cfg]#
[root@k8s-master-1 cfg]# kubectl top pod
NAME CPU(cores) MEMORY(bytes)
busybox 0m 0Mi
web-96d5df5c8-sw784 0m 1Mi
文章来源:https://blog.csdn.net/weixin_42171272/article/details/135570529
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
最新文章
- Python教程
- 深入理解 MySQL 中的 HAVING 关键字和聚合函数
- Qt之QChar编码(1)
- MyBatis入门基础篇
- 用Python脚本实现FFmpeg批量转换
- 人工智能_机器学习078_聚类算法_概念介绍_聚类升维_降维_各类聚类算法_有监督机器学习_无监督机器学习---人工智能工作笔记0118
- 【踩坑日志】SpringBoot读取nacos配置信息并提取信息中的IP地址(配置属性解析异常+排错记录)
- python怎么访问并登录有用户名密码的web。web使用https协议
- DAY15
- jav读取对应的串口程序的2种方式
- JWT身份验证
- SpringBoot ObjectMapper 返回json 指定字段排序
- C++ 智能指针实现之unique_ptr
- openmmlab大模型实战营01
- MySQl & Mybatis