某mps政务网站jsl加速乐cookie逆向解析
发布时间:2024年01月11日
本文针对的目标网站如下,使用base64解密获得
aHR0cHM6Ly93d3cubXBzLmdvdi5jbi8=
开篇:加速乐其实算是比较好处理的逆向问题了,了解过的朋友都知道,其本身跟瑞数相似,都是设置cookie后才能成功,设置cookie的过程远比瑞数要简单的多,接下来我们看具体问题
首先清除掉浏览器cookie,刷新网站后,会看到三次请求过程
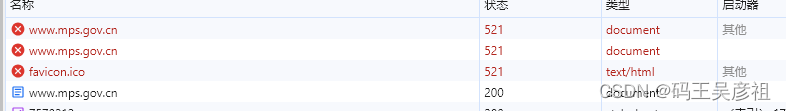
第三次才请求成功,我们先看最后一个请求成功的请求cookie,需要附带两个cookie才能请求成功
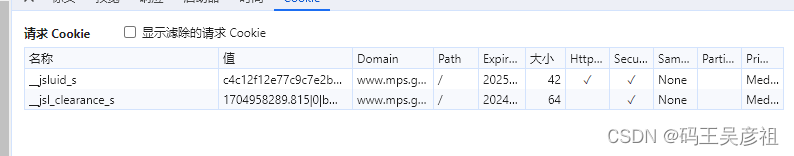
这里的第一个cookie不需要解密,在第一次请求后就会返回响应cookie,那么我们只需要分析第二个cookie的生成即可
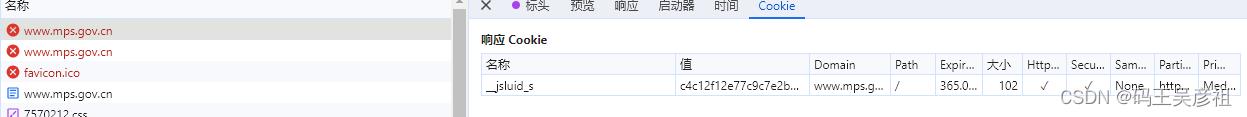
我们逐步分析每一个请求中的响应
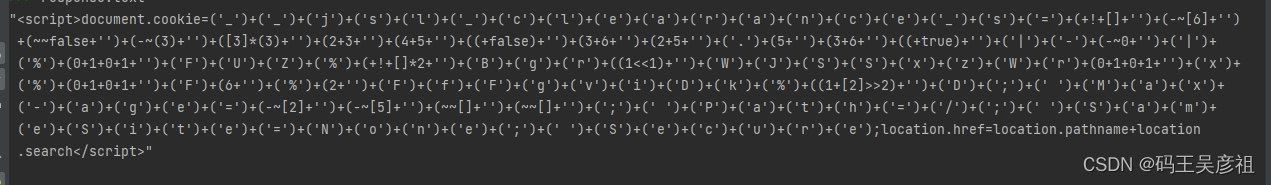
第一个请求中只返回一个script标签,可以看到,里面的js代码已经对docuemnt.cookie进行赋值了,这里的值用的aaencode加密,我们把这段代码直接放到本地来运行,并补齐一下里面缺少的环境,因为这段代码是动态生成的,所以我们也动态的返回cookie
补环境代码:
document = {};
location = {
pathname: '/article/details/132409595',
search: ''
};
{jscode} //替换的代码
function get_cookie() {
return document.cookie;
}
成功拿到cookie后,我们进行第二次请求,我们发现这次返回了一大串js
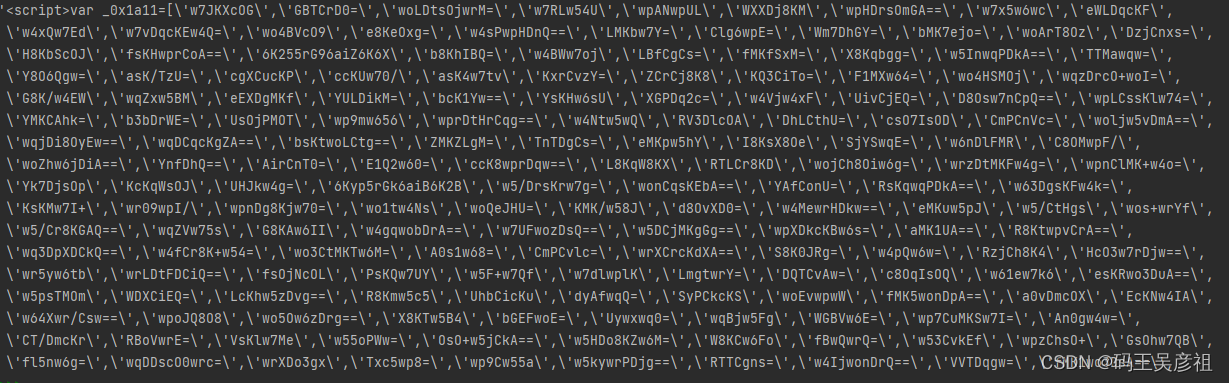
同样使用第一次的方法,将环境补齐,动态替换后,也能达到第二次的cookie,代码如下:
window = global;
navigator = {
userAgent: 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36'
}
document = {}
location = {
"ancestorOrigins": {},
"href": "https://crawler.blog.csdn.net/article/details/132409595",
"origin": "https://crawler.blog.csdn.net",
"protocol": "https:",
"host": "crawler.blog.csdn.net",
"hostname": "crawler.blog.csdn.net",
"port": "",
"pathname": "/article/details/132409595",
"search": "",
"hash": ""
}
{jscode} // 替换的代码
setTimeout(function() {
console.log(document.cookie);
}, 2000);
注意:因为发现第二次的js代码中对cookie赋值,是一个定时器,为了不破坏原代码,我这里选择用命令行执行js代码,通过获取命令行输出的方式来获取cookie
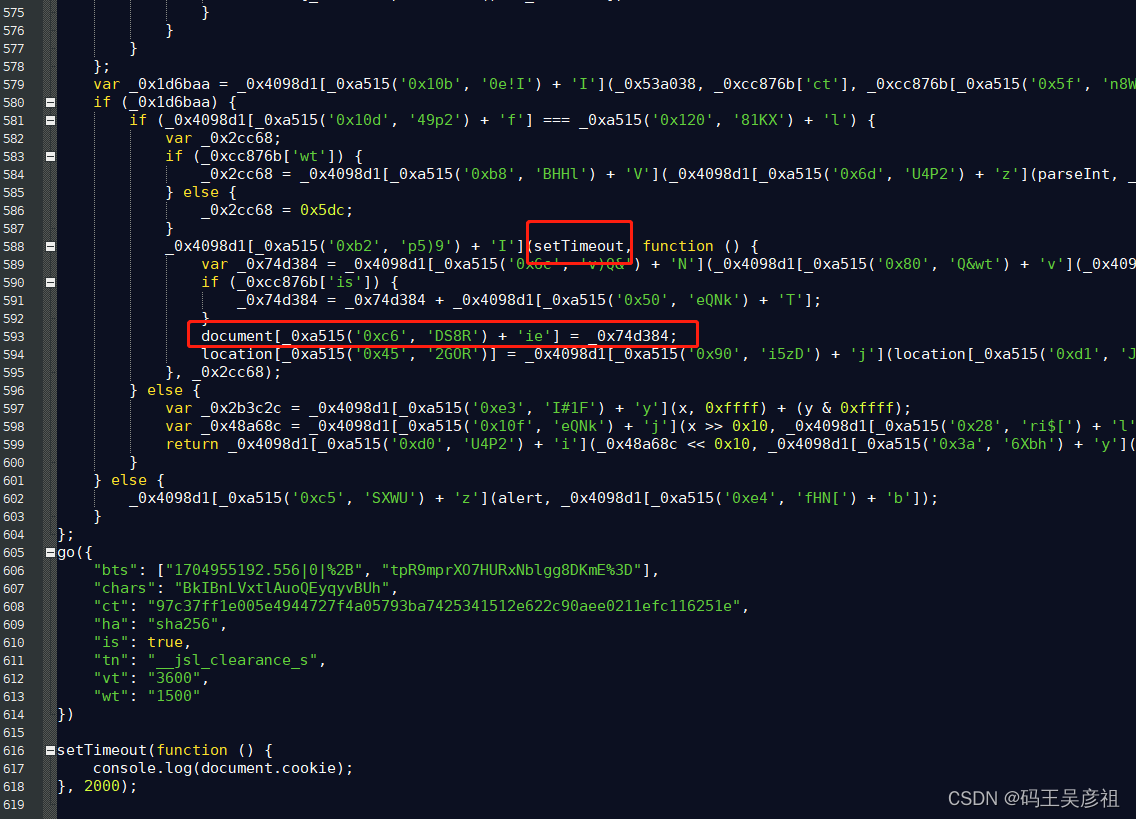
上图为延迟生成的cookie
接着,我们将代码整合一下,使用python
import requests
import execjs
import re
import subprocess
session = requests.session()
jsl1 = open("jsl.js", "r", encoding="utf8").read()
jsl2 = open("jsl2.js", "r", encoding="utf8").read()
headers = {
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7',
'Accept-Language': 'zh-CN,zh;q=0.9',
'Cache-Control': 'no-cache',
'Connection': 'keep-alive',
# 'Cookie': '__jsluid_s=eb68cf3b6f222e7557c5ac0eb5c89f23; __jsl_clearance_s=1704942137.095|0|Q0rq1qKDyBDFY0fr70q51w%2Bhk9M%3D',
'Pragma': 'no-cache',
'Referer': 'https://www.mps.gov.cn/n2254098/n4904352/index_3497341_70.html',
'Sec-Fetch-Dest': 'document',
'Sec-Fetch-Mode': 'navigate',
'Sec-Fetch-Site': 'same-origin',
'Upgrade-Insecure-Requests': '1',
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36',
'sec-ch-ua': '"Not_A Brand";v="8", "Chromium";v="120", "Google Chrome";v="120"',
'sec-ch-ua-mobile': '?0',
'sec-ch-ua-platform': '"Windows"',
}
response = session.get('https://www.mps.gov.cn/n2254098/n4904352/index_3497341_70.html', headers=headers)
print(response)
pattern = re.compile('<script>(.*?)</script>', re.S)
result = pattern.findall(response.text)
if result:
jscode = result[0]
# print(jscode)
jsl1 = jsl1.replace("{jscode}", jscode)
jsl1 = execjs.compile(jsl1)
jslcookie1 = jsl1.call("get_cookie")
jslcookie1 = jslcookie1.split(";")[0]
cookie_key, cookie_value = jslcookie1.split("=")
# print(jslcookie1)
session.cookies.update({cookie_key: cookie_value})
response = session.get('https://www.mps.gov.cn/n2254098/n4904352/index_3497341_70.html', headers=headers)
print(response)
pattern = re.compile('<script>(.*?)</script>', re.S)
result = pattern.findall(response.text)
if result:
jscode = result[0]
# print(jscode)
jsl2 = jsl2.replace("{jscode}", jscode)
with open("jsl2_cookie.js", "w", encoding="utf8") as f:
f.write(jsl2)
# 执行命令并获取输出
result = subprocess.run(['node', 'jsl2_cookie.js'], capture_output=True, text=True)
jslcookie2 = result.stdout.split(";")[0]
cookie_key, cookie_value = jslcookie2.split("=")
session.cookies.update({cookie_key: cookie_value})
# print(jslcookie2)
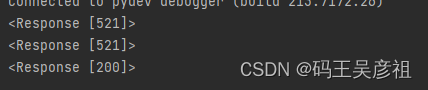
response = session.get('https://www.mps.gov.cn/n2254098/n4904352/index_3497341_70.html', headers=headers)
print(response)
# print(response.text)
成功拿到响应
文章来源:https://blog.csdn.net/qq_36551453/article/details/135531124
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
最新文章
- Python教程
- 深入理解 MySQL 中的 HAVING 关键字和聚合函数
- Qt之QChar编码(1)
- MyBatis入门基础篇
- 用Python脚本实现FFmpeg批量转换
- 14. 接口(适配器设计模式)
- vue中上传组件封装及使用
- chromedriver+Selenium+springboot+Java实现后端截图
- HAProxy搭建Web群集
- 认识loader和plugin
- vivado 使用IP Integrator源
- 聚观早报 | 一加Ace 3海外版;OpenAI发布安全指南
- 利用MATLAB设计一个(2,1,7)卷积码编译码器
- Java小案例-Java实现人事管理系统
- 解决icloud备份灰显的有效方法!