Vault实战(一)-Vault介绍
1?Vault介绍
Vault 是一个基于身份的秘密和加密管理系统。秘密是您想要严格控制访问的任何内容,例如 API 加密密钥、密码和证书。 Vault 提供由身份验证和授权方法控制的加密服务。使用 Vault 的 UI、CLI 或 HTTP API,可以安全地存储和管理、严格控制(限制)和审核对机密和其他敏感数据的访问。
2?为什么需要 Vault
- 执行密码轮换策略很痛苦
- 掌握机密的员工离职后可能泄密或是恶意报复
- 开发者不小心把机密信息随着代码上传到公网的源码仓库造成泄密
- 管理多个系统的机密非常麻烦
- 需要将机密信息安全地加密后存储,但又不想将密钥暴露给应用程序,以防止应用程序被入侵后连带密钥一起泄漏
3?Vault 架构图
Vault 只暴漏了存储后端(Storage Backend) 和 API,其他部分都被保护起来了。Vault 并不信任后端存储,存放的都是密文。

4 安装部署
4.1 二进制部署
4.1.1 下载二进制资源包
$ ls
vault_1.15.4_linux_amd64.zip4.1.2 解压安装
$ unzip vault_1.15.4_linux_amd64.zip
Archive: vault_1.15.4_linux_amd64.zip
inflating: vault
$ mv vault /usr/bin/4.2 yum方式安装
$ yum install -y yum-utils
$ yum-config-manager --add-repo https://rpm.releases.hashicorp.com/RHEL/hashicorp.repo
$ yum -y install vault5 Vault使用?
5.1 启动 Vault
5.1.1 Dev 模式
$ vault server -dev
==> Vault server configuration:
Administrative Namespace:
Api Address: http://127.0.0.1:8200
Cgo: disabled
Cluster Address: https://127.0.0.1:8201
Environment Variables: GODEBUG, HISTCONTROL, HISTSIZE, HOME, HOSTNAME, LANG, LESSOPEN, LOGNAME, LS_COLORS, MAIL, OLDPWD, PATH, PWD, SHELL, SHLVL, SSH_CLIENT, SSH_CONNECTION, SSH_TTY, TERM, USER, XDG_RUNTIME_DIR, XDG_SESSION_ID, _
Go Version: go1.21.4
Listener 1: tcp (addr: "127.0.0.1:8200", cluster address: "127.0.0.1:8201", max_request_duration: "1m30s", max_request_size: "33554432", tls: "disabled")
Log Level:
Mlock: supported: true, enabled: false
Recovery Mode: false
Storage: inmem
Version: Vault v1.15.4, built 2023-12-04T17:45:28Z
Version Sha: 9b61934559ba31150860e618cf18e816cbddc630
==> Vault server started! Log data will stream in below:
2023-12-19T21:48:24.515+0800 [INFO] proxy environment: http_proxy="" https_proxy="" no_proxy=""
2023-12-19T21:48:24.515+0800 [INFO] incrementing seal generation: generation=1
2023-12-19T21:48:24.515+0800 [WARN] no `api_addr` value specified in config or in VAULT_API_ADDR; falling back to detection if possible, but this value should be manually set
2023-12-19T21:48:24.516+0800 [INFO] core: Initializing version history cache for core
2023-12-19T21:48:24.516+0800 [INFO] events: Starting event system
2023-12-19T21:48:24.516+0800 [INFO] core: security barrier not initialized
2023-12-19T21:48:24.516+0800 [INFO] core: security barrier initialized: stored=1 shares=1 threshold=1
2023-12-19T21:48:24.516+0800 [INFO] core: post-unseal setup starting
2023-12-19T21:48:24.525+0800 [INFO] core: loaded wrapping token key
2023-12-19T21:48:24.525+0800 [INFO] core: successfully setup plugin runtime catalog
2023-12-19T21:48:24.525+0800 [INFO] core: successfully setup plugin catalog: plugin-directory=""
2023-12-19T21:48:24.525+0800 [INFO] core: no mounts; adding default mount table
2023-12-19T21:48:24.529+0800 [INFO] core: successfully mounted: type=cubbyhole version="v1.15.4+builtin.vault" path=cubbyhole/ namespace="ID: root. Path: "
2023-12-19T21:48:24.530+0800 [INFO] core: successfully mounted: type=system version="v1.15.4+builtin.vault" path=sys/ namespace="ID: root. Path: "
2023-12-19T21:48:24.530+0800 [INFO] core: successfully mounted: type=identity version="v1.15.4+builtin.vault" path=identity/ namespace="ID: root. Path: "
2023-12-19T21:48:24.532+0800 [INFO] core: successfully mounted: type=token version="v1.15.4+builtin.vault" path=token/ namespace="ID: root. Path: "
2023-12-19T21:48:24.532+0800 [INFO] rollback: Starting the rollback manager with 256 workers
2023-12-19T21:48:24.532+0800 [INFO] rollback: starting rollback manager
2023-12-19T21:48:24.532+0800 [INFO] core: restoring leases
2023-12-19T21:48:24.533+0800 [INFO] expiration: lease restore complete
2023-12-19T21:48:24.533+0800 [INFO] identity: entities restored
2023-12-19T21:48:24.533+0800 [INFO] identity: groups restored
2023-12-19T21:48:24.533+0800 [INFO] core: Recorded vault version: vault version=1.15.4 upgrade time="2023-12-19 13:48:24.533557895 +0000 UTC" build date=2023-12-04T17:45:28Z
2023-12-19T21:48:24.806+0800 [INFO] core: post-unseal setup complete
2023-12-19T21:48:24.807+0800 [INFO] core: root token generated
2023-12-19T21:48:24.807+0800 [INFO] core: pre-seal teardown starting
2023-12-19T21:48:24.807+0800 [INFO] rollback: stopping rollback manager
2023-12-19T21:48:24.807+0800 [INFO] core: pre-seal teardown complete
2023-12-19T21:48:24.807+0800 [INFO] core.cluster-listener.tcp: starting listener: listener_address=127.0.0.1:8201
2023-12-19T21:48:24.807+0800 [INFO] core.cluster-listener: serving cluster requests: cluster_listen_address=127.0.0.1:8201
2023-12-19T21:48:24.807+0800 [INFO] core: post-unseal setup starting
2023-12-19T21:48:24.807+0800 [INFO] core: loaded wrapping token key
2023-12-19T21:48:24.807+0800 [INFO] core: successfully setup plugin runtime catalog
2023-12-19T21:48:24.807+0800 [INFO] core: successfully setup plugin catalog: plugin-directory=""
2023-12-19T21:48:24.808+0800 [INFO] core: successfully mounted: type=system version="v1.15.4+builtin.vault" path=sys/ namespace="ID: root. Path: "
2023-12-19T21:48:24.808+0800 [INFO] core: successfully mounted: type=identity version="v1.15.4+builtin.vault" path=identity/ namespace="ID: root. Path: "
2023-12-19T21:48:24.809+0800 [INFO] core: successfully mounted: type=cubbyhole version="v1.15.4+builtin.vault" path=cubbyhole/ namespace="ID: root. Path: "
2023-12-19T21:48:24.809+0800 [INFO] core: successfully mounted: type=token version="v1.15.4+builtin.vault" path=token/ namespace="ID: root. Path: "
2023-12-19T21:48:24.809+0800 [INFO] rollback: Starting the rollback manager with 256 workers
2023-12-19T21:48:24.810+0800 [INFO] rollback: starting rollback manager
2023-12-19T21:48:24.810+0800 [INFO] core: restoring leases
2023-12-19T21:48:24.810+0800 [INFO] identity: entities restored
2023-12-19T21:48:24.810+0800 [INFO] identity: groups restored
2023-12-19T21:48:24.810+0800 [INFO] expiration: lease restore complete
2023-12-19T21:48:24.810+0800 [INFO] core: post-unseal setup complete
2023-12-19T21:48:24.810+0800 [INFO] core: vault is unsealed
2023-12-19T21:48:24.813+0800 [INFO] core: successful mount: namespace="" path=secret/ type=kv version=""
WARNING! dev mode is enabled! In this mode, Vault runs entirely in-memory
and starts unsealed with a single unseal key. The root token is already
authenticated to the CLI, so you can immediately begin using Vault.
You may need to set the following environment variables:
$ export VAULT_ADDR='http://127.0.0.1:8200'
The unseal key and root token are displayed below in case you want to
seal/unseal the Vault or re-authenticate.
Unseal Key: SbJGQUMajGWHZSNpYCTuxemXerDVUaHTjSWEmpR8Qhg=
Root Token: hvs.vLVLD2gBlgnLAhCrc83pDWSa
Development mode should NOT be used in production installations!
^C==> Vault shutdown triggered
2023-12-19T21:48:35.466+0800 [INFO] core: marked as sealed
2023-12-19T21:48:35.467+0800 [INFO] core: pre-seal teardown starting
2023-12-19T21:48:35.467+0800 [INFO] rollback: stopping rollback manager
2023-12-19T21:48:35.467+0800 [INFO] core: pre-seal teardown complete
2023-12-19T21:48:35.467+0800 [INFO] core: stopping cluster listeners
2023-12-19T21:48:35.467+0800 [INFO] core.cluster-listener: forwarding rpc listeners stopped
2023-12-19T21:48:35.819+0800 [INFO] core.cluster-listener: rpc listeners successfully shut down
2023-12-19T21:48:35.819+0800 [INFO] core: cluster listeners successfully shut down
2023-12-19T21:48:35.819+0800 [INFO] core: vault is sealed命令执行后的返回文本中会有 Unseal Key 和 Root Token 两个参数,这两个参数很关键一定要记录好。?
5.1.2 生产模式
5.1.2.1 配置文件
$ vim /etc/vault/config.hcl
storage "raft" {
path = "/data/vault"
node_id = "node-1"
}
listener "tcp" {
address = "127.0.0.1:8200"
tls_disable = "true"
}
api_addr = "http://127.0.0.1:8200"
cluster_addr = "https://127.0.0.1:8201"
ui = true
$ mkdir -p ./vault/data
5.1.2.2 启动
$ vault server -config=/etc/vault/config.hcl
==> Vault server configuration:
Administrative Namespace:
Api Address: http://127.0.0.1:8200
Cgo: disabled
Cluster Address: https://127.0.0.1:8201
Environment Variables: GODEBUG, HISTCONTROL, HISTSIZE, HOME, HOSTNAME, LANG, LESSOPEN, LOGNAME, LS_COLORS, MAIL, OLDPWD, PATH, PWD, SHELL, SHLVL, SSH_CLIENT, SSH_CONNECTION, SSH_TTY, TERM, USER, XDG_RUNTIME_DIR, XDG_SESSION_ID, _
Go Version: go1.21.4
Listener 1: tcp (addr: "127.0.0.1:8200", cluster address: "127.0.0.1:8201", max_request_duration: "1m30s", max_request_size: "33554432", tls: "disabled")
Log Level:
Mlock: supported: true, enabled: true
Recovery Mode: false
Storage: raft (HA available)
Version: Vault v1.15.4, built 2023-12-04T17:45:28Z
Version Sha: 9b61934559ba31150860e618cf18e816cbddc630
==> Vault server started! Log data will stream in below:
2023-12-19T22:08:53.771+0800 [INFO] proxy environment: http_proxy="" https_proxy="" no_proxy=""
2023-12-19T22:08:53.779+0800 [INFO] incrementing seal generation: generation=1
2023-12-19T22:08:53.856+0800 [INFO] core: Initializing version history cache for core
2023-12-19T22:08:53.856+0800 [INFO] events: Starting event system
2023-12-19T22:09:28.104+0800 [INFO] core: security barrier not initialized
2023-12-19T22:09:28.104+0800 [INFO] core: seal configuration missing, not initialized
2023-12-19T22:09:28.104+0800 [INFO] core: security barrier not initialized
2023-12-19T22:09:28.106+0800 [INFO] storage.raft: creating Raft: config="&raft.Config{ProtocolVersion:3, HeartbeatTimeout:5000000000, ElectionTimeout:5000000000, CommitTimeout:50000000, MaxAppendEntries:64, BatchApplyCh:true, ShutdownOnRemove:true, TrailingLogs:0x2800, SnapshotInterval:120000000000, SnapshotThreshold:0x2000, LeaderLeaseTimeout:2500000000, LocalID:\"node-1\", NotifyCh:(chan<- bool)(0xc00284d260), LogOutput:io.Writer(nil), LogLevel:\"DEBUG\", Logger:(*hclog.interceptLogger)(0xc002760330), NoSnapshotRestoreOnStart:true, skipStartup:false}"
2023-12-19T22:09:28.107+0800 [INFO] storage.raft: initial configuration: index=1 servers="[{Suffrage:Voter ID:node-1 Address:127.0.0.1:8201}]"
2023-12-19T22:09:28.107+0800 [INFO] storage.raft: entering follower state: follower="Node at node-1 [Follower]" leader-address= leader-id=
2023-12-19T22:09:36.223+0800 [WARN] storage.raft: heartbeat timeout reached, starting election: last-leader-addr= last-leader-id=
2023-12-19T22:09:36.223+0800 [INFO] storage.raft: entering candidate state: node="Node at node-1 [Candidate]" term=2
2023-12-19T22:09:36.226+0800 [INFO] storage.raft: election won: term=2 tally=1
2023-12-19T22:09:36.226+0800 [INFO] storage.raft: entering leader state: leader="Node at node-1 [Leader]"
2023-12-19T22:09:36.239+0800 [INFO] core: security barrier initialized: stored=1 shares=5 threshold=3
2023-12-19T22:09:36.256+0800 [INFO] core: post-unseal setup starting
2023-12-19T22:09:36.261+0800 [INFO] core: loaded wrapping token key
2023-12-19T22:09:36.261+0800 [INFO] core: successfully setup plugin runtime catalog
2023-12-19T22:09:36.261+0800 [INFO] core: successfully setup plugin catalog: plugin-directory=""
2023-12-19T22:09:36.261+0800 [INFO] core: no mounts; adding default mount table
2023-12-19T22:09:36.268+0800 [INFO] core: successfully mounted: type=cubbyhole version="v1.15.4+builtin.vault" path=cubbyhole/ namespace="ID: root. Path: "
2023-12-19T22:09:36.268+0800 [INFO] core: successfully mounted: type=system version="v1.15.4+builtin.vault" path=sys/ namespace="ID: root. Path: "
2023-12-19T22:09:36.269+0800 [INFO] core: successfully mounted: type=identity version="v1.15.4+builtin.vault" path=identity/ namespace="ID: root. Path: "
2023-12-19T22:09:36.283+0800 [INFO] core: successfully mounted: type=token version="v1.15.4+builtin.vault" path=token/ namespace="ID: root. Path: "
2023-12-19T22:09:36.284+0800 [INFO] rollback: Starting the rollback manager with 256 workers
2023-12-19T22:09:36.284+0800 [INFO] rollback: starting rollback manager
2023-12-19T22:09:36.285+0800 [INFO] core: restoring leases
2023-12-19T22:09:36.286+0800 [INFO] expiration: lease restore complete
2023-12-19T22:09:36.290+0800 [INFO] identity: entities restored
2023-12-19T22:09:36.290+0800 [INFO] identity: groups restored
2023-12-19T22:09:36.290+0800 [INFO] core: usage gauge collection is disabled
2023-12-19T22:09:36.293+0800 [INFO] core: Recorded vault version: vault version=1.15.4 upgrade time="2023-12-19 14:09:36.290555421 +0000 UTC" build date=2023-12-04T17:45:28Z
2023-12-19T22:09:36.852+0800 [INFO] core: post-unseal setup complete
2023-12-19T22:09:36.859+0800 [INFO] core: root token generated
2023-12-19T22:09:36.866+0800 [INFO] core: pre-seal teardown starting
2023-12-19T22:09:36.866+0800 [INFO] core: stopping raft active node
2023-12-19T22:09:36.866+0800 [INFO] rollback: stopping rollback manager
2023-12-19T22:09:36.866+0800 [INFO] core: pre-seal teardown complete5.2 查看vault服务状态
5.2.1 dev模式?
$ vault status
Key Value
--- -----
Seal Type shamir
Initialized true
Sealed false
Total Shares 1
Threshold 1
Version 1.15.4
Build Date 2023-12-04T17:45:28Z
Storage Type inmem
Cluster Name vault-cluster-5f63f394
Cluster ID 435b526b-a3fa-f015-455b-efdc6391fade
HA Enabled falsedev模式下,sealed为false,HA Enabled为false。
dev模式不可用于生产环境。
5.2.2 生产模式
$ vault status
Key Value
--- -----
Seal Type shamir
Initialized true
Sealed true
Total Shares 5
Threshold 3
Unseal Progress 0/3
Unseal Nonce n/a
Version 1.15.4
Build Date 2023-12-04T17:45:28Z
Storage Type raft
HA Enabled true5.3?server 初始化?
以下均在生产模式下演示。
$ vault operator init
Unseal Key 1: omkhzlj2RQI0uYTqFjLnc49yuKNMcuzB6u0vJ8j0zFd8
Unseal Key 2: VRaHponsWwEV7R2860A/jIBEielq+Nq2b6qBeofjdWxL
Unseal Key 3: 8JjtnzwqYYzC3/RA2iojCfctb0UXS2hYbEfWFL7Vfppc
Unseal Key 4: dFhdpx2ehGdky1YnUsMz2hN4YRtZ7G8DkABD/v4xFFGF
Unseal Key 5: 9iUEPwMERYWPyago35VthjFvyST0IofsVnWMgvbR9CwT
Initial Root Token: hvs.V1KqX0oFDc9Hj1xTy6Iini3I
Vault initialized with 5 key shares and a key threshold of 3. Please securely
distribute the key shares printed above. When the Vault is re-sealed,
restarted, or stopped, you must supply at least 3 of these keys to unseal it
before it can start servicing requests.
Vault does not store the generated root key. Without at least 3 keys to
reconstruct the root key, Vault will remain permanently sealed!
It is possible to generate new unseal keys, provided you have a quorum of
existing unseal keys shares. See "vault operator rekey" for more information.5.4?对 key 解封
初始化后,vault 还不知道如何使用具体的存储,因此处于封锁状态,在上面的 output 内容中有这样一句话:
Vault initialized with 5 key shares and a key threshold of 3.
说明 threshold 为 3,也就是说至少要对 3 个 key 执行解封操作后,server 才可以使用。
$ vault operator unseal omkhzlj2RQI0uYTqFjLnc49yuKNMcuzB6u0vJ8j0zFd8
Key Value
--- -----
Seal Type shamir
Initialized true
Sealed true
Total Shares 5
Threshold 3
Unseal Progress 1/3
Unseal Nonce 31e20274-c828-a988-5221-6b4b5643a04f
Version 1.15.4
Build Date 2023-12-04T17:45:28Z
Storage Type raft
HA Enabled true
$ vault operator unseal VRaHponsWwEV7R2860A/jIBEielq+Nq2b6qBeofjdWxL
Key Value
--- -----
Seal Type shamir
Initialized true
Sealed true
Total Shares 5
Threshold 3
Unseal Progress 2/3
Unseal Nonce 31e20274-c828-a988-5221-6b4b5643a04f
Version 1.15.4
Build Date 2023-12-04T17:45:28Z
Storage Type raft
HA Enabled true
$ vault operator unseal 8JjtnzwqYYzC3/RA2iojCfctb0UXS2hYbEfWFL7Vfppc
Key Value
--- -----
Seal Type shamir
Initialized true
Sealed false
Total Shares 5
Threshold 3
Version 1.15.4
Build Date 2023-12-04T17:45:28Z
Storage Type raft
Cluster Name vault-cluster-c341ffa4
Cluster ID 17b670dc-768d-2c9b-56d1-37fabca8eb16
HA Enabled true
HA Cluster n/a
HA Mode standby
Active Node Address <none>
Raft Committed Index 31
Raft Applied Index 31?每解封一个key,其Unseal Progress就会发生改变。
5.5?创建 engine
和其他数据存储一样,要使用 vault 我们同样需要创建 database,但在 vault 中,数据是按照类似文件系统的 path 来组织的,需要用下面的命令来开启相应的 engine。
$ vault secrets enable -path=secret kv创建了一个 path secret,并且以 kv 类型进行存储。?
5.6 封存vault?
如果觉得系统存在风险,可以使用root token登录vault,执行以下命令将vault重新封印?。
$ vault login -address='http://127.0.0.1:8200' hvs.EjKzWarVoX2yQOQkNTrO3RCd
$ vault operator seal -address='http://127.0.0.1:8200'5.7?重建root token
如果root token泄露或root token不甚丢失,可以使用本节的方法重建root token。重建 Root 令牌有两种办法,分别是一次性密码(one time password)简称OPT,以及 pgp。本次使用OPT方式重建。
$ export VAULT_ADDR=http://127.0.0.1:8200
$ vault operator generate-root -init ##生成OPT密码,这个密码我们需要记住,后面需要用到下面来重新生成root token,会提示我们输入shared key,因为默认是需要三个shared key来生成master key,所以命令需要执行三次。最后一次命令执行时,会生成一个encoded token,我们使用otp可以将它解码为root token。
$ vault operator generate-root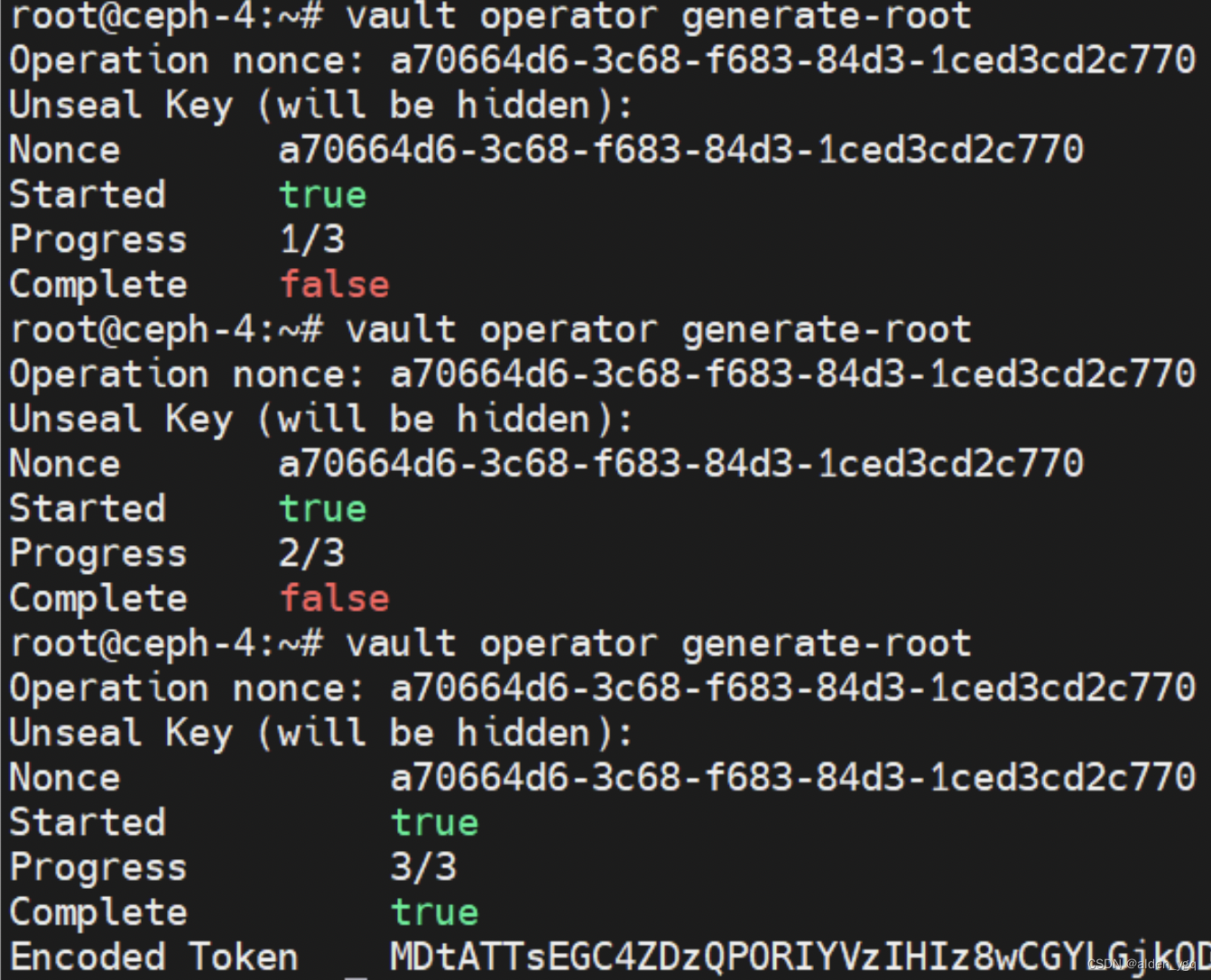
解码root token。
$ vault operator generate-root -decode=MDtATTsEGC4ZDzQPORIYVzIHIz8wCGYLGjkODA -otp=XM3cMjJcIjSzxWo6CFuMGk0CjhbY ##使用这个就可以重新生成root token了
hvs.vnRMPeguAEwaqAVrwcVHpQlU本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
- Python教程
- 深入理解 MySQL 中的 HAVING 关键字和聚合函数
- Qt之QChar编码(1)
- MyBatis入门基础篇
- 用Python脚本实现FFmpeg批量转换
- 数据分析-20-宠物小精灵数据挖掘(包含数据代码)
- 自制c++题目《抽象类与虚函数》
- 云盘后端分析
- 猴子选大王
- java反射
- 【Java】HttpServlet类简单方法和请求显示
- hcie datacom笔试考多少道题目?
- R语言——R函数、选项参数、数学统计函数(六)
- Shell编程--循环结构(for、while、until、shift、continue、break、exit)
- 江苏省发展情况统计报告可视化:探索经济新动向,描绘美好未来