【JS逆向实战案例】【17.某道翻译】请求逆向解析,数据算法解密(详细笔记)
发布时间:2024年01月06日
JS逆向实战案例
某道翻译
1. Part01:逆向请求
抓包
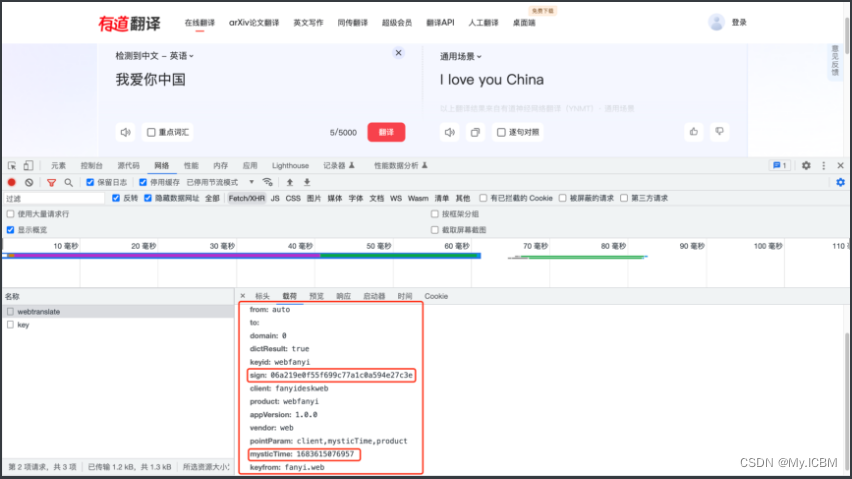
- 表单根据多次请求发现
sign这个字段不断变化,所以是加密了 mysticTime一看就是时间戳,不管他
获取JS的请求入口
获取请求入口:搜索关键字,比如sign(有时候太多不好用),比如请求路径
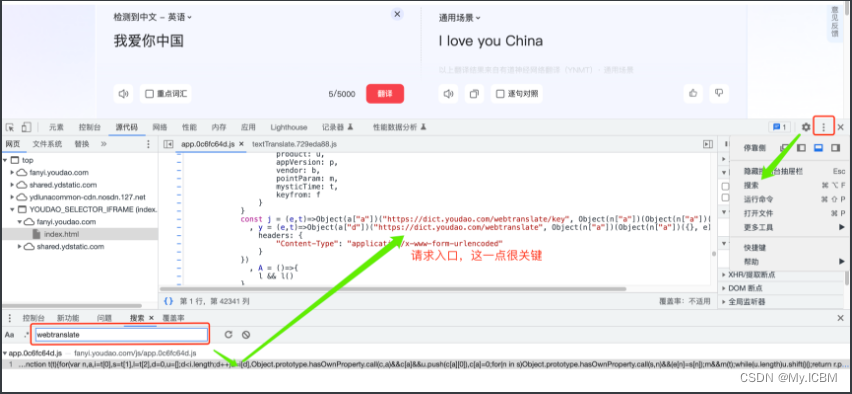
获取构建数据的目标函数
分析请求参数
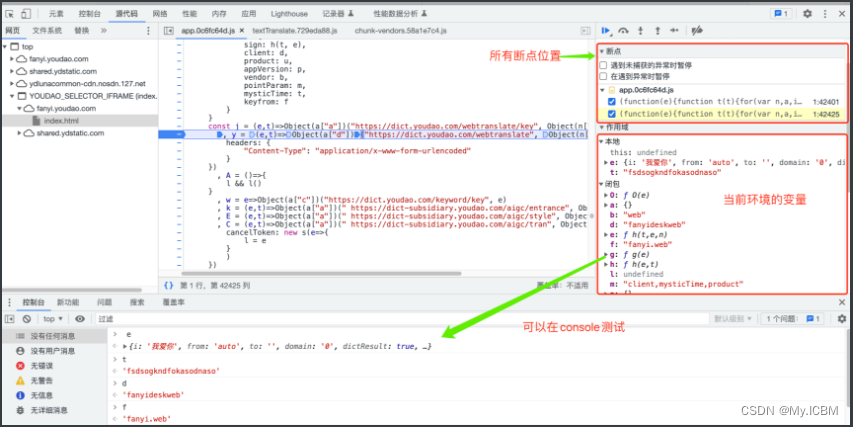
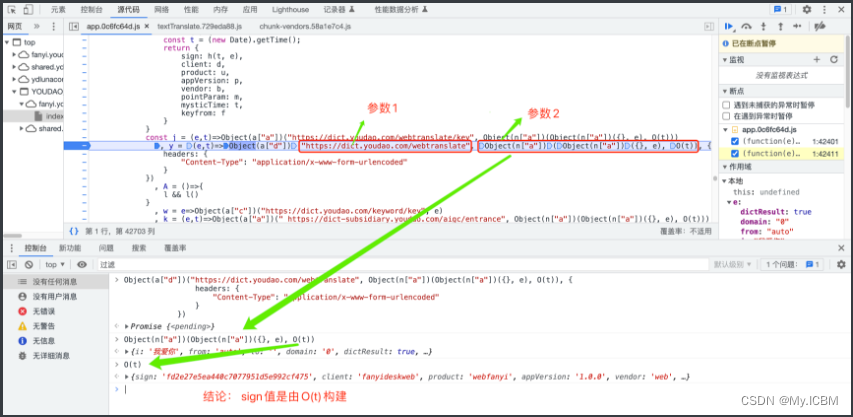
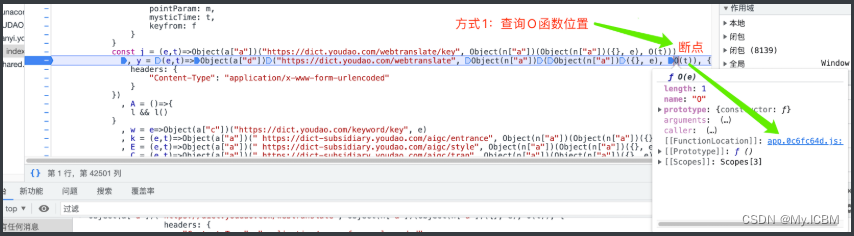
获取目标函数源码位置
方式1
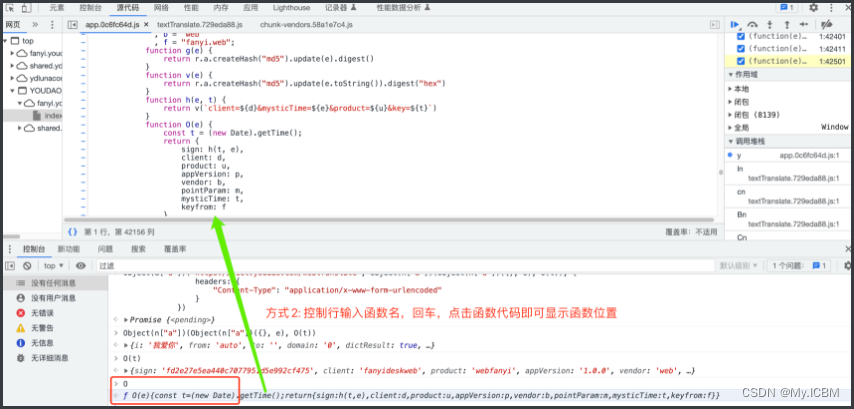
方式2
逆向实现
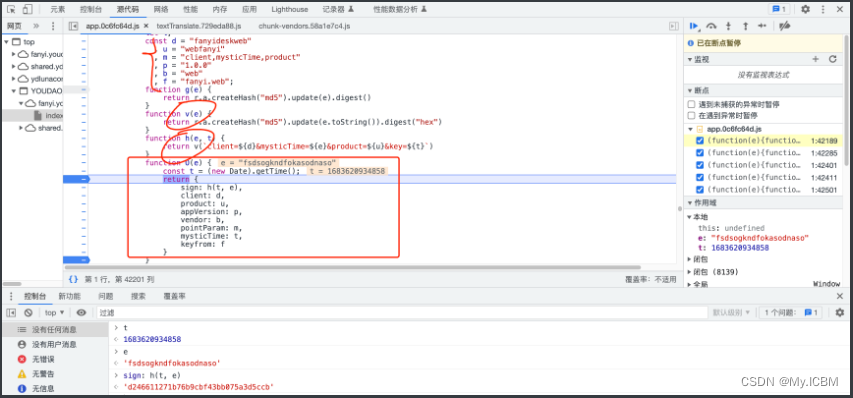
# Python逆向模拟:
import time
import hashlib
def get_md5(val, is_hex=True):
md5 = hashlib.md5()
md5.update(val.encode())
if is_hex:
return md5.hexdigest()
else:
return md5.digest()
# (1)构建逆向动态值
mysticTime = str(int(time.time() * 1000))
u = "fanyideskweb"
e = mysticTime
d = 'webfanyi'
t = 'fsdsogkndfokasodnaso'
s = f'client={u}&mysticTime={mysticTime}&product={d}&key={t}'
sign = get_md5(s)
print("sign:::",sign) # sign::: 4b5fb142ee48267335b0fe01ef57122d
完整请求代码
import requests
import time
import hashlib
import base64
def get_md5(val, is_hex=True):
md5 = hashlib.md5()
md5.update(val.encode())
if is_hex:
return md5.hexdigest()
else:
return md5.digest()
url = 'https://dict.youdao.com/webtranslate'
headers = {
'Accept': 'application/json, text/plain, */*',
'Accept-Encoding': 'gzip, deflate, br',
'Accept-Language': 'zh-CN,zh;q=0.9',
'Connection': 'keep-alive',
'Content-Length': '299',
'Content-Type': 'application/x-www-form-urlencoded',
'Cookie': 'OUTFOX_SEARCH_USER_ID=1795103355@10.112.57.88; OUTFOX_SEARCH_USER_ID_NCOO=929679451.541666',
'Host': 'dict.youdao.com',
'Origin': 'https://fanyi.youdao.com',
'Referer': 'https://fanyi.youdao.com/',
'sec-ch-ua': '";Not A Brand";v="99", "Chromium";v="94"',
'sec-ch-ua-mobile': '?0',
'sec-ch-ua-platform': '"Windows"',
'Sec-Fetch-Dest': 'empty',
'Sec-Fetch-Mode': 'cors',
'Sec-Fetch-Site': 'same-site',
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/94.0.4606.71 Safari/537.36 SE 2.X MetaSr 1.0',
}
# (1)构建逆向动态值
mysticTime = str(int(time.time() * 1000))
u = "fanyideskweb"
e = mysticTime
d = 'webfanyi'
t = 'fsdsogkndfokasodnaso'
s = f'client={u}&mysticTime={mysticTime}&product={d}&key={t}'
sign = get_md5(s)
print("sign:::", sign) # sign::: 4b5fb142ee48267335b0fe01ef57122d
# (2)请求模拟
data = {
'i': '我爱你中国',
'from': 'auto',
'to': '',
'dictResult': 'true',
'keyid': 'webfanyi',
'sign': sign,
'client': 'fanyideskweb',
'product': 'webfanyi',
'appVersion': '1.0.0',
'vendor': 'web',
'pointParam': 'client,mysticTime,product',
'mysticTime': mysticTime,
'keyfrom': 'fanyi.web',
'mid': '1',
'screen': '1',
'model': '1',
'network': 'wifi',
'abtest': '0',
'yduuid': 'abcdefg',
}
response = requests.post(url, data=data, headers=headers)
# print(response.text)
res_base64 = response.text.replace("-", "+").replace("_", "/")
print("结果::", res_base64)
结果为:
Z21kD9ZK1ke6ugku2ccWuwRmpItPkRr5XcmzOgAKD0GcaHTZL9kyNKkN2aYY6yiOv6+AZx1RxXUcmNkJv+tb/+yhZOVG+tmydrRAA1Ve0U3hvAPuYas2Jf1H7p/jPoysB7VaSz/5znWzHxcZ5jAMTrhc0tWvI+B/mePrx47S2HWS50xax2osjVGKwp/K8Zwe21q3cUt2GgC5TBecqfLBcQ==
2. Part02:解密数据
解密入口
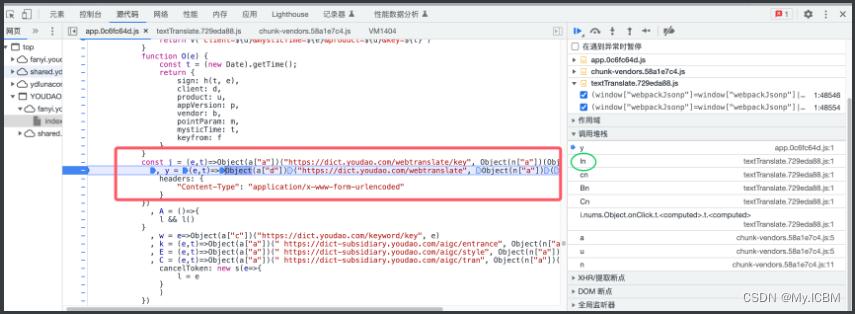
查找解密函数
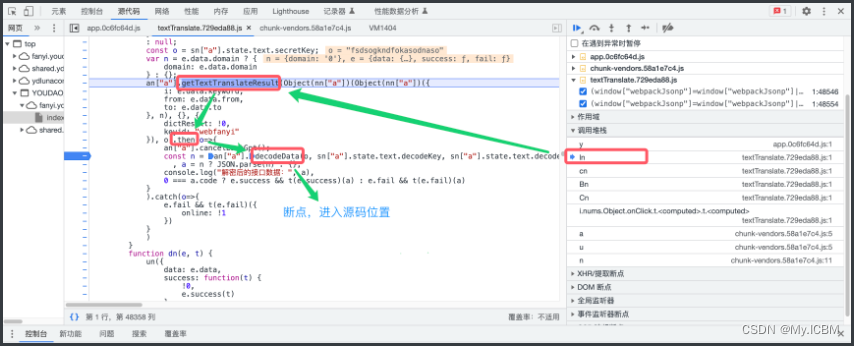
解密实现
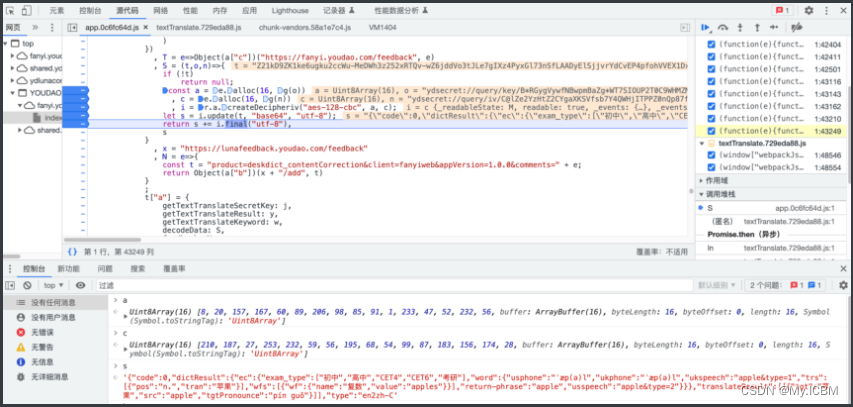
print("结果::", res_base64)
## 对结果进行解密::Z21kD9ZK1ke6ugku2ccWuwRmpItPkRr5XcmzOgAKD0GcaHTZL9kyNKkN2aYY6yiOv6+AZx1RxXUcmNkJv+tb/+yhZOVG+tmydrRAA1Ve0U3hvAPuYas2Jf1H7p/jPoysB7VaSz/5znWzHxcZ5jAMTrhc0tWvI+B/mePrx47S2HWS50xax2osjVGKwp/K8Zwe21q3cUt2GgC5TBecqfLBcQ==
def get_md5(val, is_hex=True):
md5 = hashlib.md5()
md5.update(val.encode())
if is_hex:
return md5.hexdigest()
else:
return md5.digest()
# (3)解码和解密数据
# 解码
res_encrypt = base64.b64decode(res_base64)
print(res_encrypt)
# 解密
o = 'ydsecret://query/key/B*RGygVywfNBwpmBaZg*WT7SIOUP2T0C9WHMZN39j^DAdaZhAnxvGcCY6VYFwnHl'
n = 'ydsecret://query/iv/C@lZe2YzHtZ2CYgaXKSVfsb7Y4QWHjITPPZ0nQp87fBeJ!Iv6v^6fvi2WN@bYpJ4'
# 密钥
key = get_md5(o, False)
# 偏移量
iv = get_md5(n, False)
完整请求解密数据代码
import pprint
import requests
import time
import hashlib
import base64
from Crypto.Cipher import AES
def get_md5(val, is_hex=True):
md5 = hashlib.md5()
md5.update(val.encode())
if is_hex:
return md5.hexdigest()
else:
return md5.digest()
url = 'https://dict.youdao.com/webtranslate'
headers = {
'Accept': 'application/json, text/plain, */*',
'Accept-Encoding': 'gzip, deflate, br',
'Accept-Language': 'zh-CN,zh;q=0.9',
'Connection': 'keep-alive',
'Content-Length': '299',
'Content-Type': 'application/x-www-form-urlencoded',
'Cookie': 'OUTFOX_SEARCH_USER_ID=1795103355@10.112.57.88; OUTFOX_SEARCH_USER_ID_NCOO=929679451.541666',
'Host': 'dict.youdao.com',
'Origin': 'https://fanyi.youdao.com',
'Referer': 'https://fanyi.youdao.com/',
'sec-ch-ua': '";Not A Brand";v="99", "Chromium";v="94"',
'sec-ch-ua-mobile': '?0',
'sec-ch-ua-platform': '"Windows"',
'Sec-Fetch-Dest': 'empty',
'Sec-Fetch-Mode': 'cors',
'Sec-Fetch-Site': 'same-site',
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/94.0.4606.71 Safari/537.36 SE 2.X MetaSr 1.0',
}
# (1)构建逆向动态值
mysticTime = str(int(time.time() * 1000))
u = "fanyideskweb"
e = mysticTime
d = 'webfanyi'
t = 'fsdsogkndfokasodnaso'
s = f'client={u}&mysticTime={mysticTime}&product={d}&key={t}'
sign = get_md5(s)
print("sign:::", sign) # sign::: 4b5fb142ee48267335b0fe01ef57122d
# (2)请求模拟
data = {
'i': '我爱你中国',
'from': 'auto',
'to': '',
'dictResult': 'true',
'keyid': 'webfanyi',
'sign': sign,
'client': 'fanyideskweb',
'product': 'webfanyi',
'appVersion': '1.0.0',
'vendor': 'web',
'pointParam': 'client,mysticTime,product',
'mysticTime': mysticTime,
'keyfrom': 'fanyi.web',
'mid': '1',
'screen': '1',
'model': '1',
'network': 'wifi',
'abtest': '0',
'yduuid': 'abcdefg',
}
response = requests.post(url, data=data, headers=headers)
# print(response.text)
res_base64 = response.text.replace("-", "+").replace("_", "/")
print("结果::", res_base64)
# (3)解码和解密数据
# 解码
res_encrypt = base64.b64decode(res_base64)
print(res_encrypt)
# 解密
o = 'ydsecret://query/key/B*RGygVywfNBwpmBaZg*WT7SIOUP2T0C9WHMZN39j^DAdaZhAnxvGcCY6VYFwnHl'
n = 'ydsecret://query/iv/C@lZe2YzHtZ2CYgaXKSVfsb7Y4QWHjITPPZ0nQp87fBeJ!Iv6v^6fvi2WN@bYpJ4'
# 密钥
key = get_md5(o, False)
# 偏移量
iv = get_md5(n, False)
# 构建 aes 算法对象
aes = AES.new(key, AES.MODE_CBC, iv)
source_data = aes.decrypt(res_encrypt).decode()
pprint.pprint(source_data)
文章来源:https://blog.csdn.net/weixin_43612602/article/details/135407643
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
最新文章
- Python教程
- 深入理解 MySQL 中的 HAVING 关键字和聚合函数
- Qt之QChar编码(1)
- MyBatis入门基础篇
- 用Python脚本实现FFmpeg批量转换
- javaScript设计模式-工厂
- 开放式实验管理系统的设计与实现-计算机毕业设计源码78512
- AI科幻冒险电影《侏罗纪公园2:复活之战》
- OpenStack搭建和部署
- Mediant approximation trick
- 使用C#HSLCommunication实现传感器,仪表,设备等数据的实时监视和分析
- Redis常用命令指令、描述及简单举例
- C++力扣题目37--解数独
- xtu oj 1475 冰墩墩和冰壶
- 网络对讲终端 网络音频终端 网络广播终端SV-7011V使用说明