企业VPN部署项目(学习案例)
发布时间:2024年01月11日
拓扑图:
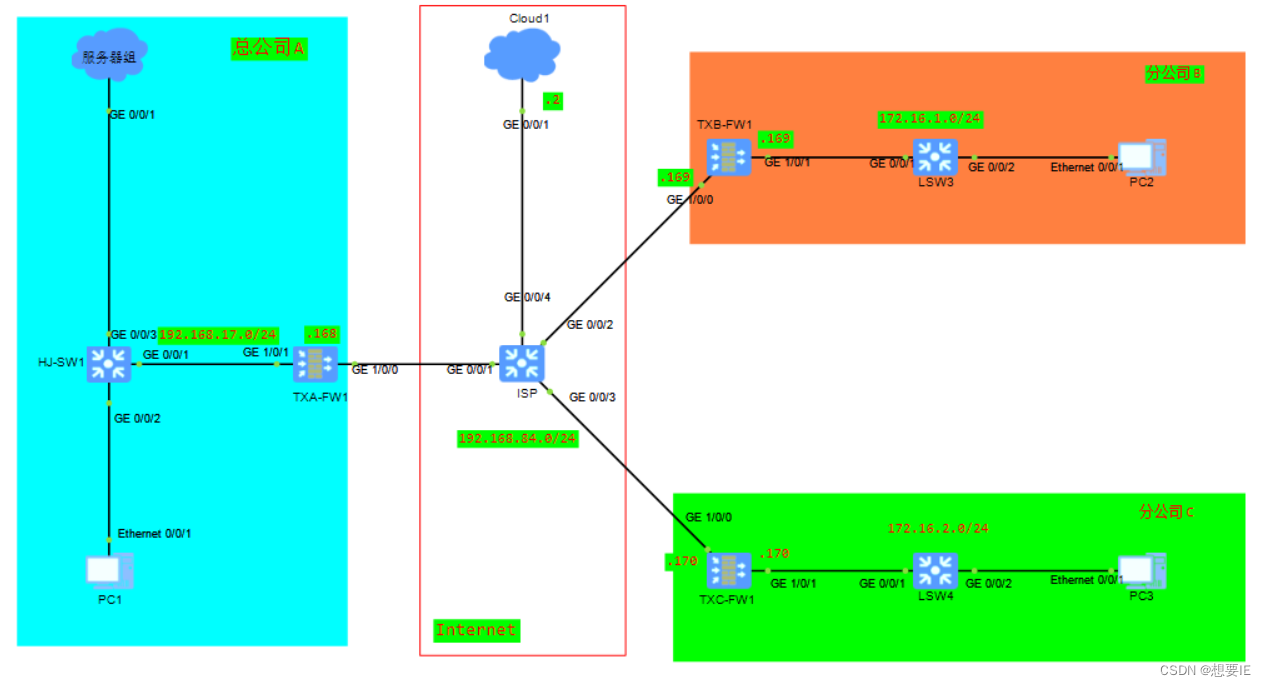
总部A、分公司B和分公司C的内部用户都能访问互联网
- 防火墙基本配置:主机名,接口IP,把接口加入相应的安全区域
- 防火墙配置安全策略,允许内部网段访问互联网(trust – untrust)
- 防火墙配置NAT策略,使用easy IP,允许内部网段访问互联网 (trust – untrust)
- 配置缺省路由
- 客户端配置IP地址和DNS,设置好eNSP的桥接
- 验证上网
-
总部防火墙配置:
sys TXA-FW1 #####配置主机名
int g1/0/0 ####进入到接口模式下
ip add 192.168.84.168 24 ####配置接口IP地址
description WAN ####描述
int g1/0/1
ip add 192.168.17.168 24
description LAN配置安全区域划分
firewall zone untrust
add interface GigabitEthernet1/0/0
firewall zone trust
add interface GigabitEthernet1/0/1
配置安全策略
security-policy
rule name data-ISP
source-zone trust
destination-zone untrust
action permit配置NAT策略
nat-policy
rule name VPN ######配置IPSEC VPN的流量不做NAT转换,为了后续的IPSEC VPN。
source-zone trust
destination-zone untrust
source-address 192.168.17.0 mask 255.255.255.0
destination-address 172.16.1.0 mask 255.255.255.0
destination-address 172.16.2.0 mask 255.255.255.0
action no-nat
rule name data-nat #####配置easy-IP
source-zone trust
destination-zone untrust
action source-nat easy-ip配置缺省路由
ip route-static 0.0.0.0 0.0.0.0 192.168.84.2-
分部B防火墙配置:
sys TXB-FW2
int g1/0/0
ip add 192.168.84.169 24
description WAN
int g1/0/1
ip address 172.16.1.169 24
description LAN
firewall zone untrust
add interface GigabitEthernet1/0/0
firewall zone trust
add interface GigabitEthernet1/0/1
security-policy
rule name data-ISP
source-zone trust
destination-zone untrust
action permit
nat-policy
rule name VPN
source-zone trust
destination-zone untrust
source-address 172.16.1.0 mask 255.255.255.0
destination-address 172.16.2.0 mask 255.255.255.0
destination-address 192.168.17.0 mask 255.255.255.0
action no-nat
rule name data-nat
source-zone trust
destination-zone untrust
action source-nat easy-ip
ip route-static 0.0.0.0 0 192.168.84.2分部C防火墙配置:
sys TXC-FW3
interface GigabitEthernet1/0/0
description WAN
ip address 192.168.84.170 255.255.255.0
interface GigabitEthernet1/0/1
description LAN
ip address 172.16.2.170 255.255.255.0
firewall zone untrust
add interface GigabitEthernet1/0/0
firewall zone trust
add interface GigabitEthernet1/0/1
security-policy
rule name data-ISP
source-zone trust
destination-zone untrust
action permit
nat-policy
rule name VPN
source-zone trust
destination-zone untrust
source-address 172.16.2.0 mask 255.255.255.0
destination-address 172.16.1.0 mask 255.255.255.0
destination-address 192.168.17.0 mask 255.255.255.0
action no-nat
rule name data-nat
source-zone trust
destination-zone untrust
action source-nat easy-ip#############################################################################
验证
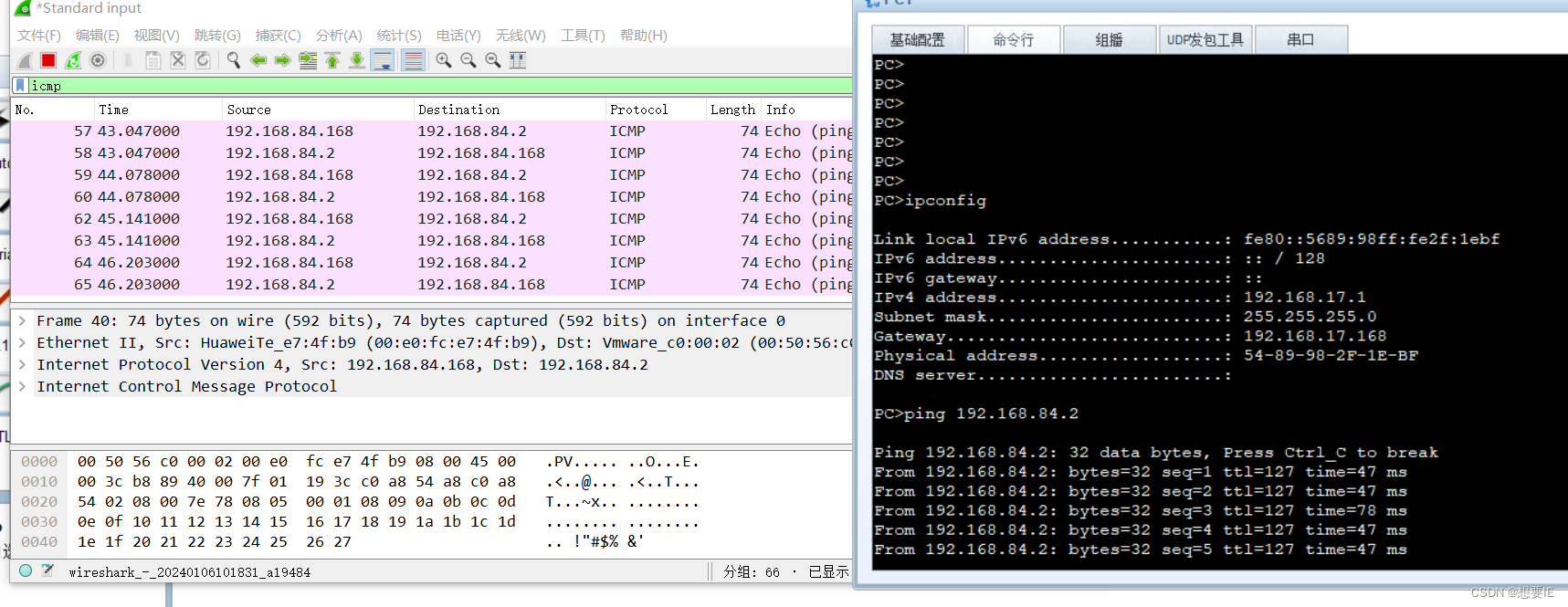
总部? NAT上网:
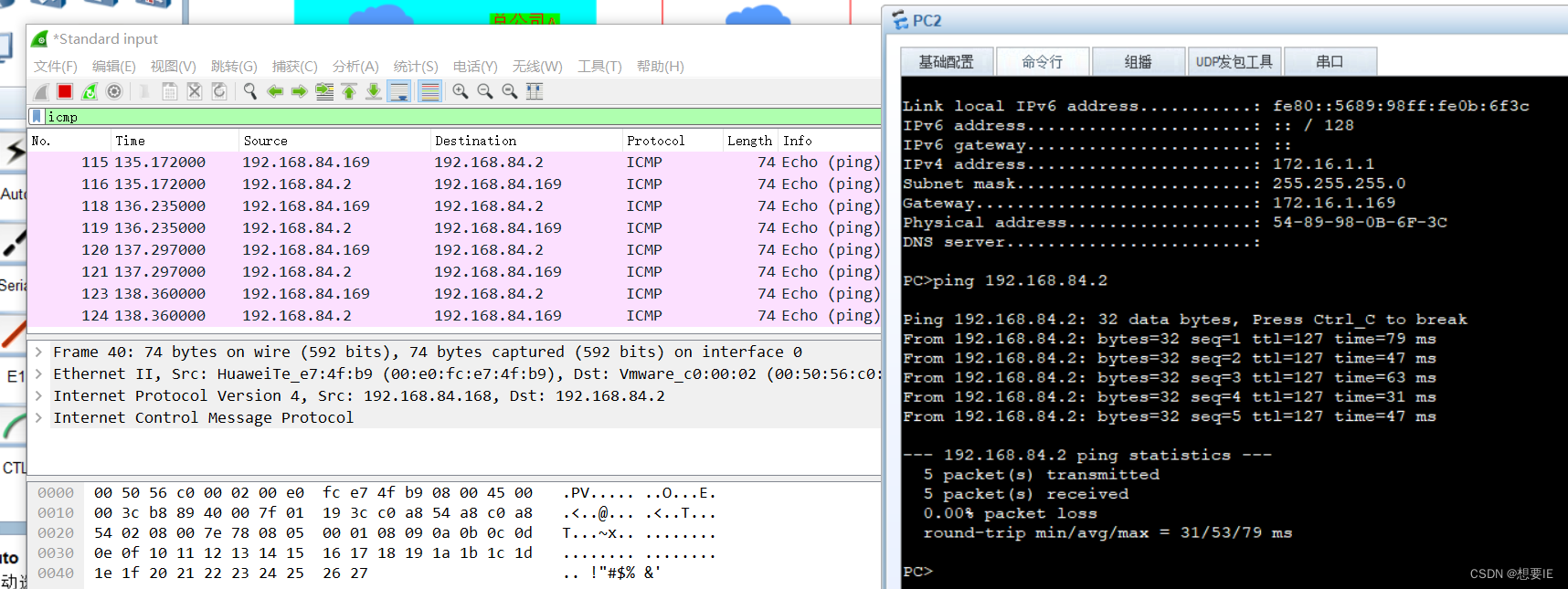
分部B? NAT上网:
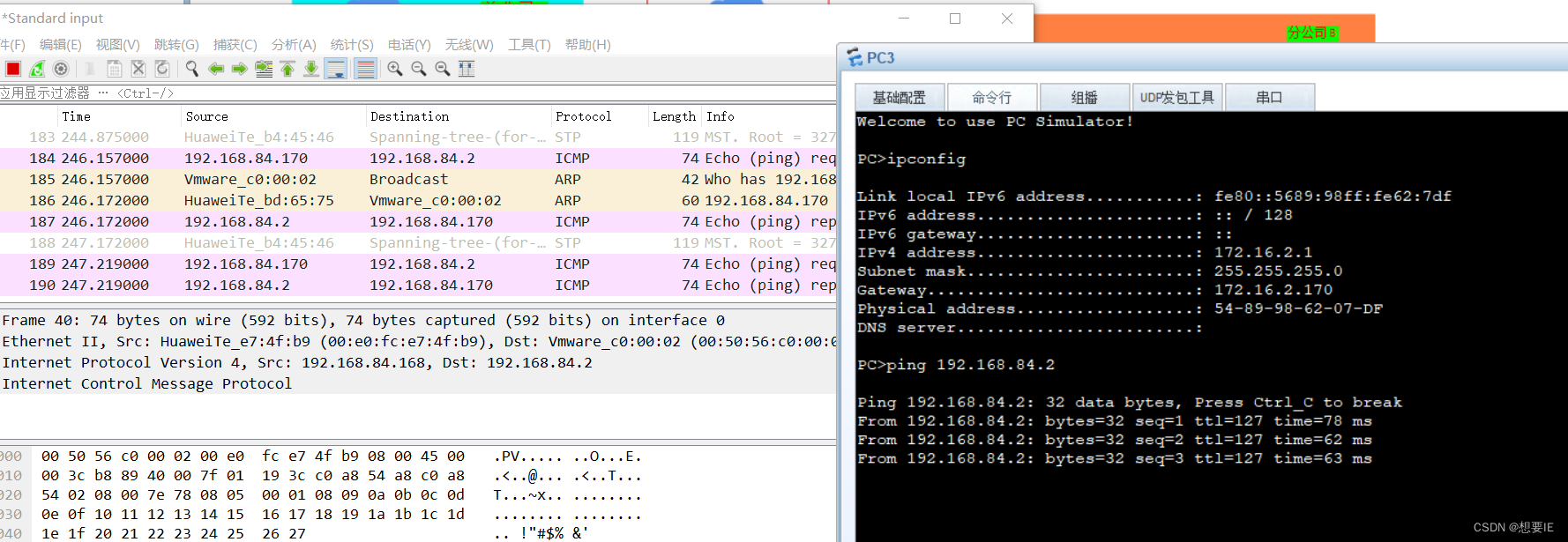
分部C? NAT上网:
分公司B和分公司C都能访问总公司A的网络,同时两个分公司能够互访
- 防火墙配置安全策略:四条策略,1. 总公司—2个分公司(trust --- untrust)?2.2个分公司---总公司(untrust – trust),3. 总公司的外网接口接口---2个分公司的外网接口(local – untrust)4. 2个分公司的外网接口---总公司的外网接口接口(untrust – local)
- 防火墙NAT策略:总公司和分公司之间的流量不做NAT,这条策略要放在最前面。
- 防火墙配置点到多点IPSec VPN:注意两边的相关参数要一致
- 防火墙配置总公司和分公司之间的静态路由
总部防火墙配置:
##向服务组添加IKE、IPSEC协商使用的isakmp报文
ip service-set ike type object 16
service 0 protocol udp source-port 500 destination-port 500
##IKE、IPSEC协商策略
security-policy
rule name data-ISP
source-zone trust
destination-zone untrust
action permit
rule name ike-ipsec
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
service ah
service esp
service ike
action permit
#####VPN之间流量
rule name ipsec-vpn
source-zone untrust
destination-zone trust
source-address 172.16.1.0 mask 255.255.255.0
source-address 172.16.2.0 mask 255.255.255.0
destination-address 192.168.17.0 mask 255.255.255.0
action permit
#####配置IPSEC感兴趣流
acl number 3000
rule 5 permit ip source 192.168.17.0 0.0.0.255 destination 172.16.1.0 0.0.0.255
rule 10 permit ip source 172.16.2.0 0.0.0.255 destination 172.16.1.0 0.0.0.255
注:rule10 分支C到分支B去总部与分支B的隧道
acl number 3001
rule 5 permit ip source 192.168.17.0 0.0.0.255 destination 172.16.2.0 0.0.0.255
rule 10 permit ip source 172.16.1.0 0.0.0.255 destination 172.16.2.0 0.0.0.255
注:rule10 分支B到分支C去总部与分支C的隧道
#########配置IKE安全提议
注:分支共用一个
ike proposal 1
encryption-algorithm aes-256
dh group5
authentication-algorithm sha2-256
authentication-method pre-share
#####配置IKE对等体
分支B:
ike peer 1
version 1
exchange-mode main
pre-shared-key admin@123
ike-proposal 1
remote-address 192.168.84.169
分支C:
ike peer 2
pre-shared-key admin@123
remote-address 192.168.84.170
version 1
exchange-mode main
ike-proposal 1
##########配置IPSEC安全提议
注:分部公用
ipsec proposal 1
transform esp
encapsulation-mode tunnel
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
############配置IPSEC安全策略
分部B:
ipsec policy vpn 100 isakmp
security acl 3000
ike-peer 1
proposal 1
分部C:
ipsec policy vpn 110 isakmp
security acl 3001
ike-peer 2
proposal 1
?
分部B 配置:
ip service-set ike type object 16
service 0 protocol udp source-port 500 destination-port 500
security-policy
rule name ike-ipsec
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
service ah
service esp
service ike
action permit
rule name ipsec-vpn
source-zone untrust
destination-zone trust
source-address 192.168.17.0 mask 255.255.255.0
source-address 172.16.2.0 mask 255.255.255.0
destination-address 172.16.1.0 mask 255.255.255.0
action permit
acl number 3000
rule 5 permit ip source 172.16.1.0 0.0.0.255 destination 192.168.17.0 0.0.0.255
rule 10 permit ip source 172.16.1.0 0.0.0.255 destination 172.16.2.0 0.0.0.255
ike proposal 1
encryption-algorithm aes-256
dh group5
authentication-algorithm sha2-256
authentication-method pre-share
ipsec proposal 1
transform esp
encapsulation-mode tunnel
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
ike peer 1
version 1
exchange-mode main
pre-shared-key admin@123
ike-proposal 1
remote-address 192.168.84.168
ipsec policy vpn 100 isakmp
security acl 3000
ike-peer 1
proposal 1分部C配置:
ip service-set ike type object 16
service 0 protocol udp source-port 500 destination-port 500
security-policy
rule name ike-ipsec
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
service ah
service esp
service ike
action permit
rule name ipsec-vpn
source-zone untrust
destination-zone trust
source-address 192.168.17.0 mask 255.255.255.0
source-address 172.16.1.0 mask 255.255.255.0
destination-address 172.16.2.0 mask 255.255.255.0
action permit
acl number 3000
rule 5 permit ip source 172.16.2.0 0.0.0.255 destination 192.168.17.0 0.0.0.255
rule 10 permit ip source 172.16.2.0 0.0.0.255 destination 172.16.1.0 0.0.0.255
ike proposal 1
encryption-algorithm aes-256
dh group5
authentication-algorithm sha2-256
authentication-method pre-share
ipsec proposal 1
transform esp
encapsulation-mode tunnel
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
ike peer 1
version 1
exchange-mode main
pre-shared-key admin@123
ike-proposal 1
remote-address 192.168.84.168
ipsec policy vpn 100 isakmp
security acl 3000
ike-peer 1
proposal 1###########################################################
这里先不验证,完成 L2tp over IPsec 一起验证
出差在外的用户可以通过SecoClient VPN访问公司总部的网络,使用域账号登录VPN
- 安装域控,创建用户
- 客户端安装Secoclient
- 防火墙配置L2tp over IPsec
- 测试登录
总部防火墙配置:
dhcp enable
###开启L2TP服务
l2tp enable
###配置地址池
ip pool l2tp
section 0 192.168.100.100 192.168.100.150
###创建业务方案绑定地址
aaa
service-scheme l2tp
ip-pool l2tp
###创建认证域
domain l2tp
service-scheme l2tp //关联业务方案
service-type internetaccess l2tp //接入类型:L2TP
internet-access mode password //认证模式
reference user current-domain
###创建用户:VPN 并调用认证域
user-manage user vpn domain l2tp
parent-group /l2tp 属于组/l2tp
bind mode unidirectional
multi-ip online enable
password vpn@123 //密码
interface Virtual-Template1
ppp authentication-mode chap
remote service-scheme l2tp
ip address 192.168.100.254 255.255.255.0
l2tp-group 1
tunnel authentication
tunnel password cipher admin@123
allow l2tp virtual-template 1 remote vpn
firewall zone dmz
add interface Virtual-Template1
security-policy
rule name L2TP-data //隧道访问内网策略
source-zone dmz
destination-zone trust
source-address 192.168.100.0 mask 255.255.255.0
destination-address 192.168.17.0 mask 255.255.255.0
action permit
rule name l2tp //l2tp协商策略
source-zone untrust
destination-zone local
action permit
acl number 3002
rule 5 permit udp source-port eq 1701
ipsec proposal 2
encapsulation-mode transport
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
ike proposal 2
encryption-algorithm aes-256
dh group5
authentication-algorithm sha2-256
authentication-method pre-share
ike peer 3
exchange-mode auto
pre-shared-key Huawei@123
ike-proposal 2
ipsec policy-template l2tp 90
security acl 3002
ike-peer 3
proposal 2总###部接口应用IPSEC
ipsec policy vpn 120 isakmp template l2tp
interface GigabitEthernet1/0/0
ipsec policy vpn
配置路由
ip route-static 172.16.1.0 255.255.255.0 192.168.84.169
ip route-static 172.16.2.0 255.255.255.0 192.168.84.170
####分部B 接口应用IPSEC
interface GigabitEthernet1/0/0
ipsec policy vpn
配置路由
ip route-static 172.16.2.0 255.255.255.0 192.168.84.170
ip route-static 192.168.17.0 255.255.255.0 192.168.84.168
####分部C 接口应用IPSEC
interface GigabitEthernet1/0/0
ipsec policy vpn
配置路由
ip route-static 172.16.1.0 255.255.255.0 192.168.84.169
ip route-static 192.168.17.0 255.255.255.0 192.168.84.168验证
验证出差人员 L2TP over IPSEC?
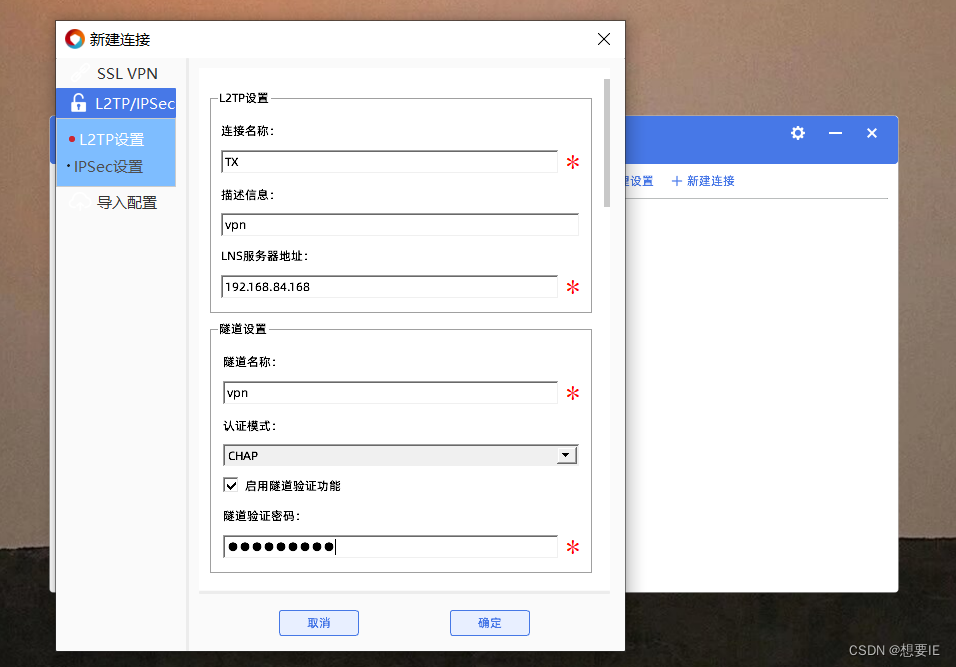
user:vpn? ? password:admin@123? ?
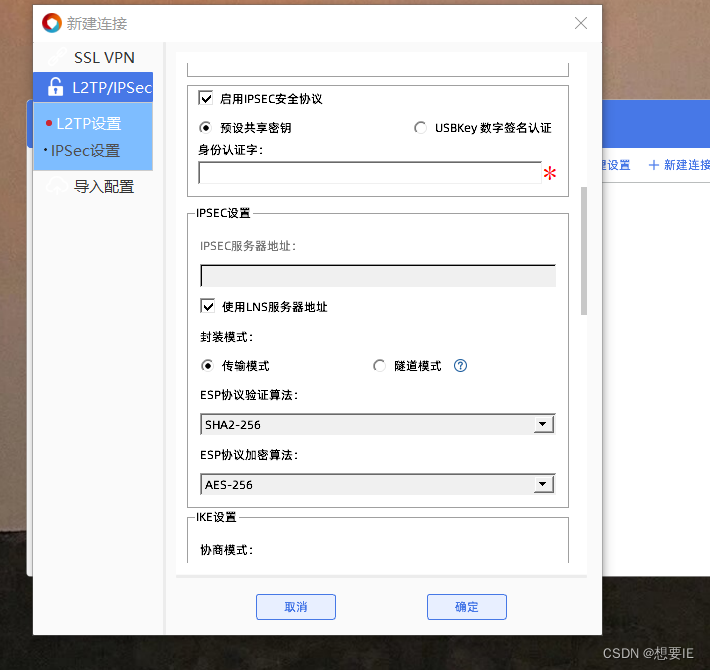
Huawei@123
?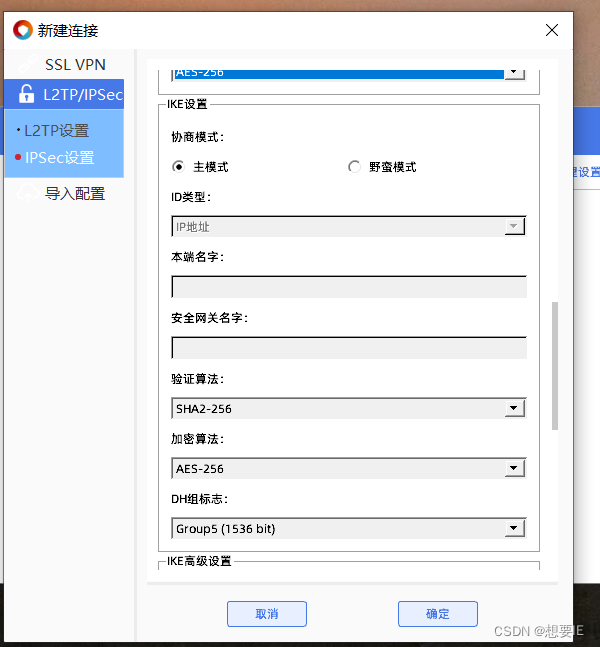
按照自己的设置选择
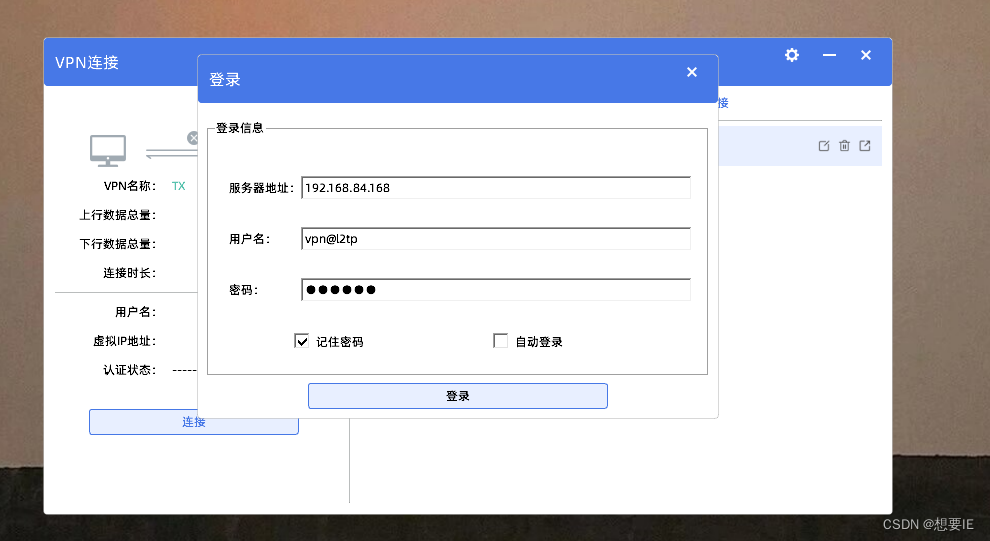
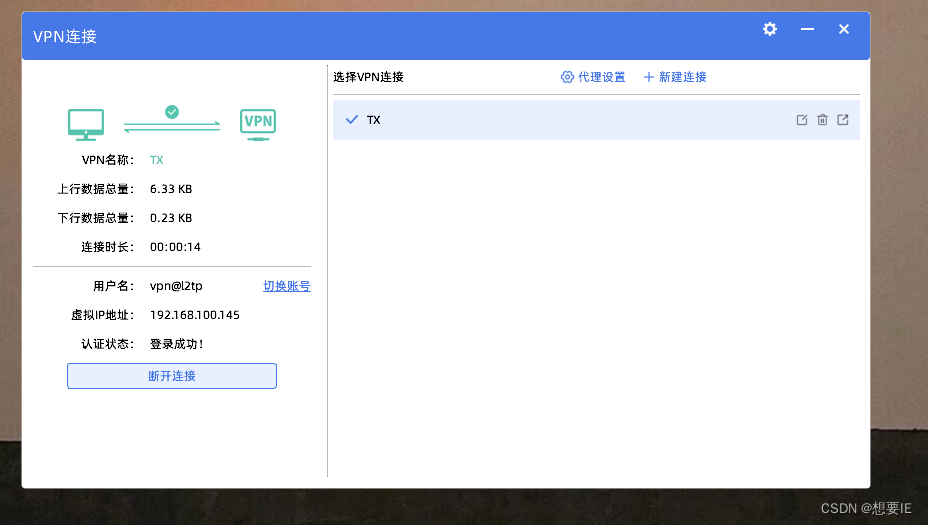
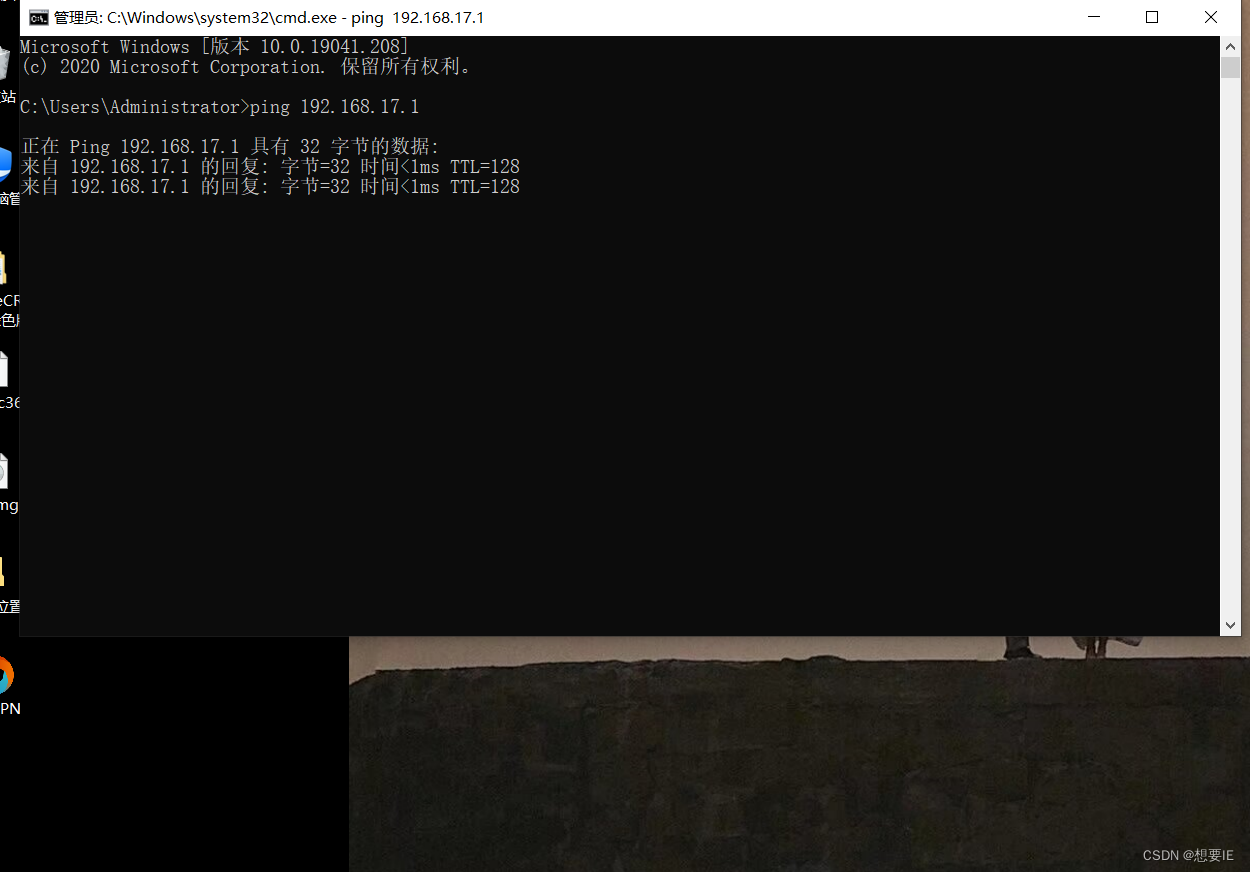
成功了
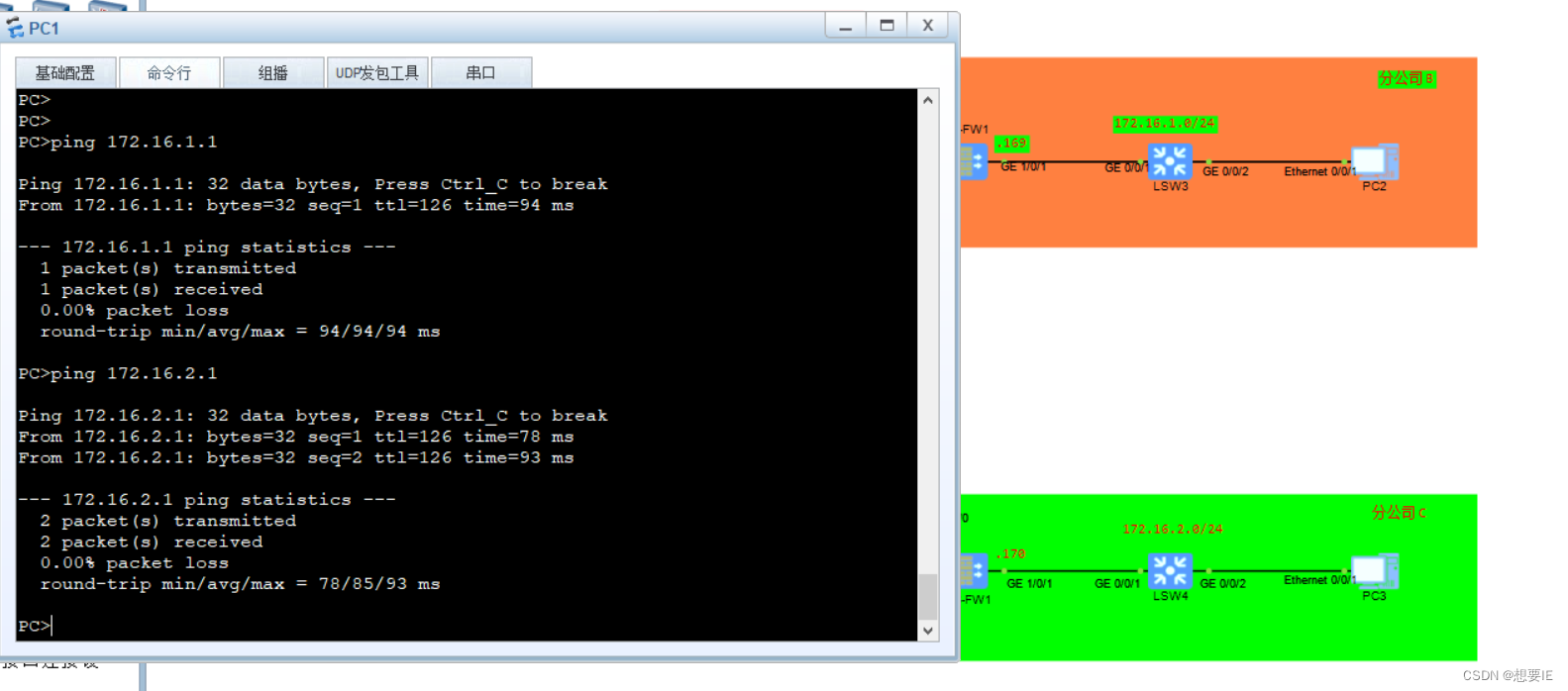
验证公司之间的 IPSEC VPN?
总部分部 之间通信:
分部之间通信:
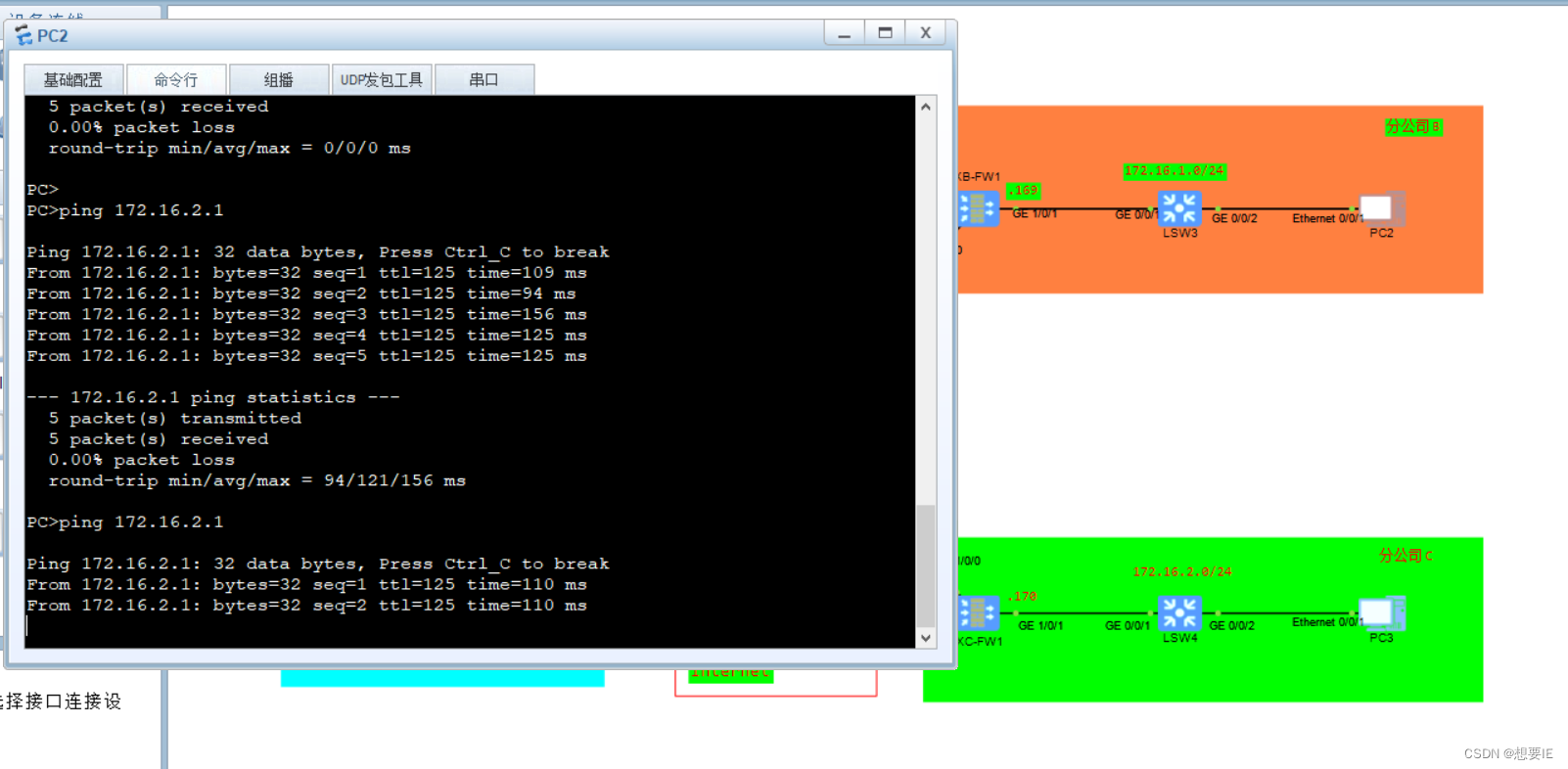
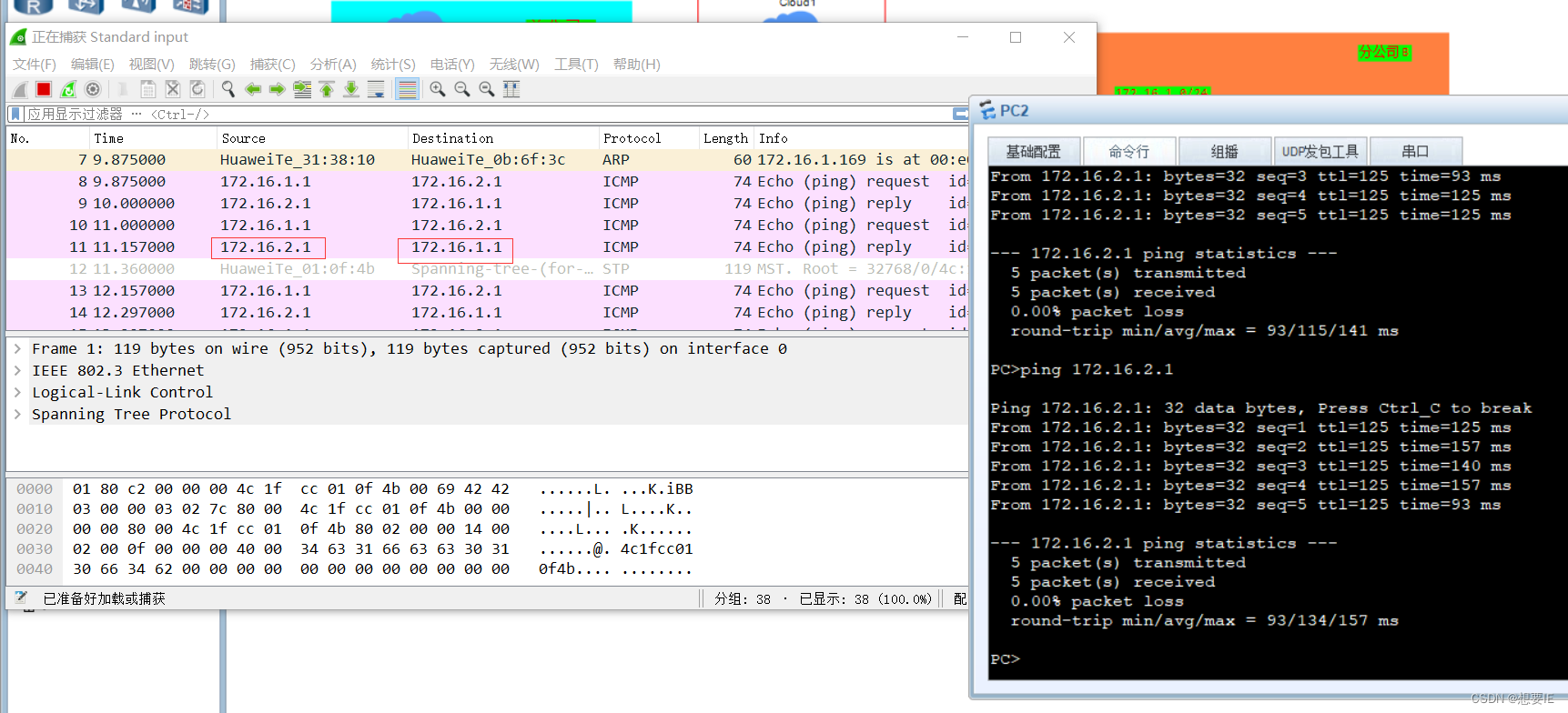
实验到此结束
查看命令:
display ?l2tp tunnel?
dis ike sa?display ipsec sa brief?
文章来源:https://blog.csdn.net/m0_72488185/article/details/135422001
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
最新文章
- Python教程
- 深入理解 MySQL 中的 HAVING 关键字和聚合函数
- Qt之QChar编码(1)
- MyBatis入门基础篇
- 用Python脚本实现FFmpeg批量转换
- AI无忧秘书智脑:重塑创意绘制的未来
- “一键批量翻译与重命名,轻松将西班牙文件名转换为中文名“
- 基于springboot垃圾分类网站
- Spring 对请求参数的优雅处方式(重写序列化方法)
- blender插件开发
- “程序员面试之道:成为求职战场上的不可忽视的力量“
- Prometheus查询语法总结
- 【虚拟仪器Labview】习题T1-详解
- 防火墙 设置 出站规则
- JOSEF约瑟 分合闸电源监视继电器 HJZZ-91 DC220V 柜内导轨安装