Terraform-云上基础设施自动化工具
https://developer.hashicorp.com/terraform/install?product_intent=terraform
根据操作系统进行对应的安装操作。
这里我选择Windows安装,配置环境变量Path,将路径添加进入
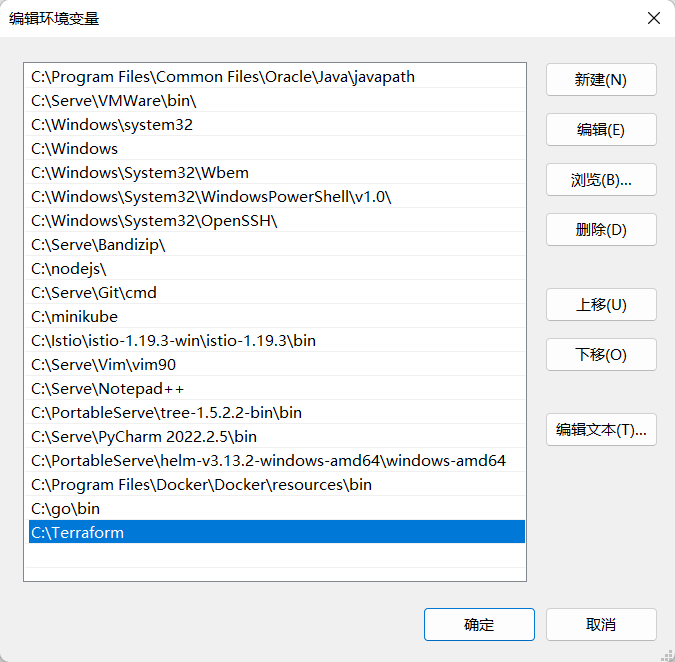
输入命令进行验证
$ terraform -v
Terraform v1.6.6
on windows_amd64
编辑器推荐使用VSCode,推荐使用Terraform插件
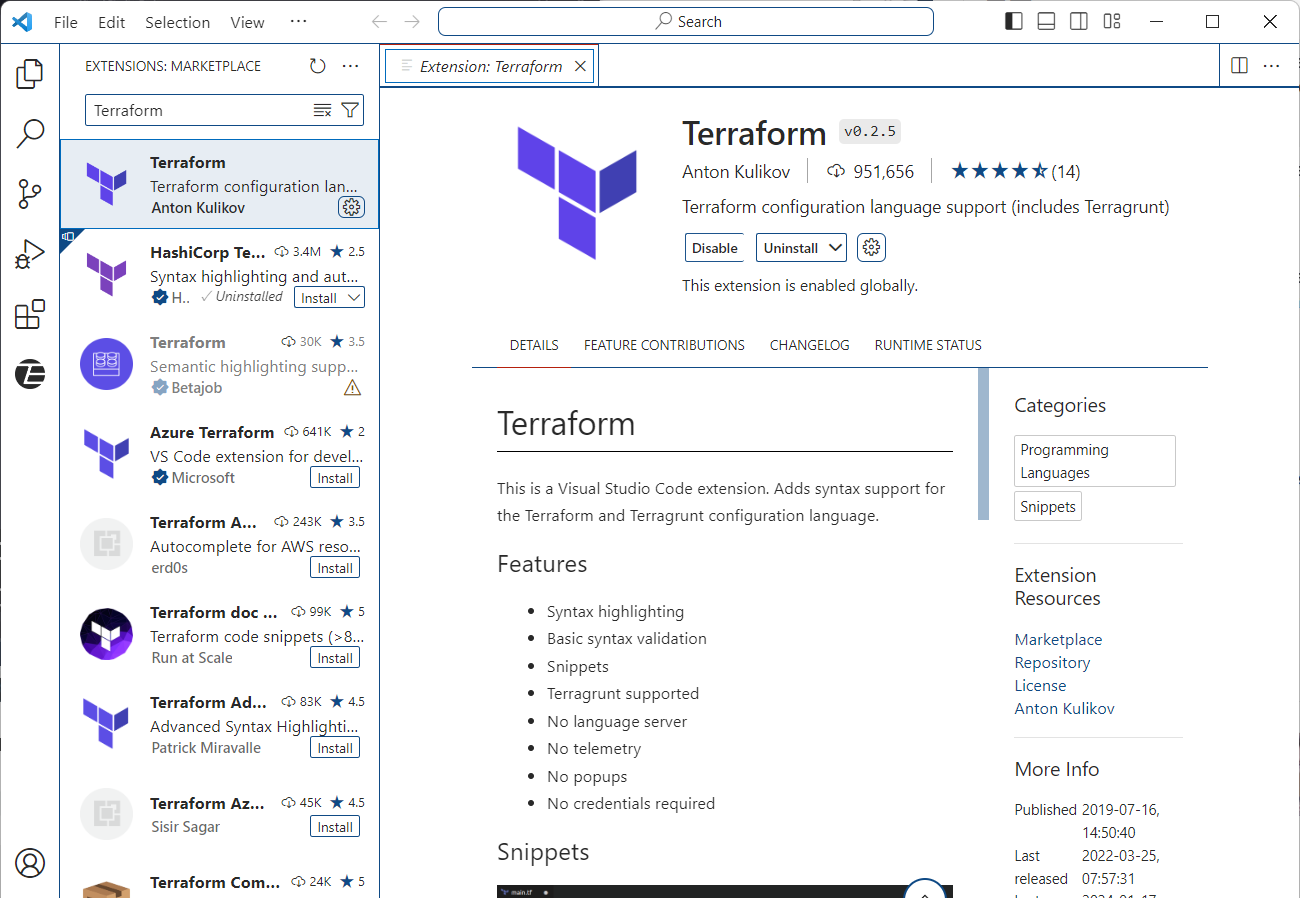
新建文件 main.tf
https://developer.hashicorp.com/terraform/language/providers
https://registry.terraform.io/browse/providers
- 定义一个提供者(允许我们与一组特定的API进行对话)
.tf文件格式:
provider "提供商" {
region = "资源地区"
access_key = "生成的access_key"
secret_key = "生成的secret_key"
}
resource "<提供商>_<资源类型>" "名称" {
# 你所定义的资源信息
key1 = "val1"
key2 = "val2"
...
}
这里以AWS为例
- 身份验证设置
创建访问密钥
创建资源
下面演示创建一个EC2实例通过Terraform
main.tf
provider "aws" {
region = "us-east-1"
access_key = "AKIA6BOCDBYWM4JBXHNU"
secret_key = "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"
}
resource "aws_instance" "my_server" {
ami = "ami-0c7217cdde317cfec"
instance_type = "t2.micro"
}
初始时并没有实例
VSCode中在项目中输入命令
terraform init
Initializing the backend...
Initializing provider plugins...
- Finding latest version of hashicorp/aws...
- Installing hashicorp/aws v5.32.1...
- Installed hashicorp/aws v5.32.1 (signed by HashiCorp)
Terraform has created a lock file .terraform.lock.hcl to record the provider
selections it made above. Include this file in your version control repository
so that Terraform can guarantee to make the same selections by default when
you run "terraform init" in the future.
Terraform has been successfully initialized!
You may now begin working with Terraform. Try running "terraform plan" to see
any changes that are required for your infrastructure. All Terraform commands
should now work.
If you ever set or change modules or backend configuration for Terraform,
rerun this command to reinitialize your working directory. If you forget, other
commands will detect it and remind you to do so if necessary.
接下来你的项目中就会多出几个文件
PS C:\Code\Terraform> dir
目录: C:\Code\Terraform
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 2024/1/17 20:22 .terraform
-a---- 2024/1/17 20:22 1377 .terraform.lock.hcl
-a---- 2024/1/17 20:19 268 main.tf
运行terraform plan去查看.tf文件产生的更改
PS C:\Code\Terraform> terraform plan
Terraform used the selected providers to generate the following execution plan. Resource
actions are indicated with the following symbols:
+ create
Terraform will perform the following actions:
# aws_instance.my_server will be created
+ resource "aws_instance" "my_server" {
+ ami = "ami-0c7217cdde317cfec"
+ arn = (known after apply)
+ associate_public_ip_address = (known after apply)
+ availability_zone = (known after apply)
+ cpu_core_count = (known after apply)
+ cpu_threads_per_core = (known after apply)
+ disable_api_stop = (known after apply)
+ disable_api_termination = (known after apply)
+ ebs_optimized = (known after apply)
+ get_password_data = false
+ host_id = (known after apply)
+ host_resource_group_arn = (known after apply)
+ iam_instance_profile = (known after apply)
+ id = (known after apply)
+ instance_initiated_shutdown_behavior = (known after apply)
+ instance_lifecycle = (known after apply)
+ instance_state = (known after apply)
+ instance_type = "t2.micro"
+ ipv6_address_count = (known after apply)
+ ipv6_addresses = (known after apply)
+ key_name = (known after apply)
+ monitoring = (known after apply)
+ outpost_arn = (known after apply)
+ password_data = (known after apply)
+ placement_group = (known after apply)
+ placement_partition_number = (known after apply)
+ primary_network_interface_id = (known after apply)
+ private_dns = (known after apply)
+ private_ip = (known after apply)
+ public_dns = (known after apply)
+ public_ip = (known after apply)
+ secondary_private_ips = (known after apply)
+ security_groups = (known after apply)
+ source_dest_check = true
+ spot_instance_request_id = (known after apply)
+ subnet_id = (known after apply)
+ tags_all = (known after apply)
+ tenancy = (known after apply)
+ user_data = (known after apply)
+ user_data_base64 = (known after apply)
+ user_data_replace_on_change = false
+ vpc_security_group_ids = (known after apply)
}
Plan: 1 to add, 0 to change, 0 to destroy.
───────────────────────────────────────────────────────────────────────────────────────────────
Note: You didn't use the -out option to save this plan, so Terraform can't guarantee to take
exactly these actions if you run "terraform apply" now.
运行terraform apply构建你的云资源
C:\Code\Terraform> terraform apply
Terraform used the selected providers to generate the following execution plan. Resource
actions are indicated with the following symbols:
+ create
Terraform will perform the following actions:
# aws_instance.my_server will be created
+ resource "aws_instance" "my_server" {
+ ami = "ami-0c7217cdde317cfec"
+ arn = (known after apply)
+ associate_public_ip_address = (known after apply)
+ availability_zone = (known after apply)
+ cpu_core_count = (known after apply)
+ cpu_threads_per_core = (known after apply)
+ disable_api_stop = (known after apply)
+ disable_api_termination = (known after apply)
+ ebs_optimized = (known after apply)
+ get_password_data = false
+ host_id = (known after apply)
+ host_resource_group_arn = (known after apply)
+ iam_instance_profile = (known after apply)
+ id = (known after apply)
+ instance_initiated_shutdown_behavior = (known after apply)
+ instance_lifecycle = (known after apply)
+ instance_state = (known after apply)
+ instance_type = "t2.micro"
+ ipv6_address_count = (known after apply)
+ ipv6_addresses = (known after apply)
+ key_name = (known after apply)
+ monitoring = (known after apply)
+ outpost_arn = (known after apply)
+ password_data = (known after apply)
+ placement_group = (known after apply)
+ placement_partition_number = (known after apply)
+ primary_network_interface_id = (known after apply)
+ private_dns = (known after apply)
+ private_ip = (known after apply)
+ public_dns = (known after apply)
+ public_ip = (known after apply)
+ secondary_private_ips = (known after apply)
+ security_groups = (known after apply)
+ source_dest_check = true
+ spot_instance_request_id = (known after apply)
+ subnet_id = (known after apply)
+ tags_all = (known after apply)
+ tenancy = (known after apply)
+ user_data = (known after apply)
+ user_data_base64 = (known after apply)
+ user_data_replace_on_change = false
+ vpc_security_group_ids = (known after apply)
}
Plan: 1 to add, 0 to change, 0 to destroy.
Do you want to perform these actions?
Terraform will perform the actions described above.
Only 'yes' will be accepted to approve.
Enter a value: yes
aws_instance.my_server: Creating...
aws_instance.my_server: Still creating... [10s elapsed]
aws_instance.my_server: Still creating... [20s elapsed]
aws_instance.my_server: Still creating... [30s elapsed]
aws_instance.my_server: Creation complete after 37s [id=i-02ddc2905564010aa]
Apply complete! Resources: 1 added, 0 changed, 0 destroyed.
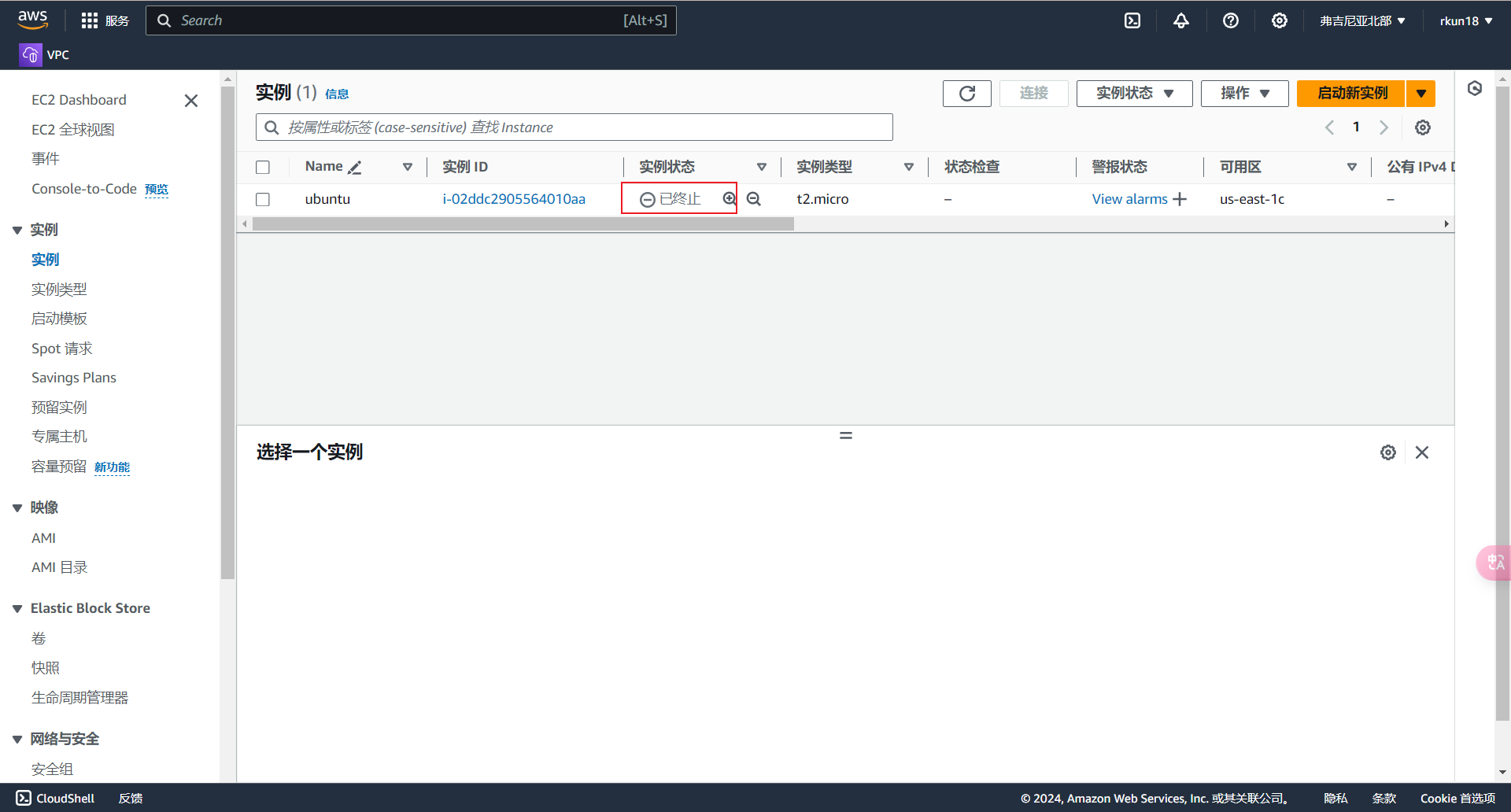
现在,我们通过Terraform创建了一个EC2实例,创建好的实例相关参数与我们定义的参数相同
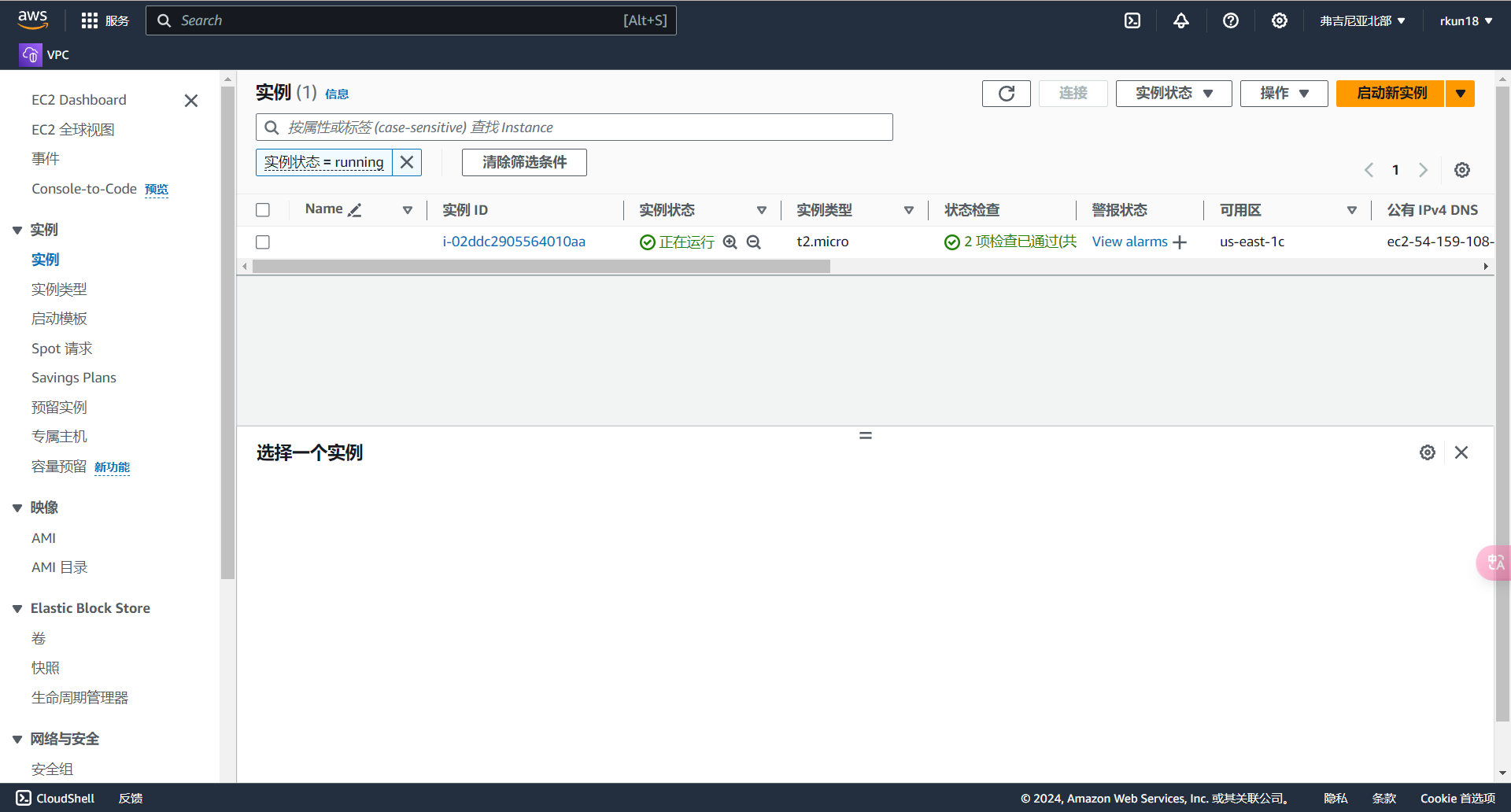
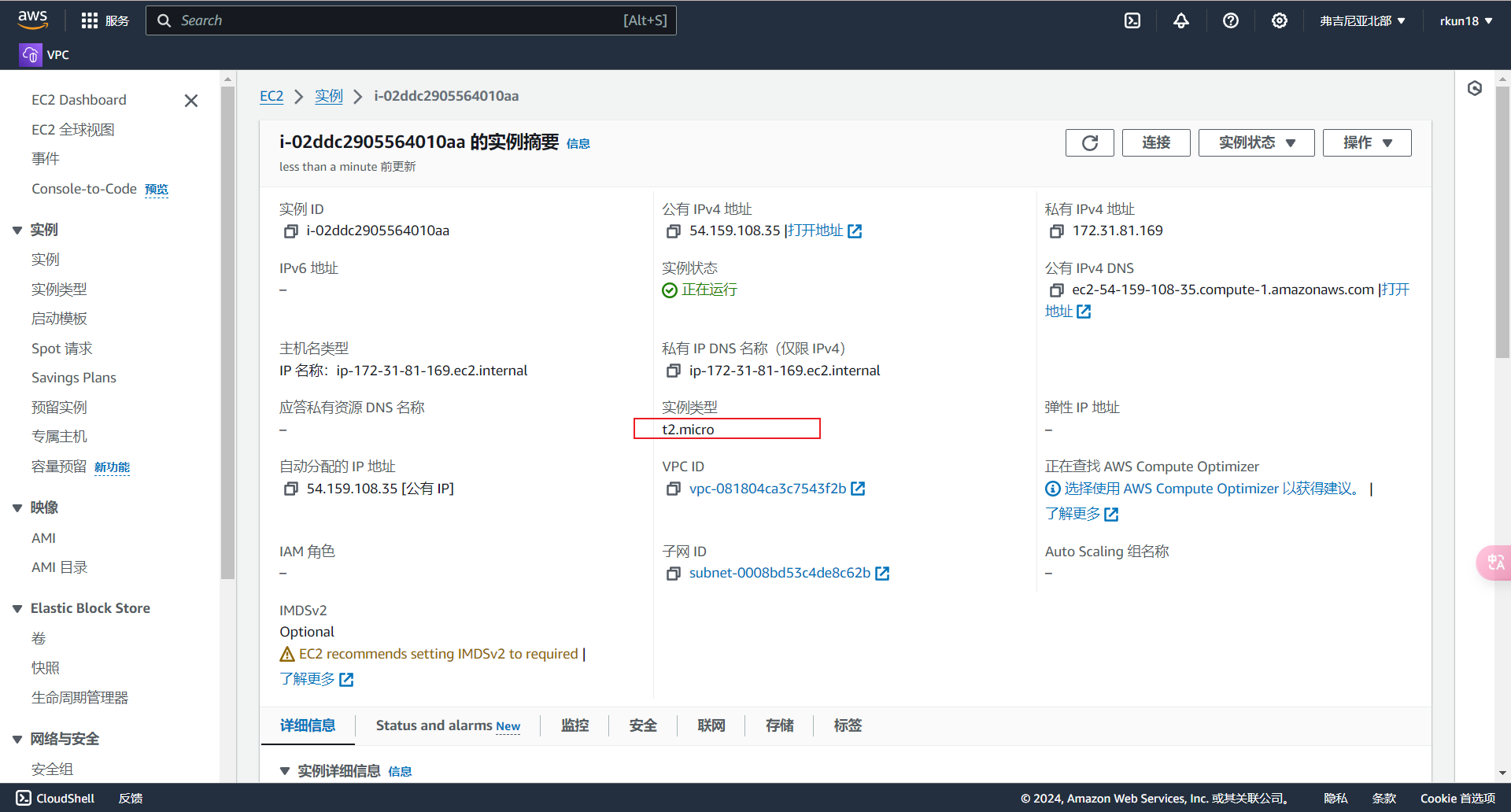
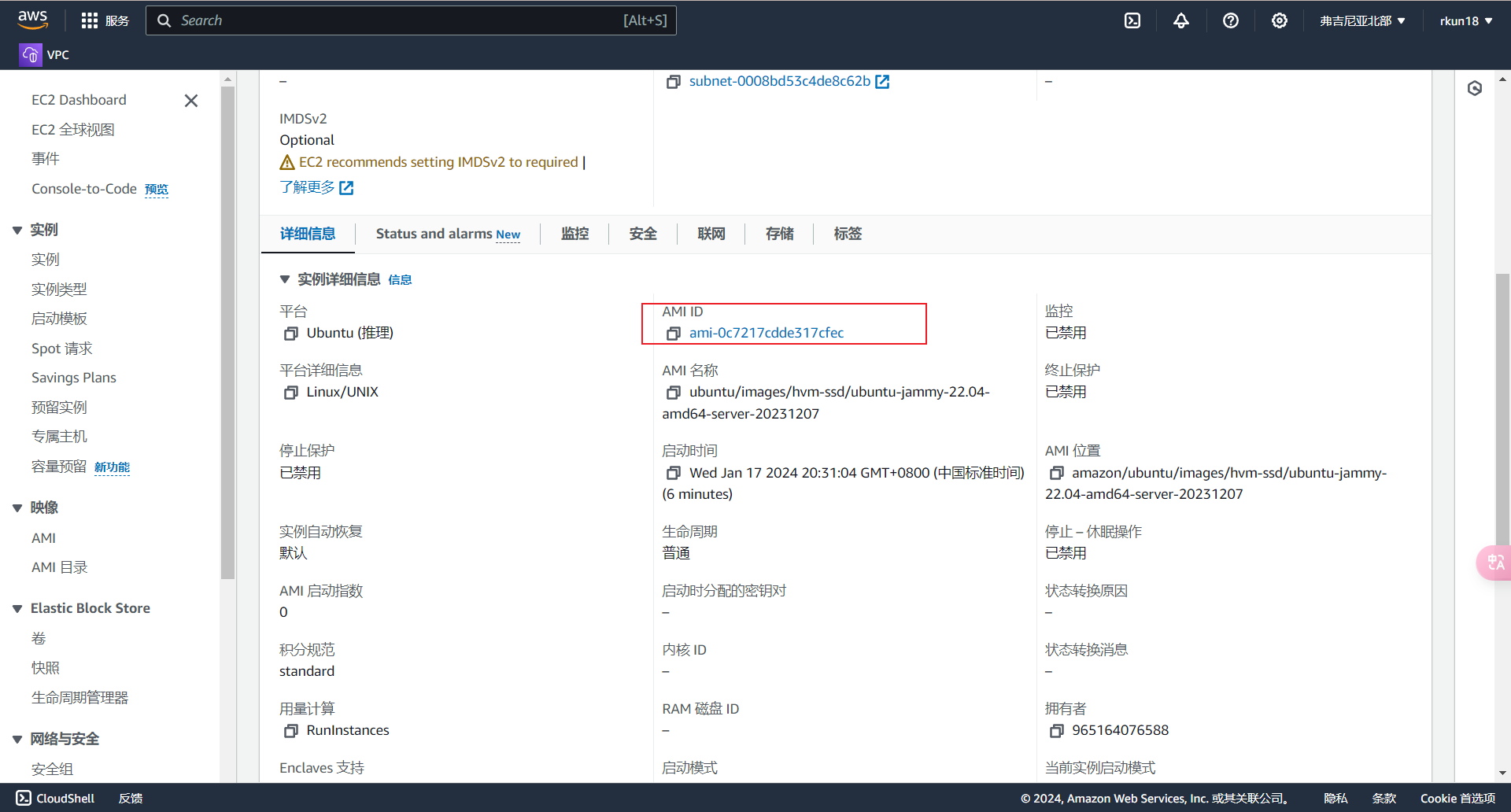
更改资源
给EC2实例添加标签
provider "aws" {
region = "us-east-1"
access_key = "AKIA6BOCDBYWM4JBXHNU"
secret_key = "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"
}
resource "aws_instance" "my_server" {
ami = "ami-0c7217cdde317cfec"
instance_type = "t2.micro"
tags = {
Name = "ubuntu"
}
}
terraform plan 查看.tf文件运行后产生的改变
PS C:\Code\Terraform> terraform plan
aws_instance.my_server: Refreshing state... [id=i-02ddc2905564010aa]
Terraform used the selected providers to generate the following execution plan. Resource
actions are indicated with the following symbols:
~ update in-place
Terraform will perform the following actions:
# aws_instance.my_server will be updated in-place
~ resource "aws_instance" "my_server" {
id = "i-02ddc2905564010aa"
~ tags = {
+ "Name" = "ubuntu"
}
~ tags_all = {
+ "Name" = "ubuntu"
}
# (30 unchanged attributes hidden)
# (8 unchanged blocks hidden)
}
Plan: 0 to add, 1 to change, 0 to destroy.
─────────────────────────────────────────────────────────────────────────────────────────
Note: You didn't use the -out option to save this plan, so Terraform can't guarantee to
take exactly these actions if you run "terraform apply" now.
terraform apply 运行
PS C:\Code\Terraform> terraform apply
aws_instance.my_server: Refreshing state... [id=i-02ddc2905564010aa]
Terraform used the selected providers to generate the following execution plan. Resource
actions are indicated with the following symbols:
~ update in-place
Terraform will perform the following actions:
# aws_instance.my_server will be updated in-place
~ resource "aws_instance" "my_server" {
id = "i-02ddc2905564010aa"
~ tags = {
+ "Name" = "ubuntu"
}
~ tags_all = {
+ "Name" = "ubuntu"
}
# (30 unchanged attributes hidden)
# (8 unchanged blocks hidden)
}
Plan: 0 to add, 1 to change, 0 to destroy.
Do you want to perform these actions?
Terraform will perform the actions described above.
Only 'yes' will be accepted to approve.
Enter a value: yes
aws_instance.my_server: Modifying... [id=i-02ddc2905564010aa]
aws_instance.my_server: Still modifying... [id=i-02ddc2905564010aa, 10s elapsed]
aws_instance.my_server: Still modifying... [id=i-02ddc2905564010aa, 20s elapsed]
aws_instance.my_server: Still modifying... [id=i-02ddc2905564010aa, 30s elapsed]
aws_instance.my_server: Modifications complete after 34s [id=i-02ddc2905564010aa]
Apply complete! Resources: 0 added, 1 changed, 0 destroyed.
控制台查看配置信息是否改变
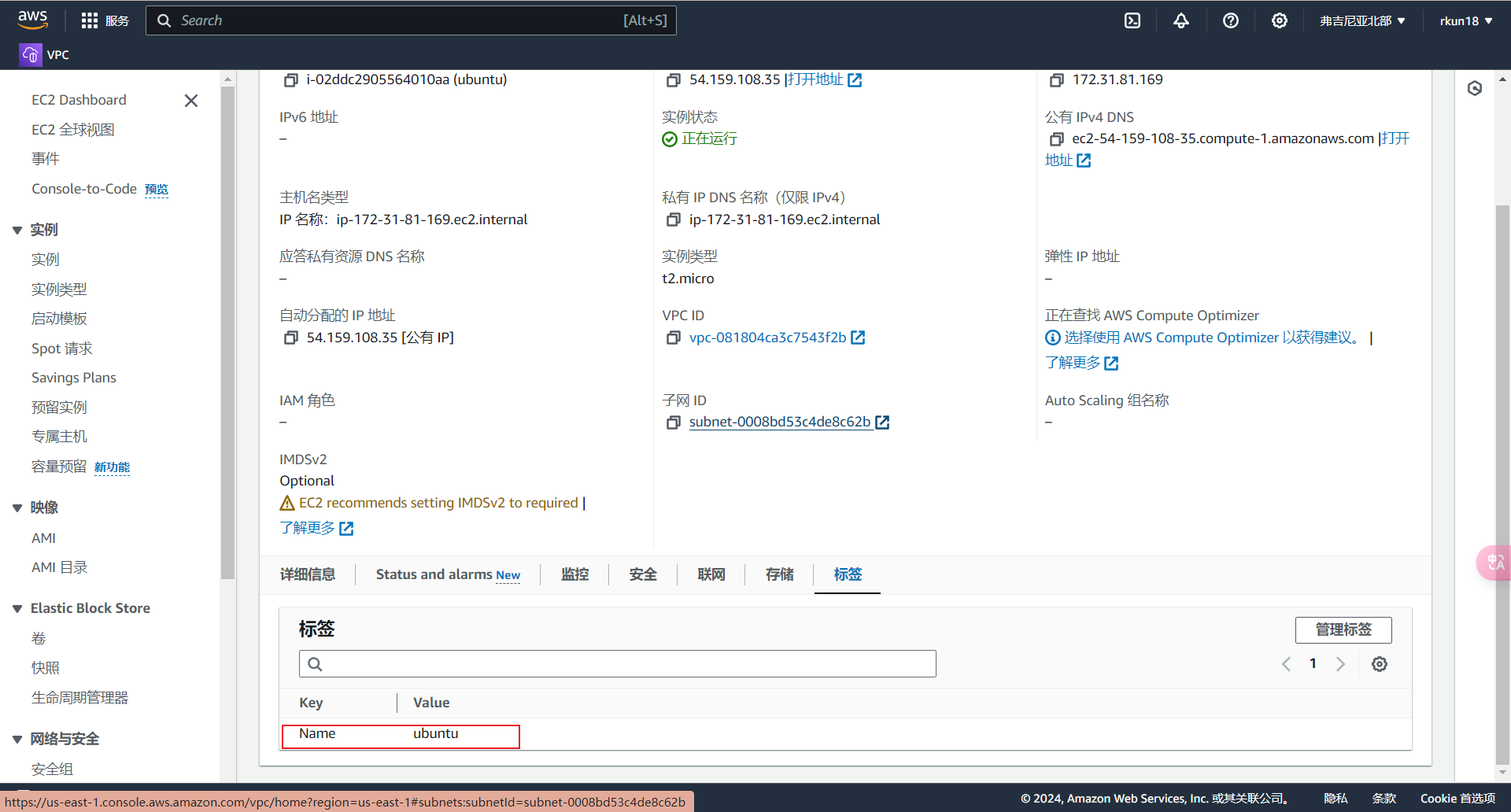
删除资源
terraform destroy 将摧毁你Terraform定义的的所有资源
PS C:\Code\Terraform> terraform destroy
aws_instance.my_server: Refreshing state... [id=i-02ddc2905564010aa]
Terraform used the selected providers to generate the following execution plan. Resource
actions are indicated with the following symbols:
- destroy
Terraform will perform the following actions:
# aws_instance.my_server will be destroyed
- resource "aws_instance" "my_server" {
- ami = "ami-0c7217cdde317cfec" -> null
- arn = "arn:aws:ec2:us-east-1:965164076588:instance/i-02ddc2905564010aa" -> null
- associate_public_ip_address = true -> null
- availability_zone = "us-east-1c" -> null
- cpu_core_count = 1 -> null
- cpu_threads_per_core = 1 -> null
- disable_api_stop = false -> null
- disable_api_termination = false -> null
- ebs_optimized = false -> null
- get_password_data = false -> null
- hibernation = false -> null
- id = "i-02ddc2905564010aa" -> null
- instance_initiated_shutdown_behavior = "stop" -> null
- instance_state = "running" -> null
- instance_type = "t2.micro" -> null
- ipv6_address_count = 0 -> null
- ipv6_addresses = [] -> null
- monitoring = false -> null
- placement_partition_number = 0 -> null
- primary_network_interface_id = "eni-05f493db48e53e6d1" -> null
- private_dns = "ip-172-31-81-169.ec2.internal" -> null
- private_ip = "172.31.81.169" -> null
- public_dns = "ec2-54-159-108-35.compute-1.amazonaws.com"
-> null
- public_ip = "54.159.108.35" -> null
- secondary_private_ips = [] -> null
- security_groups = [
- "default",
] -> null
- source_dest_check = true -> null
- subnet_id = "subnet-0008bd53c4de8c62b" -> null
- tags = {
- "Name" = "ubuntu"
} -> null
- tags_all = {
- "Name" = "ubuntu"
} -> null
- tenancy = "default" -> null
- user_data_replace_on_change = false -> null
- vpc_security_group_ids = [
- "sg-0269e952138afa470",
] -> null
- capacity_reservation_specification {
- capacity_reservation_preference = "open" -> null
}
- cpu_options {
- core_count = 1 -> null
- threads_per_core = 1 -> null
}
- credit_specification {
- cpu_credits = "standard" -> null
}
- enclave_options {
- enabled = false -> null
}
- maintenance_options {
- auto_recovery = "default" -> null
}
- metadata_options {
- http_endpoint = "enabled" -> null
- http_protocol_ipv6 = "disabled" -> null
- http_put_response_hop_limit = 1 -> null
- http_tokens = "optional" -> null
- instance_metadata_tags = "disabled" -> null
}
- private_dns_name_options {
- enable_resource_name_dns_a_record = false -> null
- enable_resource_name_dns_aaaa_record = false -> null
- hostname_type = "ip-name" -> null
}
- root_block_device {
- delete_on_termination = true -> null
- device_name = "/dev/sda1" -> null
- encrypted = false -> null
- iops = 100 -> null
- tags = {} -> null
- throughput = 0 -> null
- volume_id = "vol-0996176cc9bdc5548" -> null
- volume_size = 8 -> null
- volume_type = "gp2" -> null
}
}
Plan: 0 to add, 0 to change, 1 to destroy.
Do you really want to destroy all resources?
Terraform will destroy all your managed infrastructure, as shown above.
There is no undo. Only 'yes' will be accepted to confirm.
Enter a value: yes
aws_instance.my_server: Destroying... [id=i-02ddc2905564010aa]
aws_instance.my_server: Still destroying... [id=i-02ddc2905564010aa, 10s elapsed]
aws_instance.my_server: Still destroying... [id=i-02ddc2905564010aa, 20s elapsed]
aws_instance.my_server: Still destroying... [id=i-02ddc2905564010aa, 30s elapsed]
aws_instance.my_server: Still destroying... [id=i-02ddc2905564010aa, 41s elapsed]
aws_instance.my_server: Destruction complete after 44s
Destroy complete! Resources: 1 destroyed.
Terraform 文件
在你进行了上述操作后,项目文件夹会生成一些文件
.terraform #使用init命令 安装云提供商插件 文件夹
.terraform.lock.hcl # 该文件通常包含 Terraform 对模块版本的锁定信息
main.tf
terraform.tfstate #代表着terraform的所有状态 跟踪创建的一切
terraform.tfstate.backup #这是 terraform.tfstate 文件的备份。在每次 Terraform 执行时,
Terraform 会自动创建备份文件,以防止在执行期间发生意外的情况。
项目实战
创建EC2实例,将其部署周期自定义子网的VPC上,为其分配一个公共IP地址,我们可以通过SSH连接到它并进行操作,我们还可以设置一个网络服务器在其上运行,以便我们可以处理网络。
- 创建VPC
- 创建Internet Gateway
- 创建Custom Route table
- 创建Subnet
- 连接Subnet到Route Table
- 创建安全组允许端口22,80,443
- 创建一个网络接口使用子网的IP
- 分配一个弹性IP给网络接口
- 创建一个Ubuntu服务器并安装apache2
创建密钥对,允许我们连接到AWS服务器
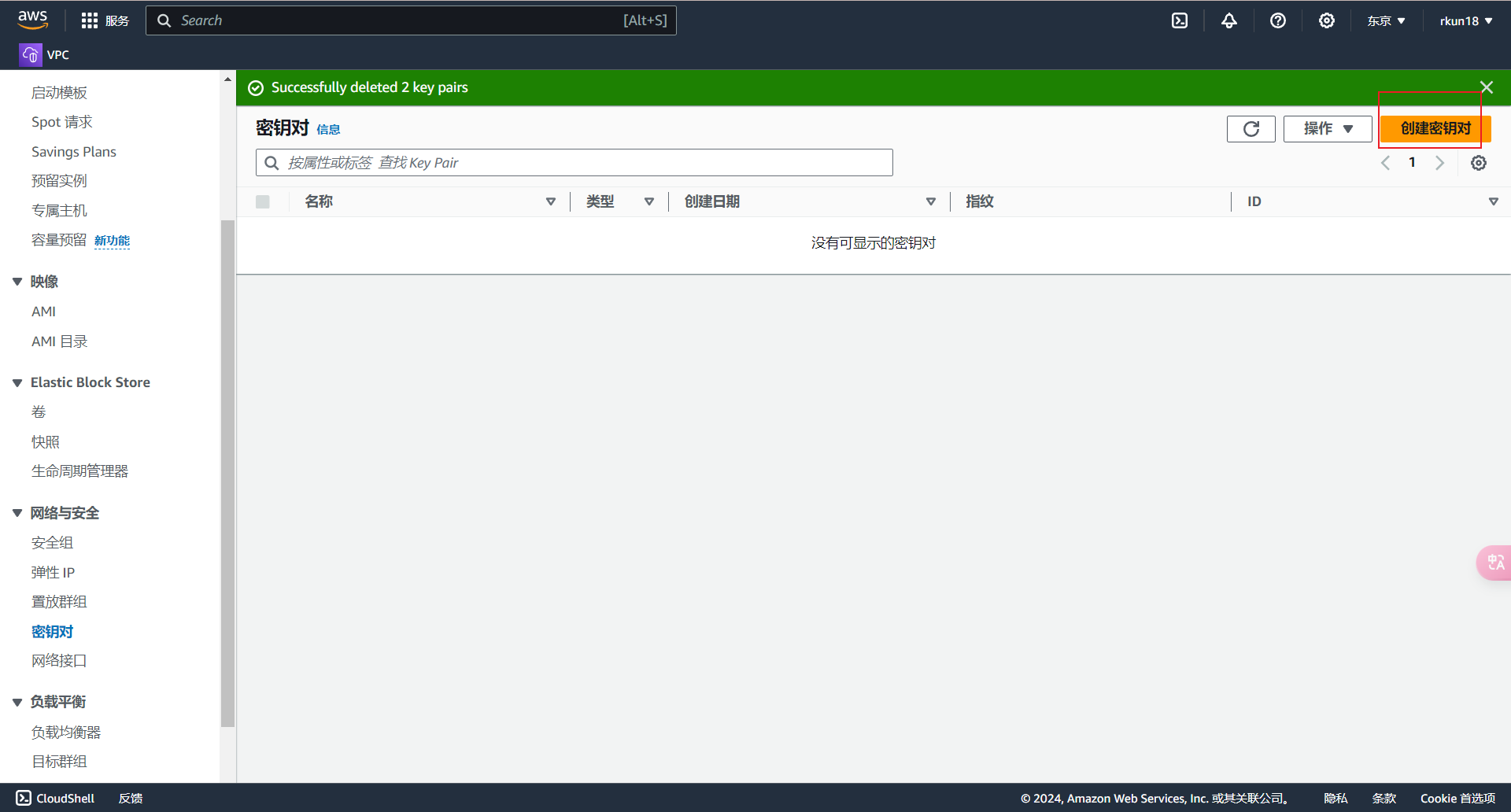
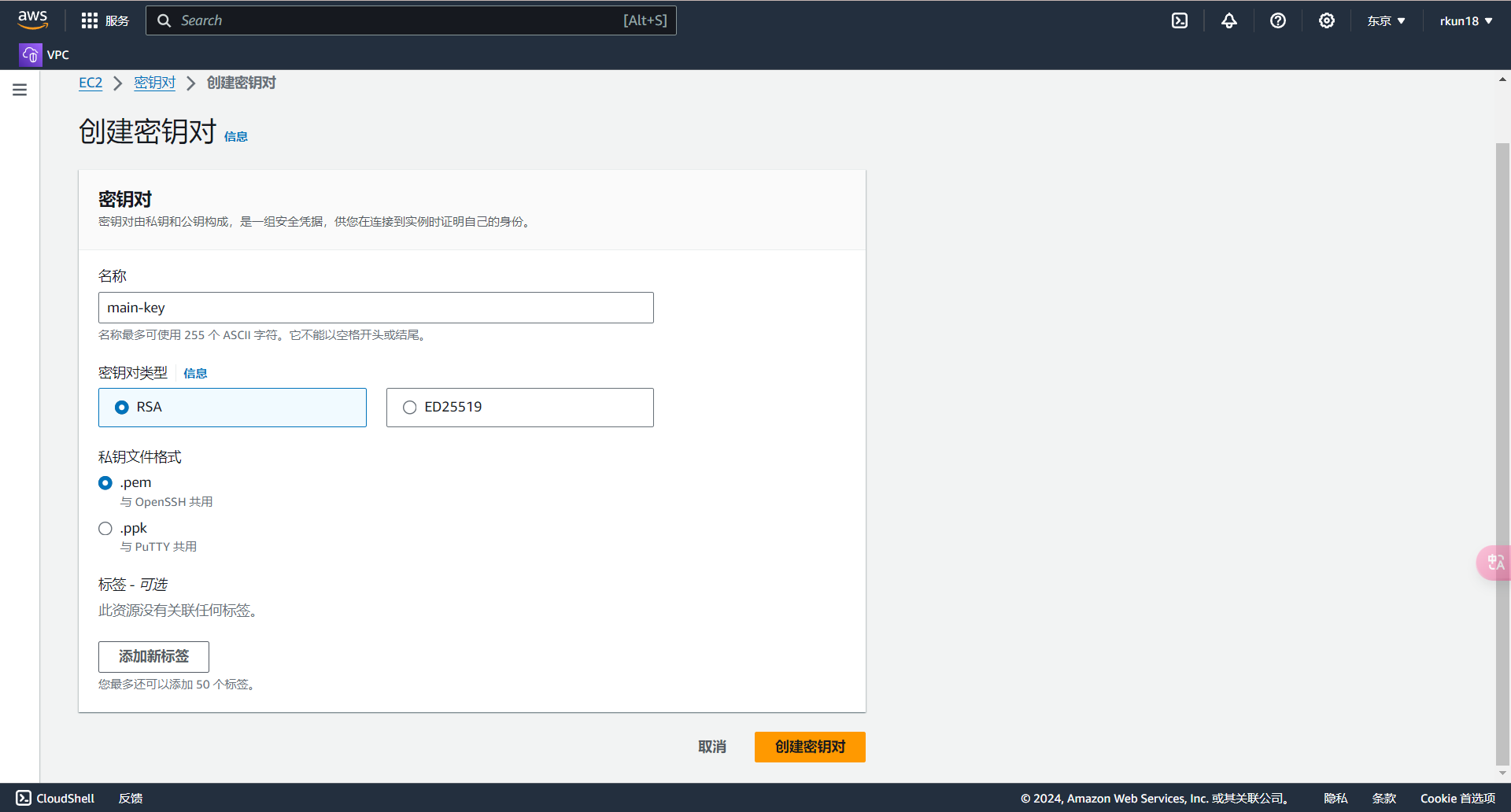
main.tf
provider "aws" {
region = "us-east-1"
access_key = "AKIA6BOCDBYWM4JBXHNU"
secret_key = "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"
}
# 创建VPC
resource "aws_vpc" "prod-vpc" {
cidr_block = "10.0.0.0/16"
tags = {
Name = "production"
}
}
#创建网关
resource "aws_internet_gateway" "gw" {
vpc_id = aws_vpc.prod-vpc.id
}
#创建路由表
resource "aws_route_table" "prod-route-table" {
vpc_id = aws_vpc.prod-vpc.id
route {
cidr_block = "0.0.0.0/0"
gateway_id = aws_internet_gateway.gw.id
}
route {
ipv6_cidr_block = "::/0"
gateway_id = aws_internet_gateway.gw.id
}
tags = {
Name = "Prod"
}
}
#创建子网
resource "aws_subnet" "subnet-1" {
vpc_id = aws_vpc.prod-vpc.id
cidr_block = "10.0.1.0/24"
availability_zone = "us-east-1a"
tags = {
Name = "prod-subnet"
}
}
#链接子网和路由表
resource "aws_route_table_association" "a" {
subnet_id = aws_subnet.subnet-1.id
route_table_id = aws_route_table.prod-route-table.id
}
#创建安全组
resource "aws_security_group" "allow_web" {
name = "allow_web_traffic"
description = "Allow Web inbound traffic "
vpc_id = aws_vpc.prod-vpc.id
ingress {
description = "HTTPS"
from_port = 443
to_port = 443
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
ingress {
description = "HTTP"
from_port = 80
to_port = 80
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
ingress {
description = "SSH"
from_port = 22
to_port = 22
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
tags = {
Name = "allow_web"
}
}
#创建网络接口
resource "aws_network_interface" "web-server-nic" {
subnet_id = aws_subnet.subnet-1.id
private_ips = ["10.0.1.50"]
security_groups = [aws_security_group.allow_web.id]
}
#设置弹性IP
resource "aws_eip" "one" {
domain = "vpc"
network_interface = aws_network_interface.web-server-nic.id
associate_with_private_ip = "10.0.1.50"
depends_on = [aws_internet_gateway.gw]
}
#创建ubuntu服务器
resource "aws_instance" "web-server-instance" {
ami = "ami-0c7217cdde317cfec"
instance_type = "t2.micro"
availability_zone = "us-east-1a"
key_name = "main-key"
network_interface {
device_index = 0
network_interface_id = aws_network_interface.web-server-nic.id
}
user_data = <<-EOF
#!/bin/bash
sudo apt update -y
sudo apt install apache2 -y
sudo systemctl start apache2
EOF
tags = {
Name = "web-server"
}
}
检查
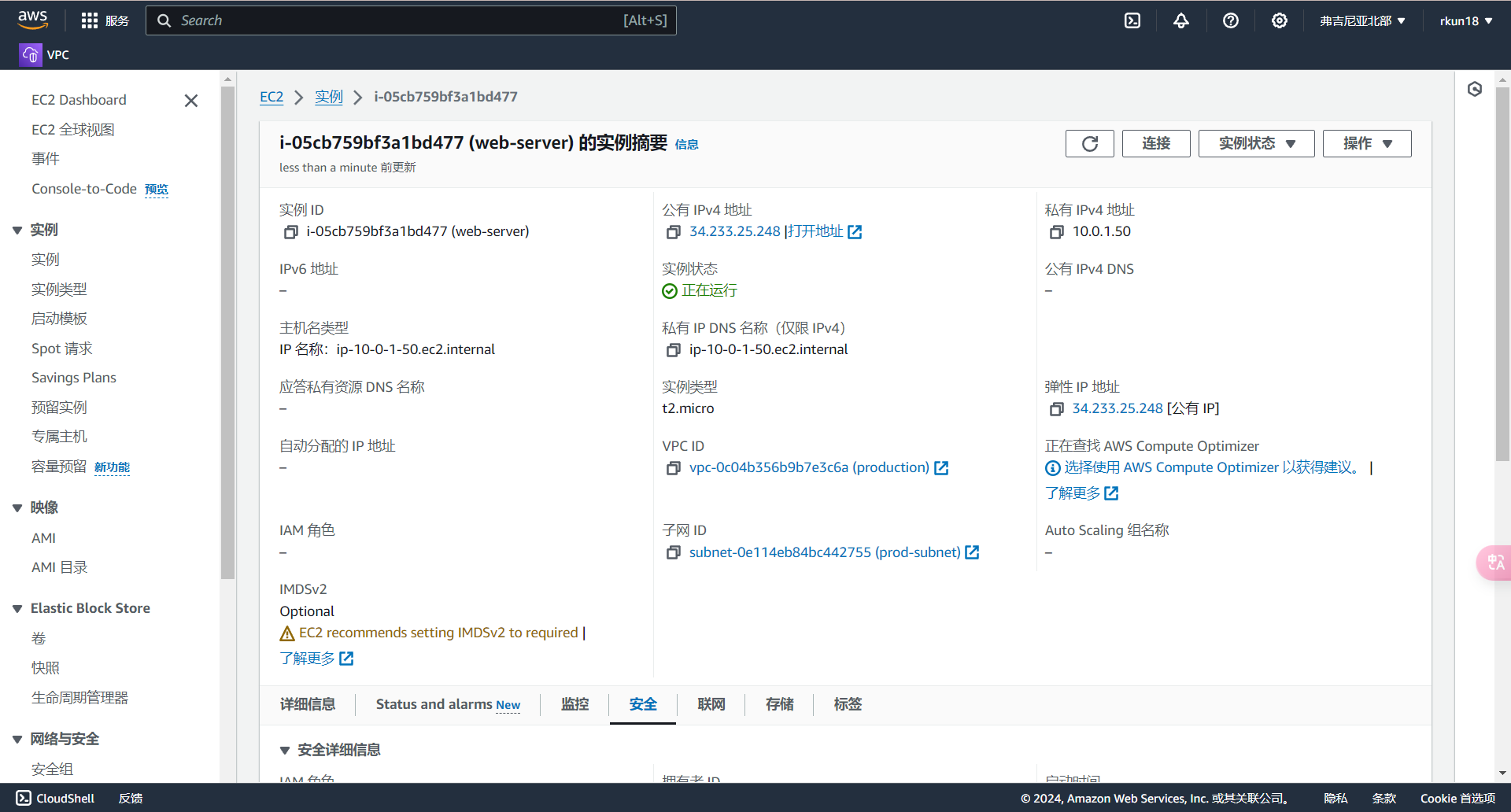
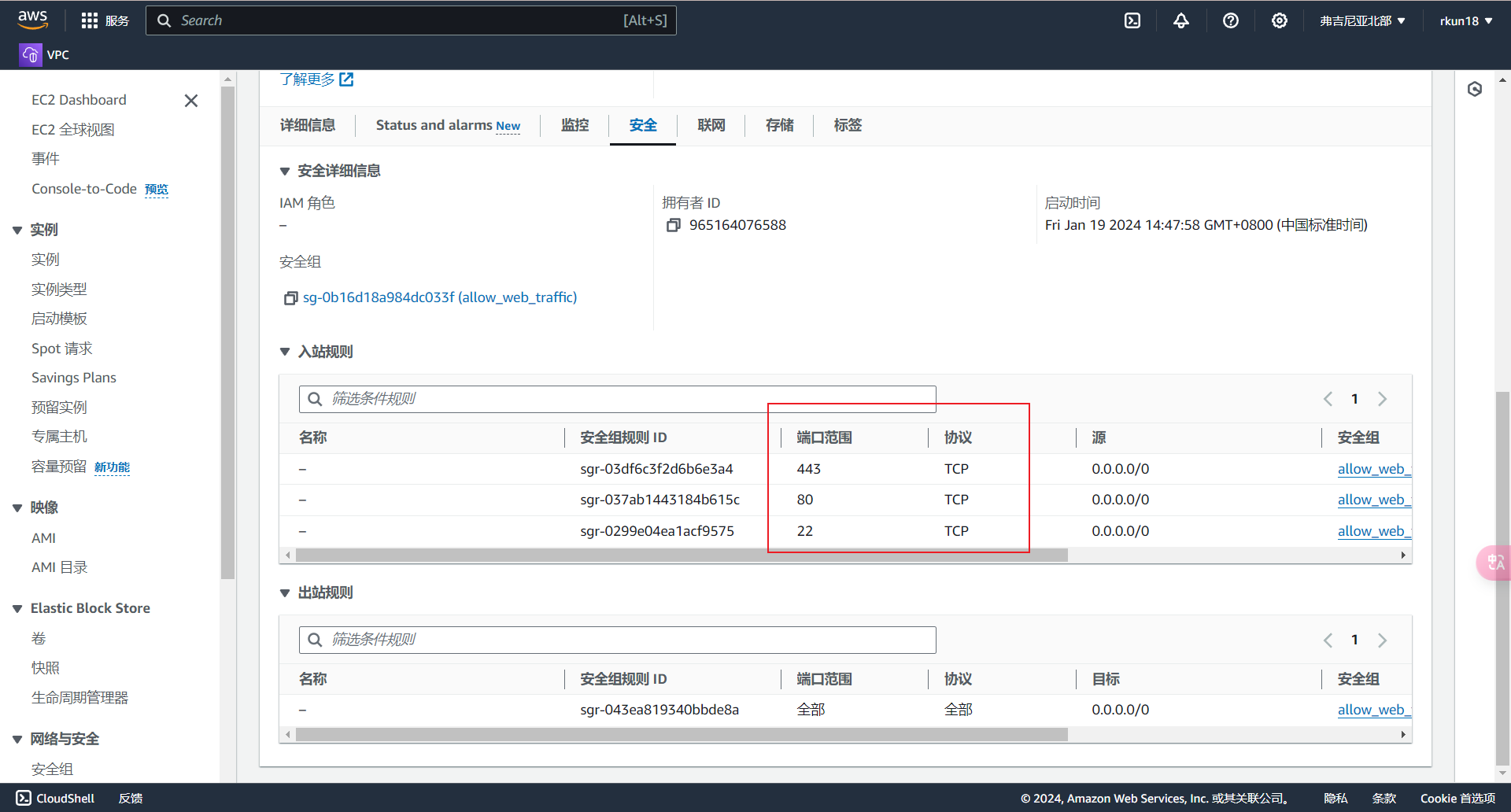
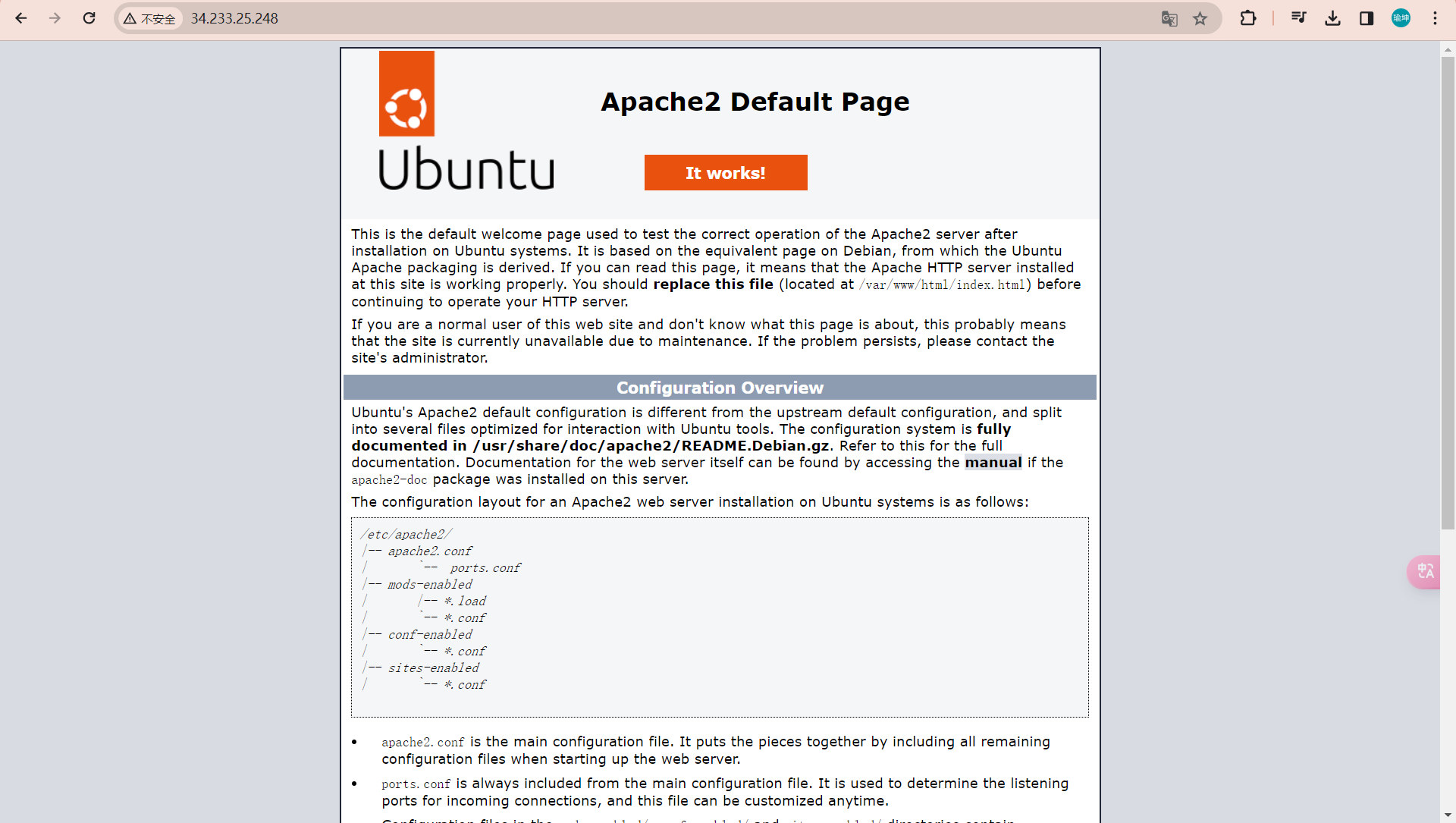
复制其公有IP进行访问,成功访问说明Terraform完成自动化云基础设置构建
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
- Python教程
- 深入理解 MySQL 中的 HAVING 关键字和聚合函数
- Qt之QChar编码(1)
- MyBatis入门基础篇
- 用Python脚本实现FFmpeg批量转换
- 2.1 DATA PARALLELISM
- vue前端开发准备工作ing...
- 一起玩儿物联网人工智能小车(ESP32)——17. 用ESP32的ADC功能读取电源电压
- 排序算法合集
- 【HarmonyOS4.0】第六篇-ArkUI系统组件(一)
- iPhone/iPad上设置和使用隧道代理HTTP
- Nas群晖中搭建自己的图片库
- 大数据安全 | 期末复习(上)| 补档
- 【微服务】springboot整合kafka-stream使用详解
- 【JavaWeb】Web程序设计期末复习总结