配置华为防火墙虚拟系统
发布时间:2023年12月29日
实验目的:
如图所示,在防火墙上创建两个虚拟系统,分别命名为vsysa、vsysb,PC1属于vsysa、PC2属于vsysb,最终实现PC1和PC2能够互相访问。
实验拓扑:
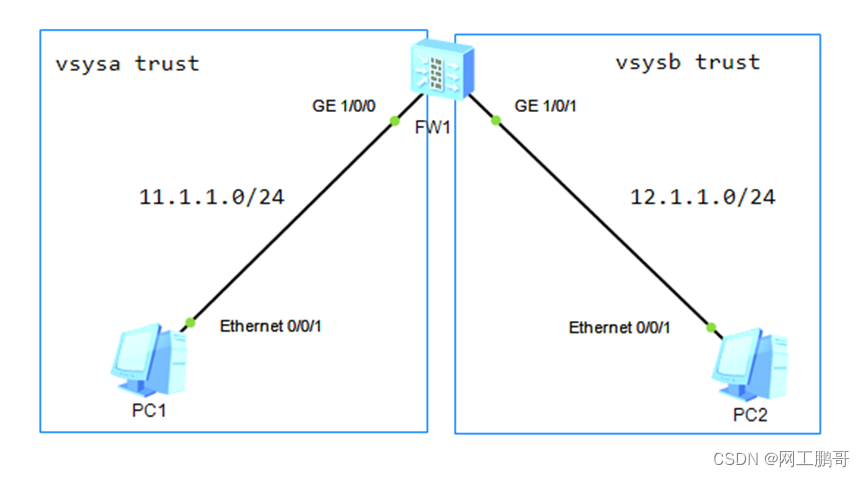
实验步骤:
步骤1:创建虚拟系统,并且将虚拟系统、根系统都视为独立的设备,将虚拟接口视为设备之间通信对应的接口,通过划分到对应的虚拟系统。
FW1的配置:
[FW1]vsys enable
[FW1]vsys name vsysa//创建虚拟系统,名字为vsysa
[FW1-vsys-vsysa] assign interface GigabitEthernet1/0/0//将G0/0/0口划分到vsysa
[FW1-vsys-vsysa] quit
[FW1]vsys name vsysb //创建虚拟系统,名字为vsysa
[FW1-vsys-vsysb] assign interface GigabitEthernet1/0/1/将虚拟接口加入G0/0/1口划分到vsysb
[FW1-vsys-vsysb] quit步骤2:进入虚拟系统视图,配置接口ip地址,并且将接口划分到安全区域并按照。
1)配置vsysa的ip地址
[FW1]switch vsys vsysa
[FW1-vsysa]display? inter br
Interface?????????????????? PHY?? Protocol? InUti OutUti?? inErrors? outErrors
GigabitEthernet1/0/0??????? up??? up?????????? 0%???? 0%????????? 0????????? 0
Virtual-if1???????????????? up??? up(s)??????? --???? --????????? 0????????? 0通过以上输出可以发现,设备为vsysa分配了一个虚拟接口virtual-if1,用于与其他虚拟系统通信。
[FW1-vsysa]interface GigabitEthernet1/0/0
[FW1-vsysa-GigabitEthernet1/0/0]ip address 11.1.1.1 255.255.255.0
[FW1-vsysa-GigabitEthernet1/0/0]q
[FW1-vsysa]interface Virtual-if1
[FW1-vsysa-Virtual-if1] ip address 172.16.1.1 255.255.255.2552)将vsysa的接口划分到安全区域
[FW1-vsysa]firewall zone trust
[FW1-vsysa-zone-trust]add interface GigabitEthernet1/0/0
[FW1-vsysa-zone-trust]q
[FW1-vsysa]firewall zone dmz
[FW1-vsysa-zone-dmz]add interface Virtual-if13)配置一般设备间互访vsysb的思路ip地址(配置前注意退出到根系统)
[FW1]switch vsys vsysb
[FW1-vsysb]display? int br
Interface?????????????????? PHY?? Protocol? InUti OutUti?? inErrors? outErrors
GigabitEthernet1/0/1??????? up??? up?????????? 0%???? 0%????????? 0????????? 0
Virtual-if2???????????????? up??? up(s)??????? --???? --????????? 0????????? 0通过以上输出可以发现,设备为vsysa分配了一个虚拟接口virtual-if2,用于与其他虚拟系统通信。
[FW1-vsysb]interface GigabitEthernet1/0/1
[FW1-vsysb-GigabitEthernet1/0/1]ip address 12.1.1.1 255.255.255.0
[FW1-vsysb-GigabitEthernet1/0/1]q
[FW1-vsysb]interface Virtual-if2
[FW1-vsysb-Virtual-if2] ip address 172.16.2.1 255.255.255.2554)将vsysb的接口划分到安全区域
[FW1-vsysb]firewall zone trust
[FW1-vsysb-zone-trust]add interface GigabitEthernet1/0/1
[FW1-vsysb-zone-trust]q
[FW1-vsysb]firewall zone dmz
[FW1-vsysb-zone-dmz]add interface Virtual-if2查看设备的vpn实例
[FW1]display? ip vpn-instance
2023-12-02 03:21:57.000
?Total VPN-Instances configured????? : 3
?Total IPv4 VPN-Instances configured : 3
?Total IPv6 VPN-Instances configured : 2
? VPN-Instance Name?????????????? RD??????????????????? Address-family
? default?????????????????????????????????????????????? IPv4
? vsysa???????????????????????????????????????????????? IPv4
? vsysa???????????????????????????????????????????????? IPv6
? vsysb???????????????????????????????????????????????? IPv4
? vsysb???????????????????????????????????????????????? IPv6通过以上输出可知,创建了虚拟系统vsysa和vsysb的同时,设备上会自动创建两个同名的vpn实例。虚拟之间的通信则查询对应的vpn实例路由表即可。
步骤3:配置静态路由和策略,就能实现,实现路由可达,不同的虚拟系统通信,需要通过virtual-if接口通信,因此静态路由的下一跳,写虚拟系统的vpn实例即可。
[FW1]ip route-static vpn-instance? vsysa 12.1.1.0 24 vpn-instance vsysb
[FW1]ip route-static vpn-instance? vsysb 11.1.1.0 24 vpn-instance vsysa查询路由表:
[FW1]display? ip routing-table vpn-instance vsysa
2023-12-02 03:23:27.090
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Tables: vsysa
???????? Destinations : 4??????? Routes : 4
Destination/Mask??? Proto?? Pre? Cost????? Flags NextHop???????? Interface
?????? 11.1.1.0/24? Direct? 0??? 0?????????? D?? 11.1.1.1??????? GigabitEthernet1/0/0
?????? 11.1.1.1/32? Direct? 0??? 0?????????? D?? 127.0.0.1?????? GigabitEthernet1/0/0
?????? 12.1.1.0/24? Static? 60?? 0?????????? D?? 172.16.2.1????? Virtual-if2
???? 172.16.1.1/32? Direct? 0??? 0?????????? D?? 127.0.0.1?????? Virtual-if1
[FW1]display? ip routing-table vpn-instance vsysb
2023-12-02 03:23:29.040
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Tables: vsysb
???????? Destinations : 4??????? Routes : 4
Destination/Mask??? Proto?? Pre? Cost????? Flags NextHop???????? Interface
?????? 11.1.1.0/24? Static? 60?? 0?????????? D?? 172.16.1.1????? Virtual-if1
?????? 12.1.1.0/24? Direct? 0??? 0?????????? D?? 12.1.1.1??????? GigabitEthernet1/0/1
?????? 12.1.1.1/32? Direct? 0??? 0?????????? D?? 127.0.0.1?????? GigabitEthernet1/0/1
???? 172.16.2.1/32? Direct? 0??? 0?????????? D?? 127.0.0.1?????? Virtual-if2通过以上输出可知,vsysa、vsysb两个vpn实例有去往对端业务网段的路由,并且下一跳为对端虚拟系统的vritual-if接口。
步骤4:配置两个虚拟系统和根系统的的安全策略。
配置vsysa的安全策略,放行PC1访问PC2的流量以及PC2访问PC1的流量。
[FW1]switch vsys vsysa
<FW1-vsysa>sys
Enter system view, return user view with Ctrl+Z.
[FW1-vsysa]security-policy
[FW1-vsysa-policy-security] rule name trust_dmz
[FW1-vsysa-policy-security-rule-trust_dmz]? source-zone dmz
[FW1-vsysa-policy-security-rule-trust_dmz]? source-zone trust
[FW1-vsysa-policy-security-rule-trust_dmz]? destination-zone dmz
[FW1-vsysa-policy-security-rule-trust_dmz]? destination-zone trust
[FW1-vsysa-policy-security-rule-trust_dmz]? action permit
[FW1]switch vsys vsysb
<FW1-vsysb>sys
Enter system view, return user view with Ctrl+Z.
[FW1-vsysb]security-policy
[FW1-vsysb-policy-security] rule name trust_dmz
[FW1-vsysb-policy-security-rule-trust_dmz]? source-zone dmz
[FW1-vsysb-policy-security-rule-trust_dmz]? source-zone trust
[FW1-vsysb-policy-security-rule-trust_dmz]? destination-zone dmz
[FW1-vsysb-policy-security-rule-trust_dmz]? destination-zone trust
[FW1-vsysb-policy-security-rule-trust_dmz]? action permit测试:
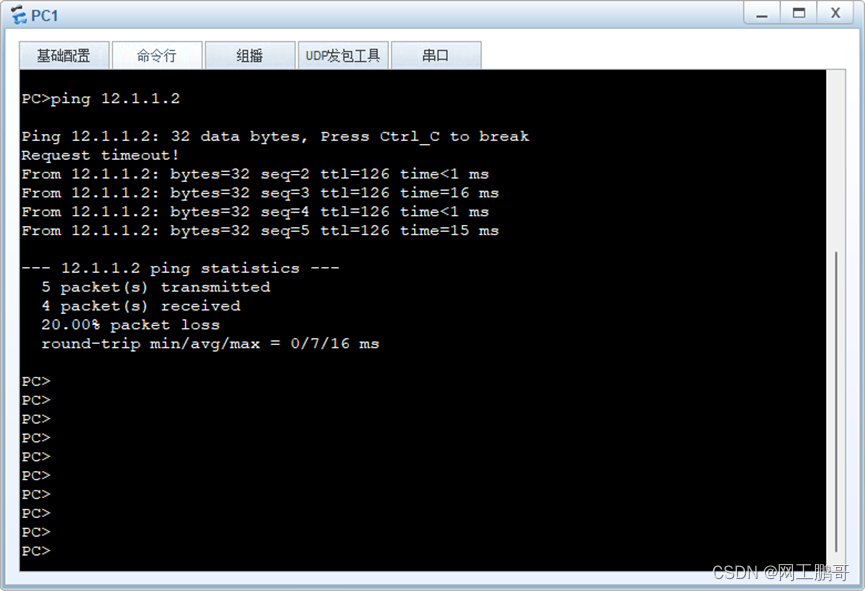
使用PC1访问PC2
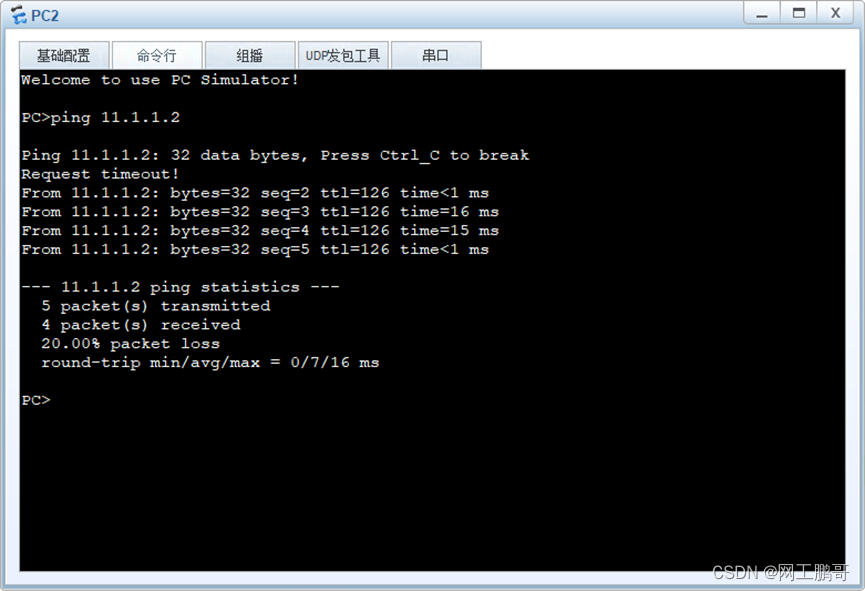
使用PC2访问PC1
文章来源:https://blog.csdn.net/2301_76769137/article/details/135292816
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
最新文章
- Python教程
- 深入理解 MySQL 中的 HAVING 关键字和聚合函数
- Qt之QChar编码(1)
- MyBatis入门基础篇
- 用Python脚本实现FFmpeg批量转换
- 【adb】--- win10 配置 adb环境 超详细 (持续更新中)
- SpringMVC执行流程
- FMQL BOOT.bin固化文件生成及固化流程记录
- 全球盲盒热潮:探寻海外市场的文化风潮与商机
- Docker单点部署[8.11.3] Elasticsearch + Kibana + ik分词器
- 基于Java SSM框架实现医院管理系统项目【项目源码】计算机毕业设计
- 【C工具】【libevent】一、win+msys2环境下的安装
- MybatisPlus是什么?它有什么功能和特性?它值不值得我们去学习?我们该如何去学习呢?
- 类与对象、this关键字
- java之反射