Software supply chain
发布时间:2024年01月05日
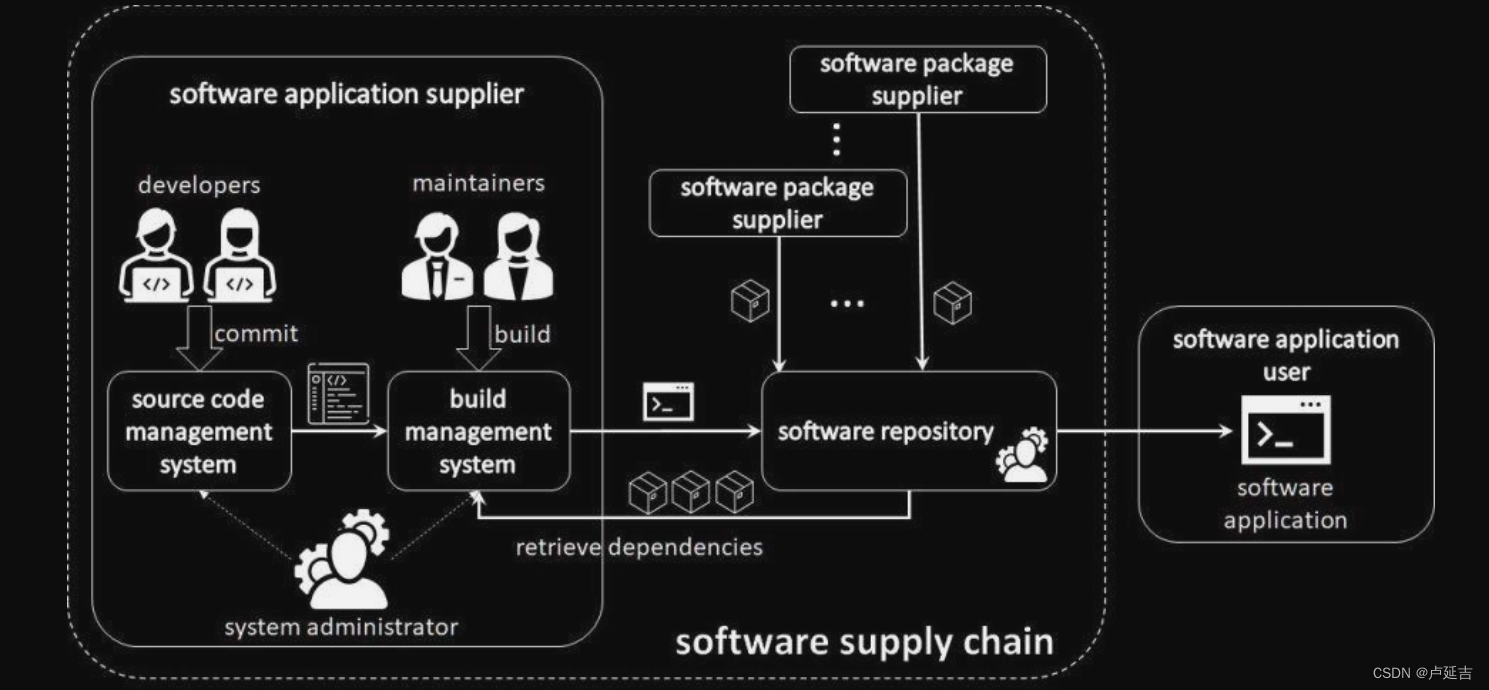
Simply put
- Requirements: The software supply chain begins with identifying and gathering user requirements. This step involves understanding the needs and expectations of software users.
- Design and Development: Once the requirements are gathered, the software is designed and developed by software engineers and developers. This includes writing code, testing, and refining the software to meet the desired functionality.
- Release and Deployment: After the development process, the software is released and deployed to the end-users. This can involve packaging the software into installation files or deploying it on cloud platforms.
- Integration and Testing: The released software often needs to be integrated with existing systems or other software components. This step ensures that the software works seamlessly with other components and is thoroughly tested for bugs and issues.
- Distribution and Delivery: Once integration and testing are complete, the software is distributed and delivered to the end-users. This can be done through digital distribution channels, physical media, or online stores.
- Maintenance and Updates: Software requires ongoing maintenance and updates to address bugs, security vulnerabilities, and introduce new features or improvements. The software supply chain includes activities related to supporting, updating, and maintaining the software post-deployment.
- Support and Customer Service: This step involves providing customer support and service to end-users. This includes assisting with technical issues, answering questions, and addressing concerns related to the software.
Review of attacks, Risk assessment strategies and Security controls
- Malware Injection: Attackers may inject malware into the software during development or distribution to gain unauthorized access or control over systems. This can be mitigated by implementing security measures such as code review, static and dynamic analysis tools, and secure coding practices.
- Dependency Vulnerabilities: Software often relies on third-party libraries and components, which may have vulnerabilities that can be exploited. Regular vulnerability scanning and timely patching or updates to dependencies can help mitigate this risk.
- Third-Party Compromise: If a third-party involved in the software supply chain is compromised, it can have a cascading effect on the software’s security. Conducting thorough risk assessments and due diligence when selecting and vetting third-party vendors or partners is essential.
- Insider Threats: Malicious insiders within the software development or distribution process can intentionally introduce vulnerabilities or leaks sensitive information. Implementing strong access controls, monitoring privileged access, and conducting regular security awareness training for employees can help mitigate this risk.
- Weak Software Update Mechanisms: Attackers may exploit vulnerabilities in the software update mechanism to distribute malicious updates or compromise the integrity of the software. Implementing secure update mechanisms, such as digital signatures and secure channels for updates, helps protect against such attacks.
- Lack of Secure Development Lifecycle (SDLC) Practices: Failing to follow secure development practices can lead to vulnerabilities and weaknesses in the software. Incorporating secure coding guidelines, conducting regular security testing and code reviews, and integrating security into the SDLC can help mitigate these risks.
- Lack of Supply Chain Visibility: Limited visibility into the software supply chain can make it difficult to identify and mitigate security risks. Implementing tools and processes for supply chain visibility, such as software bill of materials (SBOM), can help identify and manage dependencies and vulnerabilities.
- Social Engineering and Phishing Attacks: Attackers may use social engineering techniques to trick individuals within the software supply chain into disclosing sensitive information or performing unauthorized actions. Regular security awareness training and strong phishing and social engineering defenses, such as email filtering and multi-factor authentication, can help mitigate this risk.
It’s important to note that the specific risks and security controls may vary depending on the organization’s context, the software being developed or distributed, and the specific threats faced. Conducting regular risk assessments, staying updated on emerging threats and vulnerabilities, and implementing a comprehensive security program are essential for mitigating risks in the software supply chain.
Acknowledgment
https://arxiv.org/ftp/arxiv/papers/2305/2305.14157.pdf
https://nvd.nist.gov/developers
文章来源:https://blog.csdn.net/weixin_38233104/article/details/135384117
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
最新文章
- Python教程
- 深入理解 MySQL 中的 HAVING 关键字和聚合函数
- Qt之QChar编码(1)
- MyBatis入门基础篇
- 用Python脚本实现FFmpeg批量转换
- Unity 创建/删除/启用/禁用组件的惯用方法
- QT+OSG/osgEarth编译之七十六:glsl+Qt编译(一套代码、一套框架,跨平台编译,版本:OSG-3.6.5插件库osgdb_glsl)
- 利用MATLAB绘制折线图
- Git中,版本库和远程库有什么区别
- [晓理紫]每日论文分享(有中文摘要,源码或项目地址)--大模型、扩散模型、视觉导航
- 举例说明计算机视觉(CV)技术的优势和挑战
- 【AIGC工具】我找到了使用大模型问答的最短路径!
- openssl3.2 - 官方demo学习 - smime - smsign.c
- 0基础学习VR全景平台篇第137篇:720VR全景,DJI无人机遥控器调参
- 主流数据库:实现数据过滤