iptables 防火墙(一)
发布时间:2023年12月28日
本章展示:
- - 熟悉Linux防火墙的表、链结构
- - 理解数据包匹配的基本流程
- - 学会编写iptables规则
2.1 Linux 防火墙基础
在
Internet
中,企业通过架设各种应用系统来为用户提供各种网络服务,如
Web
网站、
电子邮件系统、
FTP
服务器、数据库系统等。那么,如何来保护这些服务器,过滤企业不
需要的访问甚至是恶意的入侵呢?
本章将开始学习
Linux
系统中的防火墙
——netfilter
和
iptables
,包括防火墙的结构和
匹配流程,以及如何编写防火墙规则。
Linux
的防火墙体系主要工作在网络层,针对
TCP/IP
数据包实施过滤和限制,属于典
型的包过滤防火墙(或称为网络层防火墙)。
Linux
系统的防火墙体系基于内核编码实现,
具有非常稳定的性能和高效率,也因此获得广泛的应用。
在许多安全技术资料中,
netfilter
和
iptables
都用来指
Linux
防火墙,往往使读者产生
迷惑。
netfilter
和
iptables
的主要区别如下。
?
netfilter
:指的是
Linux
内核中实现包过滤防火墙的内部结构,不以程序或文件的形式
存在,属于
“
内核态
”
(
Kernel Space
,又称为内核空间)的防火墙功能体系。
?
iptables
:指的是用来管理
Linux
防火墙的命令程序,通常位于
/sbin/iptables
目录下,
属于
“
用户态
”
(
User Space
,又称为用户空间)的防火墙管理体系。
正确认识
netfilter
和
iptables
的关系,有助于理解
Linux
防火墙的工作方式。后续课程
内容中将不再严格区分
netfilter
和
iptables
,两者均可表示
Linux
防火墙。
2.1.1 iptables
的表、链结构
iptables
的作用是为包过滤机制的实现提供规则(或称为策略),通过各种不同的规则,
告诉
netfilter
对来自某些源、前往某些目的或具有某些协议特征的数据包应该如何处理。为
了更加方便地组织和管理防火墙规则,
iptables
采用了
“
表
”
和
“
链
”
的分层结构,如图
2.1
所示。
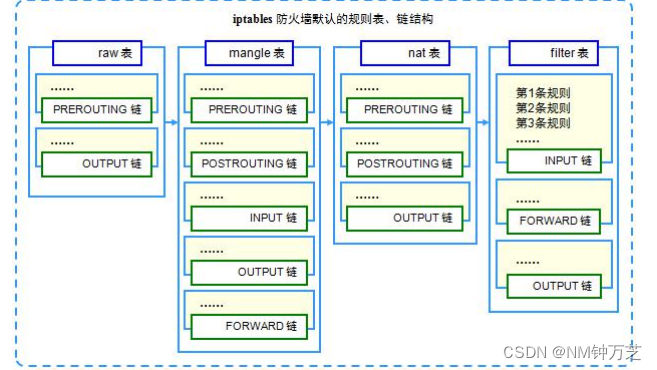
其中,每个规则
“
表
”
相当于内核空间的一个容器,根据规则集的不同用途划分为默认的
四个表;在每个
“
表
”
容器内包括不同的规则
“
链
”
,根据处理数据包的不同时机划分为五种链;
而决定是否过滤或处理数据包的各种规则,则是按先后顺序存放在各规则链中。
1
.规则表
为了从规则集的功能上有所区别,
iptables
管理着四个不同的规则表,其功能分别由独
立的内核模块实现。这四个表的名称、包含的链及各自的用途如下。
?
filter
表:
filter
表用来对数据包进行过滤,根据具体的规则要求决定如何处理一个数据
包。
filter
表对应的内核模块为
iptable_filter
,表内包含三个链,即
INPUT
、
FORWARD
、
OUTPUT
。
?
nat
表:
nat
(
Network Address Translation
,网络地址转换)表主要用来修改数据包的
IP
地址、端口号等信息。
nat
表对应的内核模块为
iptable_nat
,表内包含三个链,即
PREROUTING
、
POSTROUTING
、
OUTPUT
。
?
mangle
表:
mangle
表用来修改数据包的
TOS
(
Type Of Service
,服务类型)、
TTL
(
Time
To Live
,生存周期),或者为数据包设置
Mark
标记,以实现流量整形、策略路由等高
级 应 用 。
mangle
表 对 应 的 内 核 模 块 为
iptable_mangle
, 表 内 包 含 五 个 链 , 即
PREROUTING
、
POSTROUTING
、
INPUT
、
OUTPUT
、
FORWARD
。
?
raw
表:
raw
表是自
1.2.9
以后版本的
iptables
新增的表,主要用来决定是否对数据包
进行状态跟踪。
raw
表对应的内核模块为
iptable_raw
,表内包含两个链,即
OUTPUT
、
PREROUTING
。
在 iptables 的四个规则表中,mangle 表和 raw 表的应用相对较少。因此,本课程仅介
绍
filter
表和
nat
表的防火墙应用,关于
mangle
、
raw
表的使用,请参阅其他资料。
2
.规则链
在处理各种数据包时,根据防火墙规则的不同介入时机,
iptables
默认划分为五种不同
的规则链。这五种链的名称、各自的介入时机如下。
?
INPUT
链:当收到访问防火墙本机地址的数据包(入站)时,应用此链中的规则。
?
OUTPUT
链:当防火墙本机向外发送数据包(出站)时,应用此链中的规则。
?
FORWARD
链:当接收到需要通过防火墙中转发送给其他地址的数据包(转发)时,
应用此链中的规则。
?
PREROUTING
链:在对数据包做路由选择之前,应用此链中的规则。
?
POSTROUTING
链:在对数据包做路由选择之后,应用此链中的规则。
其中,
INPUT
、
OUTPUT
链主要用在
“
主机型防火墙
”
中,即主要针对服务器本机进行保
护的防火墙;而
FORWARD
、
PREROUTING
、
POSTROUTING
链多用在
“
网络型防火墙
”
中,如使用
Linux
防火墙作为网关服务器,在公司内网与
Internet
之间进行安全控制。
2.1.2
数据包过滤的匹配流程
iptables
管理着四个默认表和五种链,各种防火墙规则依次存放在链中。那么当一个数
据包到达防火墙以后,会优先使用哪一个表、哪一个链中的规则呢?数据包进出防火墙时的
处理过程是怎样的?
下面从不同角度分别介绍数据包过滤的匹配流程。
1
.规则表之间的顺序
当数据包抵达防火墙时,将依次应用
raw
表、
mangle
表、
nat
表和
filter
表中对应链内
的规则(如果存在),应用顺序为
raw→mangle→nat→filter
。
2
.规则链之间的顺序
根据规则链的划分原则,不同链的处理时机是比较固定的,因此规则链之间的应用顺序
取决于数据包的流向,如图
2.2
所示,具体表述如下。

?
入站数据流向:来自外界的数据包到达防火墙后,首先被
PREROUTING
链处理(是
否修改数据包地址等),然后进行路由选择(判断该数据包应发往何处);如果数据包的
目标地址是防火墙本机(如
Internet
用户访问网关的
Web
服务端口),那么内核将其传
递给
INPUT
链进行处理(决定是否允许通过等),通过以后再交给系统上层的应用程序
(如
httpd
服务器)进行响应。
?
转发数据流向:来自外界的数据包到达防火墙后,首先被
PREROUTING
链处理,然
后再进行路由选择;如果数据包的目标地址是其他外部地址(如局域网用户通过网关访
问
QQ
服务器),则内核将其传递给
FORWARD
链进行处理(允许转发或拦截、丢弃),
最后交给
POSTROUTING
链(是否修改数据包的地址等)进行处理。
?
出站数据流向:防火墙本机向外部地址发送的数据包(如在防火墙主机中测试公网
DNS
服务时),首先进行路由选择,确定了输出路径后,再经由
OUTPUT
链处理,最后再
交给
POSTROUTING
链(是否修改数据包的地址等)进行处理。
3
.规则链内部各条防火墙规则之间的顺序
当数据包经过每条规则链时,依次按第一条规则、第二条规则
……
的顺序进行匹配和处
理。链内的过滤遵循
“
匹配即停止
”
的原则,一旦找到一条相匹配的规则(使用
LOG
日志操
作的规则除外,
2.2.3
节会介绍),则不再检查本链内后续的其他规则。如果比对完整个链,
也找不到与数据包相匹配的规则,就按照该规则链的默认策略进行处理。
2.2
编写防火墙规则
本节主要介绍
netfilter
防火墙的管理工具
——iptables
命令的使用,包括基本的语法格
第
6
页共
14
页
式、数据包控制类型,以及如何管理、编写防火墙规则等。
2.2.1 iptables
的安装
CentOS 7.3
默认使用
firewalld
防火墙,如果想使用
iptables
防火墙,必须先关闭
firewalld
防火墙。
[root@oo ~]# systemctl stop firewalld.service
[root@oo ~]# systemctl disable firewalld.service
Firewalld
防火墙关闭之后,可以通过
yum
方式再安装
iptables
,因为默认
CentOS7.3
系统中并没有安装
iptables
,执行以下命令即可安装
iptables
。
[root@oo ~]# yum -y install iptables iptables-service
启动
iptables
防火墙并设置开机启动。
[root@oo ~]# systemctl start iptables.service
[root@oo ~]# systemctl enable iptables.service
Created symlink from /etc/systemd/system/basic.target.wants/iptables.service to /usr/lib/systemd/system/iptables.service.
[root@oo ~]#
2.2.2
基本语法、数据包控制类型
使用
iptables
命令管理、编写防火墙规则时,基本的命令格式如下所示。
iptables [-t
表名
]
管理选项
[
链名
] [
匹配条件
] [-j
控制类型
]
其中,表名、链名用来指定
iptables
命令所操作的表和链,未指定表名时将默认使用
filter
表;管理选项表示
iptables
规则的操作方式,如插入、增加、删除、查看等;匹配条件用来
第
7
页共
14
页
指定要处理的数据包的特征,不符合指定条件的数据包将不会处理;控制类型指的是数据包
的处理方式,如允许、拒绝、丢弃等。
对于防火墙,数据包的控制类型非常关键,直接关系到数据包的放行、封堵及做相应的
日志记录等。在
iptables
防火墙体系中,最常用的几种控制类型如下。
?
ACCEPT
:允许数据包通过。
?
DROP
:直接丢弃数据包,不给出任何回应信息。
?
REJECT
:拒绝数据包通过,必要时会给数据发送端一个响应信息。
?
LOG
:在
/var/log/messages
文件中记录日志信息,然后将数据包传递给下一条规则。
防火墙规则的
“
匹配即停止
”
对于
LOG
操作来说是一个特例,因为
LOG
只是一种辅助
动作,并没有真正处理数据包。
下面介绍一个防火墙规则操作示例:在
filter
表(
-t filter
)的
INPUT
链中插入(
-I
)一
条规则,拒绝(
-j REJECT
)发给本机的使用
ICMP
协议的数据包(
-p icmp
)。
[root@oo ~]# iptables -t filter -I INPUT -p icmp -j REJECT
上述操作产生的直接效果是其他主机无法
ping
通本机。
2.2.3
添加、查看、删除规则等基本操作
在熟练编写各种防火墙规则之前,首先需要掌握如何查看规则、添加规则、删除规则、
清空链内规则等基本操作。下面将介绍
iptables
命令中常用的几个管理选项,如表
2-1
所示。


其中,添加、删除、清空和查看规则是最常见的管理操作,下面通过一些规则操作示例
来展示相关选项的使用。
1
.添加新的规则
添加新的防火墙规则时,使用管理选项
“-A”
、
“-I”
,前者用来追加规则,后者用来插入规
则。例如,若要在
filter
表
INPUT
链的末尾添加一条防火墙规则,可以执行以下操作(其中
“-p
协议名
”
作为匹配条件)。
[root@oo ~]# iptables -t filter -A INPUT -p tcp -j ACCEPT
当使用管理选项
“-I”
时,允许同时指定新添加规则的顺序号,未指定序号时默认作为第
一条。例如,以下操作添加的两条规则将分别位于
filter
表的第一条、第二条(其中省略了
“-t
filter”
选项,默认使用
filter
表)。
[root@oo ~]# iptables -I INPUT -p udp -j ACCEPT
[root@oo ~]# iptables -I INPUT 2 -p icmp -j ACCEPT
[root@oo ~]#
2
.查看规则列表
查看已有的防火墙规则时,使用管理选项
“-L”
,结合
“--line-numbers”
选项还可显示各条
规则在链内的顺序号。例如,若要查看
filter
表
INPUT
链中的所有规则,并显示规则序号,
可以执行以下操作。
[root@oo ~]# iptables -L INPUT --line-numbers
Chain INPUT (policy ACCEPT)
num target prot opt source destination
1 ACCEPT udp -- anywhere anywhere
2 ACCEPT icmp -- anywhere anywhere
3 REJECT icmp -- anywhere anywhere reject-with icmp-port-unreachable
4 ACCEPT all -- anywhere anywhere state RELATED,ESTABLISHED
5 ACCEPT icmp -- anywhere anywhere
6 ACCEPT all -- anywhere anywhere
7 ACCEPT tcp -- anywhere anywhere state NEW tcp dpt:ssh
8 REJECT all -- anywhere anywhere reject-with icmp-host-prohibited
9 ACCEPT tcp -- anywhere anywhere
[root@oo ~]#
当防火墙规则的数量较多时,若能够以数字形式显示地址和端口信息,可以减少地址解
析的环节,在一定程度上加快命令执行的速度。例如,若要以数字地址形式查看
filter
表
INPUT
链中的所有规则,可以执行以下操作。
[root@oo ~]# iptables -n -L INPUT
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT udp -- 0.0.0.0/0 0.0.0.0/0
ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0
REJECT icmp -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-port-unreachable
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0
[root@oo ~]#
3
.删除、清空规则
删除一条防火墙规则时,使用管理选项
“-D”
。例如,若要删除
filter
表
INPUT
链中的第
三条规则,可以执行以下操作。
[root@oo ~]#
[root@oo ~]# iptables -D INPUT 3
[root@oo ~]# iptables -n -L INPUT
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT udp -- 0.0.0.0/0 0.0.0.0/0
ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0
[root@oo ~]#
清空指定链或表中的所有防火墙规则,使用管理选项
“-F”
。例如,若要清空
filter
表
INPUT
链中的所有规则,可以执行以下操作。
[root@oo ~]# iptables -F INPUT
[root@oo ~]# iptables -n -L INPUT
Chain INPUT (policy ACCEPT)
target prot opt source destination
[root@oo ~]#
4
.设置默认策略
iptables
的各条链中,默认策略是规则匹配的最后一个环节
——
当找不到任何一条能够
匹配数据包的规则时,则执行默认策略。默认策略的控制类型为
ACCEPT
(允许)、
DROP
(丢弃)两种。例如,执行以下操作可以将
filter
表中
FORWARD
链的默认策略设为丢弃,
OUTPUT
链的默认策略设为允许。
[root@oo ~]# iptables -t filter -P FORWARD DROP
[root@oo ~]# iptables -P OUTPUT ACCEPT
[root@oo ~]#
需要注意的是,当使用管理选项
“-F”
清空链时,默认策略不受影响。因此若要修改默认
策略,必须通过管理选项
“-P”
重新进行设置。另外,默认策略并不参与链内规则的顺序编排,
因此在其他规则之前或之后设置并无区别。
2.2.4
规则的匹配条件
在编写防火墙规则时,匹配条件的设置起着决定性的作用。只有清晰、准确地设置好匹
配条件,防火墙才知道要对符合什么条件的数据包进行处理,避免
“
误杀
”
。对于同一条防火
墙规则,可以指定多个匹配条件,表示这些条件必须都满足规则才会生效。根据数据包的各
种特征,结合
iptables
的模块结构,匹配条件的设置包括三大类:通用匹配、隐含匹配、显
式匹配。
1
.通用匹配
通用匹配也称为常规匹配,这种匹配方式可以独立使用,不依赖于其他条件或扩展模块。
常见的通用匹配包括协议匹配、地址匹配、网络接口匹配。
(
1
)协议匹配
编写
iptables
规则时使用
“-p
协议名
”
的形式指定,用来检查数据包所使用的网络协议
(
--protocol
),如
tcp
、
udp
、
icmp
和
all
(针对所有
IP
数据包)等,可用的协议类型存放于
Linux
系统的
/etc/procotols
文件中。例如,若要丢弃通过
icmp
协议访问防火墙本机的数据
包,允许转发经过防火墙的除
icmp
协议之外的数据包,可以执行以下操作。
[root@oo ~]# iptables -I INPUT -p icmp -j DROP
[root@oo ~]# iptables -A FORWARD ! -p icmp -j ACCEPT //感叹号”!”表示取反
[root@oo ~]#
(
2
)地址匹配
编写
iptables
规则时使用
“-s
源地址
”
或
“-d
目标地址
”
的形式指定,用来检查数据包的源
地址(
--source
)或目标地址(
--destination
)。
IP
地址、网段地址等都是可以接受的,但不
建议使用主机名、域名地址(解析过程会影响效率)。例如,若要拒绝转发源地址为
192.168.1.11
的数据,允许转发源地址位于
192.168.7.0/24
网段的数据,可以执行以下操
作。
[root@oo ~]# iptables -A FORWARD -s 192.168.1.11 -j REJECT
[root@oo ~]# iptables -A FORWARD -s 192.168.7.0/24 -j REJECT
[root@oo ~]#
当遇到小规模的网络扫描或攻击时,封锁
IP
地址是比较有效的方式。例如,若检测到
来自某个网段
(
如
10.20.30.0/24)
的频繁扫描、登录穷举等不良企图,可立即添加防火墙规则
进行封锁。
[root@oo ~]# iptables -I INPUT -s 10.20.30.0/24 -j DROP
[root@oo ~]# iptables -I FORWARD -s 10.20.30.0/24 -j DROP
(
3
)网络接口匹配
编写
iptables
规则时使用
“-i
接口名
”
和
“-o
接口名
”
的形式,用于检查数据包从防火墙的
哪一个接口进入或发出,分别对应入站网卡(
--in-interface
)、出站网卡(
--out-interface
)。
例如,若要丢弃从外网接口(
ens33
)访问防火墙本机且源地址为私有地址的数据包,可以
执行以下操作。
[root@oo ~]# iptables -A INPUT -i ens33 -s 10.0.0.0/8 -j DROP
[root@oo ~]# iptables -A INPUT -i ens33 -s 172.16.0.0/16 -j DROP
[root@oo ~]# iptables -A INPUT -i ens33 -s 192.168.0.0/16 -j DROP
2
.隐含匹配
这种匹配方式要求以指定的协议匹配作为前提条件,相当于子条件,因此无法独立使用,
其对应的功能由
iptables
在需要时自动(隐含)载入内核。常见的隐含匹配包括端口匹配、
TCP
标记匹配、
ICMP
类型匹配。
(
1
)端口匹配
编写
iptables
规则时使用
“--sport
源端口
”
或
“--dport
目标端口
”
的形式,针对的协议为
TCP
或
UDP
,用来检查数据包的源端口(
--source-port
)或目标端口(
--destination-port
)。
单个端口号或者以冒号
“:”
分隔的端口范围都是可以接受的,但不连续的多个端口不能采用这
种方式。例如,若要允许为网段
192.168.4.0/24
转发
DNS
查询数据包,可以执行以下操作。
[root@oo ~]# iptables -A FORWARD -s 192.168.4.0/24 -p udp --dport 53 -j ACCEPT
[root@oo ~]# iptables -A FORWARD -s 192.168.4.0/24 -p udp --sport 53 -j ACCEPT
[root@oo ~]#
再例如,构建
Vsftpd
服务器时,若要开放
20
、
21
端口,以及用于被动模式的端口范
围为
24500
~
24600
,可以参考以下操作设置防火墙规则。
[root@oo ~]# iptables -A INPUT -p tcp --dport 20:21 -j ACCEPT
[root@oo ~]# iptables -A INPUT -p tcp --dport 24500:24600 -j ACCEPT
(
2
)
ICMP
类型匹配
编写
iptables
规则时使用
“--icmp-type ICMP
类型
”
的形式,针对的协议为
ICMP
,用来
检查
ICMP
数据包的类型(
--icmp-type
)。
ICMP
类型使用字符串或数字代码表示,如
“Echo-Request”
(代码为
8
)、
“Echo-Reply”
(代码为
0
)、
“Destination-Unreachable”
(代
码为
3
),分别对应
ICMP
协议的请求、回显、目标不可达。例如,若要禁止从其他主机
ping
本机,但是允许本机
ping
其他主机,可以执行以下操作。
[root@oo ~]# iptables -A INPUT -p icmp --icmp-type 8 -j DROP
[root@oo ~]# iptables -A INPUT -p icmp --icmp-type 0 -j ACCEPT
[root@oo ~]# iptables -A INPUT -p icmp --icmp-type 3 -j ACCEPT
[root@oo ~]# iptables -A INPUT -p icmp -j DROP
[root@oo ~]#
关于可用的
ICMP
协议类型,可以执行
“iptables -p icmp -h”
命令,在帮助信息的最后部
分列出了所有支持的类型。
[root@oo ~]# iptables -p icmp -h
iptables v1.4.21
Usage: iptables -[ACD] chain rule-specification [options]
iptables -I chain [rulenum] rule-specification [options]
iptables -R chain rulenum rule-specification [options]
iptables -D chain rulenum [options]
iptables -[LS] [chain [rulenum]] [options]
iptables -[FZ] [chain] [options]
iptables -[NX] chain
iptables -E old-chain-name new-chain-name
iptables -P chain target [options]
iptables -h (print this help information)
Commands:
Either long or short options are allowed.
3
.显式匹配
这种匹配方式要求有额外的内核模块提供支持,必须手动以
“-m
模块名称
”
的形式调用
相应的模块,然后方可设置匹配条件。添加了带显式匹配条件的规则以后,可以执行
“lsmod
| grep xt_”
命令查看到相关的内核扩展模块(如
xt_multiport
、
xt_iprange
、
xt_mac
、
xt_state
)。
常见的显式匹配包括多端口匹配、
IP
范围匹配、
MAC
地址匹配、状态匹配。
(
1
)多端口匹配
编写
iptables
规则时使用
“-m multiport --dports
端口列表
”
、
“-m multiport --sports
端口
列表
”
的形式,用来检查数据包的源端口、目标端口,多个端口之间以逗号进行分隔。例如,
若要允许本机开放
25
、
80
、
110
、
143
端口,以便提供电子邮件服务,可以执行以下操作。
[root@oo ~]# iptables -A INPUT -p tcp -m multiport --dport 25,80,110,143 -j ACCEPT
(
2
)
IP
范围匹配
编写
iptables
规则时使用
“-m iprange --src-range IP
范围
”
、
“-m iprange --dst-range IP
范围
”
的形式,用来检查数据包的源地址、目标地址,其中
IP
范围采用
“
起始地址
-
结束地址
”
第
13
页共
14
页
的形式表示。例如,若要禁止转发源
IP
地址位于
192.168.4.21
与
192.168.4.28
之间的
TCP
数据包,可以执行以下操作。
[root@oo ~]# iptables -A FORWARD -p tcp -m iprange --src-range 192.168.4.21-192.168.4.28 -j DROP
[root@oo ~]#
(
3
)
MAC
地址匹配
编写
iptables
规则时使用
“-m mac --mac-source MAC
地址
”
的形式,用来检查数据包的
源
MAC
地址。由于
MAC
地址本身的局限性,此类匹配条件一般只适用于内部网络。例如,
若要根据
MAC
地址封锁主机,禁止其访问本机的任何应用,可以参考以下操作。
[root@oo ~]# iptables -A INPUT -m mac --mac-source 00:0c:29:7e:ab:51 -j DROP
(
4
)状态匹配
编写
iptables
规则时使用
“-m state --state
连接状态
”
的形式,基于
iptables
的状态跟踪
机制用来检查数据包的连接状态(
State
)。常见的连接状态包括
NEW
(与任何连接无关的)、
ESTABLISHED
(响应请求或者已建立连接的)和
RELATED
(与已有连接有相关性的,如
FTP
数据连接)。例如,若要禁止转发与正常
TCP
连接无关的非
--syn
请求数据包(如伪造
的网络攻击数据包),可以执行以下操作。
[root@oo ~]# iptables -A FORWARD -m state --state NEW -p tcp ! --syn -j DROP
[root@oo ~]#
再例如,若只开放本机的
Web
服务(
80
端口),但对发给本机的
TCP
应答数据包予以
放行,其他入站数据包均丢弃,则对应的入站控制规则可参考以下操作。
[root@oo ~]# iptables -I INPUT -p tcp -m multiport --dport 80 -j ACCEPT
[root@oo ~]# iptables -I INPUT -p tcp -m state --state ESTABLISHED -j ACCEPT
[root@oo ~]# iptables -P INPUT DROP
最后看一下我们配置的INPUT表
[root@oo ~]# iptables -n -L INPUT
Chain INPUT (policy DROP)
target prot opt source destination
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state ESTABLISHED
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 multiport dports 80
DROP all -- 10.20.30.0/24 0.0.0.0/0
DROP icmp -- 0.0.0.0/0 0.0.0.0/0
DROP all -- 10.0.0.0/8 0.0.0.0/0
DROP all -- 172.16.0.0/16 0.0.0.0/0
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpts:20:21
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpts:24500:24600
DROP icmp -- 0.0.0.0/0 0.0.0.0/0 icmptype 8
ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 icmptype 0
ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 icmptype 3
DROP icmp -- 0.0.0.0/0 0.0.0.0/0
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 multiport dports 25,80,110,143
文章来源:https://blog.csdn.net/ZXDNM_zwz/article/details/135264611
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
最新文章
- Python教程
- 深入理解 MySQL 中的 HAVING 关键字和聚合函数
- Qt之QChar编码(1)
- MyBatis入门基础篇
- 用Python脚本实现FFmpeg批量转换
- Pytest成魔之路 —— fixture 之大解剖!
- 2023年度最热 AI 应用 TOP 50,除了 ChatGPT 还有这么多宝藏
- [笔记]深度学习入门 基于Python的理论与实现(一)
- 云原生Kubernetes:K8S集群版本升级(v1.22.14 - v1.23.14)
- 东郊到家模式,东郊到家小程序app功能优势
- 四款坚固耐用、小尺寸、1EDB9275F、1EDS5663H、1EDN9550B、1EDN7512G单通道栅极驱动器IC
- @DependsOn:解析 Spring 中的依赖关系之艺术
- djangoee家教管理系统(程序+开题报告)
- 编译原理 SLR(1)分析技术识别字符串
- React Hooks 使用 Fabric.js