openssl3.2 - 官方demo学习 - cms - cms_ver.c
发布时间:2024年01月13日
openssl3.2 - 官方demo学习 - cms - cms_ver.c
概述
CMS验签, 将单独签名和联合签名出来的签名文件都试试.
验签成功后, 将签名数据明文写入了文件供查看.
也就是说, 只有验签成功后, 才能看到签名数据的明文.
验签时, 使用的是上一级的证书(这里是CA证书)
签名时, 使用的是低级证书(接收者证书, 或者说是签名者证书, 这些证书都是CA证书发出来的)
运行结果
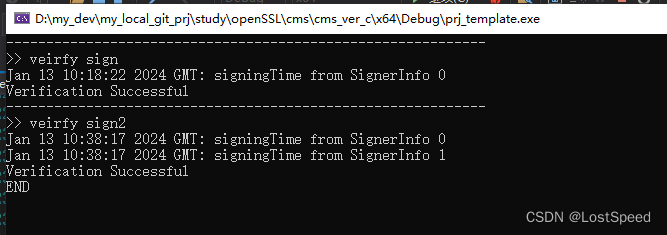
不管是单独签名, 还是联合签名, 验签都是一个API搞定.
笔记
/*!
\file cms_ver.c
\note openssl3.2 - 官方demo学习 - cms - cms_ver.c
CMS验签, 将单独签名和联合签名出来的签名文件都试试.
验签成功后, 将签名数据明文写入了文件供查看.
也就是说, 只有验签成功后, 才能看到签名数据的明文.
验签时, 使用的是上一级的证书(这里是CA证书)
签名时, 使用的是低级证书(接收者证书)
*/
/*
* Copyright 2008-2023 The OpenSSL Project Authors. All Rights Reserved.
*
* Licensed under the Apache License 2.0 (the "License"). You may not use
* this file except in compliance with the License. You can obtain a copy
* in the file LICENSE in the source distribution or at
* https://www.openssl.org/source/license.html
*/
/* Simple S/MIME verification example */
#include <openssl/pem.h>
#include <openssl/cms.h>
#include <openssl/err.h>
#include "my_openSSL_lib.h"
/*
* print any signingTime attributes.
* signingTime is when each party purportedly signed the message.
*/
static void print_signingTime(CMS_ContentInfo *cms)
{
STACK_OF(CMS_SignerInfo) *sis;
CMS_SignerInfo *si;
X509_ATTRIBUTE *attr;
ASN1_TYPE *t;
ASN1_UTCTIME *utctime;
ASN1_GENERALIZEDTIME *gtime;
BIO *b;
int i, loc;
int iSignCnt = 0;
b = BIO_new_fp(stdout, BIO_NOCLOSE | BIO_FP_TEXT);
sis = CMS_get0_SignerInfos(cms);
iSignCnt = sk_CMS_SignerInfo_num(sis);
for (i = 0; i < iSignCnt; i++) {
si = sk_CMS_SignerInfo_value(sis, i);
loc = CMS_signed_get_attr_by_NID(si, NID_pkcs9_signingTime, -1);
attr = CMS_signed_get_attr(si, loc);
t = X509_ATTRIBUTE_get0_type(attr, 0);
if (t == NULL)
continue;
switch (t->type) {
case V_ASN1_UTCTIME:
utctime = t->value.utctime;
ASN1_UTCTIME_print(b, utctime);
break;
case V_ASN1_GENERALIZEDTIME:
gtime = t->value.generalizedtime;
ASN1_GENERALIZEDTIME_print(b, gtime);
break;
default:
fprintf(stderr, "unrecognized signingTime type\n");
break;
}
BIO_printf(b, ": signingTime from SignerInfo %i\n", i);
}
BIO_free(b);
return;
}
int verify_sign()
{
BIO* in = NULL, * out = NULL, * tbio = NULL, * cont = NULL;
X509_STORE* st = NULL;
X509* cacert = NULL;
CMS_ContentInfo* cms = NULL;
int ret = EXIT_FAILURE;
//OpenSSL_add_all_algorithms();
//ERR_load_crypto_strings();
/* Set up trusted CA certificate store */
st = X509_STORE_new();
if (st == NULL)
goto err;
/* Read in CA certificate */
tbio = BIO_new_file("cacert.pem", "r");
if (tbio == NULL)
goto err;
cacert = PEM_read_bio_X509(tbio, NULL, 0, NULL);
if (cacert == NULL)
goto err;
if (!X509_STORE_add_cert(st, cacert))
goto err;
/* Open message being verified */
in = BIO_new_file("smout.txt", "r");
if (in == NULL)
goto err;
/* parse message */
cms = SMIME_read_CMS(in, &cont);
if (cms == NULL)
goto err;
print_signingTime(cms);
/* File to output verified content to */
out = BIO_new_file("smver.txt", "w");
if (out == NULL)
goto err;
if (!CMS_verify(cms, NULL, st, cont, out, 0)) {
fprintf(stderr, "Verification Failure\n");
goto err;
}
printf("Verification Successful\n");
ret = EXIT_SUCCESS;
err:
if (ret != EXIT_SUCCESS) {
fprintf(stderr, "Error Verifying Data\n");
ERR_print_errors_fp(stderr);
}
X509_STORE_free(st);
CMS_ContentInfo_free(cms);
X509_free(cacert);
BIO_free(in);
BIO_free(out);
BIO_free(tbio);
return ret;
}
int verify_sign2()
{
BIO* in = NULL, * out = NULL, * tbio = NULL, * cont = NULL;
X509_STORE* st = NULL;
X509* cacert = NULL;
CMS_ContentInfo* cms = NULL;
int ret = EXIT_FAILURE;
//OpenSSL_add_all_algorithms();
//ERR_load_crypto_strings();
/* Set up trusted CA certificate store */
st = X509_STORE_new();
if (st == NULL)
goto err;
/* Read in CA certificate */
tbio = BIO_new_file("cacert.pem", "r");
if (tbio == NULL)
goto err;
cacert = PEM_read_bio_X509(tbio, NULL, 0, NULL);
if (cacert == NULL)
goto err;
if (!X509_STORE_add_cert(st, cacert))
goto err;
/* Open message being verified */
in = BIO_new_file("smout2.txt", "r");
if (in == NULL)
goto err;
/* parse message */
cms = SMIME_read_CMS(in, &cont);
if (cms == NULL)
goto err;
print_signingTime(cms);
/* File to output verified content to */
out = BIO_new_file("smver2.txt", "w");
if (out == NULL)
goto err;
if (!CMS_verify(cms, NULL, st, cont, out, 0)) {
fprintf(stderr, "Verification Failure\n");
goto err;
}
printf("Verification Successful\n");
ret = EXIT_SUCCESS;
err:
if (ret != EXIT_SUCCESS) {
fprintf(stderr, "Error Verifying Data\n");
ERR_print_errors_fp(stderr);
}
X509_STORE_free(st);
CMS_ContentInfo_free(cms);
X509_free(cacert);
BIO_free(in);
BIO_free(out);
BIO_free(tbio);
return ret;
}
#define LINE10 "----------"
#define LINE60 LINE10 LINE10 LINE10 LINE10 LINE10 LINE10
int main(int argc, char **argv)
{
OpenSSL_add_all_algorithms();
ERR_load_crypto_strings();
printf("%s\n", LINE60);
printf(">> veirfy sign\n");
if (EXIT_SUCCESS != verify_sign())
{
return -1;
}
printf("%s\n", LINE60);
printf(">> veirfy sign2\n");
if (EXIT_SUCCESS != verify_sign2())
{
return -1;
}
printf("END\n");
return 0;
}
END
文章来源:https://blog.csdn.net/LostSpeed/article/details/135574320
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
最新文章
- Python教程
- 深入理解 MySQL 中的 HAVING 关键字和聚合函数
- Qt之QChar编码(1)
- MyBatis入门基础篇
- 用Python脚本实现FFmpeg批量转换
- 【深度学习:LSTM Networks】了解 LSTM 网络
- ElementUI中修改el-table的滚动条样式
- PHP知识点复习
- “寻龙量化”,寻龙诀AI量化系统套装,实时监测游资与主力资金动向
- 面试题:从 MySQL 读取 100w 数据进行处理,应该怎么做?
- 新闻稿件发稿:新闻稿的5大长远意义
- 芯知识 | WT588F02B语音芯片IC支持用户自行更换语音内容的应用优势介绍
- 常见的6种软件测试用例设计方法
- NOIP2018提高组day2 - T1:旅行
- rime中州韵 weasel.custom.yaml 配置 之 配色方案