[RoarCTF2019] TankGame
发布时间:2023年12月28日
不多说,用dnspy反编译data文件夹中的Assembly-CSharp文件
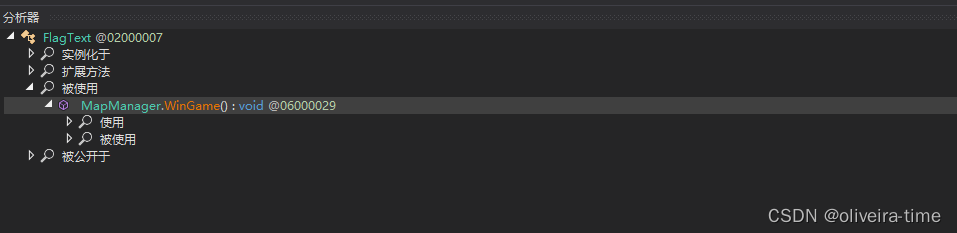
使用分析器分析一下可疑的FlagText 发现其在WinGame中被调用,跟进WinGame函数
public static void WinGame()
{
if (!MapManager.winGame && (MapManager.nDestroyNum == 4 || MapManager.nDestroyNum == 5))
{
string text = "clearlove9";
for (int i = 0; i < 21; i++)
{
for (int j = 0; j < 17; j++)
{
text += MapManager.MapState[i, j].ToString();
}
}
string a = MapManager.Sha1(text);
if (a == "3F649F708AAFA7A0A94138DC3022F6EA611E8D01")
{
FlagText._instance.gameObject.SetActive(true);
FlagText.str = "RoarCTF{wm-" + MapManager.Md5(text) + "}";
MapManager.winGame = true;
}
}
}拿flag逻辑很简单,如果被摧毁的方块数为4或5且此时游戏没有结束,那么遍历21x17的某数组尽数加入某字符串。判断sha1(“clearlove9”+mapstate)是否为指定值,如果是则flag为"RoarCTF{wm-" + MapManager.Md5(text) + "}",这个md5是“clearlove9”+mapdata的md5的前十个字符。
MapState为游戏当前的地图数据,观察游戏初始时的地图数据(21x17)和我们游戏地图相比对得出:
?
8 空的
1 砖头
4 水
5 草
2 钢铁
0 家(炸了之后就是9)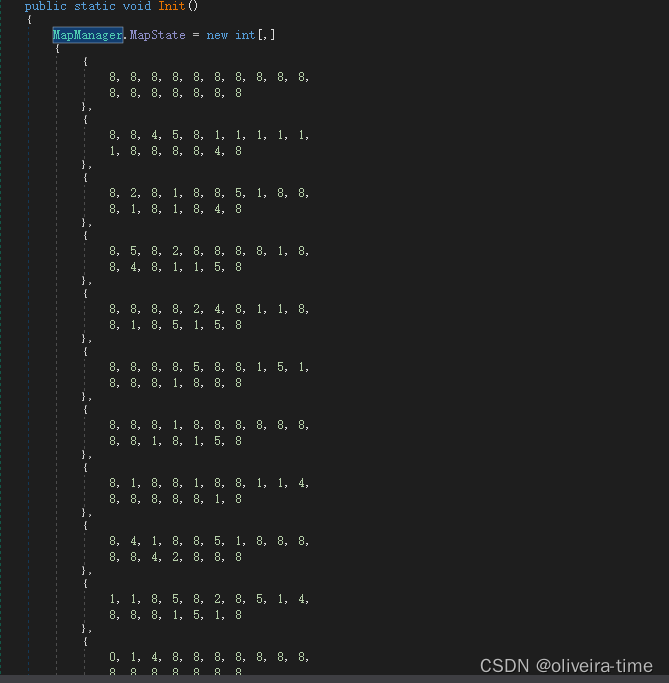
 ?其中只有砖头和家可以打碎,打碎后砖头变成空(1)家打碎了就gg了。接下来写脚本遍历所有情况即可(python2环境下运行,python3 hashlib的要求不同,该脚本会报错)。
?其中只有砖头和家可以打碎,打碎后砖头变成空(1)家打碎了就gg了。接下来写脚本遍历所有情况即可(python2环境下运行,python3 hashlib的要求不同,该脚本会报错)。
import hashlib
data = [
[8, 8, 8, 8, 8, 8, 8, 8, 8, 8, 8, 8, 8, 8, 8, 8, 8],
[8, 8, 4, 5, 8, 1, 1, 1, 1, 1, 1, 8, 8, 8, 8, 4, 8],
[8, 2, 8, 1, 8, 8, 5, 1, 8, 8, 8, 1, 8, 1, 8, 4, 8],
[8, 5, 8, 2, 8, 8, 8, 8, 1, 8, 8, 4, 8, 1, 1, 5, 8],
[8, 8, 8, 8, 2, 4, 8, 1, 1, 8, 8, 1, 8, 5, 1, 5, 8],
[8, 8, 8, 8, 5, 8, 8, 1, 5, 1, 8, 8, 8, 1, 8, 8, 8],
[8, 8, 8, 1, 8, 8, 8, 8, 8, 8, 8, 8, 1, 8, 1, 5, 8],
[8, 1, 8, 8, 1, 8, 8, 1, 1, 4, 8, 8, 8, 8, 8, 1, 8],
[8, 4, 1, 8, 8, 5, 1, 8, 8, 8, 8, 8, 4, 2, 8, 8, 8],
[1, 1, 8, 5, 8, 2, 8, 5, 1, 4, 8, 8, 8, 1, 5, 1, 8],
[9, 1, 4, 8, 8, 8, 8, 8, 8, 8, 8, 8, 8, 8, 8, 8, 8],
[1, 1, 8, 1, 8, 8, 2, 1, 8, 8, 5, 2, 1, 8, 8, 8, 8],
[8, 8, 8, 8, 4, 8, 8, 2, 1, 1, 8, 2, 1, 8, 1, 8, 8],
[8, 1, 1, 8, 8, 4, 4, 1, 8, 4, 2, 4, 8, 4, 8, 8, 8],
[8, 4, 8, 8, 1, 2, 8, 8, 8, 8, 1, 8, 8, 1, 8, 1, 8],
[8, 1, 1, 5, 8, 8, 8, 8, 8, 8, 8, 8, 1, 8, 8, 8, 8],
[8, 8, 1, 1, 5, 2, 8, 8, 8, 8, 8, 8, 8, 8, 2, 8, 8],
[8, 8, 4, 8, 1, 8, 2, 8, 1, 5, 8, 8, 4, 8, 8, 8, 8],
[8, 8, 2, 8, 1, 8, 8, 1, 8, 8, 1, 8, 2, 2, 5, 8, 8],
[8, 2, 1, 8, 8, 8, 8, 2, 8, 4, 5, 8, 1, 1, 2, 5, 8],
[8, 8, 8, 8, 8, 8, 8, 8, 8, 8, 8, 8, 8, 8, 8, 8, 8]
]
text = ''
for i in range(21):
for j in range(17):
text += str(data[i][j])
text = list(text)
def work(data,index,num):
if num == 3:
temp=''.join(data)
if hashlib.sha1('clearlove9'+temp).hexdigest() == '3f649f708aafa7a0a94138dc3022f6ea611e8d01':
key=hashlib.md5('clearlove9'+temp).hexdigest().upper()[:10]
flag="RoarCTF{wm-"+key+"}"
print(flag)
return
if index == 21*17:
return
if data[index] =='1':
temp=list(data)
temp[index]='8'
work(temp,index+1,num+1)
work(data,index+1,num)
if __name__ == "__main__":
work(text,0,0)
文章来源:https://blog.csdn.net/m0_52484587/article/details/135275421
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
最新文章
- Python教程
- 深入理解 MySQL 中的 HAVING 关键字和聚合函数
- Qt之QChar编码(1)
- MyBatis入门基础篇
- 用Python脚本实现FFmpeg批量转换
- 回溯法:回溯法通用模版以及模版应用
- 设计模式——解释器模式
- MySQL DDL DML DQL DCL 通用语法
- 超声波清洗机买哪款?哪款超声波清洗机最值得入手?一篇教会你选
- 宋仕强论道之华强北山寨手机(三十)
- 如何设计销售人员的薪酬结构
- 洁净室洁净度如何快速计算?附详细计算公式
- Xpath的问题:为什么在DOM中确定存在(可见)的元素,用//表达式匹配不到(附解决办法)
- 便携式储能有什么优点?MOS该如何选型?
- K8S学习指南(23)-k8s核心对象Ingress