【攻防世界】Reverse——bad_python writeup
发布时间:2024年01月08日
pyc 文件是 Python 在解释执行源代码时生成的一种字节码文件,它包含了源代码的编译结果和相关的元数据信息,以便于 Python 可以更快地加载和执行代码。
可以使用uncompyle把pyc还原成py:
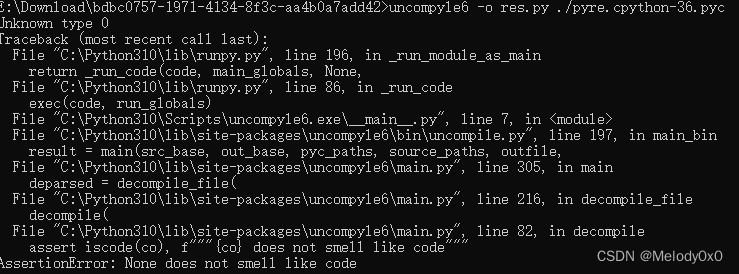
发现无法编译成功,结合题目名字bad_python和cpython-36.pyc, 猜测是用python3.6编译的,但是头部被损坏导致uncompyle无法解析。
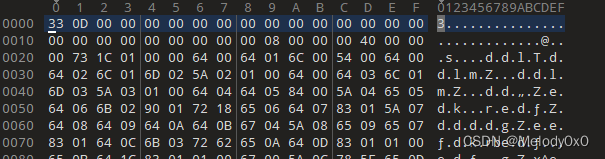
而正常的用python3.6编译的pyc文件的头是这样的:

复制正常文件的头到pyre-cpython-36.pyc,就可以成功编译了。得到如下代码:
# uncompyle6 version 3.9.0
# Python bytecode version base 3.6 (3379)
# Decompiled from: Python 3.6.2 |Continuum Analytics, Inc.| (default, Jul 20 2017, 12:30:02) [MSC v.1900 64 bit (AMD64)]
# Embedded file name: pyre.py
# Compiled at: 2024-01-05 10:16:56
# Size of source mod 2**32: 52 bytes
from ctypes import *
from Crypto.Util.number import bytes_to_long
from Crypto.Util.number import long_to_bytes
def encrypt(v, k):
v0 = c_uint32(v[0])
v1 = c_uint32(v[1])
sum1 = c_uint32(0)
delta = 195935983
for i in range(32):
v0.value += (v1.value << 4 ^ v1.value >> 7) + v1.value ^ sum1.value + k[sum1.value & 3]
sum1.value += delta
v1.value += (v0.value << 4 ^ v0.value >> 7) + v0.value ^ sum1.value + k[sum1.value >> 9 & 3]
return (
v0.value, v1.value)
if __name__ == '__main__':
flag = input('please input your flag:')
k = [255, 187, 51, 68]
if len(flag) != 32:
print('wrong!')
exit(-1)
a = []
for i in range(0, 32, 8):
v1 = bytes_to_long(bytes(flag[i:i + 4], 'ascii'))
v2 = bytes_to_long(bytes(flag[i + 4:i + 8], 'ascii'))
a += encrypt([v1, v2], k)
enc = [
'4006073346', '2582197823', '2235293281', '558171287', '2425328816',
'1715140098', '986348143', '1948615354']
for i in range(8):
if enc[i] != a[i]:
print('wrong!')
exit(-1)
print('flag is flag{%s}' % flag)使用下面的代码得到flag
from ctypes import *
def decrypt(v, k):
v0 = c_uint32(v[0])
v1 = c_uint32(v[1])
sum1 = c_uint32(0)
delta = 195935983
sum1.value = delta * 32
for i in range(32):
v1.value -= (v0.value << 4 ^ v0.value >> 7) + v0.value ^ sum1.value + k[sum1.value >> 9 & 3]
sum1.value -= delta
v0.value -= (v1.value << 4 ^ v1.value >> 7) + v1.value ^ sum1.value + k[sum1.value & 3]
return (
v0.value, v1.value)
if __name__ == '__main__':
k = [255, 187, 51, 68]
dec = []
for i in range(0,8,2):
enc = [4006073346, 2582197823, 2235293281, 558171287,
2425328816, 1715140098, 986348143, 1948615354]
dec+=decrypt([enc[i], enc[i + 1]], k)
print(dec)
byte_array = bytearray()
for i in range(0, 8):
num = dec[i]
for i in range(4):
byte = num >> (8*(3-i)) & 0xff
byte_array.append(byte)
flag = ''.join([chr(x) for x in byte_array])
print("flag{"+flag+"}")
文章来源:https://blog.csdn.net/2301_77295404/article/details/135402683
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
最新文章
- Python教程
- 深入理解 MySQL 中的 HAVING 关键字和聚合函数
- Qt之QChar编码(1)
- MyBatis入门基础篇
- 用Python脚本实现FFmpeg批量转换
- 概率论基础知识补充
- 【教学类-综合练习-09】20240105 大4班 综合材料(美术类:骰子、面具、AB手环)
- 基于Java版本与鸿鹄企业电子招投标系统的二次开发实践-鸿鹄企业电子招投标系统源代码+支持二开+鸿鹄电子招投标系统
- 九州金榜如何高质量培养孩子成长
- qml实现动态轮播图
- 融资项目——全局统一日志说明
- 被辞退了,因为小数点计算错误
- 应用案例——楼宇对讲、可视门铃芯片组成分析
- 给定一个整数数组和一个整数目标值,在该数组中找出和为目标值的那两个整数,并返回它们的数组下标。(找到一个就返回)
- YOLOv8算法改进【NO.98】改进损失函数为最新提出的Shape-IoU