C++ 输入用户名和密码 防止注入攻击
发布时间:2024年01月14日
1、问题解释:注入攻击?,无密码直接登录数据库
可视化展示
1.1、当你的数据库为:其中包含三个字段id user 以及md5密码
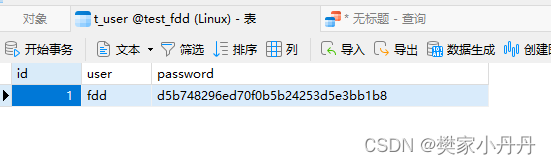
?1.2、在使用C++堆数据库信息进行访问的时候,使用多条语句进行查询
string sql = "select id from t_user where user='";
sql += username;
sql += "' and password =md5('";
sql += password;
sql += "')";
cout << sql << endl;1.3、sql语句最终输出为,展示数据库如下。
select id from t_user where user='fdd' and password =md5('990107Wjl@')
1.4、那么如果一些人想要违法查看你的数据,他们直接插入语句,生成一个密码
select md5(1);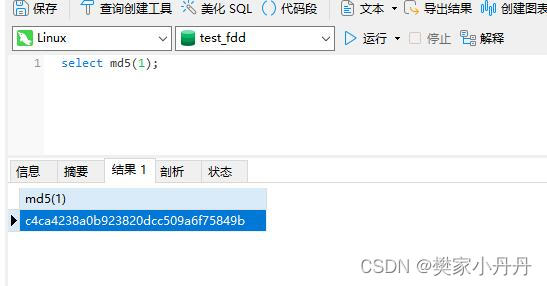
1.5、在C++编程中,输入如下代码,就可以查看你的数据库的任意信息,所以说是很危险的。
select id from t_user where user = '1'or '1'='1' and password = md5('1') or'c4ca4238a0b923820dcc509a6f75849b'=md5('1');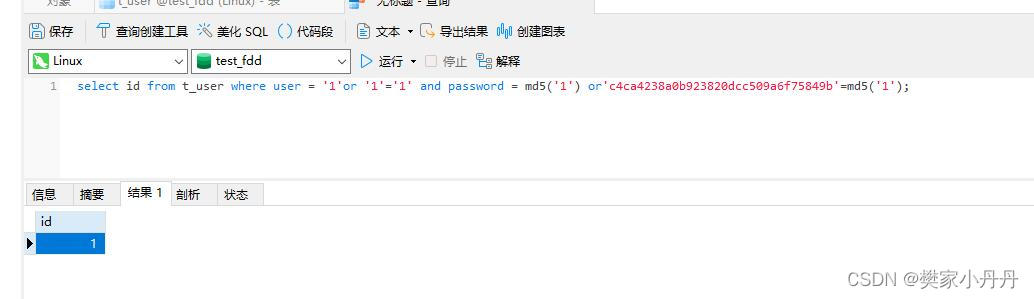
?在Linux下,也攻击成功了,十分危险
input password : ***********************************************select id from t_user where user = '1' or '1' = '1' and password = md5('1') or 'c4ca4238a0b923820dcc509a6f75849b' = md5('1')
? ? ? ? ? ? login success!

?2、解决思路
? ? ? ? 2.1、解决1:使用独立用户,设定权限,限制用户的权限,不用root用户,只给只读权限
? ? ? ? 2.2、解决2:用预处理语句(比较麻烦stmt)
? ? ? ? 2.3检查用户的输入? ?
3、本博客主要讲解第三种方法:检查用户的输入
3.1、从如下代码可以查看
select id from t_user where user = '1'or '1'='1' and password = md5('1') or'c4ca4238a0b923820dcc509a6f75849b'=md5('1');?username=1'or'1'='1
?password= 1') or'c4ca4238a0b923820dcc509a6f75849b'=md5('1
发现攻击密码包含引号,等于号以及括号,所以解决的话就不可以有'',不可以有= 不可以有)
3.2、写一个函数,检查用户的输入
//用于检查用户的输入 false不安全。 true表示安全
bool XClient::CheckInput(const std::string& in)
{
//限定不允许出现的字符
string str = "'\"()";
for (char a : str)
{
//size_t 类型表示C中任何对象所能达到的最大长度,它是无符号整数。
size_t found = in.find(a);
//输入字符in是否可以在a中被找到
//如果字符串不存在包含关系,那么返回值就一定是npos
if (found != string::npos)//发现违规字符
{
return false;
}
}
return true;
} if (!CheckInput(password) || !CheckInput(username))
{
//输入是危险的
cerr << "Injection attacks!!!! Inout password or username dangerous!!" << endl;
continue;
}?4、测试:Linux
直接输出注入攻击错误
input username:1'or'1'='1
input password:***********************************************Injection attacks!!!! Inout password or username dangerous!!

完结花花
文章来源:https://blog.csdn.net/wjl990316fddwjl/article/details/135582715
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
最新文章
- Python教程
- 深入理解 MySQL 中的 HAVING 关键字和聚合函数
- Qt之QChar编码(1)
- MyBatis入门基础篇
- 用Python脚本实现FFmpeg批量转换
- 边缘计算:挑战与机遇并存
- 余震强度预测能力升级,Nature 刊文认证基于神经网络的模型性能优于传统模型
- Docker实战06|深入剖析Docker Run命令
- 第四章 Qt 常用按钮组件
- 2024年可能会用到的几个地图可视化模板
- 遥感技术应用于作物类型种植面积估算实例
- 53_最大子数组和
- 在阿里巴巴,平台赋予你的能力,并不是你的能力
- 电脑屏幕一直闪烁怎么解决?三大妙招还你清晰视野
- AI全栈大模型工程师(二十)SKvs.LangChain