华为防火墙双机热备
实验需求:
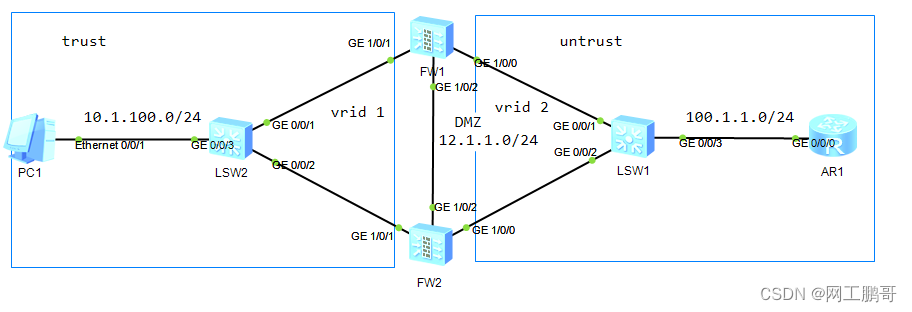
如图所示,PC1为公司内部网络设备,AR1为出口设备,在FW1和FW2上配置双机热备,当网络正常时PC1访问AR1路径为FW1-AR1,当FW1出现故障后,切换路径为FW2-AR1。
实现目的:
了解防火墙双机热备的配置
实验步骤:
1、配置ip地址
FW1:
interface GigabitEthernet1/0/1
ip address 10.1.100.1 255.255.255.0
interface GigabitEthernet1/0/0
ip address 100.1.1.1 255.255.255.0
interface GigabitEthernet1/0/2
ip address 12.1.1.1 255.255.255.0
FW2:
interface GigabitEthernet1/0/1
?ip address 10.1.100.2 255.255.255.0
interface GigabitEthernet1/0/0
?ip address 100.1.1.2 255.255.255.0
interface GigabitEthernet1/0/2
ip address 12.1.1.2 255.255.255.0
AR1:
interface GigabitEthernet0/0/0
?ip address 100.1.1.3 255.255.255.0
interface LoopBack0
?ip address 1.1.1.1 255.255.255.255
2、将接口加入安全区域
FW1:
firewall zone trust
add interface GigabitEthernet1/0/1
firewall zone untrust
?add interface GigabitEthernet1/0/0
firewall zone dmz
?add interface GigabitEthernet1/0/2
FW2:
firewall zone trust
add interface GigabitEthernet1/0/1
firewall zone untrust
?add interface GigabitEthernet1/0/0
firewall zone dmz
?add interface GigabitEthernet1/0/2
3、配置静态路由,实现AR1和PC的互通。
FW1:
ip route-static 1.1.1.1 32 100.1.1.3
FW2:
ip route-static 1.1.1.1 32 100.1.1.3
AR1:
IP route-static 10.1.100.0 24 100.1.1.254 //AR1访问内部PC的下一跳为vrrp vrid2的虚拟ip
4、配置VRRP,将FW1设置为主设备,FW2设置为备用设备。
FW1:
interface GigabitEthernet1/0/1
vrrp vrid 1 virtual-ip 10.1.100.254 active
interface GigabitEthernet1/0/0
vrrp vrid 2 virtual-ip 100.1.1.254 active
FW2:
interface GigabitEthernet1/0/1
vrrp vrid 1 virtual-ip 10.1.100.254 standby
interface GigabitEthernet1/0/0
vrrp vrid 2 virtual-ip 100.1.1.254 standby
4、配置安全策略,允许心跳接口之间交互HRP报文。
FW1:
security-policy
?rule name local_dmz
? source-zone dmz
? source-zone local
? destination-zone dmz
? destination-zone local
? service protocol udp destination-port 18514 //放行hrp报文,目的端口为udp 18514
? action permit
FW2:
security-policy
?rule name local_dmz
? source-zone dmz
? source-zone local
? destination-zone dmz
? destination-zone local
? service protocol udp destination-port 18514
? action permit
5、配置HRP(配置HRP的目的是为了实现主设备故障后,备用设备能够平滑接替主设备的工作)
FW1:
hrp? interface G1/0/2 remote 12.1.1.2
hrp enable
FW2:
hrp? interface g1/0/2 remote 12.1.1.1
hrp enable
在FW1上查看HRP的状态:
HRP_M[FW1]display? hrp?? state
Role: active, peer: standby //此处表示本设备状态为主,邻居为备用设备
?Running priority: 45000, peer: 45000
?Backup channel usage: 0.00%
?Stable time: 0 days, 0 hours, 6 minutes
?Last state change information: 2023-03-28 7:13:26 HRP link changes to up.
查看FW1的VRRP状态。
HRP_M[FW1]display vrrp brief?
2023-03-28 07:23:32.950
Total:2???? Master:2???? Backup:0???? Non-active:0?????
VRID? State??????? Interface??????????????? Type???? Virtual IP????
----------------------------------------------------------------
1???? Master?????? GE1/0/1????????????????? Vgmp???? 10.1.100.254??
2???? Master?????? GE1/0/0????????????????? Vgmp???? 100.1.1.254?
?通过以上输出,可知FW1的上下行接口都为vrrp的主设备。
6、配置放行PC访问AR1流量的安全策略
FW1:
security-policy
rule name trust_untrust
? source-zone trust
? destination-zone untrust
? action permit
在FW1上配置了安全策略,设备会自动通过HRP将对应的安全策略配置同步到备用设备上。
在FW2查看设备的安全策略:
HRP_S[FW2]display? security-policy rule? name trust_untrust
2023-03-28 07:25:17.240
?(0 times matched)
?rule name trust_untrust
? source-zone trust
? destination-zone untrust
? action permit
通过以上输出,可以得知FW2通过HRP自动备份了FW1的安全策略。
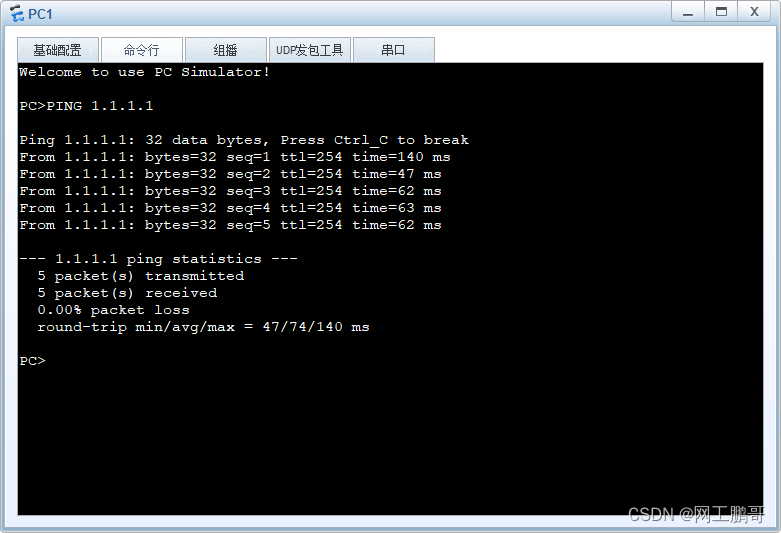
7、测试(使用PC1访问AR1的环回口)
查看FW1的会话表:
HRP_M[FW1]display? firewall session table?
2023-03-28 07:26:30.340
?Current Total Sessions : 8
?icmp? VPN: public --> public? 10.1.100.100:20121 --> 1.1.1.1:2048
?udp? VPN: public --> public? 12.1.1.2:16384 --> 12.1.1.1:18514
?udp? VPN: public --> public? 12.1.1.1:49152 --> 12.1.1.2:18514
?icmp? VPN: public --> public? 10.1.100.100:19353 --> 1.1.1.1:2048
?icmp? VPN: public --> public? 10.1.100.100:20377 --> 1.1.1.1:2048
?icmp? VPN: public --> public? 10.1.100.100:19609 --> 1.1.1.1:2048
?icmp? VPN: public --> public? 10.1.100.100:19865 --> 1.1.1.1:2048
?udp? VPN: public --> public? 12.1.1.2:49152 --> 12.1.1.1:18514
流量通过FW1访问AR1,产生了ICMP的会话表项。
查看FW2的会话表:
HRP_S[FW2]display? firewall session table?
2023-03-28 07:27:29.090
?Current Total Sessions : 8
?icmp? VPN: public --> public? Remote 10.1.100.100:40089 --> 1.1.1.1:2048
?udp? VPN: public --> public? 12.1.1.1:16384 --> 12.1.1.2:18514
?udp? VPN: public --> public? 12.1.1.1:49152 --> 12.1.1.2:18514
?icmp? VPN: public --> public? Remote 10.1.100.100:39833 --> 1.1.1.1:2048
?icmp? VPN: public --> public? Remote 10.1.100.100:40857 --> 1.1.1.1:2048
?icmp? VPN: public --> public? Remote 10.1.100.100:40601 --> 1.1.1.1:2048
?icmp? VPN: public --> public? Remote 10.1.100.100:41113 --> 1.1.1.1:2048
?udp? VPN: public --> public? 12.1.1.2:49152 --> 12.1.1.1:18514
流量并不会经过FW2,但是FW2可以通过HRP备份会话表项信息,来实现主备的平滑切换。
?需要更多项目使用或数通考试题目的 ,点赞+私 ,找鹏哥领取资料!!

本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!