shell编程-4
正则表达式
- 正则表达式
- 1.什么是正则表达式
- 2.明确一个知识点: shell的解析流程
- 3.通配符
- 4.grep
- 5.正则表达式的普通内容
- 6.一些问题
- 7.作业
- 1.查找 var/log/messages 这个文件里单词的长度在16-18之间的单词显示出来
- 2.进入/lianxi目录,复制/etc/passwd到当前目录下,然后对passwd进行操作
- 3、查找出当前passwd文件中以ftp或者mail开头的行,在屏幕上输出。
- 4、查找出当前passwd文件中首行不是以r、m、f开头的行,在屏幕上输出。
- 5、查找出当前passwd文件中以bash结尾的行。
- 6、查找出/etc/login.defs文件中的有效行(不显示空行和注释行)。
- 7、查找出/var/log/messages文档中有16个字母的单词?
- 8、查找出来/etc/passwd文件里用户名包含liu同时使用bash的用户
- 9、查找/etc/ssh/sshd_config 里的有效行
- 10、查找出/etc/ssh/sshd_config 文件里的包含连续2个数字的行
- 11、查找出包含特殊字符的行
- 12、查找出不包含数字的行
- 13、查找出/var/log/secure里的ip地址出来
- 14、写一个表示下面网址的正则表达式出来。
- 15、写一个表示下面网址的正则表达式出来。
- 16、写一个表示邮箱的正则
- 17、C类ip地址的正则表达式 section1:范围在192-223之间 section2和section3和section4范围:0-255之间
- 18.用简单的正则匹配 netstat -antplu 的ip地址,去重
- 19.用shell生成 16位的密码
- 20.使用ps命令查看进程(pid=2345)的启动时间
正则表达式
一个重要的命令: grep---->过滤文本
1.什么是正则表达式
正则表达式: regular expression
本质上是:一种思想,方法。理解为一套方法或者工艺
别的命令采用这套方法,去查找内容
按照某种正确的规则,将字母,数字,特殊符号组合成一个公式,用来表达某个意思
作用: 一些查找类的命令,喜欢使用正则表达式去搜索符合条件的内容
写正则表达式 就是根据某个特点,使用规则表示出来,然后grep可以根据这个规律去查找

2.明确一个知识点: shell的解析流程
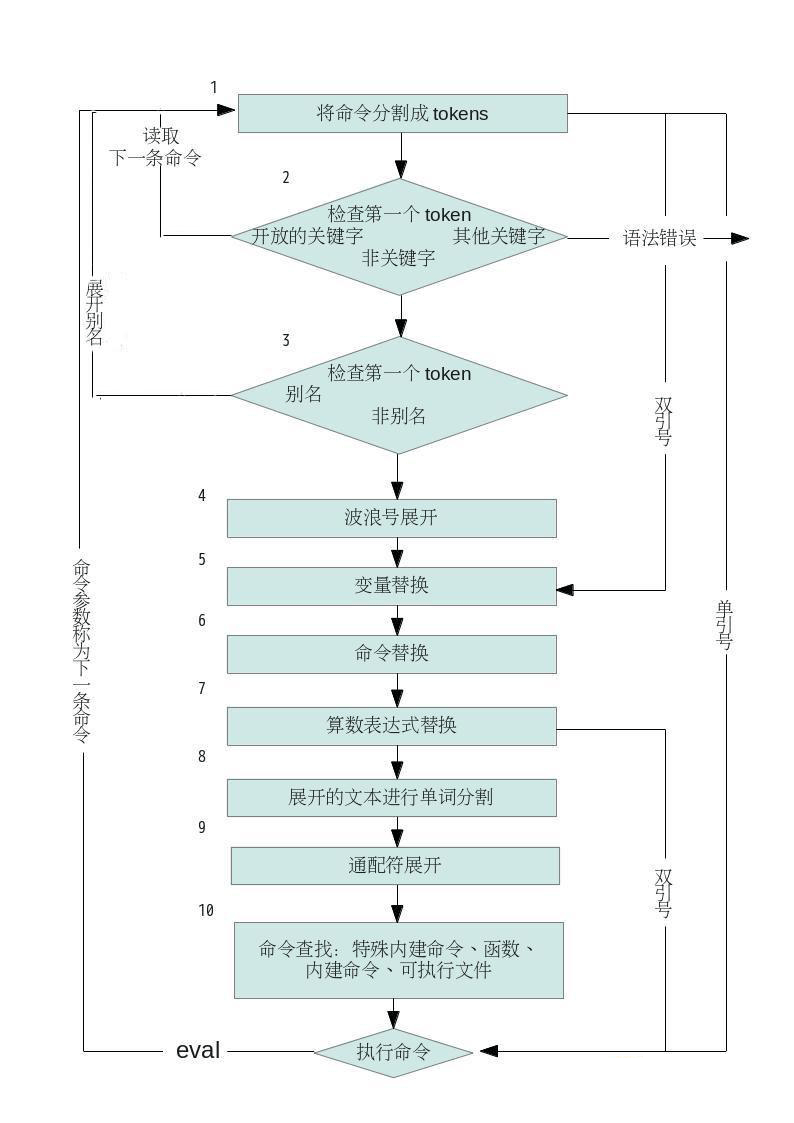
-
**在输入一条命令的时候 会将命令分割成 tokens 比方说 mkdir -p gao{1…20} **
-
先查看mkdir检查是不是关键字
-
检查第一个token是不是别名
-
然后看看有没有波浪符号
-
再看有没有变量替换
-
再看有没有命令替换(优先级高)
-
看有没有算数表达式
-
再看展开的文本进行单词的分割
-
展开通配符
-
命令查找
-
执行命令
-
eval会再执行一下
**eval命令将会首先扫描命令行进行所有的替换,然后再执行命令。该命令使用于那些一次扫描无法实现其功能的变量。该命令对变量进行两次扫描。这些需要进行两次扫描的变量有时候被称为复杂变量 **
两次扫描 test.txt内容:hello shell world! myfile="cat test.txt" (1)echo $myfile #result:cat test.txt (2)eval $myfile #result:hello shell world! 从(2)可以知道第一次扫描进行了变量替换,第二次扫描执行了该字符串中所包含的命令
3.通配符

- [0-9] 取0到9之间的任意一个字符
- [^0-9] 不是0到9的字符
- [abc] 取a或者b或者c
- [a-z] 取字母a-z之间的字符
- [A-Z] 取字母A-Z之间的字符
? 表示匹配1个字符或者0个
[root@gh-shell 1-18] echo "abc abbc ac"|egrep -o "ab?c" abc ac [root@gh-shell 1-18]#
加号表示,至少要有一个
[root@gh-shell 1-18] echo "abc abbc abbbbc ac"|egrep -o "ab+c" abc abbc abbbbc [root@gh-shell 1-18]#
{4} 表示前面的字符出现4次
[root@gh-shell 1-18] echo "abc abbc abbbbc ac"|egrep -o "ab{4}c" abbbbc [root@gh-shell 1-18]#
{4,}代表 4次及以上
[root@gh-shell 1-18] echo "abc abbc abbbbbbbbc abbbbc ac"|egrep -o "ab{4,}c" abbbbbbbbc abbbbc [root@gh-shell 1-18]#
{4,8}表示4-8之内都可以
{,8}表示0-8都可以 很像切片
(ab){,8} 表示 ab 出现0到8次 ,ab是整体
[root@gh-shell 1-18] echo "abc abbc abbbbbbbbc abbbbc ac"|egrep -o "(ab){,8}c" abc c c c c [root@gh-shell 1-18]#
4.grep


grep和egrep的区别:
grep是基本正则:^ $ . *
egrep是扩展正则: | + ? {} —>支持更多的元字符
-i: 不区分大小写
[root@gh-shell 1-18] cat mobile_phone.txt
xiaomi HUAWEI
oppo VIVO vivo
huawei apple
sanxin > 123
XIAOMI DAMI
LG lenovo nokia NOKIA
12345 sanchaung
oneplus 2345 #$
[root@gh-shell 1-18] cat mobile_phone.txt |egrep "xiaomi"
xiaomi HUAWEI
[root@gh-shell 1-18] cat mobile_phone.txt |egrep -i "xiaomi"
xiaomi HUAWEI
XIAOMI DAMI
[root@gh-shell 1-18] cat mobile_phone.txt |egrep -i "xiaomi|huawei"
xiaomi HUAWEI
huawei apple
XIAOMI DAMI
-
^表示以什么开头 -
$表示以什么结尾
-E 就是扩展正则,相当于egrep
-n 是编号,出现在文本的第几行
[root@gh-shell 1-18] cat mobile_phone.txt |egrep -n -i "xiaomi|huawei"
1:xiaomi HUAWEI
3:huawei apple
5:XIAOMI DAMI
[root@gh-shell 1-18]#
-o only-match 仅仅匹配符合要求的行
[root@gh-shell 1-18] cat mobile_phone.txt |egrep -n -o -i "xiaomi|huawei"
1:xiaomi
1:HUAWEI
3:huawei
5:XIAOMI
[root@gh-shell 1-18]#
[root@gh-shell 1-18] cat /etc/passwd|grep -o root #查找所有包含root的行
root
root
root
root
root
root
root
root
root
[root@gh-shell 1-18] cat /etc/passwd|grep -o root|wc -l
9
[root@gh-shell 1-18]#
-v取反的意思(整行取反)
区别[^] 这个是单字符取反
[root@gh-shell 1-18] cat /etc/passwd|grep -v root
-c 满足要求的行的次数
[root@gh-shell 1-18] cat mobile_phone.txt |grep -c -i "xiaomi"
2
[root@gh-shell 1-18]#
-A 找出符合要求的后面的行数
[root@gh-shell 1-18] cat mobile_phone.txt |egrep -A 3 vivo
oppo VIVO vivo
huawei apple
sanxin > 123
XIAOMI DAMI
-C 找出符合要求的上下n行
[root@gh-shell 1-18] cat mobile_phone.txt |egrep -C 2 apple
xiaomi HUAWEI
oppo VIVO vivo
huawei apple
sanxin > 123
XIAOMI DAMI
[root@gh-shell 1-18]#
-r递归查找 后边接的是文件夹
[root@gh-shell 1-18] egrep "xiaomi" -r /shell
/shell/1-18/mobile_phone.txt:xiaomi HUAWEI
/shell/1-18/gao.txt:xiaomi dami
[root@gh-shell 1-18]#
\<:表示词首部 表示以这个单词开头
\<abc\>: 表示abc这个单词
\< 或者 \>符合 可以用 \b来表示 单词的边界
[root@gh-shell 1-18] echo "chenjinhuai chenjinjin chenjingui"|egrep "jin\b" chenjinhuai chenjinjin chenjingui [root@gh-shell 1-18]#
'表示单词以chen开头'
[root@gh-shell 1-18] echo "chenjinhuai chenjinjin chenjingui"|egrep "\<chen"
chenjinhuai chenjinjin chenjingui
[root@gh-shell 1-18]#
'只找chenjinhuai这个单词'
[root@gh-shell 1-18] echo "chenjinhuai chenjinjin chenjingui"|egrep "\<chenjinhuai\>"
chenjinhuai chenjinjin chenjingui
[root@gh-shell 1-18]#
'找单词以gui结尾的'
[root@gh-shell 1-18] echo "chenjinhuai chenjinjin chenjingui"|egrep "gui\>"
chenjinhuai chenjinjin chenjingui
[root@gh-shell 1-18]#
5.正则表达式的普通内容


[root@gh-shell 1-18] echo aaabbbcc|egrep "b*"
aaabbbcc
[root@gh-shell 1-18]#
[root@gh-shell 1-18] cat mobile_phone.txt |egrep -n "^huawei$"
9:huawei
[root@gh-shell 1-18] cat mobile_phone.txt |egrep -n "^$"
11:
12:
13:
[root@gh-shell 1-18]#
取反,显示行号,匹配空行,以#开头
[root@gh-shell 1-18] cat /etc/ssh/sshd_config|egrep -n -v "^$|^#"
.代表单个任意字符
[root@gh-shell 1-18] cat /etc/passwd|egrep "^sc....:"
sc10:x:1009:1009::/home/sc10:/bin/bash
sc11:x:1010:1010::/home/sc11:/bin/bash
sc12:x:1011:1011::/home/sc12:/bin/bash
sc13:x:1012:1012::/home/sc13:/bin/bash
sc14:x:1013:1013::/home/sc14:/bin/bash
sc15:x:1014:1014::/home/sc15:/bin/bash
sc16:x:1015:1015::/home/sc16:/bin/bash
sc17:x:1016:1016::/home/sc17:/bin/bash
sc18:x:1017:1017::/home/sc18:/bin/bash
sc19:x:1018:1018::/home/sc19:/bin/bash
sc20:x:1019:1019::/home/sc20:/bin/bash
[root@gh-shell 1-18]#
任意内容:
[root@gh-shell 1-18] cat /etc/passwd|egrep "^sc.*:"
sc1:x:1000:1000::/home/sc1:/bin/bash
sc2:x:1001:1001::/home/sc2:/bin/bash
sc3:x:1002:1002::/home/sc3:/bin/bash
sc4:x:1003:1003::/home/sc4:/bin/bash
sc5:x:1004:1004::/home/sc5:/bin/bash
sc6:x:1005:1005::/home/sc6:/bin/bash
sc7:x:1006:1006::/home/sc7:/bin/bash
sc8:x:1007:1007::/home/sc8:/bin/bash
sc9:x:1008:1008::/home/sc9:/bin/bash
sc10:x:1009:1009::/home/sc10:/bin/bash
sc11:x:1010:1010::/home/sc11:/bin/bash
sc12:x:1011:1011::/home/sc12:/bin/bash
sc13:x:1012:1012::/home/sc13:/bin/bash
sc14:x:1013:1013::/home/sc14:/bin/bash
sc15:x:1014:1014::/home/sc15:/bin/bash
sc16:x:1015:1015::/home/sc16:/bin/bash
sc17:x:1016:1016::/home/sc17:/bin/bash
sc18:x:1017:1017::/home/sc18:/bin/bash
sc19:x:1018:1018::/home/sc19:/bin/bash
sc20:x:1019:1019::/home/sc20:/bin/bash
[root@gh-shell 1-18]#
6.一些问题
怎么找出特殊字符
[root@gh-shell 1-18] cat mobile_phone.txt |egrep "[^0-Z]"
xiaomi HUAWEI
oppo VIVO vivo
huawei apple
sanxin > 123
XIAOMI DAMI
LG lenovo nokia NOKIA
12345 sanchaung
oneplus 2345 #$
[root@gh-shell 1-18] cat mobile_phone.txt |egrep "[^0-9a-zA-Z]"
xiaomi HUAWEI
oppo VIVO vivo
huawei apple
sanxin > 123
XIAOMI DAMI
LG lenovo nokia NOKIA
12345 sanchaung
oneplus 2345 #$
[root@gh-shell 1-18]#
怎么知道字符串的长度
[root@gh-shell 1-18] u_pwd="asfasfafasdfgefdgae"
[root@gh-shell 1-18] echo ${#u_pwd}
19
[root@gh-shell 1-18] echo $u_pwd|wc -L
19
[root@gh-shell 1-18]#
判断用户的密码里是否有特殊字符
[root@gh-shell 1-18] echo ${u_pwd}|egrep "[0-9]"|egrep "[A-Z]"|egrep "[^0-Z]"
asfasfafasdfgefdgae1$&FGTT
[root@gh-shell 1-18]#
判断用户密码是否符合复杂性要求
[root@gh-shell 1-18] cat user_passwd.sh
#!/bin/bash
#将第一个位置变量的内容复制给 u_pwd
u_pwd=$1
#判断密码的长度
pwd_l=${#u_pwd}
#判断长度是否大于8
if (( $pwd_l >=8 ));then
#判断是否包含数字,大写,特殊符合
if echo $u_pwd|egrep "[0-9]"|egrep "[A-Z]"|egrep "[^0-Z]" &>/dev/null;then
echo "密码满足复杂性要求"
else
echo "密码不满足复杂性要求"
fi
else
echo "密码长度小于8,请重新输入"
fi
[root@gh-shell 1-18]#
7.作业
1.查找 var/log/messages 这个文件里单词的长度在16-18之间的单词显示出来
[root@gh-shell 1-18] cat /var/log/messages|egrep "\<[a-Z]{16,18}\>"
2.进入/lianxi目录,复制/etc/passwd到当前目录下,然后对passwd进行操作
[root@gh-shell 1-18] cd /lianxi/
[root@gh-shell lianxi] cp /etc/passwd .
[root@gh-shell lianxi]#
3、查找出当前passwd文件中以ftp或者mail开头的行,在屏幕上输出。
[root@gh-shell lianxi] cat passwd |egrep "^ftp|^mail"
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
[root@gh-shell lianxi]#
4、查找出当前passwd文件中首行不是以r、m、f开头的行,在屏幕上输出。
[root@gh-shell lianxi] cat passwd |egrep -v "^r|^m|^f"
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
nobody:x:99:99:Nobody:/:/sbin/nologin
systemd-network:x:192:192:systemd Network Management:/:/sbin/nologin
dbus:x:81:81:System message bus:/:/sbin/nologin
polkitd:x:999:998:User for polkitd:/:/sbin/nologin
tss:x:59:59:Account used by the trousers package to sandbox the tcsd daemon:/dev/null:/sbin/nologin
sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin
postfix:x:89:89::/var/spool/postfix:/sbin/nologin
chrony:x:998:996::/var/lib/chrony:/sbin/nologin
sc1:x:1000:1000::/home/sc1:/bin/bash
sc2:x:1001:1001::/home/sc2:/bin/bash
sc3:x:1002:1002::/home/sc3:/bin/bash
sc4:x:1003:1003::/home/sc4:/bin/bash
sc5:x:1004:1004::/home/sc5:/bin/bash
sc6:x:1005:1005::/home/sc6:/bin/bash
sc7:x:1006:1006::/home/sc7:/bin/bash
sc8:x:1007:1007::/home/sc8:/bin/bash
sc9:x:1008:1008::/home/sc9:/bin/bash
sc10:x:1009:1009::/home/sc10:/bin/bash
sc11:x:1010:1010::/home/sc11:/bin/bash
sc12:x:1011:1011::/home/sc12:/bin/bash
sc13:x:1012:1012::/home/sc13:/bin/bash
sc14:x:1013:1013::/home/sc14:/bin/bash
sc15:x:1014:1014::/home/sc15:/bin/bash
sc16:x:1015:1015::/home/sc16:/bin/bash
sc17:x:1016:1016::/home/sc17:/bin/bash
sc18:x:1017:1017::/home/sc18:/bin/bash
sc19:x:1018:1018::/home/sc19:/bin/bash
sc20:x:1019:1019::/home/sc20:/bin/bash
[root@gh-shell lianxi]#
5、查找出当前passwd文件中以bash结尾的行。
[root@gh-shell lianxi] cat passwd |egrep "bash$"
root:x:0:0:root:/root:/bin/bash
sc1:x:1000:1000::/home/sc1:/bin/bash
sc2:x:1001:1001::/home/sc2:/bin/bash
sc3:x:1002:1002::/home/sc3:/bin/bash
sc4:x:1003:1003::/home/sc4:/bin/bash
sc5:x:1004:1004::/home/sc5:/bin/bash
sc6:x:1005:1005::/home/sc6:/bin/bash
sc7:x:1006:1006::/home/sc7:/bin/bash
sc8:x:1007:1007::/home/sc8:/bin/bash
sc9:x:1008:1008::/home/sc9:/bin/bash
sc10:x:1009:1009::/home/sc10:/bin/bash
sc11:x:1010:1010::/home/sc11:/bin/bash
sc12:x:1011:1011::/home/sc12:/bin/bash
sc13:x:1012:1012::/home/sc13:/bin/bash
sc14:x:1013:1013::/home/sc14:/bin/bash
sc15:x:1014:1014::/home/sc15:/bin/bash
sc16:x:1015:1015::/home/sc16:/bin/bash
sc17:x:1016:1016::/home/sc17:/bin/bash
sc18:x:1017:1017::/home/sc18:/bin/bash
sc19:x:1018:1018::/home/sc19:/bin/bash
sc20:x:1019:1019::/home/sc20:/bin/bash
root1:x:1020:1020::/home/root1:/bin/bash
[root@gh-shell lianxi]#
6、查找出/etc/login.defs文件中的有效行(不显示空行和注释行)。
[root@gh-shell lianxi] cat /etc/login.defs |egrep -v "^$|^#"
MAIL_DIR /var/spool/mail
PASS_MAX_DAYS 99999
PASS_MIN_DAYS 0
PASS_MIN_LEN 5
PASS_WARN_AGE 7
UID_MIN 1000
UID_MAX 60000
SYS_UID_MIN 201
SYS_UID_MAX 999
GID_MIN 1000
GID_MAX 60000
SYS_GID_MIN 201
SYS_GID_MAX 999
CREATE_HOME yes
UMASK 077
USERGROUPS_ENAB yes
ENCRYPT_METHOD SHA512
[root@gh-shell lianxi]#
7、查找出/var/log/messages文档中有16个字母的单词?
[root@gh-shell lianxi] cat /var/log/messages|egrep "\b[a-Z]{16}\b"
8、查找出来/etc/passwd文件里用户名包含liu同时使用bash的用户
[root@gh-shell lianxi] cat /etc/passwd|egrep ".*liu.*:x.*/bin/bash"
liu:x:1022:1022::/home/liu:/bin/bash
liu1:x:1023:1023::/home/liu1:/bin/bash
liu2:x:1024:1024::/home/liu2:/bin/bash
liu3:x:1025:1025::/home/liu3:/bin/bash
[root@gh-shell lianxi]#
9、查找/etc/ssh/sshd_config 里的有效行
[root@gh-shell lianxi] cat /etc/ssh/sshd_config |egrep -v "^$|^#"
HostKey /etc/ssh/ssh_host_rsa_key
HostKey /etc/ssh/ssh_host_ecdsa_key
HostKey /etc/ssh/ssh_host_ed25519_key
SyslogFacility AUTHPRIV
AuthorizedKeysFile .ssh/authorized_keys
PasswordAuthentication yes
ChallengeResponseAuthentication no
GSSAPIAuthentication yes
GSSAPICleanupCredentials no
UsePAM yes
X11Forwarding yes
AcceptEnv LANG LC_CTYPE LC_NUMERIC LC_TIME LC_COLLATE LC_MONETARY LC_MESSAGES
AcceptEnv LC_PAPER LC_NAME LC_ADDRESS LC_TELEPHONE LC_MEASUREMENT
AcceptEnv LC_IDENTIFICATION LC_ALL LANGUAGE
AcceptEnv XMODIFIERS
Subsystem sftp /usr/libexec/openssh/sftp-server
[root@gh-shell lianxi]#
10、查找出/etc/ssh/sshd_config 文件里的包含连续2个数字的行
[root@gh-shell lianxi] cat /etc/ssh/sshd_config |egrep "\b[0-9]{2}\b"
# $OpenBSD: sshd_config,v 1.100 2016/08/15 12:32:04 naddy Exp $
#Port 22
#MaxSessions 10
#X11DisplayOffset 10
#MaxStartups 10:30:100
[root@gh-shell lianxi]#
11、查找出包含特殊字符的行
[root@gh-shell lianxi] cat /etc/ssh/sshd_config |egrep "[^0-Z]"
# $OpenBSD: sshd_config,v 1.100 2016/08/15 12:32:04 naddy Exp $
# This is the sshd server system-wide configuration file. See
# sshd_config(5) for more information.
# This sshd was compiled with PATH=/usr/local/bin:/usr/bin
# The strategy used for options in the default sshd_config shipped with
# OpenSSH is to specify options with their default value where
# possible, but leave them commented. Uncommented options override the
# default value.
# If you want to change the port on a SELinux system, you have to tell
# SELinux about this change.
# semanage port -a -t ssh_port_t -p tcp #PORTNUMBER
#
#Port 22
#AddressFamily any
#ListenAddress 0.0.0.0
#ListenAddress ::
HostKey /etc/ssh/ssh_host_rsa_key
#HostKey /etc/ssh/ssh_host_dsa_key
HostKey /etc/ssh/ssh_host_ecdsa_key
HostKey /etc/ssh/ssh_host_ed25519_key
# Ciphers and keying
#RekeyLimit default none
# Logging
#SyslogFacility AUTH
SyslogFacility AUTHPRIV
#LogLevel INFO
# Authentication:
#LoginGraceTime 2m
#PermitRootLogin yes
#StrictModes yes
#MaxAuthTries 6
#MaxSessions 10
#PubkeyAuthentication yes
# The default is to check both .ssh/authorized_keys and .ssh/authorized_keys2
# but this is overridden so installations will only check .ssh/authorized_keys
AuthorizedKeysFile .ssh/authorized_keys
#AuthorizedPrincipalsFile none
#AuthorizedKeysCommand none
#AuthorizedKeysCommandUser nobody
# For this to work you will also need host keys in /etc/ssh/ssh_known_hosts
#HostbasedAuthentication no
# Change to yes if you don't trust ~/.ssh/known_hosts for
# HostbasedAuthentication
#IgnoreUserKnownHosts no
# Don't read the user's ~/.rhosts and ~/.shosts files
#IgnoreRhosts yes
# To disable tunneled clear text passwords, change to no here!
#PasswordAuthentication yes
#PermitEmptyPasswords no
PasswordAuthentication yes
# Change to no to disable s/key passwords
#ChallengeResponseAuthentication yes
ChallengeResponseAuthentication no
# Kerberos options
#KerberosAuthentication no
#KerberosOrLocalPasswd yes
#KerberosTicketCleanup yes
#KerberosGetAFSToken no
#KerberosUseKuserok yes
# GSSAPI options
GSSAPIAuthentication yes
GSSAPICleanupCredentials no
#GSSAPIStrictAcceptorCheck yes
#GSSAPIKeyExchange no
#GSSAPIEnablek5users no
# Set this to 'yes' to enable PAM authentication, account processing,
# and session processing. If this is enabled, PAM authentication will
# be allowed through the ChallengeResponseAuthentication and
# PasswordAuthentication. Depending on your PAM configuration,
# PAM authentication via ChallengeResponseAuthentication may bypass
# the setting of "PermitRootLogin without-password".
# If you just want the PAM account and session checks to run without
# PAM authentication, then enable this but set PasswordAuthentication
# and ChallengeResponseAuthentication to 'no'.
# WARNING: 'UsePAM no' is not supported in Red Hat Enterprise Linux and may cause several
# problems.
UsePAM yes
#AllowAgentForwarding yes
#AllowTcpForwarding yes
#GatewayPorts no
X11Forwarding yes
#X11DisplayOffset 10
#X11UseLocalhost yes
#PermitTTY yes
#PrintMotd yes
#PrintLastLog yes
#TCPKeepAlive yes
#UseLogin no
#UsePrivilegeSeparation sandbox
#PermitUserEnvironment no
#Compression delayed
#ClientAliveInterval 0
#ClientAliveCountMax 3
#ShowPatchLevel no
#UseDNS yes
#PidFile /var/run/sshd.pid
#MaxStartups 10:30:100
#PermitTunnel no
#ChrootDirectory none
#VersionAddendum none
# no default banner path
#Banner none
# Accept locale-related environment variables
AcceptEnv LANG LC_CTYPE LC_NUMERIC LC_TIME LC_COLLATE LC_MONETARY LC_MESSAGES
AcceptEnv LC_PAPER LC_NAME LC_ADDRESS LC_TELEPHONE LC_MEASUREMENT
AcceptEnv LC_IDENTIFICATION LC_ALL LANGUAGE
AcceptEnv XMODIFIERS
# override default of no subsystems
Subsystem sftp /usr/libexec/openssh/sftp-server
# Example of overriding settings on a per-user basis
#Match User anoncvs
# X11Forwarding no
# AllowTcpForwarding no
# PermitTTY no
# ForceCommand cvs server
[root@gh-shell lianxi]#
12、查找出不包含数字的行
[root@gh-shell lianxi] cat /etc/ssh/sshd_config |egrep -v "[0-9]"
# This is the sshd server system-wide configuration file. See
# This sshd was compiled with PATH=/usr/local/bin:/usr/bin
# The strategy used for options in the default sshd_config shipped with
# OpenSSH is to specify options with their default value where
# possible, but leave them commented. Uncommented options override the
# default value.
# If you want to change the port on a SELinux system, you have to tell
# SELinux about this change.
# semanage port -a -t ssh_port_t -p tcp #PORTNUMBER
#
#AddressFamily any
#ListenAddress ::
HostKey /etc/ssh/ssh_host_rsa_key
#HostKey /etc/ssh/ssh_host_dsa_key
HostKey /etc/ssh/ssh_host_ecdsa_key
# Ciphers and keying
#RekeyLimit default none
# Logging
#SyslogFacility AUTH
SyslogFacility AUTHPRIV
#LogLevel INFO
# Authentication:
#PermitRootLogin yes
#StrictModes yes
#PubkeyAuthentication yes
# but this is overridden so installations will only check .ssh/authorized_keys
AuthorizedKeysFile .ssh/authorized_keys
#AuthorizedPrincipalsFile none
#AuthorizedKeysCommand none
#AuthorizedKeysCommandUser nobody
# For this to work you will also need host keys in /etc/ssh/ssh_known_hosts
#HostbasedAuthentication no
# Change to yes if you don't trust ~/.ssh/known_hosts for
# HostbasedAuthentication
#IgnoreUserKnownHosts no
# Don't read the user's ~/.rhosts and ~/.shosts files
#IgnoreRhosts yes
# To disable tunneled clear text passwords, change to no here!
#PasswordAuthentication yes
#PermitEmptyPasswords no
PasswordAuthentication yes
# Change to no to disable s/key passwords
#ChallengeResponseAuthentication yes
ChallengeResponseAuthentication no
# Kerberos options
#KerberosAuthentication no
#KerberosOrLocalPasswd yes
#KerberosTicketCleanup yes
#KerberosGetAFSToken no
#KerberosUseKuserok yes
# GSSAPI options
GSSAPIAuthentication yes
GSSAPICleanupCredentials no
#GSSAPIStrictAcceptorCheck yes
#GSSAPIKeyExchange no
# Set this to 'yes' to enable PAM authentication, account processing,
# and session processing. If this is enabled, PAM authentication will
# be allowed through the ChallengeResponseAuthentication and
# PasswordAuthentication. Depending on your PAM configuration,
# PAM authentication via ChallengeResponseAuthentication may bypass
# the setting of "PermitRootLogin without-password".
# If you just want the PAM account and session checks to run without
# PAM authentication, then enable this but set PasswordAuthentication
# and ChallengeResponseAuthentication to 'no'.
# WARNING: 'UsePAM no' is not supported in Red Hat Enterprise Linux and may cause several
# problems.
UsePAM yes
#AllowAgentForwarding yes
#AllowTcpForwarding yes
#GatewayPorts no
#PermitTTY yes
#PrintMotd yes
#PrintLastLog yes
#TCPKeepAlive yes
#UseLogin no
#UsePrivilegeSeparation sandbox
#PermitUserEnvironment no
#Compression delayed
#ShowPatchLevel no
#UseDNS yes
#PidFile /var/run/sshd.pid
#PermitTunnel no
#ChrootDirectory none
#VersionAddendum none
# no default banner path
#Banner none
# Accept locale-related environment variables
AcceptEnv LANG LC_CTYPE LC_NUMERIC LC_TIME LC_COLLATE LC_MONETARY LC_MESSAGES
AcceptEnv LC_PAPER LC_NAME LC_ADDRESS LC_TELEPHONE LC_MEASUREMENT
AcceptEnv LC_IDENTIFICATION LC_ALL LANGUAGE
AcceptEnv XMODIFIERS
# override default of no subsystems
Subsystem sftp /usr/libexec/openssh/sftp-server
# Example of overriding settings on a per-user basis
#Match User anoncvs
# AllowTcpForwarding no
# PermitTTY no
# ForceCommand cvs server
[root@gh-shell lianxi]#
13、查找出/var/log/secure里的ip地址出来
[root@gh-shell lianxi] cat /var/log/secure|egrep "[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}"
Jan 17 15:46:23 gh-shell sshd[5760]: Address 192.168.153.1 maps to localhost, but this does not map back to the address - POSSIBLE BREAK-IN ATTEMPT!
Jan 17 15:46:23 gh-shell sshd[5760]: Accepted password for root from 192.168.153.1 port 59386 ssh2
Jan 17 15:46:25 gh-shell sshd[5781]: Address 192.168.153.1 maps to localhost, but this does not map back to the address - POSSIBLE BREAK-IN ATTEMPT!
Jan 17 15:46:25 gh-shell sshd[5781]: Accepted password for root from 192.168.153.1 port 59387 ssh2
Jan 18 08:28:36 gh-shell sshd[6481]: Address 192.168.153.1 maps to localhost, but this does not map back to the address - POSSIBLE BREAK-IN ATTEMPT!
Jan 18 08:28:36 gh-shell sshd[6481]: Accepted password for root from 192.168.153.1 port 64503 ssh2
Jan 18 08:28:39 gh-shell sshd[6502]: Address 192.168.153.1 maps to localhost, but this does not map back to the address - POSSIBLE BREAK-IN ATTEMPT!
Jan 18 08:28:39 gh-shell sshd[6502]: Accepted password for root from 192.168.153.1 port 64504 ssh2
[root@gh-shell lianxi]# cat /var/log/secure|egrep "([0-9]{1,3}\.){3}[0-9]{1,3}"
Jan 17 15:46:23 gh-shell sshd[5760]: Address 192.168.153.1 maps to localhost, but this does not map back to the address - POSSIBLE BREAK-IN ATTEMPT!
Jan 17 15:46:23 gh-shell sshd[5760]: Accepted password for root from 192.168.153.1 port 59386 ssh2
Jan 17 15:46:25 gh-shell sshd[5781]: Address 192.168.153.1 maps to localhost, but this does not map back to the address - POSSIBLE BREAK-IN ATTEMPT!
Jan 17 15:46:25 gh-shell sshd[5781]: Accepted password for root from 192.168.153.1 port 59387 ssh2
Jan 18 08:28:36 gh-shell sshd[6481]: Address 192.168.153.1 maps to localhost, but this does not map back to the address - POSSIBLE BREAK-IN ATTEMPT!
Jan 18 08:28:36 gh-shell sshd[6481]: Accepted password for root from 192.168.153.1 port 64503 ssh2
Jan 18 08:28:39 gh-shell sshd[6502]: Address 192.168.153.1 maps to localhost, but this does not map back to the address - POSSIBLE BREAK-IN ATTEMPT!
Jan 18 08:28:39 gh-shell sshd[6502]: Accepted password for root from 192.168.153.1 port 64504 ssh2
[root@gh-shell lianxi]# cat /var/log/secure|egrep "([0-9]{1,3}\.){3}[0-9]{1,3}"
Jan 17 15:46:23 gh-shell sshd[5760]: Address 192.168.153.1 maps to localhost, but this does not map back to the address - POSSIBLE BREAK-IN ATTEMPT!
Jan 17 15:46:23 gh-shell sshd[5760]: Accepted password for root from 192.168.153.1 port 59386 ssh2
Jan 17 15:46:25 gh-shell sshd[5781]: Address 192.168.153.1 maps to localhost, but this does not map back to the address - POSSIBLE BREAK-IN ATTEMPT!
Jan 17 15:46:25 gh-shell sshd[5781]: Accepted password for root from 192.168.153.1 port 59387 ssh2
Jan 18 08:28:36 gh-shell sshd[6481]: Address 192.168.153.1 maps to localhost, but this does not map back to the address - POSSIBLE BREAK-IN ATTEMPT!
Jan 18 08:28:36 gh-shell sshd[6481]: Accepted password for root from 192.168.153.1 port 64503 ssh2
Jan 18 08:28:39 gh-shell sshd[6502]: Address 192.168.153.1 maps to localhost, but this does not map back to the address - POSSIBLE BREAK-IN ATTEMPT!
Jan 18 08:28:39 gh-shell sshd[6502]: Accepted password for root from 192.168.153.1 port 64504 ssh2
[root@gh-shell lianxi]#
14、写一个表示下面网址的正则表达式出来。
例如: http://www.baidu.com
http://www.sina.com
http://www.163.com
http://www.12306.cn
http://www.qillu.edu
[root@gh-shell lianxi] cat web.txt|egrep "[a-Z]+://([0-Z]+\.){2}[0-Z]+"
http://www.baidu.com
http://www.sina.com
http://www.163.com
http://www.12306.cn
http://www.qillu.edu
15、写一个表示下面网址的正则表达式出来。
例如: http://www.baidu.com
http://www.sina.com
http://www.163.com
http://www.12306.cn
http://www.qillu.edu
rsync://www.github.com/abc
ftp://192.168.0.1
ftp://www.baidu.com
[root@gh-shell lianxi] cat web2.txt|egrep "[a-Z]+://([0-Z]+\.){2}[0-Z]+"
http://www.baidu.com
http://www.sina.com
http://www.163.com
http://www.12306.cn
http://www.qillu.edu
rsync://www.github.com/abc
ftp://192.168.0.1
ftp://www.baidu.com
[root@gh-shell lianxi]#
16、写一个表示邮箱的正则
feng@qq.com
1234feng@163.com
meng.xianhui@yahoo.cn
liudehua@sina.com
10001@qq.com
123_ui@12306.cn
qilu@qilu.edu
qilu@qilu.edu/fjdkfjk/fjdk
[root@gh-shell lianxi] cat mail.txt|egrep "[0-Z_]+@[0-Z]+\.[a-z]+"
feng@qq.com
1234feng@163.com
meng.xianhui@yahoo.cn
liudehua@sina.com
10001@qq.com
123_ui@12306.cn
qilu@qilu.edu
qilu@qilu.edu/fjdkfjk/fjdk
[root@gh-shell lianxi]#
17、C类ip地址的正则表达式 section1:范围在192-223之间 section2和section3和section4范围:0-255之间
例如:193.168.23.1
[root@gh-shell lianxi] cat /var/log/secure|egrep "\b(([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])\.){3}([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9])\b"
Jan 17 15:46:23 gh-shell sshd[5760]: Address 192.168.153.1 maps to localhost, but this does not map back to the address - POSSIBLE BREAK-IN ATTEMPT!
Jan 17 15:46:23 gh-shell sshd[5760]: Accepted password for root from 192.168.153.1 port 59386 ssh2
Jan 17 15:46:25 gh-shell sshd[5781]: Address 192.168.153.1 maps to localhost, but this does not map back to the address - POSSIBLE BREAK-IN ATTEMPT!
Jan 17 15:46:25 gh-shell sshd[5781]: Accepted password for root from 192.168.153.1 port 59387 ssh2
Jan 18 08:28:36 gh-shell sshd[6481]: Address 192.168.153.1 maps to localhost, but this does not map back to the address - POSSIBLE BREAK-IN ATTEMPT!
Jan 18 08:28:36 gh-shell sshd[6481]: Accepted password for root from 192.168.153.1 port 64503 ssh2
Jan 18 08:28:39 gh-shell sshd[6502]: Address 192.168.153.1 maps to localhost, but this does not map back to the address - POSSIBLE BREAK-IN ATTEMPT!
Jan 18 08:28:39 gh-shell sshd[6502]: Accepted password for root from 192.168.153.1 port 64504 ssh2
[root@gh-shell lianxi]#
A: 1~127
B:128~191
C:192~223
1位数字
0-9
2位数
10~99
3位数
100~199
200~249
250~255
'4个255的正则'
\b(([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])\.){3}([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9])\b
'B类:128~191'
(12[89]|1[3-8][0-9]|19[01])(\.([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])){3}
'A类:1~127'
([1-9]|[1-9][0-9]|11[0-9]|12[0-7])(\.([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])){3}
[root@gh-shell lianxi] cat /var/log/secure|egrep "\b([1-9]|[1-9][0-9]|11[0-9]|12[0-7])(\.([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])){3}\b"
1.12.34.5
2.12.34.5
88.12.34.5
[root@gh-shell lianxi]#
18.用简单的正则匹配 netstat -antplu 的ip地址,去重
[root@gh-shell lianxi] netstat -antplu|egrep -o "\b(([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])\.){3}([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9])\b"|sort|uniq
0.0.0.0
127.0.0.1
192.168.153.1
192.168.153.161
[root@gh-shell lianxi]#
19.用shell生成 16位的密码
[root@gh-shell lianxi] echo "$RANDOM"|md5sum|cut -c 1-16
97e41756d502e1e6
[root@gh-shell lianxi]#
20.使用ps命令查看进程(pid=2345)的启动时间
[root@gh-shell lianxi] ps aux|awk '$2 == 23 {print $0}'
root 23 0.0 0.0 0 0 ? S 1月17 0:00 [migration/3]
[root@gh-shell lianxi] ps aux|awk '$2 == 23 {print $9}'
1月17
[root@gh-shell lianxi]#
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
- Python教程
- 深入理解 MySQL 中的 HAVING 关键字和聚合函数
- Qt之QChar编码(1)
- MyBatis入门基础篇
- 用Python脚本实现FFmpeg批量转换
- ubuntu22下安装minconda
- 电脑无法开机?重装系统教程在这!超详细
- 数据结构【3】:数组 VS 列表
- 项目记录:RabbitMq+Redis配置消息队列
- 【C++】upper_bound和lower_bound
- 【深入挖掘Java技术】「源码原理体系」盲点问题解析之HashMap工作原理全揭秘(上)
- c++11 标准模板(STL)(std::pair)(五)创建一个 pair 对象,其类型根据各实参类型定义
- Redis学习——入门篇②
- QML —— RadioButton的两个经典示例(附完整源码)
- 电脑上怎么录屏?教你3种方法,轻松搞定!