firewall防火墙(一)
1、Linux防火墙基础
? ? ? ??防火墙是指设置在不同网络与网络安全域之间的一系列部件的组合,也是不同安全域之间信息的唯一出口。通过检测、限制并更改跨越防火墙的数据流,尽可能地对外屏蔽网络内部的信息、架构和运行状态,且有选择地接收外部网络访问。从传统意义上来说防火墙技术分为三类:包过滤、应用代理、状态检测。无论一个防火墙的实现过程有多复杂,归根结底都是在这三种技术的基础上进行扩展的。

2、firewall-cmd命令。
?1)启动、停止、查看firewalld服务
????????在安装CentOS 7系统时,会自动安装firewalld和图形化工具firewall-config。
[root@localhost ~]# systemctl start firewalld //启动firewalld
[root@localhost ~]# systemctl enable firewalld //设置开机自启动
Created symlink from /etc/systemd/system/dbus-org.fedoraproject.FirewallD1.service to /usr/lib/systemd/system/firewalld.service.
Created symlink from /etc/systemd/system/multi-user.target.wants/firewalld.service to /usr/lib/systemd/system/firewalld.service.
? ? ? ? 如果firewalld正在运行,通过下面的命令可以查看运行状态
[root@localhost ~]# systemctl status firewalld
● firewalld.service - firewalld - dynamic firewall daemon
Loaded: loaded (/usr/lib/systemd/system/firewalld.service; enabled; vendor preset: enabled)
Active: active (running) since 二 2024-01-09 16:05:04 CST; 5min ago
Docs: man:firewalld(1)
Main PID: 11193 (firewalld)
CGroup: /system.slice/firewalld.service
└─11193 /usr/bin/python -Es /usr/sbin/firewalld --nofork --nopid
1月 09 16:05:04 localhost.localdomain systemd[1]: Starting firewalld - dynamic firewall daemon...
1月 09 16:05:04 localhost.localdomain systemd[1]: Started firewalld - dynamic firewall daemon.
[root@localhost ~]# firewall-cmd --state
running
?????????如果想要禁用firewalld,执行以下命令即可实现
[root@localhost ~]# systemctl stop firewalld //停止firewalld
[root@localhost ~]# systemctl disable firewalld //设置开机不自启动
2)获得预定义信息
[root@localhost ~]# firewall-cmd --get-zones
block dmz drop external home internal public trusted work
[root@localhost ~]# firewall-cmd --get-services
RH-Satellite-6 amanda-client amanda-k5-client bacula bacula-client bgp bitcoin bitcoin-rpc bitcoin-testnet bitcoin-testnet-rpc ceph ceph-mon cfengine condor-collector ctdb dhcp dhcpv6 dhcpv6-client dns docker-registry docker-swarm dropbox-lansync elasticsearch freeipa-ldap freeipa-ldaps freeipa-replication freeipa-trust ftp ganglia-client ganglia-master git gre high-availability http https imap imaps ipp ipp-client ipsec irc ircs iscsi-target jenkins kadmin kerberos kibana klogin kpasswd kprop kshell ldap ldaps libvirt libvirt-tls managesieve mdns minidlna mongodb mosh mountd ms-wbt mssql murmur mysql nfs nfs3 nmea-0183 nrpe ntp openvpn ovirt-imageio ovirt-storageconsole ovirt-vmconsole pmcd pmproxy pmwebapi pmwebapis pop3 pop3s postgresql privoxy proxy-dhcp ptp pulseaudio puppetmaster quassel radius redis rpc-bind rsh rsyncd samba samba-client sane sip sips smtp smtp-submission smtps snmp snmptrap spideroak-lansync squid ssh syncthing syncthing-gui synergy syslog syslog-tls telnet tftp tftp-client tinc tor-socks transmission-client upnp-client vdsm vnc-server wbem-https xmpp-bosh xmpp-client xmpp-local xmpp-server zabbix-agent zabbix-server
[root@localhost ~]# firewall-cmd --get-icmptypes
address-unreachable bad-header communication-prohibited destination-unreachable echo-reply echo-request fragmentation-needed host-precedence-violation host-prohibited host-redirect host-unknown host-unreachable ip-header-bad neighbour-advertisement neighbour-solicitation network-prohibited network-redirect network-unknown network-unreachable no-route packet-too-big parameter-problem port-unreachable precedence-cutoff protocol-unreachable redirect required-option-missing router-advertisement router-solicitation source-quench source-route-failed time-exceeded timestamp-reply timestamp-request tos-host-redirect tos-host-unreachable tos-network-redirect tos-network-unreachable ttl-zero-during-reassembly ttl-zero-during-transit unknown-header-type unknown-option

3)区域管理

//显示当前系统中的默认区域
[root@localhost ~]# firewall-cmd --get-default-zone
public
//显示默认区域的所有规则
[root@localhost ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: ens33 ens37 ens38
sources:
services: ssh dhcpv6-client
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
//显示网络接口ens33对应区域
[root@localhost ~]# firewall-cmd --get-zone-of-interface=ens33
public
4)将网络接口ens33对应区域更改为internal区域
[root@localhost ~]# firewall-cmd --zone=internal --change-interface=ens33
The interface is under control of NetworkManager, setting zone to 'public'.
success
[root@localhost ~]# firewall-cmd --zone=internal --list-interfaces
ens33
[root@localhost ~]# firewall-cmd --get-zone-of-interface=ens33
internal
5)显示所有激活区域
[root@localhost ~]# firewall-cmd --get-active-zones
public
interfaces: ens33 ens37 ens38
2.2、服务管理

?1)为默认区域设置允许访问的服务
[root@localhost ~]# firewall-cmd --list-services
ssh dhcpv6-client //默认区域内允许访问的所有服务
//设置默认区域允许访问http服务和https服务
[root@localhost ~]# firewall-cmd --add-service=http
success
[root@localhost ~]# firewall-cmd --add-service=https
success
[root@localhost ~]# firewall-cmd --list-services
ssh dhcpv6-client http https
2)为internal区域设置允许访问的服务
//设置internal区域允许访问mysql服务
[root@localhost ~]# firewall-cmd --zone=internal --add-service=mysql
success
//设置internal区域不允许访问samba-client服务
[root@localhost ~]# firewall-cmd --zone=internal --remove-service=samba-client
success
//显示internal区域允许访问的所有服务
[root@localhost ~]# firewall-cmd --zone=internal --list-services
ssh mdns dhcpv6-client mysql
2.3、端口管理
1)在进行服务配置时,预定义的网络服务可以使用服务名配置,服务所涉及的端口就会自动打开。但是,对应非预定义的服务只能手动为指定的区域添加端口。
//在internal区域打开443/tcp端口
[root@localhost ~]# firewall-cmd --zone=internal --add-port=443/tcp
success
//禁止443/tcp端口访问
[root@localhost ~]# firewall-cmd --zone=internal --remove-port=443/tcp
success
3、两种配置模式
? ? ? ? firewall-cmd命令工具有两种配置模式:运行时模式表示当前内存中运行的防火墙配置,在系统或firewall服务重启、停止时配置将失效;永久模式表示重启防火墙或重新加载防火墙时的规则配置,是永久存储在配置文件中的。
????????firewall-cmd命令工具与配置模式相关的选项有三个:

4、firewalld防火墙应用案例
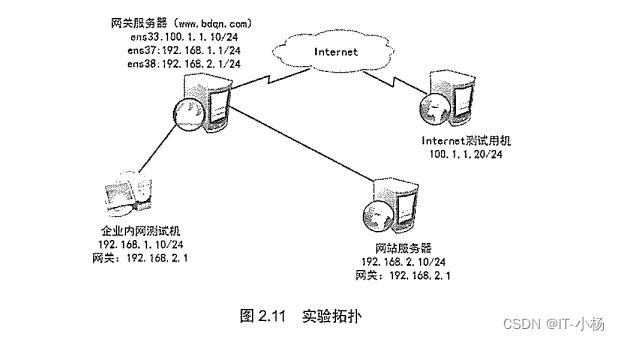
实验环境:
1)准备一台Linux网关服务器;一台LinuxWeb服务器
2)一台内网测试机;一台internet测试机
3)网关服务器设置三张网卡;分别为NAT、仅主机1和仅主机2
实验需求
1)ens33分配到external(外部)区域;ens37分配到trusted(信任)区域;ens38分配到dmz(非军事)。
2)网站服务器和网关服务均通过SSH来远程管理,为了安全,将SSH默认端口改为12345。
3)网站服务器开启https,过滤未加密的http流量
4)网站服务器拒绝ping
4.1、基本环境配置
1)在网关服务器上配置主机名即网卡地址
[root@localhost ~]# hostname HEY
[root@localhost ~]# vim /etc/hostname
HEY
[root@localhost ~]# ip add
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group
inet 192.168.136.24/24 brd 192.168.136.255 scope global noprefixroute ens33
3: ens37: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group
inet 192.168.154.254/24 brd 192.168.154.255 scope global noprefixroute ens37
4: ens38: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group
inet 192.168.177.254/24 brd 192.168.177.255 scope global noprefixroute ens38
2)开启网关服务器的路由转发功能
[root@localhost ~]# vim /etc/sysctl.conf
net.ipv4.ip_forward = 1
[root@localhost ~]# sysctl -p
net.ipv4.ip_forward = 14.2、网站服务器环境搭建
?1)配置Web服务器的主机及网卡地址
[root@localhost ~]# vim /etc/hostname
web
[root@localhost ~]# ifconfig
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.177.100 netmask 255.255.255.0 broadcast 192.168.177.255
2)安装http和mod_ssl软件包
[root@web ~]# yum -y install httpd mod_ssl
3)启用并启动httpd服务
[root@web ~]# systemctl start httpd
[root@web ~]# systemctl enable httpd
Created symlink from /etc/systemd/system/multi-user.target.wants/httpd.service to /usr/lib/systemd/system/httpd.service.
4)创建网站首页测试页index.html
[root@web ~]# vim /var/www/html/index.html
5)更改SSH的侦听地址,并重启sshd服务,注意需要将SELinux关闭
[root@web ~]# vim /etc/ssh/sshd_config
Port 12345
[root@web ~]# systemctl restart sshd4.3、在网站服务器上启动并配置firewalld防火墙
1)在网站服务器上启动firewalld防火墙并将默认区域设置为dmz区域,并将接口加入到dmz区域中
[root@web ~]# systemctl start firewalld
[root@web ~]# systemctl enable firewalld
[root@web ~]# systemctl status firewalld
● firewalld.service - firewalld - dynamic firewall daemon
Loaded: loaded (/usr/lib/systemd/system/firewalld.service; enabled; vendor preset: enabled)
Active: active (running) since 二 2024-01-09 17:07:05 CST; 11s ago
[root@web ~]# firewall-cmd --change-interface=ens33 --zone=dmz
2)为dmz区域打开https服务及添加tcp的12345端口
[root@web ~]# firewall-cmd --zone=dmz --add-service=https --permanent
success
[root@web ~]# firewall-cmd --zone=dmz --add-port=12345/tcp --permanent
success
3)禁止ping
[root@web ~]# firewall-cmd --add-icmp-block=echo-request --zone=dmz --permanent
success
4)因为预定义的SSH服务已经更改默认端口,所以将预定义SSH服务移除
[root@web ~]# firewall-cmd --zone=dmz --remove-service=ssh --permanent
5)重新加载firewalld激活配置,并查看刚才的配置
[root@web ~]# firewall-cmd --reload
firsuccess
[root@web ~]# firewall-cmd --list-all --zone=dmz
dmz
target: default
icmp-block-inversion: no
interfaces:
sources:
services: https
ports: 12345/tcp
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks: echo-request
rich rules:
4.4、在网关服务器上配置firewalld防火墙
1)验证firewalld在网关服务器上启动并正在运行
[root@HEY ~]# firewall-cmd --state
not running
[root@HEY ~]# systemctl start firewalld
[root@HEY ~]# systemctl enable firewalld
[root@HEY ~]# firewall-cmd --state
running2)配置默认区域为external区域,并查看配置结果
[root@HEY ~]# firewall-cmd --set-default-zone=external
success
[root@HEY ~]# firewall-cmd --list-all
external (active)
target: default
icmp-block-inversion: no
interfaces: ens37 ens38 ens33
sources:
services: ssh
ports:
protocols:
masquerade: yes
forward-ports:
source-ports:
icmp-blocks:
rich rules:
3)将ens37网卡配置到trusted区域,将ens38配置到dmz区域
[root@HEY ~]# firewall-cmd --change-interface=ens37 --zone=trusted
The interface is under control of NetworkManager, setting zone to 'trusted'.
success
[root@HEY ~]# firewall-cmd --change-interface=ens38 --zone=dmz
The interface is under control of NetworkManager, setting zone to 'dmz'.
success
4)查看配置情况
[root@HEY ~]# firewall-cmd --get-active-zones
dmz
interfaces: ens38
external
interfaces: ens33
trusted
interfaces: ens37
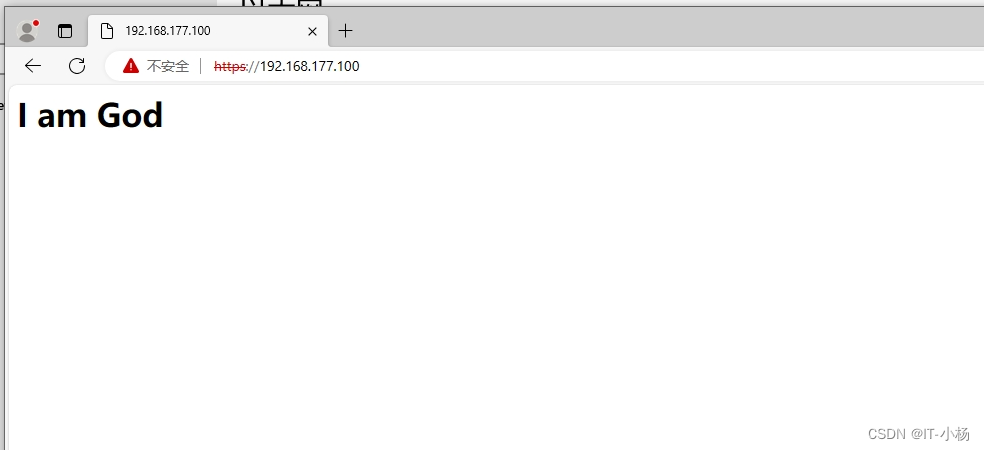
5)使用内网测试机访问Web网站
 ?
?
6)更改SSH的侦听端口,并重启服务(需关闭SELinux)
[root@HEY ~]# vim /etc/ssh/sshd_config
Port 12345
[root@HEY ~]# systemctl restart sshd
7)配置external区域添加tcp的12345端口
[root@HEY ~]# firewall-cmd --zone=external --add-port=12345/tcp --permanent
success
8)配置external区域移除SSH服务
[root@HEY ~]# firewall-cmd --zone=external --remove-service=ssh --permanent
success
9)配置external区域禁止ping
[root@HEY ~]# firewall-cmd --zone=external --add-icmp-block=echo-request --permanent
success
10)重新加载防火墙激活配置
[root@HEY ~]# firewall-cmd --reload
success
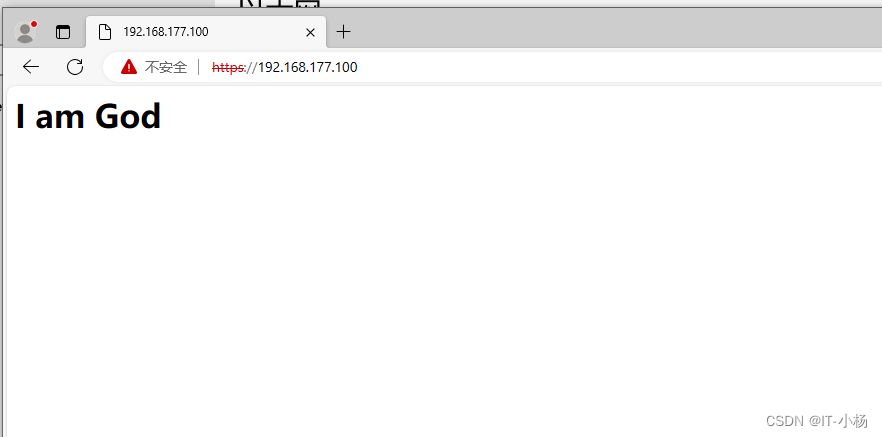
11)使用internet测试机访问Web网站
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!