Qlik Sense Ports
Ports
Qlik Sense Enterprise?uses ports to communicate between web browsers (users) and proxies, and between services in single and multi-node deployments.
Ports overview
The following tables are an overview of the ports used in a?Qlik Sense?deployment.
| Service | Inbound | Outbound | Internal only |
|---|---|---|---|
| Qlik Sense Proxy Service (QPS) | 80 (HTTP) 443 (HTTPS) 4243 (REST API) | 4239 (QRS websocket) 4242 (QRS REST API) 4747 (Engine) 4899 (Printing) 4900 (Broker) 4949 (Data profiling) 7070 (Logging service) | 4244 (Windows authentication) |
| Qlik Sense Engine Service (QES) | 4747 (QES listen port) | 7070 (Logging service) | 4748 (notifications from QRS) |
| Qlik Sense Repository Service (QRS) | 4242 (REST?API) 4239 (from QPS - websocket) 4240 (When QRS is run in test mode) 4444 (Setup API - inbound on rim nodes) | 4242 (REST?API) 4243 (Proxy REST API) 4240 (When QRS is run in test mode) 4444 (Setup API – outbound on central node) 4747 (Engine) 4748 (Engine notification API) 5050 (Scheduler manager API) 7070 (Logging service) 9200 (License Service) | 4570 (Certificate unlock) |
| Qlik Sense Scheduler Service (QSS) | 5050 (Manager REST API) 5151 (Worker REST API) 5252 (Monitoring API - optional) | 4242 (QRS REST API) 7070 (Logging Service) 5050 (Worker to?Manager) 5151 (Manager to Worker) | No additional ports. |
| Qlik Sense Repository Database (QRD) | 4432 (default listen port for database connections) | - | No additional ports. |
| Qlik Sense Printing service (QPR) | 4899 (QPR listen port) | - | 443 (Sense web server - proxy) 4242 (QRS REST API) 8088 (CEF debugging) |
| Qlik License Service | - | 443 (HTTPS) | 9200 |
| Broker service | 4900 | 3003 (Converter service) 4555 (Chart sharing) 4949 (Data profiling) 4950 (Precedents service) 9028 (Hub service) 9031 (Capability service) 9032 (About Service) 9041 (Connector registry proxy - server) 9051 (Connector registry proxy - desktop) 9054 (Precedents service) 9079 (Depgraph service) 9080 (Web extension service) 9081 (Qlik?Notifier Service) 9082 (Qlik?Mobility Registrar) 9090 (DownloadPrep) 9098 (On-demand app service) 21060 (Resource Distribution Service) 46277 (Deployment based warnings service) 64210 (Cayley.io—Open source graph database layer used by Precedents service) | - |
| Data profiling service | 4949 (listen port for REST API and websocket) | 4242 (QRS REST API) 4747 (QES) | |
| App Distribution Service | - | 5926 | No additional ports. |
| Hybrid Deployment Service | - | 5927 | No additional ports. |
| Hybrid Setup Console - HSC | 5929 | - | No additional ports. |
| Logging Service | 7080 7081 | - | - |
| Qlik Catalog Service | 4850 | - | - |
| NL Parser Service | 4952 | - | - |
| NL Broker Service | 4951 | - | - |
| NLApp Search Service | 4953 | ||
| BotChannel Service | 4954 |
| Service | Purpose |
|---|---|
| Qlik Sense Service Dispatcher (QSD) | Starts up the following services:
|
Information noteTo allow access to the file share, ensure that you open the Microsoft Windows SMB?port 445.
Ports used internally within a node
The ports in the following table are used between?Qlik Sense?services that run on the same node. In most cases, the ports do not have to be open through any firewalls.
| Service | Port | Direction | Purpose |
|---|---|---|---|
| Converter Service | 3003 | Internal | This port is used by the?Converter Service?which is utilized by?QlikView converter. |
| QPS | 4243 | Inbound | Qlik Sense Proxy Service?(QPS) REST API listen port. If web ticketing is used for security, this port is used by the software or service that requests tickets for users. If the software or service is remote, this port needs to be open to the location from which it is called. |
| QRD | 4432 | Internal | Default listen port for the?Qlik Sense Repository Database?(QRD). With shared persistence, this port is used to listen for connections from the?Qlik Sense Repository Service?(QRS). |
| Chart Sharing Service | 4555 | Internal | This port is used by the?Chart Sharing Service?for chart sharing between?Qlik Sense?users. The service is launched and managed by the?Qlik Sense Service Dispatcher?(QSD) when required. This port uses HTTPS for communication. |
| QRS | 4570 | Internal | Certificate password verification port, only used within multi-node sites by?Qlik Sense Repository Services (QRSs) on rim nodes to receive the password that unlocks a distributed certificate. The port can only be accessed from localhost and it is closed immediately after the certificate has been unlocked. The communication is always unencrypted. |
| QES | 4748 | Internal | This callback port is used by the?Qlik Sense Repository Service?(QRS) for sending HTTP events to the?Qlik Sense Engine Service?(QES). |
| Data Profiling Service | 4949 | Internal | This port is used by the?Data Profiling Service?to access and modify the app load data model. It communicates directly with the?Qlik Sense Engine Service?(QES) on the node. |
| Broker Service | 4900 | Internal | Default listen port for the?Broker Service. |
| Hub Service | 9028 | Internal | Default listen port for the?Hub Service. |
| Capability Service | 9031 | Internal | This port is used by the?Capability Service?to handle?Qlik Sense?system feature configuration. |
| About Service | 9032 | Internal | Default listen port for inbound calls to the?About Service. |
| Depgraph Service | 9079 | Internal | This port is used by the Service Dispatcher launched microservices. |
| Web Extension Service | 9080 | Internal | Default listen port for the?Web Extension Service. |
| DownloadPrep | 9090 | Internal | This port is used by the Service Dispatcher launched microservices. |
| On-demand App Service | 9098 | Internal | Default listen port for the?On-demand App Service. |
| Connector registry proxy (server) | 9041 | Internal | This port is used by the distributed connectivity service for discovering and listing connectors. |
| Connector registry proxy (desktop) | 9051 | Internal | This port is used by the distributed connectivity service for discovering and listing connectors. |
| Qlik?Notifier Service | 9081 | Internal | This port is used by the?Qlik?Notifier Service, which handles push notifications to mobile devices. It is installed on each node in a?Qlik Sense Enterprise?deployment. |
| Qlik?Mobility Registrar | 9082 | Internal | This port is used by the?Qlik?Mobility Registrar, which is installed on each node in a?Qlik Sense Enterprise?deployment. |
Ports used from user web browser
The default ports are exposed to the?Qlik Sense?users and need to be open through any firewalls in the site.
| Service | Port | Direction | Purpose | Host |
|---|---|---|---|---|
| QPS | 443 | Inbound | Inbound user web traffic when using HTTPS. | Qlik Sense Proxy Service?(QPS) in the site. |
| QPS | 80 | Inbound | Inbound user web traffic when using HTTP (optional). | Qlik Sense Proxy Service?(QPS) in the site. |
| Map | 443 | Inbound | User web traffic for standard map background. For users hosting their own map server, use the name of the host server. | maps.qlikcloud.com |
| Map | 443 | Inbound | User web traffic for satellite map background. Information noteAs of December 7, 2021, the server is ibasemaps-api.arcgis.com. Previously this was services.arcgisonline.com. | ibasemaps-api.arcgis.com |
The following diagram shows the ports used for the communication between a web browser and as single note site.
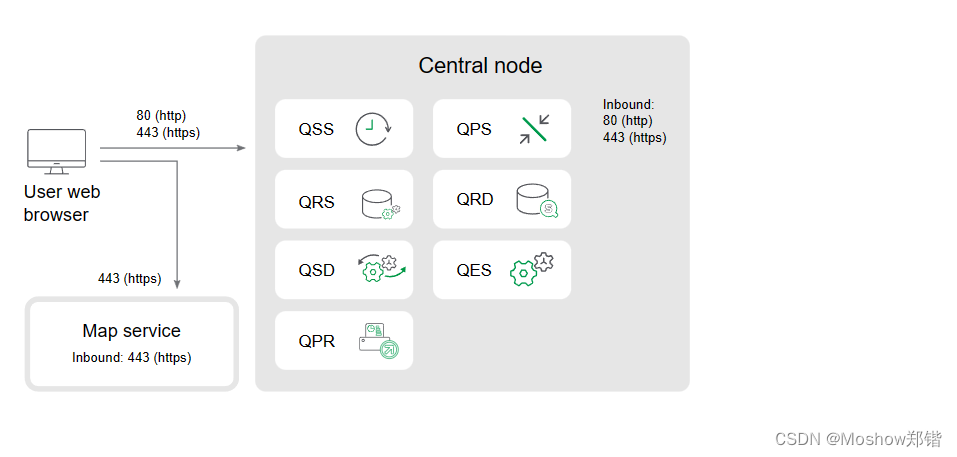
Ports used between nodes and?Qlik Sense?services
The ports in this section are used for communication between the?Qlik Sense?services.
In a single node site, all ports listed in this section are used by the various services, but do not need access through firewalls.
In a multi-node site, the ports in use vary depending on the services installed and running on each node. The ports need to be open in any firewalls between the nodes, but do not have to be open to the?Qlik Sense?users.
Minimum ports used for communication in multi-node sites
The following ports must always be open between the nodes in a multi-node site. The ports must be open to allow for service health, and some specific operations.
Information noteInbound ports indicate the listening ports for the services running on each node. Firewall rules must allow inbound traffic to these ports. Outbound ports indicate the destination of the communication from one node to other nodes in the environment. Firewall rules must allow the node to send outbound traffic to these outbound ports.
| Service | Port | Direction | Purpose |
|---|---|---|---|
| QRS | 4242 | Bi-directional between the central node and all proxy nodes | This port is used for a number of operations including new user registration. |
| QRD | 4432 | Inbound from?Qlik Sense?nodes to the repository database | The default listen port used by all nodes in a site for connecting to the?Qlik Sense Repository Database. |
| QRS | 4444 | Between the central node and all rim nodes | This port has two functions:
|
Ports used between manager and worker schedulers
The ports in the following table are used when a worker?Qlik Sense Scheduler Service?(QSS) is used.
| Service | Port | Direction | Purpose |
|---|---|---|---|
| QSS | 5050 | Inbound (from scheduler nodes only) | This port is used by the manager?QSS?on the central node to issue commands to and receive replies from worker?QSS?nodes. |
| QSS | 5151 | Inbound (from the central node only) | A worker?QSS?runs on a worker scheduler node and is accessed only by the manager?QSS?on the central node. |
Ports used between a proxy node and an engine node
The ports in the following table define the minimum needed to allow regular user traffic and load balancing between a proxy node and an engine node.
| Service | Port | Direction | Purpose |
|---|---|---|---|
| QES | 4747 | Inbound (from proxy nodes) | Qlik Sense Engine Service?(QES) listen port. This is the main port used by the?QES. The port is used via the?Qlik Sense Proxy Service?(QPS) for communication with the?Qlik Sense?clients. |
| QRS | 4239 | Inbound (from proxy nodes) | Qlik Sense Repository Service?(QRS) WebSocket port. The port is used via the?Qlik Sense Proxy Service?(QPS) by the?Qlik Sense?hub to obtain apps and stream lists. |
| QRS | 4242 | Inbound (from proxy nodes) | Qlik Sense Repository Service?(QRS) REST API listen port. This port is mainly accessed by local?Qlik Sense?services. However, the port must be open to all proxy nodes in a multi-node site to deliver images and static content. |
| Data Profiling Service | 4949 | Inbound (from proxy nodes) | This port is used by the?Data Profiling Service?when accessing and modifying the application load model. The service is launched and managed by the?Qlik Sense Service Dispatcher?(QSD) when required. The port is access via the?Qlik Sense Proxy Service?(QPS). |
| Broker Service | 4900 | Inbound (from proxy nodes) | Default listen port for the?Broker Service. |
| Hub Service | 9028 | Inbound (from proxy nodes) | Default listen port for the?Hub Service. Open for local services such as the broker service on the engine node. |
Ports used between a proxy node and a node running the printing service
The?Qlik Sense Printing Service?(QPR) may be installed on the same node as other services or on a separate node. The ports in the following table must be accessible between a?QPS?and all?QPRs to which the?QPS?can load balance traffic.
| Service | Port | Direction | Purpose |
|---|---|---|---|
| QPR | 4899 | Inbound (from proxy nodes) | Qlik Sense Printing Service?(QPR) port. This port is used for printed export in?Qlik Sense. The port is accessed by any node that runs a?QPS. |
Qlik Sense?Desktop ports
The following ports are used by?Qlik Sense?Desktop.
| Component | Port | Direction |
|---|---|---|
| Qlik associative engine?(including authentication) | 9076 | Internal |
| DataPrep Service | 9072 | Internal |
| Broker Service?(Desktop) | 4848 | Internal/inbound |
| Capability Service | 9075 | Internal |
| About Service | 9078 | Internal |
| Broker Service | 9070 | Internal |
| NPrinting | 9073 | Internal |
| Hub Service | 9071 | Internal |
| Converter Service | 9077 | Internal |
| Dependency Graph Service | 9033 | Internal |
| Web Extension Service | 9034 | Internal |
| Connector Registry Proxy | 9051 | Internal |
| NL Broker Service | 9055 | Internal |
| NL Parser Service | 9056 | Internal |
Qlik DataTransfer?ports
Qlik DataTransfer?uses the following ports:
| Service | Port | Direction |
|---|---|---|
| Secure web browser communication (HTTPS) Information noteYou must open this port in your firewall. | 443 | Outbound |
| Data Upload service | 5505 | Internal |
| Engine service | 5506 | Internal |
| Connector Registry proxy | 5507 | Internal |
Ports examples
This section provides examples of the ports that are used in different?Qlik Sense?deployments.
Information noteThe diagrams in this section do not show all outbound proxy node ports. For a full list of proxy node ports see the?Ports overview?table.
Single node site
This example shows the ports that are used in a single node site.
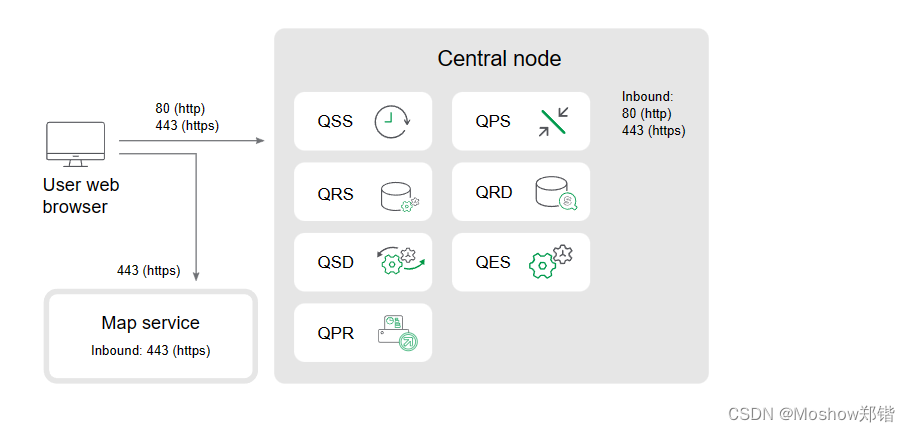
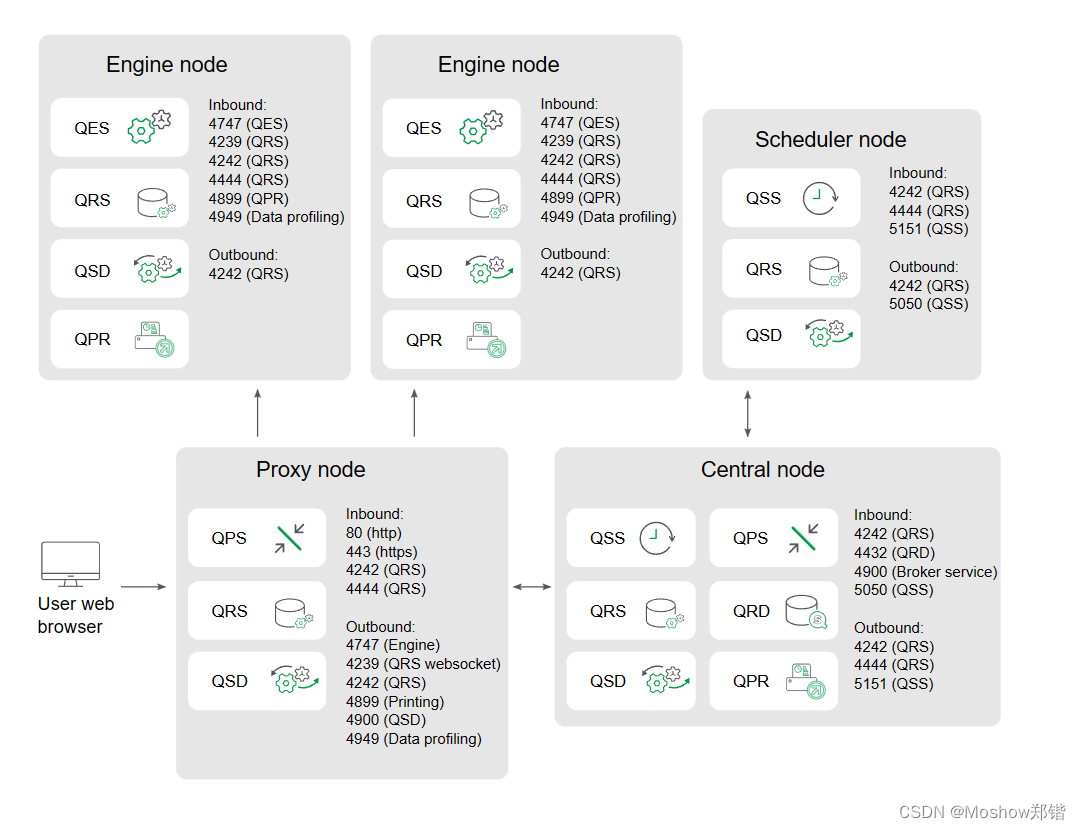
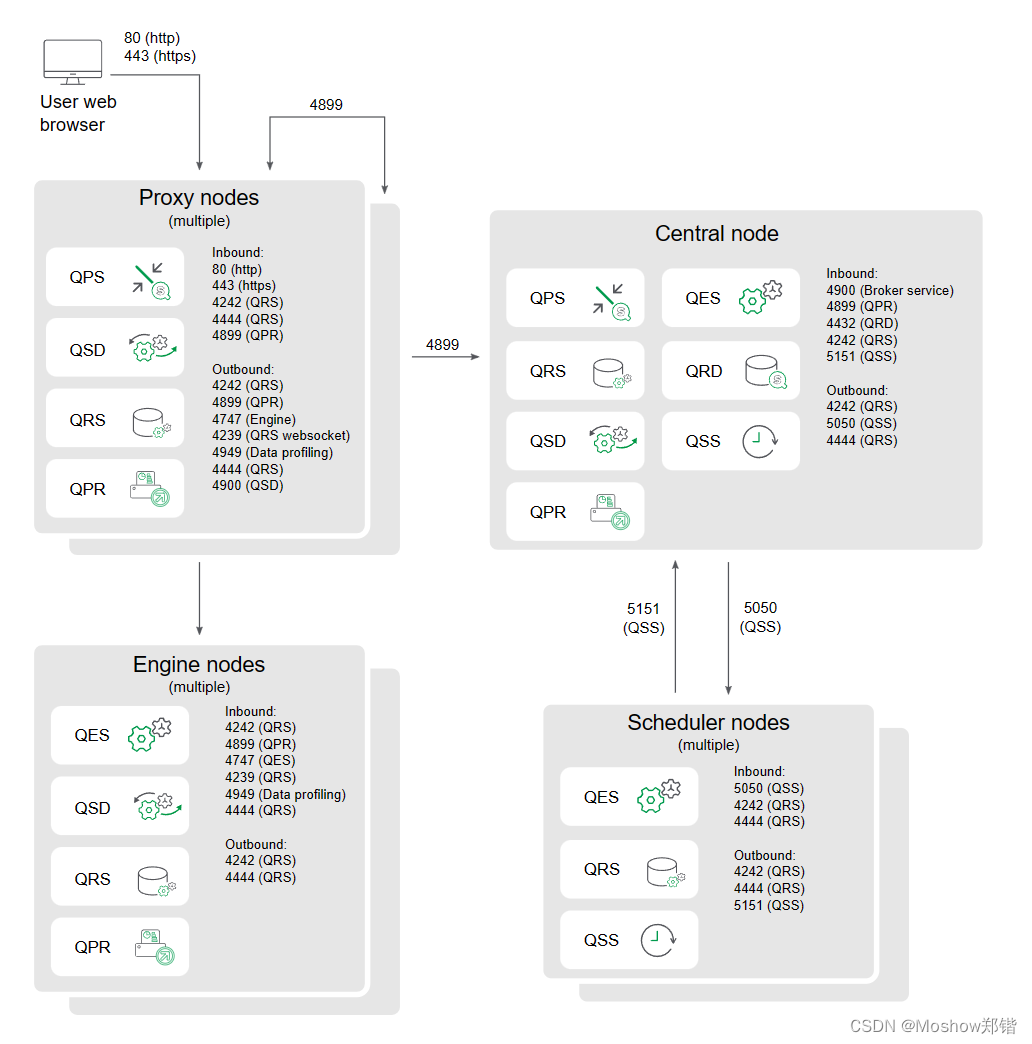
Multi-node site
The following is an example of the ports that are used in a multi-node site that consists of five nodes.
Inbound ports indicate the listening ports for the services running on each node. Firewall rules must allow inbound traffic to these ports. Outbound ports indicate the destination of the communication from one node to other nodes in the environment. Firewall rules must allow the node to send outbound traffic to these outbound ports.
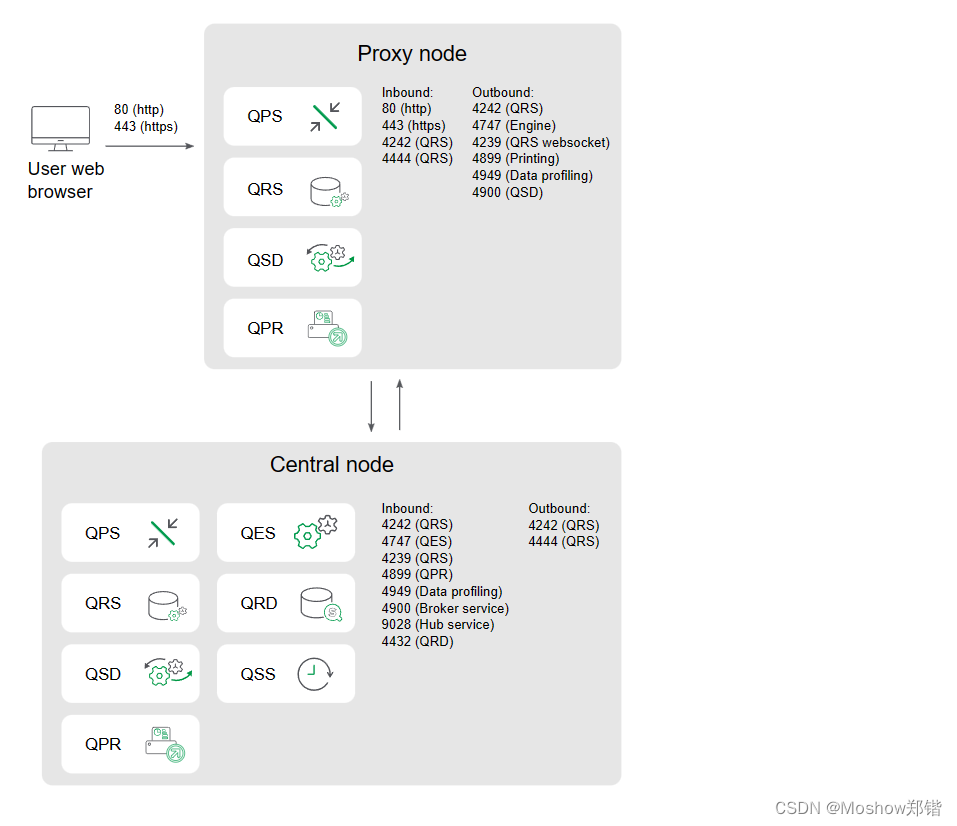
Proxy node in demilitarized zone
This example shows the ports that are used in a multi-node site when deploying a proxy node in a demilitarized zone.
Inbound ports indicate the listening ports for the services running on each node. Firewall rules must allow inbound traffic to these ports. Outbound ports indicate the destination of the communication from one node to other nodes in the environment. Firewall rules must allow the node to send outbound traffic to these outbound ports.
Separate proxy and engine node
This example shows the ports that are used in a multi-node site when deploying a separate proxy and engine node. The proxy load balancing excludes the engine on the central node.
Inbound ports indicate the listening ports for the services running on each node. Firewall rules must allow inbound traffic to these ports. Outbound ports indicate the destination of the communication from one node to other nodes in the environment. Firewall rules must allow the node to send outbound traffic to these outbound ports.
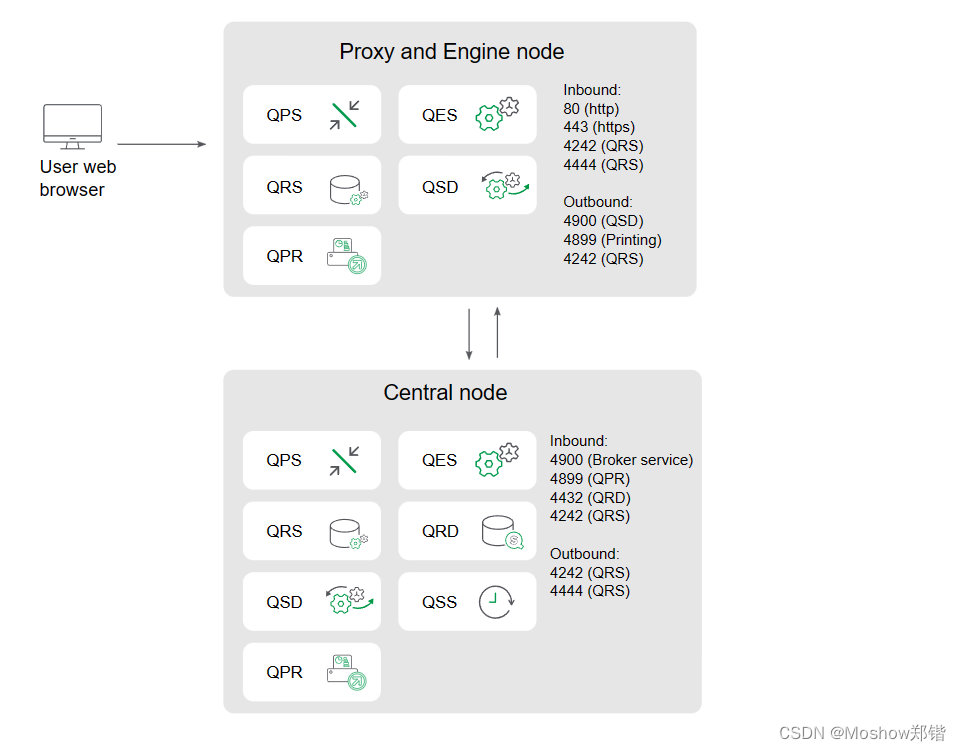
High availability proxy and engine nodes
This example shows the ports that are used in a multi-node site when deploying more than one proxy and engine node. The proxy load balancing excludes the engine on the central node.
Inbound ports indicate the listening ports for the services running on each node. Firewall rules must allow inbound traffic to these ports. Outbound ports indicate the destination of the communication from one node to other nodes in the environment. Firewall rules must allow the node to send outbound traffic to these outbound ports.
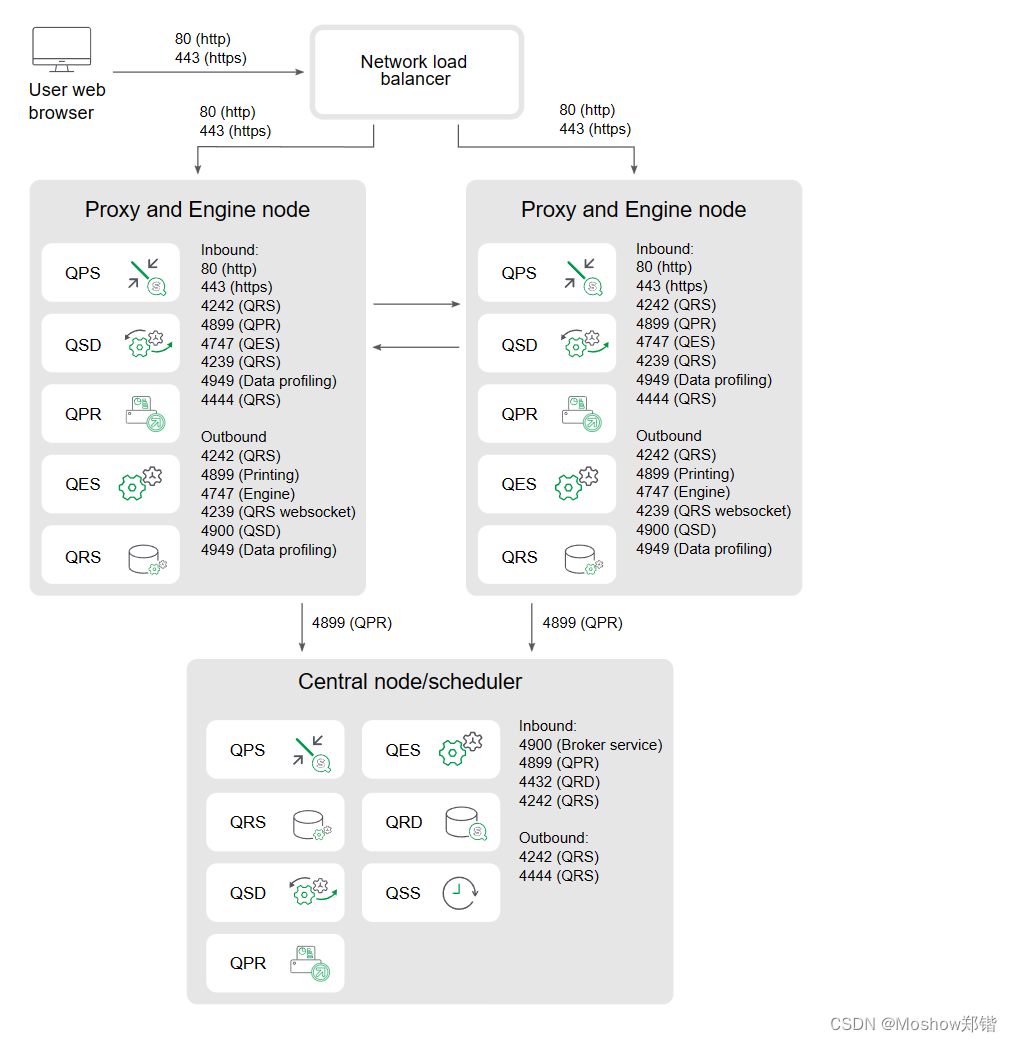
Separate scheduler node and high availability proxy and engine nodes
This example shows the ports that are used in a multi-node site when deploying a separate scheduler node and more than one proxy and engine node. The proxy load balancing excludes the engine on the central node.
Inbound ports indicate the listening ports for the services running on each node. Firewall rules must allow inbound traffic to these ports. Outbound ports indicate the destination of the communication from one node to other nodes in the environment. Firewall rules must allow the node to send outbound traffic to these outbound ports.
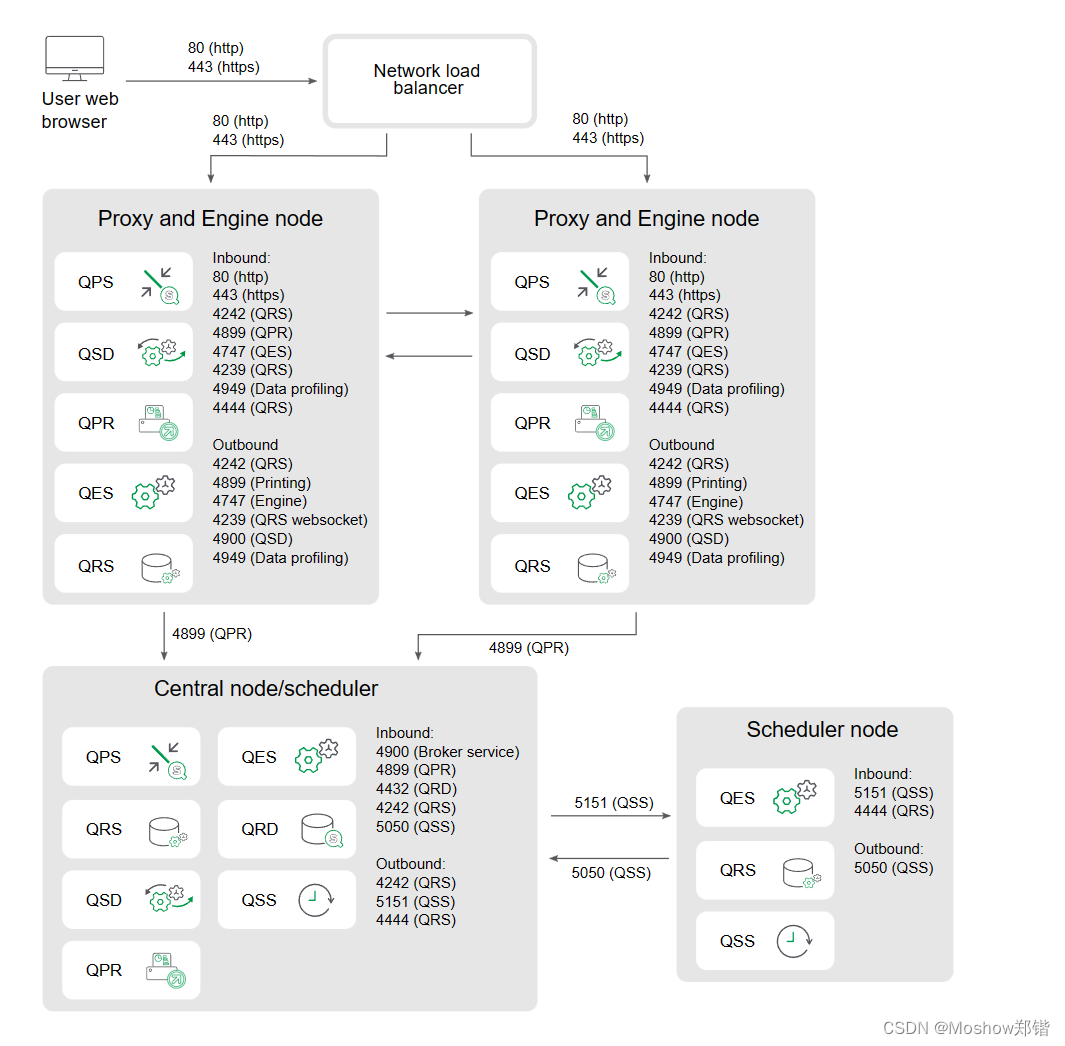
Separate proxy and scheduler nodes and high availability engine nodes
This example shows the ports that are used in a multi-node site when deploying separate proxy and scheduler nodes and more than one engine node. The proxy load balancing excludes the engine on the central node.
Inbound ports indicate the listening ports for the services running on each node. Firewall rules must allow inbound traffic to these ports. Outbound ports indicate the destination of the communication from one node to other nodes in the environment. Firewall rules must allow the node to send outbound traffic to these outbound ports.
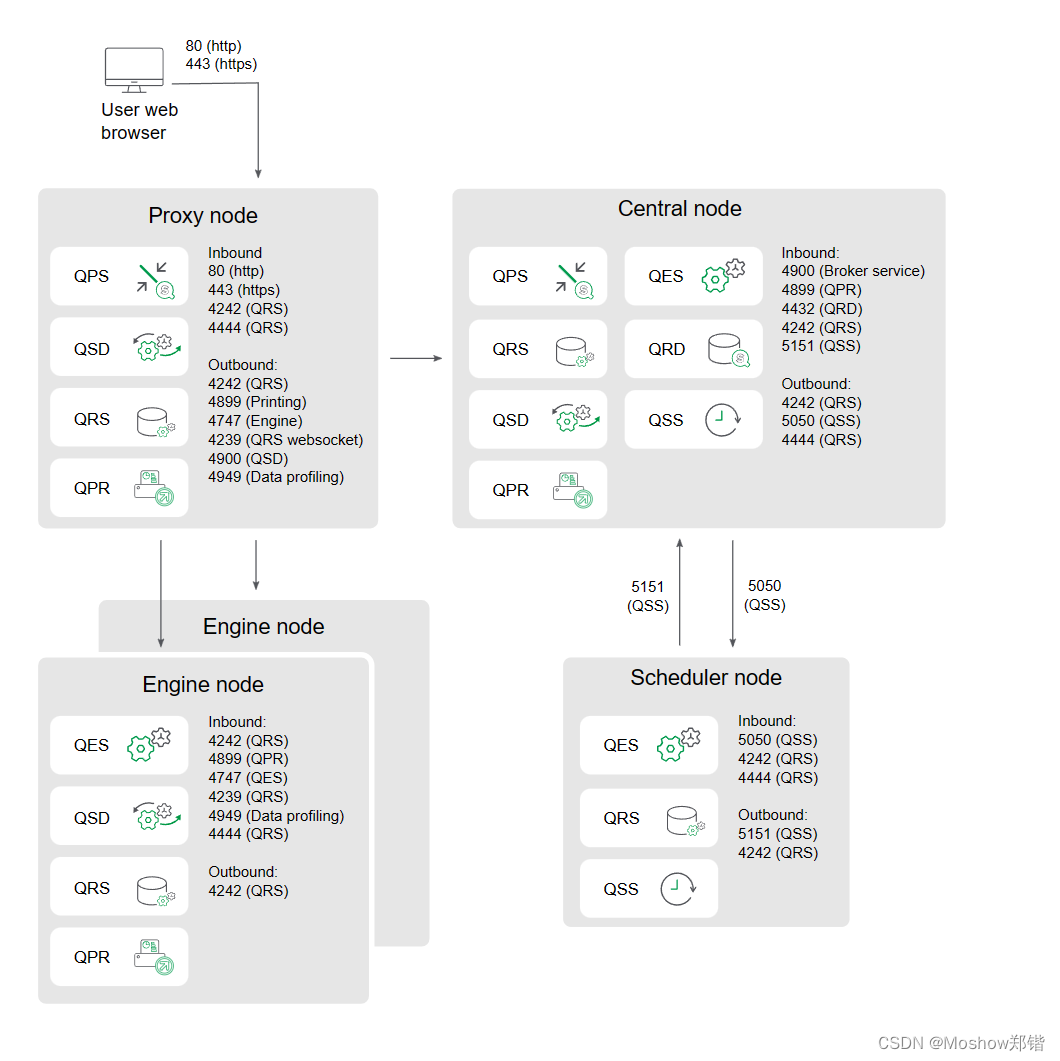
Generic scale out
This example shows the ports that are used in a multi-node site when scaling the site by adding additional proxy, engine, or scheduler nodes. The proxy load balancing excludes the engine on the central node.
Inbound ports indicate the listening ports for the services running on each node. Firewall rules must allow inbound traffic to these ports. Outbound ports indicate the destination of the communication from one node to other nodes in the environment. Firewall rules must allow the node to send outbound traffic to these outbound ports.
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
- Python教程
- 深入理解 MySQL 中的 HAVING 关键字和聚合函数
- Qt之QChar编码(1)
- MyBatis入门基础篇
- 用Python脚本实现FFmpeg批量转换
- 【Spark精讲】Spark五种JOIN策略
- Vue3组件库开发 之Button(1)
- 网工内推 | 网络服务工程师,HCIE认证优先,带薪年假,年终奖
- LeetCode 1154. 一年中的第几天:2023年最后一道每日一题
- K8S学习指南(33)-k8s权限管理模型RBAC
- 基于Java SSM框架实现课程思政元素收集系统项目【项目源码+论文说明】
- 苹果MacOS12系统 Monterey最新正式版下载 MacOS12系统镜像包
- Java版企业电子招标采购系统源码Spring Cloud + Spring Boot +二次开发+ MybatisPlus + Redis
- OpenSource - 基于Netty的网络扩展库HServer
- 第一次在RUST官方论坛上留言发布我的Rust板箱