rhel7/centos7升级openssh到openssh9.5-p1
openssh9.3-p2以下版本有如下漏洞

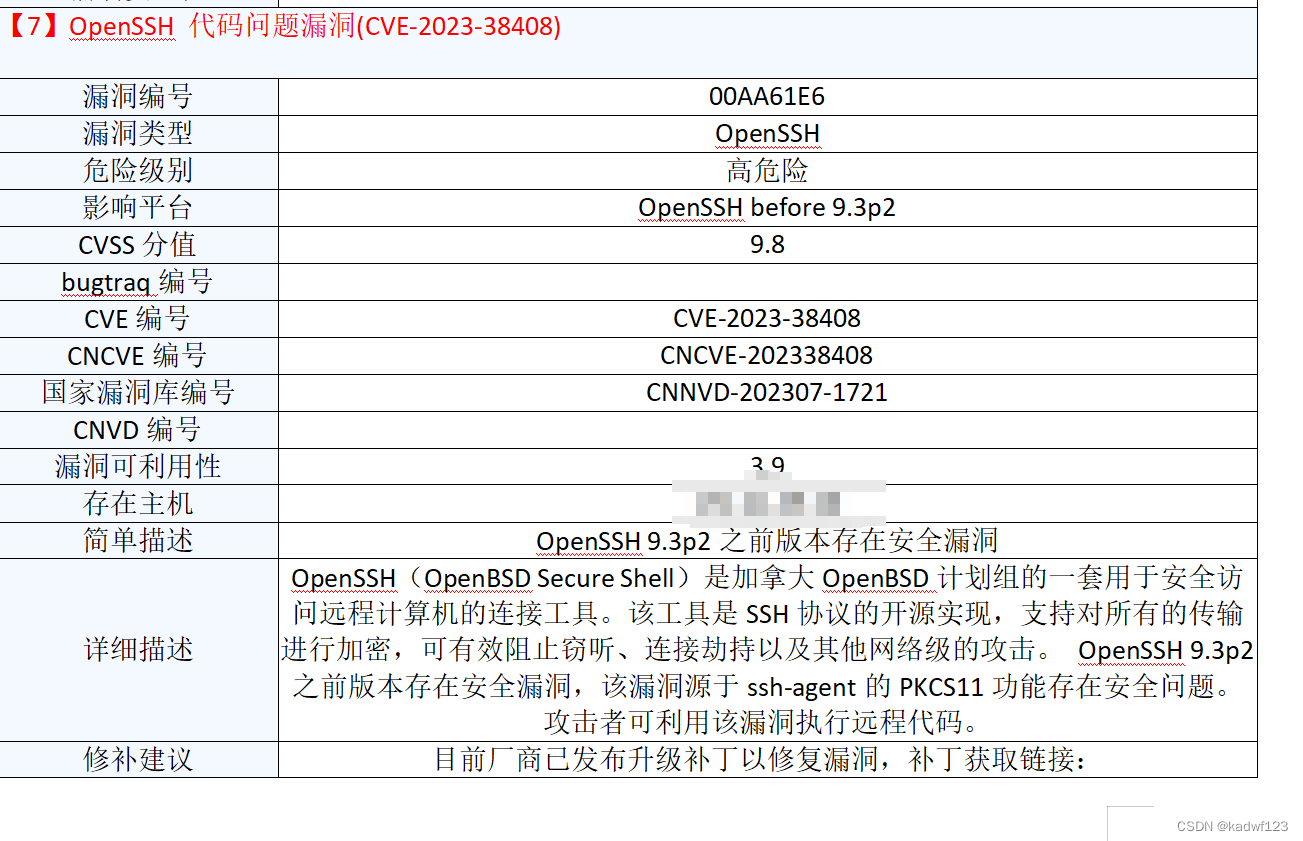
在rhel7.4/7.5/7.6均做过测试。
本文需要用到的rpm包如下:
https://download.csdn.net/download/kadwf123/88652359
升级步骤
1、升级前启动telnet
##升级前启动telnet服务
yum -y install telnet-server
yum -y install xinetd
yum -y install telnet
systemctl restart telnet.socket
systemctl restart xinetd
##注意:默认telnet远程连接不能使用root用户。
?
2、升级openssl到1.1.1w
##升级openssl到1.1.1w
cd /root/rpmbuild/RPMS/x86_64/
rpm -ivh ?openssl-1.1.1w-1.el7.x86_64.rpm openssl-devel-1.1.1w-1.el7.x86_64.rpm --force --nodeps
[root@cdm421 ~]# rpm -qa | grep openssl
xmlsec1-openssl-1.2.20-7.el7_4.x86_64
openssl-1.0.2k-25.el7_9.x86_64
openssl-devel-1.1.1w-1.el7.x86_64
openssl098e-0.9.8e-29.el7_2.3.x86_64
openssl-libs-1.0.2k-25.el7_9.x86_64
openssl-devel-1.0.2k-25.el7_9.x86_64
openssl-1.1.1w-1.el7.x86_64
rpm -e openssl-1.0.2k-25.el7_9.x86_64 openssl-devel-1.0.2k-25.el7_9.x86_64 --nodeps
[root@cdm421 ~]# rpm -qa | grep openssl
xmlsec1-openssl-1.2.20-7.el7_4.x86_64
openssl-devel-1.1.1w-1.el7.x86_64
openssl098e-0.9.8e-29.el7_2.3.x86_64
openssl-libs-1.0.2k-25.el7_9.x86_64
openssl-1.1.1w-1.el7.x86_64
openssl version
root@hostdb2[/root]#openssl version
OpenSSL 1.1.1w ?11 Sep 2023
?
3、升级openssh到9.5-p1
##升级openssh前备份
mkdir ~/ssh_bak
mkdir ~/ssh_bak/service
mkdir ~/ssh_bak/pam.d/
# 备份PAM配置
cp /etc/pam.d/* ?~/ssh_bak/pam.d/
# 备份sshd_config
cp /etc/ssh/sshd_config ~/ssh_bak/
# 备份sshd的启动服务
cp /usr/lib/systemd/system/sshd* ~/ssh_bak/service/
# 备份ssh环境变量文件
cp /etc/sysconfig/sshd ?~/ssh_bak/
rpm -qa | grep openssh
[root@cdm421 ~]# rpm -qa | grep openssh
openssh-server-7.4p1-22.el7_9.x86_64
openssh-7.4p1-22.el7_9.x86_64
openssh-clients-7.4p1-22.el7_9.x86_64
rpm -ivh openssh-9.5p1-1.el7.x86_64.rpm openssh-clients-9.5p1-1.el7.x86_64.rpm openssh-server-9.5p1-1.el7.x86_64.rpm --force
rpm -qa | grep openssh
[root@cdm421 ~]# rpm -qa | grep openssh
openssh-server-7.4p1-22.el7_9.x86_64
openssh-9.5p1-1.el7.x86_64
openssh-7.4p1-22.el7_9.x86_64
openssh-clients-7.4p1-22.el7_9.x86_64
openssh-clients-9.5p1-1.el7.x86_64
openssh-server-9.5p1-1.el7.x86_64
rpm -e openssh-server-7.4p1-22.el7_9.x86_64 openssh-7.4p1-22.el7_9.x86_64 openssh-clients-7.4p1-22.el7_9.x86_64
[root@cdm421 ~]# rpm -qa | grep openssh
openssh-9.5p1-1.el7.x86_64
openssh-clients-9.5p1-1.el7.x86_64
openssh-server-9.5p1-1.el7.x86_64
chmod 0600 /etc/ssh/ssh_host_rsa_key
chmod 0600 /etc/ssh/ssh_host_ecdsa_key
chmod 0600 /etc/ssh/ssh_host_ed25519_key
恢复PAM设置
cp -f ~/ssh_bak/sshd /etc/pam.d/
chmod 0400 /etc/ssh/ssh_host_*
##恢复配置文件(可选)
###注意,该步骤为可选步骤,仅在服务启动失败时供排查报错或者恢复配置使用!
###(我这边实际测试需要恢复/etc/pam.d/sshd,否则能正常启动sshd服务,
###但是远程ssh连接的时候报错PAM unable to dlopen(/usr/lib64/security/pam_stack.so): /usr/lib64/security/pam_stack.so)
###另外两个是都要恢复,如果不恢复,重启os后会有问题,sshd服务起不来
cp -f ~/ssh_bak/sshd /etc/sysconfig/sshd
cp -f ~/ssh_bak/pam.d/sshd /etc/pam.d/sshd
cp -f ~/ssh_bak/service/* /usr/lib/systemd/system/
vi /etc/ssh/sshd_config?
PermitRootLogin yes
取消上面的root远程登录的注释
vi /usr/lib/systemd/system/sshd.service?
[Service]下新增
Type=simple
?
systemctl restart sshd
systemctl status sshd
?
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!