BUUCTF--[FlareOn6]Overlong 无需动态调试,直接写脚本
发布时间:2024年01月23日
BUUCTF–[FlareOn6]Overlong 无需动态调试,直接写脚本
发现网上的多半都是采用的动态调试的方法,但是动调得到的flag不能直接复制粘贴啊,再加上有些小伙伴可能用不惯OD,所以这里给出一种新的解决思路
查壳

32位,无壳
拖入IDA
分析代码

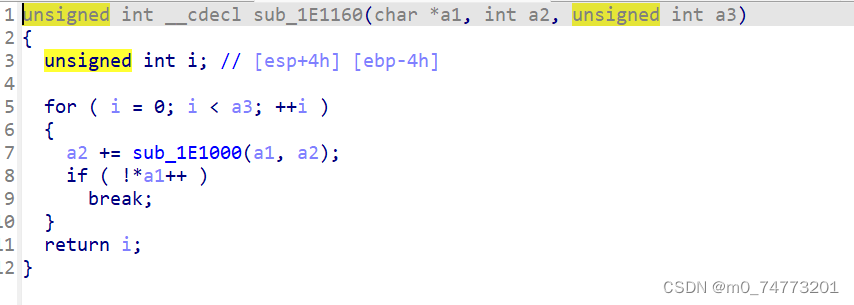
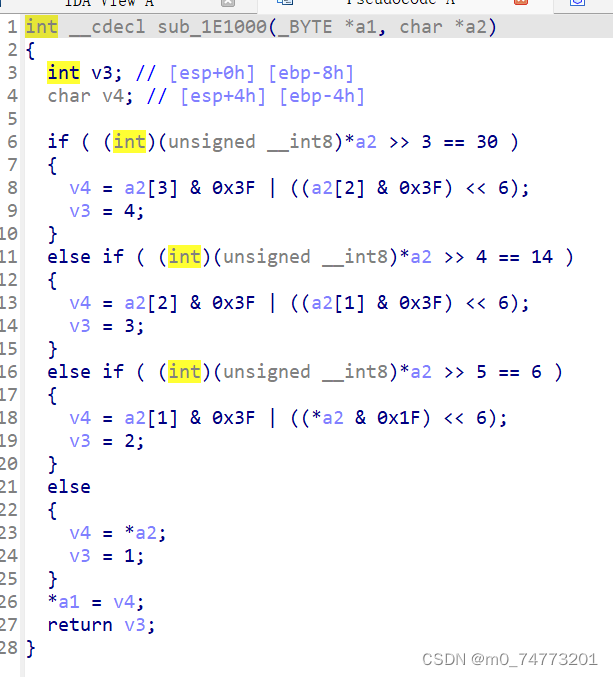
一共只有三个函数,结构比较简单。猜测flag应该和text有关,先把text还原出来。
写脚本
a2=[0xe0,0x81,0x89,0xc0,0xa0,0xc1,0xae,0xe0,0x81,0xa5,
0xc1,0xb6,0xf0,0x80,0x81,0xa5,0xe0,0x81,0xb2,0xf0,
0x80,0x80,0xa0,0xe0,0x81,0xa2,0x72,0x6f,0xc1,0xab,
0x65,0xe0,0x80,0xa0,0xe0,0x81,0xb4,0xe0,0x81,0xa8,
0xc1,0xa5,0x20,0xc1,0xa5,0xe0,0x81,0xae,0x63,0xc1,
0xaf,0xe0,0x81,0xa4,0xf0,0x80,0x81,0xa9,0x6e,0xc1,
0xa7,0xc0,0xba,0x20,0x49,0xf0,0x80,0x81,0x9f,0xc1,
0xa1,0xc1,0x9f,0xc1,0x8d,0xe0,0x81,0x9f,0xc1,0xb4,
0xf0,0x80,0x81,0x9f,0xf0,0x80,0x81,0xa8,0xc1,0x9f,
0xf0,0x80,0x81,0xa5,0xe0,0x81,0x9f,0xc1,0xa5,0xe0,
0x81,0x9f,0xf0,0x80,0x81,0xae,0xc1,0x9f,0xf0,0x80,
0x81,0x83,0xc1,0x9f,0xe0,0x81,0xaf,0xe0,0x81,0x9f,
0xc1,0x84,0x5f,0xe0,0x81,0xa9,0xf0,0x80,0x81,0x9f,
0x6e,0xe0,0x81,0x9f,0xe0,0x81,0xa7,0xe0,0x81,0x80,
0xf0,0x80,0x81,0xa6,0xf0,0x80,0x81,0xac,0xe0,0x81,
0xa1,0xc1,0xb2,0xc1,0xa5,0xf0,0x80,0x80,0xad,0xf0,
0x80,0x81,0xaf,0x6e,0xc0,0xae,0xf0,0x80,0x81,0xa3,
0x6f,0xf0,0x80,0x81,0xad,0x0]
flag=[]
j=0
for i in range(28):
if a2[j]>>3==30:
v4=a2[j+3]&0x3f|((a2[j+2]&0x3f)<<6)
v3=4
elif a2[j]>>4==14:
v4 = a2[j+2] & 0x3F | ((a2[j+1] & 0x3F) << 6)
v3 = 3
elif a2[j] >> 5 == 6:
v4 = a2[j+1] & 0x3F | ((a2[j] & 0x1F) << 6)
v3 = 2
else:
v4=a2[j]
v3=1
flag.append(chr(v4))
j+=v3
for x in flag:
print(x,end='')
其中a2为unk_1E2008处的数据,运行结果为
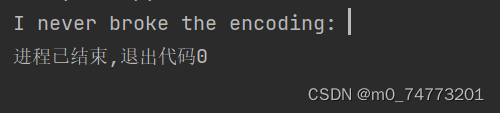
直接运行exe文件的结果为
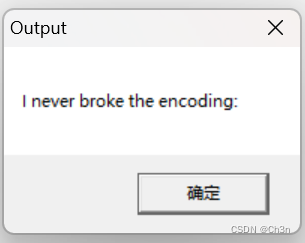
可以看到和直接运行程序时得到的结果一样,然而,我们的a2可是有一百多位,这样还原大概连a2的一半都没用到,再加上encording后是一个冒号,后面应该还是有东西的,于是增加解密次数至68,再次运行
a2=[0xe0,0x81,0x89,0xc0,0xa0,0xc1,0xae,0xe0,0x81,0xa5,
0xc1,0xb6,0xf0,0x80,0x81,0xa5,0xe0,0x81,0xb2,0xf0,
0x80,0x80,0xa0,0xe0,0x81,0xa2,0x72,0x6f,0xc1,0xab,
0x65,0xe0,0x80,0xa0,0xe0,0x81,0xb4,0xe0,0x81,0xa8,
0xc1,0xa5,0x20,0xc1,0xa5,0xe0,0x81,0xae,0x63,0xc1,
0xaf,0xe0,0x81,0xa4,0xf0,0x80,0x81,0xa9,0x6e,0xc1,
0xa7,0xc0,0xba,0x20,0x49,0xf0,0x80,0x81,0x9f,0xc1,
0xa1,0xc1,0x9f,0xc1,0x8d,0xe0,0x81,0x9f,0xc1,0xb4,
0xf0,0x80,0x81,0x9f,0xf0,0x80,0x81,0xa8,0xc1,0x9f,
0xf0,0x80,0x81,0xa5,0xe0,0x81,0x9f,0xc1,0xa5,0xe0,
0x81,0x9f,0xf0,0x80,0x81,0xae,0xc1,0x9f,0xf0,0x80,
0x81,0x83,0xc1,0x9f,0xe0,0x81,0xaf,0xe0,0x81,0x9f,
0xc1,0x84,0x5f,0xe0,0x81,0xa9,0xf0,0x80,0x81,0x9f,
0x6e,0xe0,0x81,0x9f,0xe0,0x81,0xa7,0xe0,0x81,0x80,
0xf0,0x80,0x81,0xa6,0xf0,0x80,0x81,0xac,0xe0,0x81,
0xa1,0xc1,0xb2,0xc1,0xa5,0xf0,0x80,0x80,0xad,0xf0,
0x80,0x81,0xaf,0x6e,0xc0,0xae,0xf0,0x80,0x81,0xa3,
0x6f,0xf0,0x80,0x81,0xad,0x0]
flag=[]
j=0
for i in range(68):
if a2[j]>>3==30:
v4=a2[j+3]&0x3f|((a2[j+2]&0x3f)<<6)
v3=4
elif a2[j]>>4==14:
v4 = a2[j+2] & 0x3F | ((a2[j+1] & 0x3F) << 6)
v3 = 3
elif a2[j] >> 5 == 6:
v4 = a2[j+1] & 0x3F | ((a2[j] & 0x1F) << 6)
v3 = 2
else:
v4=a2[j]
v3=1
flag.append(chr(v4))
j+=v3
for x in flag:
print(x,end='')
运行结果就变成了
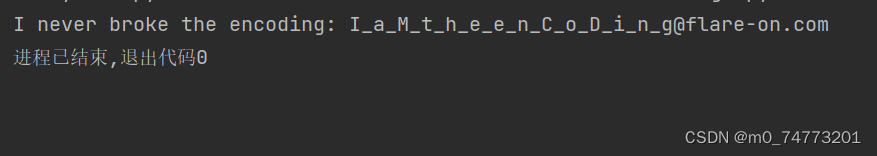
冒号之后的即为flag
补充
如果用动调来解决的话,同样只需把28(0x1C)改成68(0x44)即可,并不需要改到175,该成68是因为整段text一共就68个字符,所以只要编译到68就行了,改成175完全是没有逻辑的
文章来源:https://blog.csdn.net/m0_74773201/article/details/135758039
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
最新文章
- Python教程
- 深入理解 MySQL 中的 HAVING 关键字和聚合函数
- Qt之QChar编码(1)
- MyBatis入门基础篇
- 用Python脚本实现FFmpeg批量转换
- 【Linux】线程控制:线程创建、终止、等待、分离等
- PostgreSQL学习笔记01
- [论文分享]TimesURL:通用时间序列表示学习的自监督对比学习
- Standoff 12 网络演习
- 桃红葡萄酒是如何成为当代宠儿的?
- 字符串排序 sort(str.begin(),str.end(),greater<>())
- Origin 或 Referer 的关系和区别
- 为什么ChatGPT采用SSE协议而不是Websocket?
- 企业如何实现数字化转型?有哪些好处(下)
- 基于springboot+vue网上图书商城(程序+数据库+文档)