跨区域大型医院的网络设计与搭建
背景
? ? ? ?随着社会的发展,企业信息化建设的推进,全国各大中型企业基本上都有了自己的网络,作为医院的决策者们来说,建立高速的网络,使信息流通更快速,将医院建成信息化的高效的医院,使医院立于不败之林。由于邳州人民医院的网络业务量并不大,主要应用是医院内部的信息传递,除此之外,Http、Ftp、Email便是医院与Internet连接的最大流量了。从技术上讲应该采用标准、开放、可扩充的、能与其它厂商产品配套使用的设计。根据用户的总体需求,结合对应用系统的考虑,我们提出网络系统的设计的原则是:可靠的技术选型、标准的体系结构、1000M骨干网、安全性较高、运行性能可靠以及遵循面向应用,注重实效,急用先上,逐步完善的原则。?
- 实用性:根椐应用系统的要求确定整个系统的结构,即从系统功能和信息需求出发,拟建系统的结构必须满足系统的传输能力要求、信息安全要求、人机交互能力要求、信息处理要求等;
- ?先进性:以先进、成熟的网络通信技术进行组网,并能确保网络技术和网络产品几年内不落后;
- ?可靠性:系统必须可靠运行;
- ?开放性:选择的产品应具有好的互操作性和可移植性,并符合相关的国际标准和工业标准;
- ?可扩充性:系统是一个逐步发展的应用环境,在系统结构、产品系统、系统容量与处理能力等方面必须具有升级换代的可能,这种扩充不仅能充分保护原有资源,而且具有较高的性能价格比,使整个网络系统是可扩展的,便于系统升级,改装;
- ?可伸缩性原则:网络的建设是一项持续性的系统工程项目,坚持网络建设规模的可伸缩性原则,将使得网络的建设费用降低,避免不必要的浪费,也体现了网络建设的灵活性;
- ?安全性:信息系统安全问题的中心任务是保证信息网络的畅通,确保授权实体经过该网络安全地获取信息,并保证该信息的完整和可靠。网络系统的每一个环节都可能造成安全与可靠性问题。
拓扑图如下:
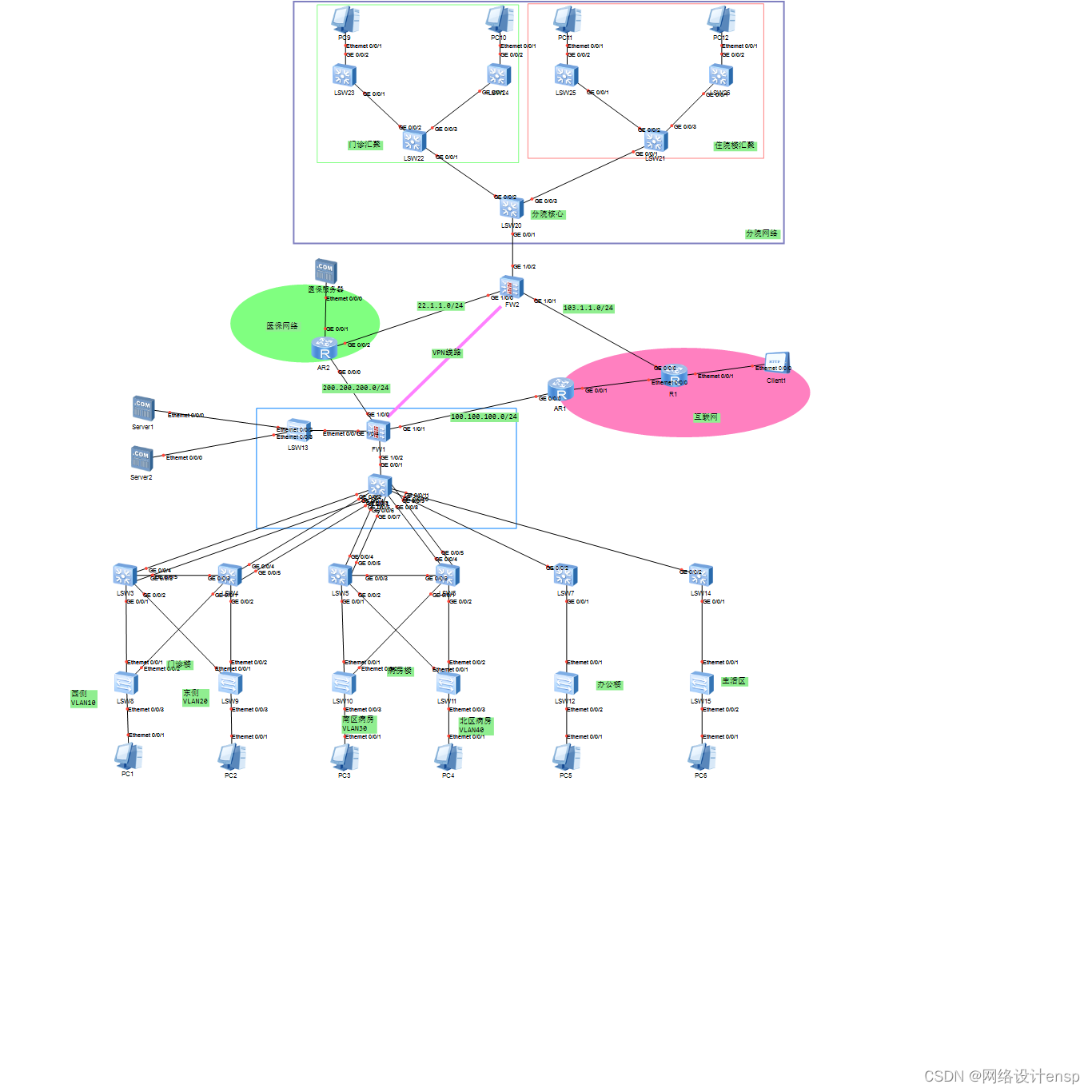
部门vlan划分及IP地址
| 网络用户 | IP网段 | 网关 | 所属VLAN |
| 门诊楼西侧 | 192.168.10.0/24 | 192.168.10.254 | Vlan10 |
| 门诊楼东侧 | 192.168.20.0/24 | 192.168.20.254 | VLAN20 |
| 病房南区 | 192.168.30.0/24 | 192.168.30.254 | VLAN30 |
| 病房北区 | 192.168.40.0/24 | 192.168.40.254 | VLAN40 |
| 办公楼网络 | 192.168.50.0/24 | 192.168.50.254 | VLAN50 |
| 生活区 | 192.168.60.0/24 | 192.168.60.254 | VLAN60 |
| 服务器 | 192.168.200.0/24 | 192.168.200.254 | - |
| 分院 | |||
| 门诊1# | 10.1.10.0/24 | 10.1.10.254 | 10 |
| 门诊2# | 10.1.20.0/24 | 10.1.20.254 | 20 |
| 住院楼1# | 10.1.30.0/24 | 10.1.30.254 | 30 |
| 住院楼2# | 10.1.40.0/24 | 10.1.40.254 | 40 |
网络配置实施
本院配置
接入二层划分vlan、以及接口配置
将每层的1-21口进行Access的vlan划分 ?23-24口为上行接口
[ACC-L1]port-group ?group-member ?GigabitEthernet ?0/0/1 to ?GigabitEthernet 0/0/21
[ACC-L1-port-group]port link-type access
[ACC-L1-port-group]port default ?vlan ?10
[ACC-L1]int g0/0/24
[ACC-L1-GigabitEthernet0/0/24]port link-type trunk ?
[ACC-L1-GigabitEthernet0/0/24]port trunk allow-pass vlan all
[ACC-L1]int g0/0/23
[ACC-L1-GigabitEthernet0/0/23]port link-type trunk ?
[ACC-L1-GigabitEthernet0/0/23]port trunk allow-pass vlan all
其他设备相同配置即可
三层SIV接口配置及vrrp配置
interface Vlanif10
?ip address 192.168.10.1?255.255.255.0
vrrp vrid 10 virtual-ip 192.168.10.254
vrrp vrid 10?priority 120
interface Vlanif10
?ip address 192.168.10.2?255.255.255.0
?vrrp vrid 10 virtual-ip 192.168.10.254
配置MSTP
stp region-configuration ???//进入MSTP模式
region-name huawei ???????????//配置域名为huawei
instance 1 vlan 10 ?????//将vlan10 加入实例1中
instance 2 vlan 20 ?????//将vlan20加入实例2中
active region-configuration ?//激活配置
stp instance 1 root primary ????//指定本交换机为主根桥
stp instance 2?root sec?????//指定本交换机为次根桥
其他部分的mstp?与vrrp配置相同
链路聚合配置
在两台汇聚交换机间设置链路聚合,关键代码如下:
interface eth-trunk 0?????//创建ID为0的Eth-Trunk接口
trunkport GigabitEthernet 0/0/23 to 0/0/24 ???将 23??24号口加入到聚合组中
(对端配置完全相同)
路由协议OSPF配置
[Huawei]ospf 1
[Huawei-ospf-1]a 0
[Huawei-ospf-1-area-0.0.0.0]network ?192.168.0.0 0.0.255.255
//出口设备需要配置如下命令:
[USG6000V1]ip route-static 0.0.0.0 0 100.100.100.254
[USG6000V1-ospf-1]default-route-advertise
配置出口防火墙安全策略
security-policy
?rule name vpn-data
??source-zone dmz
??source-zone trust
??source-zone untrust
??destination-zone dmz
??destination-zone trust
??destination-zone untrust
??source-address 10.1.0.0 mask 255.255.0.0
??source-address 192.168.0.0 mask 255.255.0.0
??destination-address 10.1.0.0 mask 255.255.0.0
??destination-address 192.168.0.0 mask 255.255.0.0
??action permit
?rule name deny ??//拒绝门诊访问互联网
??source-zone trust
??destination-zone untrust
??source-address 192.168.10.0 mask 255.255.255.0
??source-address 192.168.20.0 mask 255.255.255.0
??action deny
?rule name Server
??source-zone trust
??destination-zone dmz
??destination-address 192.168.200.0 mask 255.255.255.0
??action permit
?rule name ISP
??source-zone trust
??destination-zone untrust
??source-address 192.168.30.0 mask 255.255.255.0
??source-address 192.168.40.0 mask 255.255.255.0
??source-address 192.168.50.0 mask 255.255.255.0
??source-address 192.168.60.0 mask 255.255.255.0
??action permit
?rule name YB
??source-zone trust
??destination-zone YB
??action permit
?rule name Nat-server
??source-zone untrust
??destination-zone dmz
??destination-address 192.168.200.200 mask 255.255.255.255
??action permit
?rule name vpn
??source-zone local
??source-zone untrust
??destination-zone local
??destination-zone untrust
??source-address 100.100.100.1 mask 255.255.255.255
??source-address 103.1.1.1 mask 255.255.255.255
??destination-address 100.100.100.1 mask 255.255.255.255
??destination-address 103.1.1.1 mask 255.255.255.255
??action permit
外网路由及NAT配置
nat-policy
?rule name ISP
??source-zone trust
??destination-zone untrust
??source-address 192.168.30.0 mask 255.255.255.0
??source-address 192.168.40.0 mask 255.255.255.0
??source-address 192.168.50.0 mask 255.255.255.0
??source-address 192.168.60.0 mask 255.255.255.0
??action source-nat easy-ip
?rule name YB
??source-zone trust
??destination-zone YB
??action source-nat easy-ip
医保网路由配置
配置多出口路由
[USG6000V1]ip route-static 123.123.123.0 24 200.200.200.254 ?//去往医保服务器
VPN配置
总院
[USG6000V1]acl 3000
[USG6000V1-acl-adv-3000] rule permit ?ip source ?192.168.0.0 0.0.255.255 ???destination 10.1.0.0 0.0.255.255
[USG6000V1]ike proposal 1
[USG6000V1-ike-proposal-1]q
[USG6000V1]ike peer fw1
[USG6000V1-ike-peer-fw1]pre-shared-key admin@123
[USG6000V1-ike-peer-fw1] ike-proposal 1
[USG6000V1-ike-peer-fw1] remote-address 103.1.1.1
[USG6000V1]ipsec proposal 1
[USG6000V1]ipsec policy p1 10 isakmp ?
[USG6000V1-ipsec-policy-isakmp-p1-10]ike-peer fw1
[USG6000V1-ipsec-policy-isakmp-p1-10]proposal 1
[USG6000V1-ipsec-policy-isakmp-p1-10]tunnel local 100.100.100.1
[USG6000V1-ipsec-policy-isakmp-p1-10]security ?acl 3000
[USG6000V1]int g1/0/1
[USG6000V1-GigabitEthernet1/0/1]ipsec policy ?p1
分院
[USG6000V1]acl 3000
[USG6000V1-acl-adv-3000]rule permit ?ip source ?10.1.0.0 0.0.255.255 destination 192.168.0.0 0.0.255.255
[USG6000V1]ike proposal 1
[USG6000V1-ike-proposal-1]q
[USG6000V1]ike peer fw1
[USG6000V1-ike-peer-fw1]pre-shared-key admin@123
[USG6000V1-ike-peer-fw1] ike-proposal 1
[USG6000V1-ike-peer-fw1] remote-address 100.100.100.1
[USG6000V1]ipsec proposal 1
[USG6000V1]ipsec policy p1 10 isakmp ?
[USG6000V1-ipsec-policy-isakmp-p1-10]ike-peer fw1
[USG6000V1-ipsec-policy-isakmp-p1-10]proposal 1
[USG6000V1-ipsec-policy-isakmp-p1-10]tunnel local 103.1.1.1
[USG6000V1-ipsec-policy-isakmp-p1-10]security ?acl 3000
[USG6000V1]int g1/0/1
[USG6000V1-GigabitEthernet1/0/1]ipsec policy ?p1
分院配置
接入交换机配置
[Huawei]vlan ?batch ?10
[Huawei]int g0/0/2
[Huawei-GigabitEthernet0/0/2]port link-type access
[Huawei-GigabitEthernet0/0/2]port default ?vlan ?10
[Huawei-GigabitEthernet0/0/2]int g0/0/1
[Huawei-GigabitEthernet0/0/1]port link-type trunk
[Huawei-GigabitEthernet0/0/1]port trunk ?allow-pass ?vlan ?all
上述对vlan进行划分 其他交换机配置相同
汇聚交换机配置
[Huawei]vlan b 10 20
Info: This operation may take a few seconds. Please wait for a moment...done.
[Huawei]interface GigabitEthernet0/0/1
[Huawei-GigabitEthernet0/0/1] port link-type trunk
[Huawei-GigabitEthernet0/0/1] port trunk allow-pass vlan 2 to 4094
[Huawei-GigabitEthernet0/0/1]#
[Huawei-GigabitEthernet0/0/1]interface GigabitEthernet0/0/2
[Huawei-GigabitEthernet0/0/2] port link-type trunk
[Huawei-GigabitEthernet0/0/2] port trunk allow-pass vlan 2 to 4094
[Huawei-GigabitEthernet0/0/2]#
[Huawei-GigabitEthernet0/0/2]interface GigabitEthernet0/0/3
[Huawei-GigabitEthernet0/0/3] port link-type trunk
[Huawei-GigabitEthernet0/0/3] port trunk allow-pass vlan 2 to 4094
做流量汇聚,放行对应vlan通过即可
核心网关配置
[Huawei]vlan b 10 20 30 40
Info: This operation may take a few seconds. Please wait for a moment...done.
[Huawei]interface GigabitEthernet0/0/1
[Huawei-GigabitEthernet0/0/1] port link-type trunk
[Huawei-GigabitEthernet0/0/1] port trunk allow-pass vlan 2 to 4094
[Huawei-GigabitEthernet0/0/1]#
[Huawei-GigabitEthernet0/0/1]interface GigabitEthernet0/0/2
[Huawei-GigabitEthernet0/0/2] port link-type trunk
[Huawei-GigabitEthernet0/0/2] port trunk allow-pass vlan 2 to 4094
[Huawei-GigabitEthernet0/0/2]#
[Huawei-GigabitEthernet0/0/2]interface GigabitEthernet0/0/3
[Huawei-GigabitEthernet0/0/3] port link-type trunk
[Huawei-GigabitEthernet0/0/3] port trunk allow-pass vlan 2 to 4094
接口放行vlan
[Huawei]interface Vlanif10
[Huawei-Vlanif10] ip address 10.1.10.254 255.255.255.0
[Huawei-Vlanif10]interface Vlanif20
[Huawei-Vlanif20] ip address 10.1.20.254 255.255.255.0
[Huawei-Vlanif20]interface Vlanif30
[Huawei-Vlanif30] ip address 10.1.30.254 255.255.255.0
[Huawei-Vlanif30]interface Vlanif40
[Huawei-Vlanif40] ip address 10.1.40.254 255.255.255.0
核心dhcp配置
[Huawei]dhcp enable
[Huawei]interface Vlanif10
[Huawei-Vlanif10]dhcp select int
[Huawei-Vlanif10]interface Vlanif20
[Huawei-Vlanif20]dhcp select int
[Huawei-Vlanif20]
[Huawei-Vlanif20]interface Vlanif30
[Huawei-Vlanif30]dhcp select int
[Huawei-Vlanif30]interface Vlanif40
[Huawei-Vlanif40]dhcp select int
[Huawei-Vlanif40]
核心路由配置
[Huawei]ospf 1
[Huawei-ospf-1]a 0
[Huawei-ospf-1-area-0.0.0.0]network ?10.1.0.0 0.0.255.255
[Huawei-ospf-1-area-0.0.0.0]
[Huawei-ospf-1]silent-interface Vlanif ?10
[Huawei-ospf-1]silent-interface Vlanif 20
[Huawei-ospf-1]silent-interface Vlanif 20
[Huawei-ospf-1]silent-interface Vlanif 30
[Huawei-ospf-1]silent-interface Vlanif 40
出口防火墙区域配置
[USG6000V1]firewall zone ?trust ?
[USG6000V1-zone-trust]add ?interface ?g1/0/2
[USG6000V1]firewall zone ?untrust ?
[USG6000V1-zone-untrust]add ?interface ?g1/0/1
[USG6000V1]firewall zone ?name yb
[USG6000V1-zone-yb]set ?priority ?40
[USG6000V1-zone-yb]add ?interface ?g1/0/0
出口路由配置
[USG6000V1]ip route-static 0.0.0.0 0 103.1.1.254
[USG6000V1]ospf 1
[USG6000V1-ospf-1]a 0
[USG6000V1-ospf-1-area-0.0.0.0]network ?10.1.0.0 0.0.255.255
[USG6000V1-ospf-1]default-route-advertise
医保网路由配置
[USG6000V1]ip route-static 123.123.123.0 24 22.1.1.254 ?//去往医保服务器
分院NAT配置
[USG6000V1]nat-policy ?
[USG6000V1-policy-nat]rule name no
[USG6000V1-policy-nat-rule-no]source-zone trust ?
[USG6000V1-policy-nat-rule-no]destination-zone ?untrust ?
[USG6000V1-policy-nat-rule-no]source-address 10.1.0.0 16
[USG6000V1-policy-nat-rule-no]destination-address 192.168.0.0 16
[USG6000V1-policy-nat-rule-no]action ?no-nat ?
[USG6000V1-policy-nat]rule name internet
[USG6000V1-policy-nat-rule-internet]source-zone trust ?
[USG6000V1-policy-nat-rule-internet]destination-zone untrust ?
[USG6000V1-policy-nat-rule-internet]action ?source-nat ?easy-ip ?
[USG6000V1-policy-nat]rule name yb
[USG6000V1-policy-nat-rule-yb]source-zone trust ?
[USG6000V1-policy-nat-rule-yb]destination-zone yb
[USG6000V1-policy-nat-rule-yb]action ?source-nat easy-ip
网络测试
测试截图csdn站内私信获取
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:chenni525@qq.com进行投诉反馈,一经查实,立即删除!
- Python教程
- 深入理解 MySQL 中的 HAVING 关键字和聚合函数
- Qt之QChar编码(1)
- MyBatis入门基础篇
- 用Python脚本实现FFmpeg批量转换
- 【数字电路】MacBook使用iverilog进行数字电路仿真
- linux软件安装(yum命令)
- 【HTML】-- 01 初识HTML
- Wireshark把DDoS照原形
- 科创金融的向善力量:浙商银行多措并举赋能科创企业,打造科技金融服务生态圈
- Stable Diffusion的 webui 如何在Windows上使用 AMD GPU显卡?
- IF=16.6 | Quick CTL细胞免疫佐剂免疫HLA转基因小鼠,助力TCR- T细胞构建!
- 高级JavaScript。如何用JavaScript手撸一个富文本编辑器?
- 2024年回炉计划之排序算法(一)
- 基于大数据的校园一卡通数据分析与可视化平台-计算机毕业设计